How the platforms for analyzing information about threats work and what functions are provided by advanced software from this area; comparison of products based on the ROI4CIO analytical table .
The insane increase in the number of advanced threats (APTs) and the increase in the amount of data that needs to be processed to detect attacks are making the work of security analysts more difficult every day. In recent years, the job of an information security engineer has often been to manually sift through hundreds of alerts in an attempt to find real threats. Because of the datasets that organizations generate, manual threat search teams are no longer effective. Resources and software are used to combat this problem, but often the introduction of new tools is hampered by integration into the organization's infrastructure.
The Threat Intelligence Platform automates and adds context to basic threat intelligence — feeds. Feeds are streams of data with indicators of compromise, by which a potential threat is identified: hashes of malicious files, IP addresses and domains associated with criminal activity. Process automation frees up overburdened workforce, provides accurate real-time analysis tools to respond quickly and accurately to threats.
Threat intelligence platforms have emerged because of the amount of data available — both internally and externally — about current and emerging IT security threats. Companies that monitor threats, such as updating antivirus products, have been maintaining global threat databases for years, consisting of software agents running on millions of client computers and other devices. This data, together with feeds from other sources, constitutes platform tools.
What is a Threat Intelligence Platform?
Threat analysis platform ( Threat Intelligence Platform, the TIP ) - a software solution used by organizations for detection, blocking and removal of threats to information security. The platform combines multiple threat intelligence channels, compares against previous events, and generates alerts for the security team. TIPs integrate with existing security information and event management (SIEM) solutions and assign values to alerts, prioritizing them according to urgency.
The advantage of the platform is the ability of information security teams to safely share information about enterprise cybersecurity with other departments and external security experts. The system collects and analyzes threat data, coordinating the tactics and actions of stakeholders. When the security team detects a threat, all relevant departments are involved in the investigation. Thanks to this ability to synchronize actions and manage efforts, the platform is indispensable at critical moments.
Why do you need a platform?
Unlike movies, where hackers do instant harm, in life, hackers can hide on your network for a long time. In this regard, security is changing its focus from protection and response to preventive action - not to eliminate the consequences of an attack, but to find and eliminate threats before causing any damage. Consider the tasks that the platform performs.
Automation of routine tasks and freeing up time
A recent Ponemon Institute survey of IT security personnel found that 84% of respondents believe that threat intelligence should be a fundamental part of strong security systems. According to the traditional IS scheme, teams conduct an iterative search on alarms to distinguish real threats from false positives. At the same time, the platform provides teams with already enriched information to determine the type and severity of the threat, automatically discarding false alerts.
Improving the Accuracy of Your Threat Intelligence
One of the reasons people do poorly at repetitive, routine tasks is that at some point their eyes become blurry and eventually a processing error occurs. The platform eliminates the likelihood of such errors.
Finding Your Own Vulnerabilities
Often times, security teams are more concerned with external threats than with internal ones. TIP scans for vulnerabilities and warns of weaknesses in your IT infrastructure and third-party ecosystem, helping to proactively address weaknesses and strengthen the system.
Accelerating data processing
Manual data handling processes are laborious and time-consuming. This becomes a decisive factor during an attack, when an instant reaction is needed to contain a breakthrough.
Ensuring a consistent response to threats
The automated platform provides relevant security information to everyone involved in the cyber defense process in the company. This means that the entire team receives the necessary information at the same time, the strategy and security processes will be coordinated.
Principle of operation
Threat intelligence platforms serve three main functions:
- Aggregation is a collection of channels through which information about threats enters a centralized feed.
- Analysis - data processing using indicators for identifying and identifying security threats.
- Action - Notify Incident Response Teams about threat data.
These functions are implemented by the platform through the automation of the workflow of the entire security system life cycle. Stages related to the threat intelligence security lifecycle:
Collecting
Summarizing data from multiple channels including STIX, XML, JSON, OpenIOC. It is important to include data from internal sources such as weblogs and external sources such as the Internet and the dark web. The deeper and better the feeds, the more effective the platform.
Correlation The
automated TIP process sorts and organizes data using tag metadata and removes irrelevant or redundant information. Then there is a comparison with the supervised information, patterns and correspondences are found for detecting threats.
Contextualization
Context is a key parameter in threat intelligence. Without it, it is easy to confuse an anomaly with a threat, and vice versa, to ignore the real threat. At this point, TIP provides context to the sorted data to eliminate false positives by adding specifications - IP addresses, network and domain block lists, providing teams with as much information as possible about a potential threat.
Threat Analysis
TIP analyzes threat indicators in real time for data relationships. Further, this information can be “taken into circulation” by security analysts to find hidden threats.
Integration
Threat intelligence platforms integrate with the security tools used by the organization to maximize the flow of information. At this stage, the platform transfers the collected and analyzed data to the appropriate departments for processing.
When the platform detects a threat, a warning is sent to the information security group about the need to launch an incident response.
Action An
effective threat intelligence platform is responsive. Integrated TIPs partner with Information Clearing and Analysis Centers (ISACs) and Information Sharing and Analysis Organizations (ISAOs) to provide them with the information they need to develop security tools and applications.
Vendor delivery models
Threat Intelligence Service Providers are relative newcomers to the security industry, so the types of services provided still vary a lot.
Some of these services provide only feeds that are cleared of false positives. The most common paid services provide aggregated and correlated feeds (two or more), custom alerts and alerts specific to the customer's risk landscape.
Another type of threat intelligence service aggregates and correlates data and automatically incorporates information into security appliances — firewalls, security information and event management, industry threat assessments, and security consultancy.
Each type of threat intelligence platform is available on a subscription basis, typically at two or three pricing tiers, and delivered via the cloud, or more rarely on-premise or hybrid.
Due to the high cost of such platforms, as well as the need for equipment for local deployment, now such services are targeted at large organizations and enterprises. However, as cloud services expand into lower market segments, threat intelligence tools will become more accessible as well.
The cost of the platforms varies as much as the cost of the threat intelligence services themselves. Data links alone can cost thousands of dollars a month, but the associated costs include the cost of maintaining a 24/7 security operations center staffed by technicians and analysts. In comparison, managed security services typically cost tens of thousands of dollars a month. The least expensive services require more human time and effort on the part of the client.
Because threat intelligence services are very different from one another, understanding how the information will be used and having the necessary personnel to properly use the service becomes a major challenge in selection.
We compared six ROI4CIO threat intelligence platforms based on the following characteristics:
- own feed-suppliers or feed pre-processing analytical centers;
- number of feed suppliers out of the box; supported ways of receiving feeds;
- the possibility of enriching data from external sources (for example - WHOis, PassiveDNS, VirusTotal, etc.);
- search for matches in SIEM events;
- direct response to incidents by integrating with third-party information security systems;
- incident response using complex algorithms (playbooks);
- the ability to integrate via REST API;
- the ability to build a graph of links between feed objects and internal artifacts.
ThreatQ by ThreatQuotinet
ThreatQ is an open and extensible threat intelligence platform that provides security teams with the context and advanced customization they need to improve security and conduct successful threat mitigation and management operations.

The product from ThreatQuotient, a digital security company founded in 2013, prioritizes threats and automates processes to support decision-making while making the most of limited resources. The company specializes in incident response, threat hunting, anti-phishing, alert sorting, and vulnerability management.
ThreatQ Platform is ThreatQuotient's flagship solution. The platform provides SOC analysts, incident response specialists, and analysts with flexibility, visibility and control by providing context and keeping data up to date.
How it works
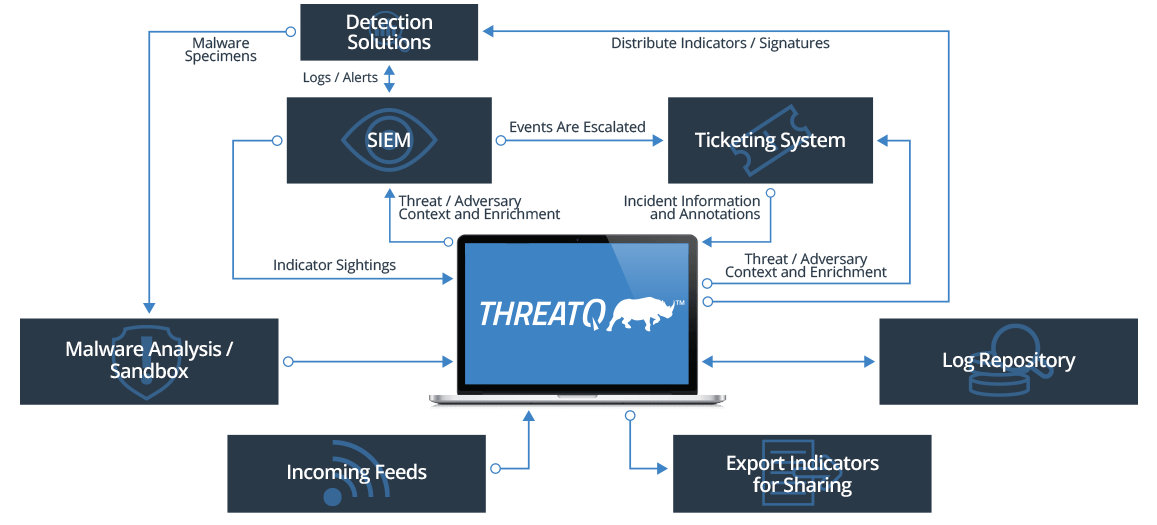
The Solution Threat Library is a central repository of external threat intelligence that is enriched and augmented with internal threat and event data for up-to-date and contextual information customized to your unique business environment.
Using the integrated Threat Library, Adaptive Workbench, Open Exchange, and ThreatQ Investigations, threat analysts can detect, investigate, and act faster than the security operations center.
ThreatQ works with your existing processes and technologies to improve the efficiency of your existing infrastructure — the platform gives customers more insight into their security resources. The Open Exchange ThreatQ library adds value to existing security investments with industry-standard interfaces and SDK / APIs for customization, tool, command, and workflow integration.
Interface

Characteristics
Own feed-suppliers / analytical centers for feed preprocessing: present
Number of feed-suppliers out of the box: 100+
Supported ways of receiving feeds: CSV, JSON
Possibility of enriching data from external sources (for example - WHOis, PassiveDNS, VirusTotal, etc. .):present
Search for coincidences in SIEM events: present
Direct response to incidents by integration with third-party information security systems: present
Response to incidents using complex algorithms (playbooks): present
Possibility of integration via REST API: present
Possibility of building a graph of links between feed objects and internal artifacts : present
ThreatStream by Anomali
Anomali integrates with SIEM and other log sources, maintaining historical visibility without duplicate logs. Historical data is constantly analyzed, compared with new and existing threat data to identify signs of violations.

Anomali ThreatStream is a SaaS threat intelligence platform that can also be deployed locally as a virtual machine. The tool includes over 140 open source channels and makes it easy to include commercial channels through the Anomali APP Store.
A key feature of the ThreatStream platform is the Investigation Dashboard, which is used to dive into threats of interest. This is where new investigations can be easily created as you add the observables you want — just assign them to a user or team and use ThreatStream integration with ServiceNow to assign a ticket if needed.
Scheme of work
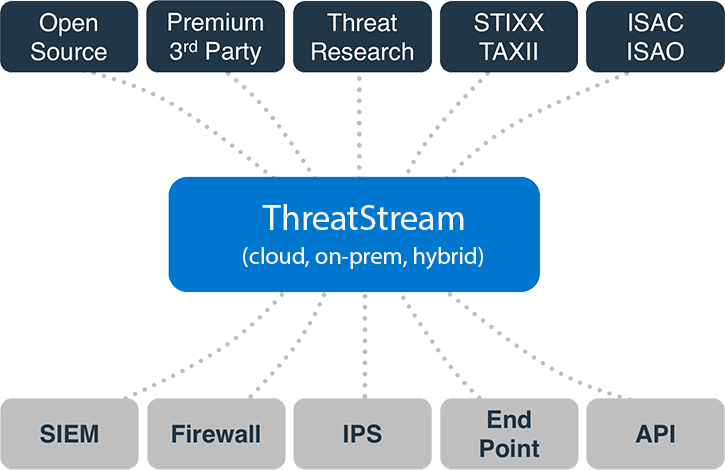
ThreatStream includes a built-in sandbox that allows you to upload and analyze files. You can also import intelligence reports or IoCs lists. The product integrates with many popular SIEMs, includes a case management function for assigning research tasks, support for an analyst's workflow, and allows you to collaborate with trusted partners. With ThreatStream Link, data can be exchanged directly with devices in the enterprise.
In addition to proprietary monitoring indicators, the platform takes feeds and enriches them with information from its own sources, visualizing information and breaking it down into components for better understanding.
Investigation reports are issued in STIX, Kill Chain or Diamond format. The platform integrates with Splunk, providing additional useful tools.
Interface
Characteristics
Own feed-suppliers / feed pre-processing analytical centers: present
Number of feed-suppliers out of the box: 100+
Supported methods of receiving feeds: CSV, JSON, HTTP
Possibility to enrich data from external sources (for example - WHOis, PassiveDNS, VirusTotal and others): present
Search for matches in SIEM events: present
Direct response to incidents by integrating with third-party information security systems: present
Responding to incidents using complex algorithms (playbooks): N / A
Possibility of integration via REST API: present
Possibility of building a graph of links of feed objects and internal artifacts: present
EclecticIQ Platform
EclecticIQ is a platform that enables analysts to conduct faster, better, and more deep investigations while spreading intelligence at machine speed.

The EclecticIQ platform processes both structured and unstructured threat data from open sources, industry partners and internal resources, which are combined into a single dashboard. The platform can be deployed both in the cloud and on-premises.
EclecticIQ does not use a data collection method. Instead, the company employs a team of analysts who continually investigate threats to gather all intelligence in a structured format and offer a comprehensive overview with practical solutions.
Scheme of work
The solution is both a consumer and production platform. Here analysts can create a workspace for an individual incident, which will contain all investigations related to it. Once completed, the organization can archive the workspace and make it active again if the incident reoccurs.
Security teams can configure Discovery Alerts to accompany the emergence of currently monitored threats. It also regulates the setting of alerts to hunt for specific entities (malware families, threat actors, etc.) and signaling of any incoming threat variants related to these entities.
The Report Builder feature demonstrates the EclecticIQ production environment. She can create reports based on specific options, and analysts can easily add information and context to the report. The solution uses TLP to prevent the spread of information outside the platform.
Interface
Characteristics
Own feed-suppliers / feed pre-processing think tanks: present
Number of feed-suppliers out of the box: 20-100
Supported ways of receiving feeds: CSV, JSON, HTTP
Possibility to enrich data from external sources (for example - WHOis, PassiveDNS, VirusTotal, etc.): present
Search for matches in SIEM events: present
Direct response to incidents by integration with third-party information security systems: present
Response to incidents using complex algorithms (playbooks): N / A
Possibility of integration via REST API: present
Possibility to build a graph of links between feed objects and internal artifacts: present
ThreatConnect Platform
The ThreatConnect platform was designed to understand the mindset of adversaries, automate workflows and mitigate threats using intelligence. ThreatConnect offers a suite of products built on an analytical automated platform.

The ThreatConnect platform provides the ability to automate the aggregation of threat intelligence sources, freeing teams from the routine task of collecting data. Building on its data aggregation capabilities, ThreatConnect integrates with a variety of analytical tools and services to further streamline and automate team work. Deployment to the cloud or on-premises is available. There is an orchestration option for those looking to deploy a system across multiple environments.
Scheme of work

ThreatConnect Research Group - Globally renowned cybersecurity analysts who continually provide new intelligence. The group includes the best analysts in the industry from intelligence agencies and the most informed analytical circles. They curate information source, TC Identify, which provides verified threat intelligence collected from over 100 open sources and crowdsourced data from dozens of communities.
ThreatConnect allows security teams to create and customize dashboards for specific needs, while the main dashboard provides a quick visualization of recently observed metrics and trending topics.
The platform's playbook panel provides hundreds of application options to automate the processing of almost any action. Customers can create their own applications or modify existing ones. The platform supports sophisticated filtering with tags to classify elements by behavior, geography, and a range of other characteristics. Analysts can collaborate within the incident report details page.
The platform supports multiple SIEM integrations, in particular Splunk, creating a two-way communication between ThreatConnect and Splunk, so threat information goes directly to Splunk, where teams can view threat summaries and other information.
Interface
Characteristics
Own feed-suppliers / feed preprocessing think tanks:present
Number of feed-providers out of the box: 100+
Supported ways of receiving feeds: CSV, JSON, HTTP
Possibility of enriching data from external sources (for example - WHOis, PassiveDNS, VirusTotal, etc.): present
Search for matches in SIEM events: present
Direct incident response by integrating with third-party information security systems: present Incident response
using complex algorithms (playbooks): N / A
Possibility of REST API integration: present
Possibility to build a graph of links between feed objects and internal artifacts: present
Threat Intelligence Platform by R-Vision
R-Vision TIP is a platform that allows you to automate the collection of indicators of compromise from both free and commercial exchange channels, process them, enrich them with information and use them in internal security systems for timely detection of threats and investigation of incidents.

R-Vision is a Russian cybersecurity systems developer who, since 2011, has been developing solutions and services to counter current cyber threats and ensure reliable information security management.
The company's platform, R-Vision TIP, provides automatic collection, normalization and enrichment of indicators of compromise, transfer of processed data to internal security measures, search and detection of indicators in the organization's infrastructure using sensors.
Supported sources of information about threats include data from FinCERT of the Central Bank of the Russian Federation, Kaspersky, Group-IB, IBM X-Force Exchange, AT&T Cybersecurity. A set of sensors allows the platform to monitor in real time, retrospectively search for traces of malicious activity in the organization's infrastructure and notify security analysts in the event of a risk.
R-Vision TIP simplifies the work with threat data by collecting, normalizing and storing data from many sources in a single database, facilitates the identification of hidden threats by monitoring relevant indicators in SIEM, syslog and DNS queries using sensors.
Scheme of work
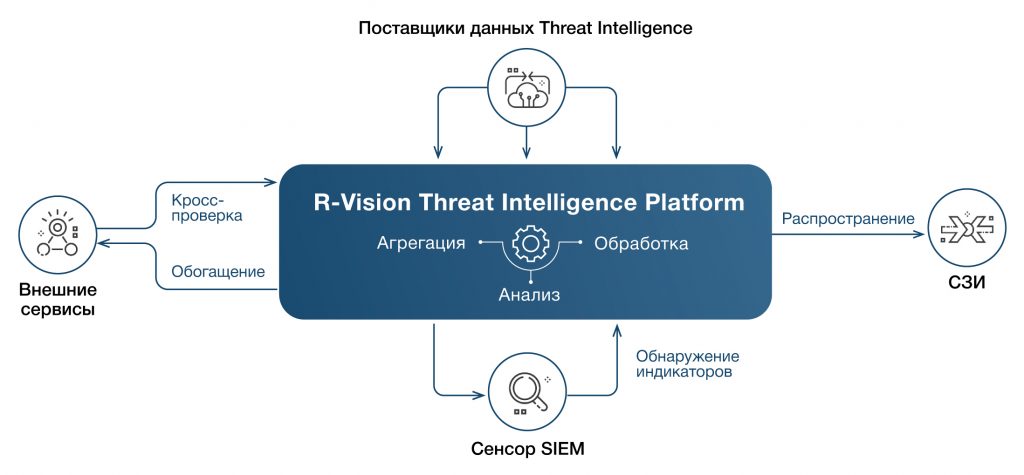
TIP allows you to block threats in time by automatically uploading processed data directly to internal defenses. Pre-processing reduces the number of false positives that occur when using raw data. Supports automatic uploading of indicators to equipment Cisco, PaloAlto Networks, Check Point.
R-Vision Threat Intelligence Platform allows you to implement and automate the required scenario for working with indicators. The scenario may include enrichment, detection, distribution to protection, notification.
The new release of the product introduces the link graph tool. It displays the relationship of the malicious indicator with other entities, displaying a visual representation of the threat. The graph contains tools for scaling, filtering and clustering objects by various attributes.
Interface
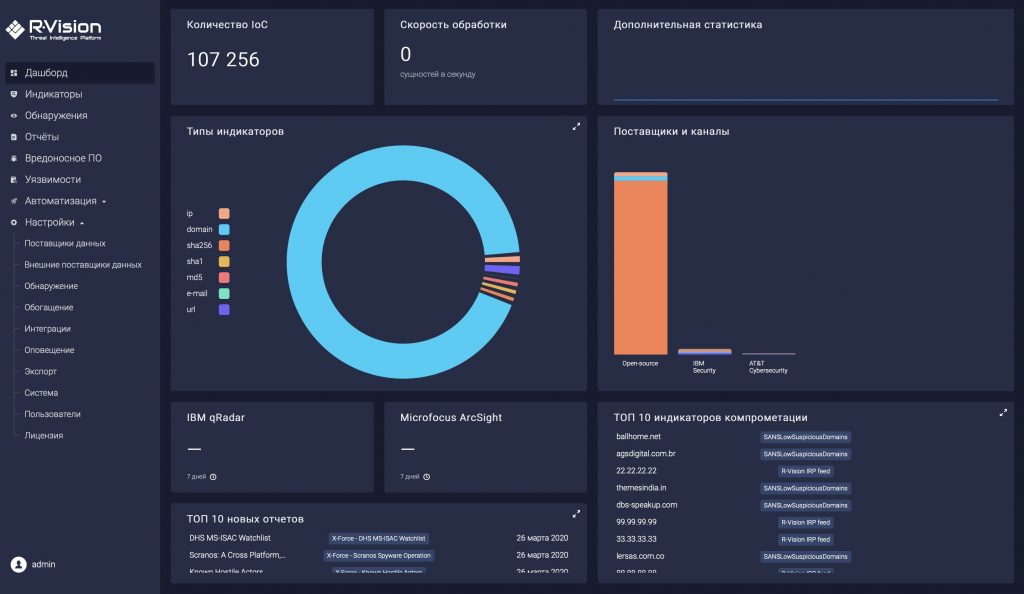
Characteristics
Own feed-suppliers / feed analysis centers: N / A
Number of feed-suppliers out of the box: 20-100
Supported ways of receiving feeds: CSV, JSON, HTTP
Possibility to enrich data from external sources (for example - WHOis, PassiveDNS, VirusTotal, etc.): present
Search for matches in SIEM events: present
Direct response to incidents through integration with third-party information security systems: present
Response to incidents using complex algorithms (playbooks): N / A
Possibility of integration via REST API: present
Possibility of building a graph of links between feed objects and internal artifacts: N / A
——
Natalka Chech for ROI4CIO