Intel Boot Guard technology is designed to exclude such attacks: in theory, it ensures that only trusted code is loaded at the initial stage of computer startup. As it turned out, when the computer wakes up from S3 sleep, not all devices authenticate the contents of the flash memory, which allows you to change the code. The consequences of such an attack can be serious. In particular, it becomes possible to decrypt data on a hard disk if it is possible to read the keys stored in RAM.
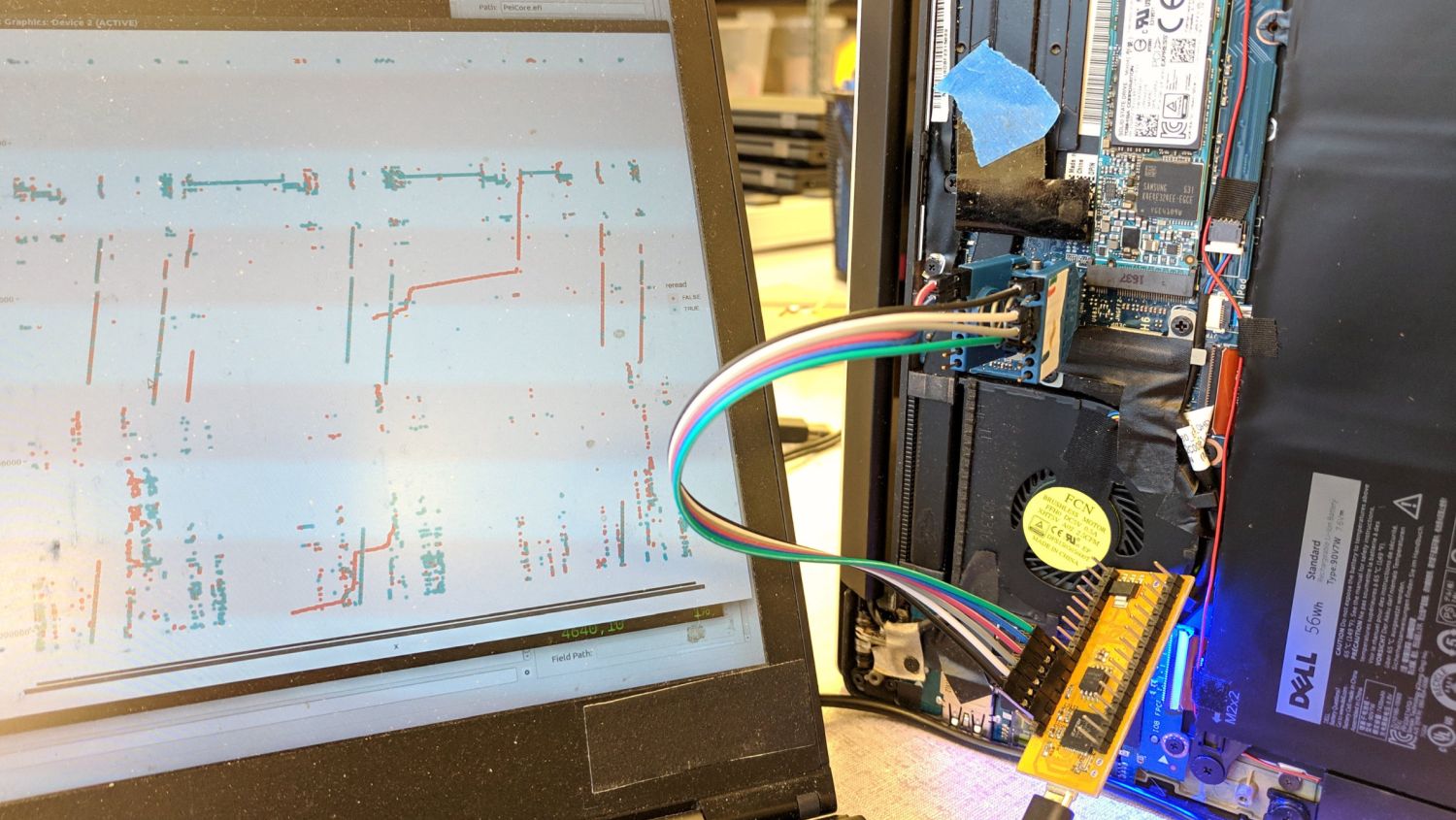
To detect the attack, Trammell used his own development - a hardware flash memory emulator spispy , which allows both to track access to the BIOS chip and to replace the boot code on the fly, in part or in whole. The vulnerability is qualified as a Time-of-check / Time-of-Use (TOCTOU) error - this term describes a situation when the code is validated “at the wrong moment”, and after verification, the possibility of software substitution remains.
There is a hint in the study that hardware manufacturers often refuse additional validation of the BIOS code (Hudson discovered the problem in devices from five different vendors). Perhaps they do this because of the requirements of Microsoft, which sets serious restrictions on the time the Windows logo appears after waking up from sleep. If true, safety has been sacrificed for user comfort. The problem is aggravated by the fact that such parameters are set in hardware and cannot be changed by software.
Although Hudson does not know exactly how Intel solved the problem, most likely the vendor's settings are now partially ignored, and the new firmware of the CSME module forcibly checks the validity of the BIOS code upon exiting sleep.
Attacks like the one described by Hudson, by definition, cannot be massive, but it will not be easy to close the vulnerability - you have to wait until the patch reaches specific devices through the laptop or motherboard manufacturer. On the other hand, you can protect your valuable data from such an attack yourself: just turn off your laptop in situations where it is left unattended.
What else happened
Kaspersky Lab experts examined in detail the work of two ransomware Trojans, Ragnar Locker and Egregor. These two examples show how cybercriminals not only extort money for decryption, but also steal victims' data and threaten to publish it.
Nvidia has fixed another major bug in its software, this time in the GeForce Now software. The arbitrary code execution vulnerability relates to the open source library OpenSSL used in the software.
Avast found a bunch of applications on Google Play that allegedly extend the functionality of the Minecraft game, but in fact charge the victims $ 30 a week.
Microsoft's monthly patch set has closed at least one Zero Day (we wrote about this vulnerability two weeks ago), as well as a serious vulnerability in the Network File System service. Another vulnerability (CVE-2020-1599) allows malicious code to attach to an executable file, while maintaining the validity of the digital signature. Meanwhile, two more zero-days are patched in the Google Chrome browser.
Apple requires software vendors to provide a manifest detailing how to handle user data. The company itself is being criticized (see tweet above) for new functionality in macOS Big Sur: system applications can now connect directly to the company's servers, ignoring custom firewalls and VPN clients. First, this practice can be exploited by malware. Secondly, this approach reveals the real IP of the user, even if he wants to hide it.