
For more than 15 years I have been working in a small, but rather well-known in narrow circles of the Russian company from Novosibirsk "Tornado Modular Systems", which develops and implements software and hardware complexes for process control systems of energy facilities. Over the years, I have been engaged in completely different areas: programming specialized top-level software systems for MP relay protection and automation, setting up telemechanics and automated process control systems, participating in the development of a modern industrial computer and selling complex projects for many tens of millions of rubles. Such a variety of production tasks, perhaps, predetermined what interested me in this new direction - IS ACS TP.
But first things first. Now it may seem that the current, one might say, avalanche-like growth of the market for equipment, software and services for solving the problem of information security of an automated process control system is due to the emergence of threats of influence on technological processes from the outside, which also leads to a natural growth of the regulatory framework of the FSTEC regulator, etc. This opinion is largely true, however, it seems to me that the foundation of these processes is the uncontrolled spread of the Ethernet interface as a de facto standard for organizing industrial networks of industrial control systems. Why uncontrollable? How can you say so? In my opinion, there is every reason for this. The topic of IS ACS TP appeared not so long ago, and before that, any designer of an ACS or a subsystem, with a light movement of his hand, connected the networks of the power unit, the switchyard of the station, the main control panel and many more small and not very control and management systems.All this was done on the orders of the customer in order to ensure greater observability of the facility and improve the quality of control and management.
What are the results of these good intentions? Specialists in the maintenance of technological monitoring and control systems have largely lost their understanding of the processes taking place in these LANs and their possible impact on maintaining the operability of the technological process. You might think that this is a consequence of the low qualifications of the staff. But in many cases this is not true. The fact is that the scale of information for analysis by personnel affects the adequacy of the perception of the state of the control object. The volume of industrial networks and the number of active devices today is such that even a qualified specialist cannot foresee the possible consequences of making changes to the settings of the controllers of the automated process control system, network equipment, installing new devices, or even bringing the control subsystems into repair or routine adjustment modes.And I am not yet touching on the issues of external hackers with various tasks and means of penetration and influence.
Thus, the appearance of information security specialists at industrial facilities at checkpoints, in general, organically coincided with this growing pressure of industrial networks, under which the backs of the valiant operating personnel have already begun to bend. These knights of firewalls, anti-virus defenses and intrusion detection systems were supposed to take up the banner of industrial security and ensure its smooth operation in modern conditions with Internet connections, remote communication channels, MES and ERP sucking gigabytes of data from the process control system.
I believe that in many respects this task is being solved by modern developers of information security systems for process control systems, or will be mainly solved in the coming years. Of course, there are difficulties, not all ICS are steadfastly transferring the integration of information security tools into their sensitive architectures. But these are working moments. However, I think that there are a number of conceptual issues that should be analyzed by suppliers and integrators of information security ICS tools.
In order to understand the effectiveness of the means of ensuring the information security of the APCS, it is useful to consider those means that provide its target tasks. The main tasks of the APCS in order of priority are:
1. Maintaining the technological process
2. If it is impossible to save the first technological equipment and the life of personnel
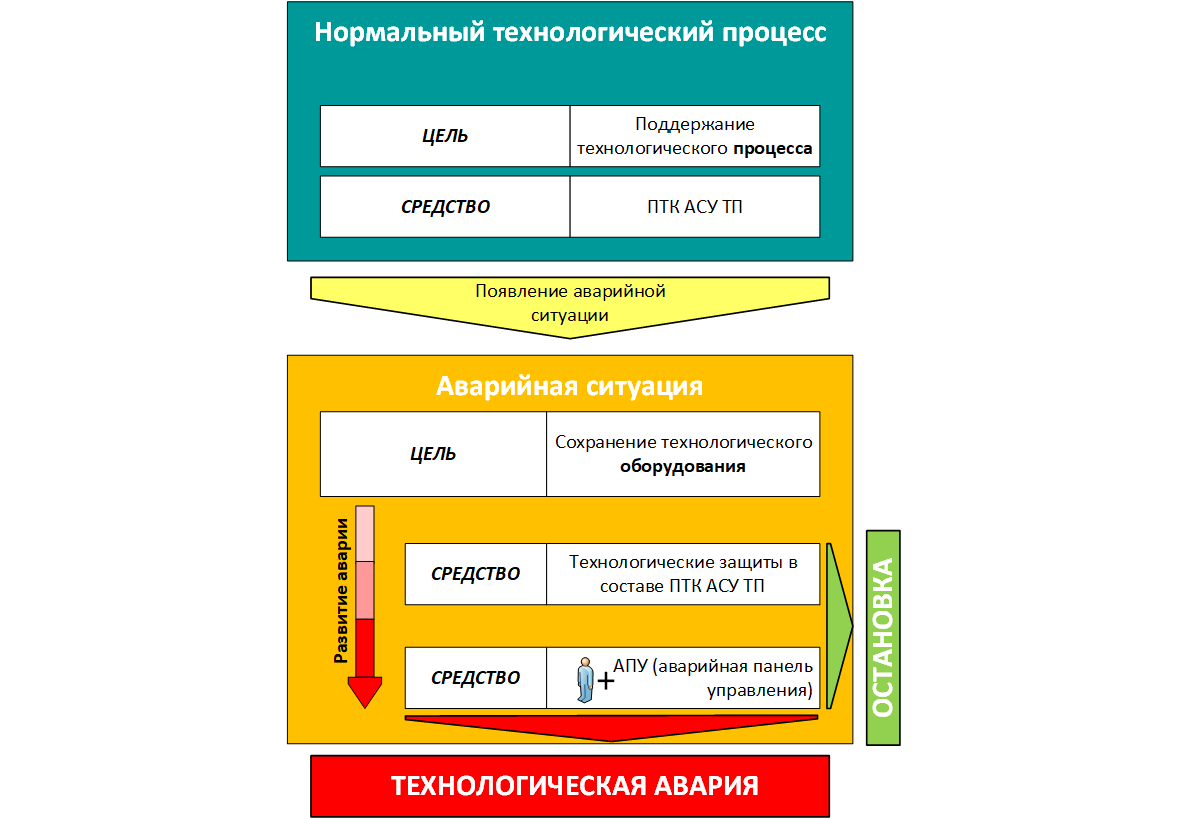
In the event of a technological accident, there are two options for the development of the situation. The development of an emergency situation can be stopped by the automatic action of the protection subsystem as part of the software and hardware complex of the APCS, or by stopping the technological process by the personnel on duty using the emergency control panel. In this case, a routine shutdown of the technological process will be implemented. If, for some reason, these measures did not allow to routinely stop the technological process, an emergency situation may develop with unpredictable consequences. So, all modern APCS include software and hardware and simple hardware designed for automatic or manual safe shutdown of the technological process.
Now we will consider the target tasks of the IS of the APCS. Companies developing software and hardware for information security control systems have historically been the developers of the same solutions for the IT market. But the tasks of IS IT and IS ICS are ideologically different. In the part of information security IT, the task is to maintain the operability of the entire IT infrastructure of the organization, including all connections (connection to the Internet, vpn to branches, etc.). We can even say that the performance of these connections is one of the main priorities, since a useful product of many organizations, when disconnected, for example, the connection to the Internet tends to zero. As for the IS of the APCS, today the main task is formulated as:
1. Ensuring the functioning of the APCS, including all communications
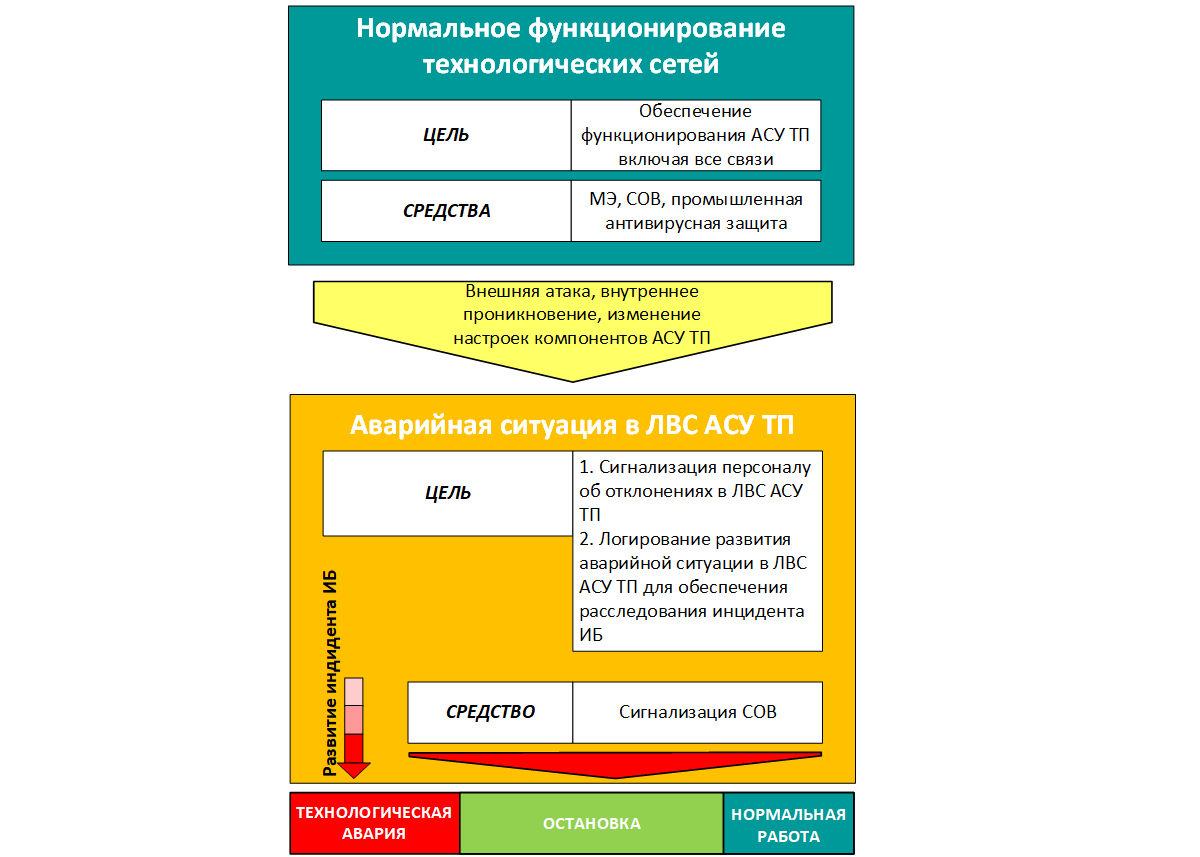
Attention is drawn to the fact that in the event of an information security incident, its outcome can be anything, up to a technological accident, and practically does not depend on the facility's personnel on duty. At present, SOCs for objects with APCS are practically not found, and their appearance can be restrained by an assessment of their financial and especially target efficiency for APCSs. This means that the existing paradigm for the development of IS ICS is distinguished by the absence of means of active influence on the development of an incident of IS ICS after the moment of successful penetration into the LAN of the ICS.
In fact, at an industrial facility, we can decompose all industrial networks into conditionally isolated segments, which by themselves ensure the operation of the technological process. Thus, in critical situations, or situations with an increased level of danger for the IS of an industrial facility, the connections of such subnets are not valuable from the point of view of the technological process. And here there is the first dissonance - information security specialists are used to seeing as their goal the preservation of the operability of the entire infrastructure of the organization, while in the part of information security, ICS, they must begin to understand that not all connections are valuable. Consequently, in certain situations, they can be physically disabled to minimize or stop the spread of destructive processes in the APCS network.
Let me give you one example. We all know the accident at the Sayano-Shushenskaya HPP. I will not touch upon this object itself, the development of the accident is well described. One of the factors that led to it was the transfer of the Sayano-Shushenskaya HPP to the frequency control mode in the power system. The reason for this transfer is that a fire broke out in the communication room of the Bratsk hydroelectric power station, which is the main frequency regulator in the Siberian power system. As a result, the main dispatch center of the ODU of Siberia lost all communication with all the automated systems of the Bratsk HPP, including the automatic frequency and power control system. Thus, one of the key energy facilities in Siberia dropped out of the automatic regulation process. The communication of the automated systems was broken.How did this affect the functioning of the Bratsk hydroelectric power station itself? Actually, almost nothing. Of course, the station no longer performed automatic regulation, but the generators remained in operation, the station was controlled via voice communication channels from the Siberian ODU, and the station automation systems worked. This example shows that even the loss of important control and management channels may not lead to a process shutdown. What can we say about the numerous, in fact, informational connections of the APCS - data transfer to ERP and MES, general facility control panels, remote access channels, etc. Consequently, in terms of ensuring measures for IS ICS, a new principle should appear - not all LAN connections of the ICS are valuable, such connections should be identified when developing IS ICS projects,the project must provide for the possibility of physically disconnecting such links.
The second dissonance that I feel relates to the response to incidents of information security ICS. As a person involved in automated process control systems, I am used to the fact that when any disturbance appears, the control system with its algorithms compensates for this disturbance. That is, there is an active reaction. And what is meant by the term "Response to an ICS incident"? In most cases at an industrial facility, this action implies a post-analysis of the incident and the adoption of measures to adjust the protections and settings in terms of information security and APCS to prevent such a case in the future. One case of a regular shutdown and subsequent restart of a large technological unit can cost tens of millions of rubles, a shutdown of a technological unit with damage to technological equipment can cost hundreds of millions of rubles. So what,all attacks and intrusions occur so quickly that the on-duty personnel (the information security specialist of the facility, at least now, is not the on-duty personnel) cannot do anything? In most cases, no. The modern IDS software, together with the analysis of the value of the LAN connections of the APCS, make it possible to form effective scenarios for the response of the facility personnel on duty to incidents in the industrial networks of the APCS.
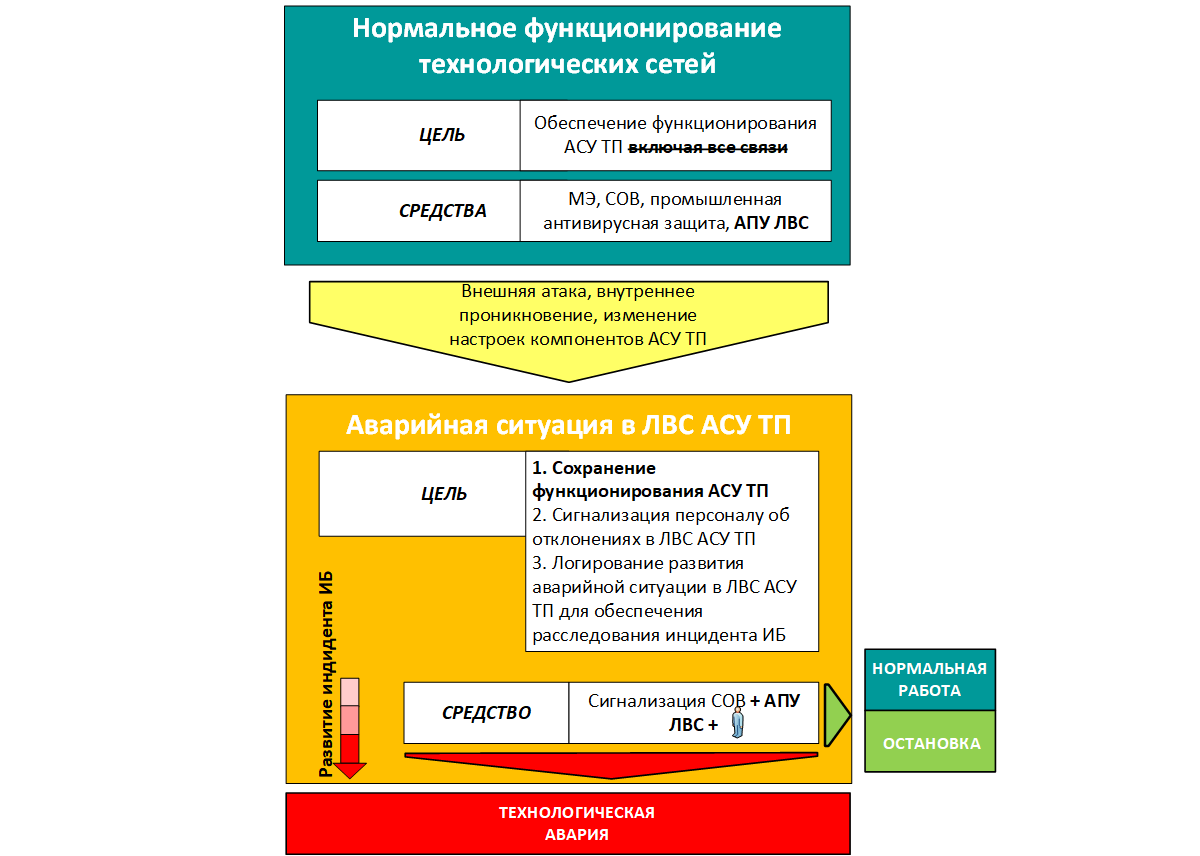
Disabling unnecessary links can stop the attack, or prevent it from spreading to other connected ICS LANs. Of course, in this matter, it is necessary to form certain scenarios for analyzing IDS messages and assessing the adequacy of an object's controllability in an incident, on the basis of which it is necessary to formulate instructions for the actions of operational and duty personnel in conditions of a threat or the implementation of an information security incident. To implement the function of disconnecting unnecessary links, an Emergency LAN Control Panel of the APCS can be provided, which contains Ethernet breakers.
And the last aspect regarding the introduction of modern IDS systems for process control systems. It seems to me that, at least for today, the main danger for the process control system is the facility's own personnel or seconded specialists. Moreover, I consider them dangerous even if they do not have an installation to damage the APCS or they themselves do not know that their flash drive has a program for penetrating the APCS, which is activated automatically. Today's realities are such that reconfiguring any protection terminal can increase the network load by 10% in the normal operating mode of the technical process. This can lead to a LAN failure at the time of the transition of the technological process to pre-emergency and emergency modes and a possible failure of technological protection, equipment damage.This circumstance should push the developers of IDS to create means of displaying key metrics of technological networks of process control systems. Such as: loading of various network segments (average on an interval, maximum), response time, displaying information flows between different subnets to diagnose insufficient LAN segmentation, etc. Such information, it seems to me, will be in demand by operating personnel and will maintain the required level of process hygiene exchange of technological data in industrial networks of automated process control systems.will be in demand by operating personnel and will allow maintaining the required level of hygiene of the process of exchanging technological data in industrial networks of the process control system.will be in demand by operating personnel and will allow maintaining the required level of hygiene of the process of exchanging technological data in industrial networks of the process control system.