Like many other scientific works, research is of little use in practice, just like, say, eavesdropping through a light bulb or talking with a smart speaker using a laser.
According to cryptographer Bruce Schneier, what is impressive in this case is the fact that the researchers were able to figure out at least something. And one more thing: as a rule, such algorithms work better, the more material is available for analysis. The pandemic and mass remote control have created a situation where it is theoretically possible to collect an archive of hundreds of hours of video for each of us.
The scholarly work contains a dozen references to similar past studies to assess the arsenal of eavesdropping and eavesdropping tools. Among them - keylogging by electromagnetic radiation, by the movement of the eyes of the printer, by the movements of the tablet (it is assumed that we are shooting the back of the device). They mention the video analysis used in practice, in real attacks, where a PIN code is typed on the keyboard of an ATM or payment terminal. Further, it is even more interesting: recognition of input through vibration analysis - by a third-party sensor or using standard sensors of a mobile device or smart watch. Surveys around the topic determine keystrokes by the actual sound of the keyboard, for this, even a video is not required. In the Zoom version, it is theoretically possible to combine analysis methods for sound and picture.
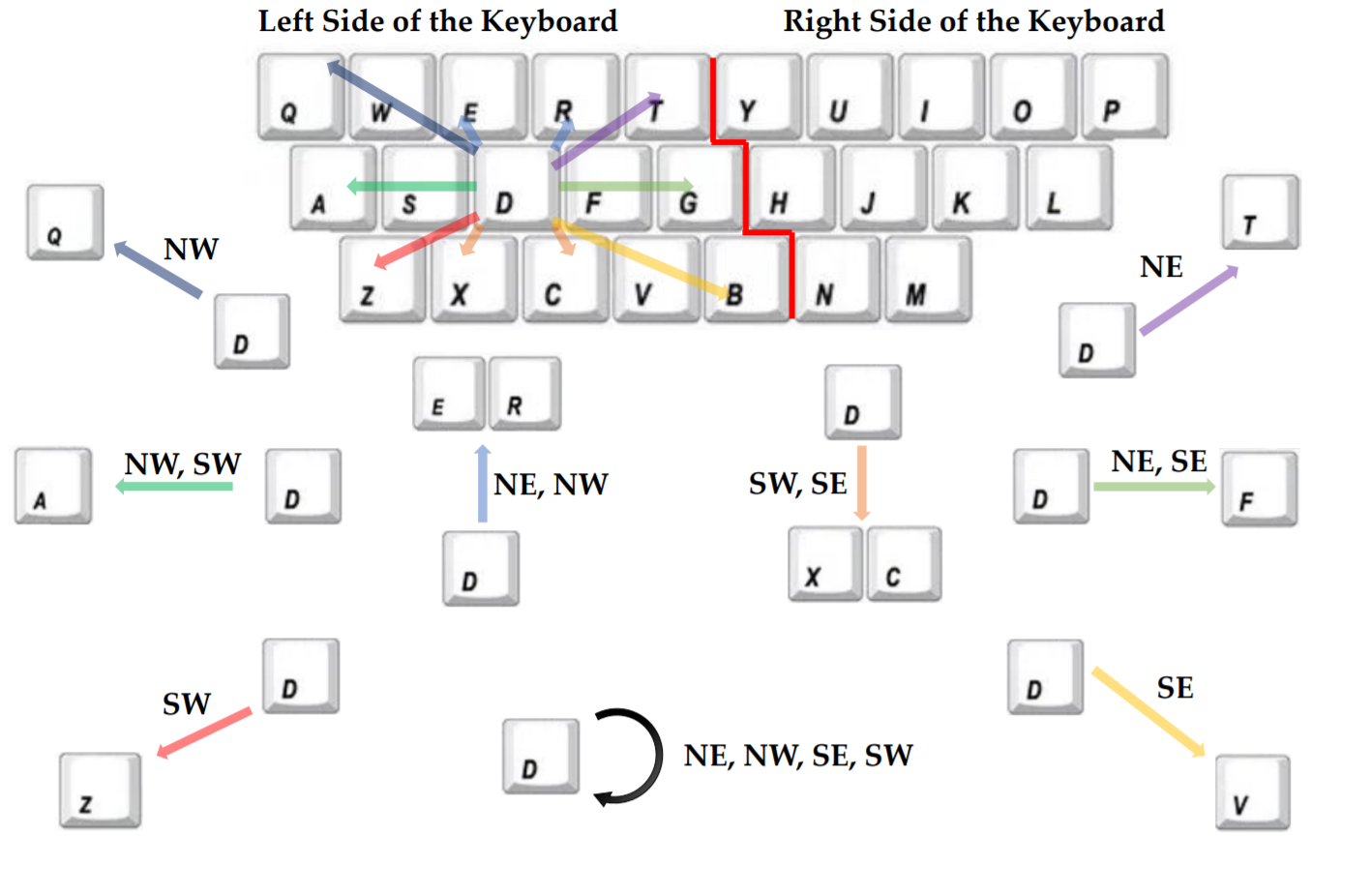
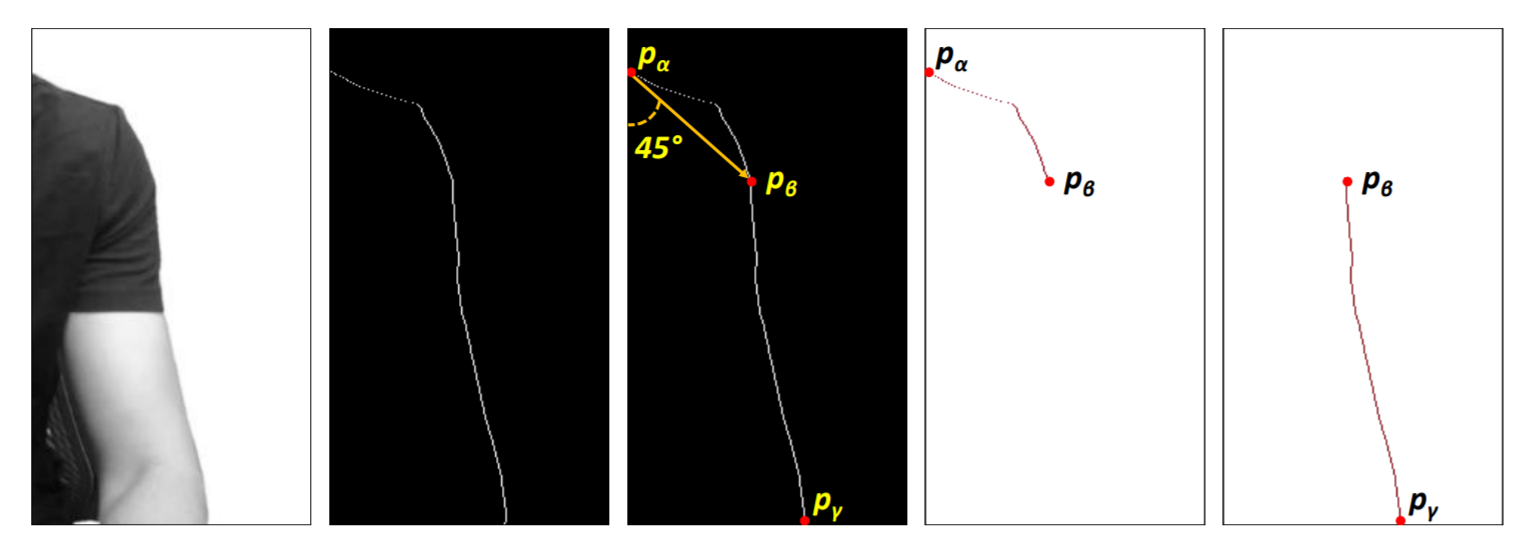
In an extremely simplified form, the new peeping method works like this: the victim's face is recognized, and small shoulder movements are analyzed. The keyboard is conventionally divided into two parts: for the left and right hands. Further, the direction is roughly determined: with one movement, we assume that the key is pressed above and to the left of the center of one of the keyboard halves. Otherwise, it is lower and to the right, and so on. Acceptable accuracy is given by comparing guesswork with a dictionary, which gives the title of this post a light golden crust.
The password, if it can be stolen, is the simplest one, which can be determined by brute-force in five minutes. For minimally difficult, the probability of identification was 18.9% The technique also suffers from the simplest methods that make tracking difficult. It is supposed to be set with two hands, which means that it will not be possible to determine the set of letters with the fingers of one hand. It is required to determine the movement of the shoulders, and this is hampered by loose clothing. In general, this is an extremely impractical study, which nevertheless impresses with its audacity and is certainly useful for information security enthusiasts.

What else happened
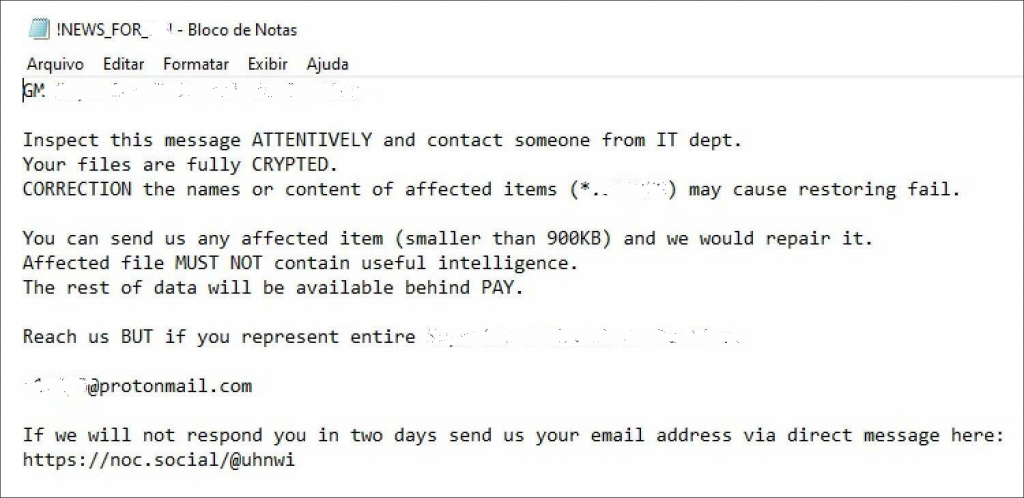
Kaspersky Lab experts are investigating a Linux encryption Trojan recently spotted in attacks on the Texas Department of Transportation and Konica Minolta. The picture above is the result of a Windows Trojan, presumably used by the same group.
The Twitter thread above describes an interesting experiment. A private key is uploaded to the public source code repository to access the server on Amazon Web Services, and the time until the attempt to log into the server is tracked. On GitHub hosting, the AWS token was used within 11 minutes, on GitLab - an hour after the commit.
In the release of iOS and iPadOS 14.2, Apple closed 24 vulnerabilities, three of which were allegedly used in attacks.
US law enforcement authorities gained control over the Bitcoin wallet used in the operations of the Silk Road darknet market (closed in 2013). Since then, almost 70 thousand bitcoins have been stored there, at the time of publication it is about a billion US dollars.
New researchshows how forms are used for phishing in Google Forms. Among the companies attacked is Google itself.