Containerization, CI / CD, orchestration, microservices, and agile processes are the tag cloud now in the vocabulary of security engineers. The microservice model and related technologies have led to a variety of approaches in the implementation of the security architecture of modern solutions, and a single approach to its construction has not yet been seen. But there are technology leaders in the field of microservice development, there are known configuration flaws and vulnerabilities in the implementation of different architectural approaches, and there are a huge number of "best practices" for building a reliable architecture. In this material, prepared on the basis of a research article published jointly with Denis Makrushin (makrushin) from the Advanced Security Research team of the Huawei Advanced Software Technology Lab, we will analyze typical architectural approaches to implementing authentication and authorization in microservice systems, their advantages and disadvantages. And we will do this so that security architects have the opportunity to focus on the implementation of the required model, and not on hours of searching for the necessary information.
Research objectives
Microservices architecture is increasingly used for the design and implementation of application systems in both the cloud and on-premises infrastructures, large-scale applications and services. It is enough to study Habr for various practices related to the development of distributed and fault-tolerant systems to make sure of the widespread implementation of the microservice model.
. , a (Application Security Architect – , Security Engineer'a, , ) , ( , ). , . , .
:
- ?
- ?
- ?
, , (, OWASP Moscow Meetup).
:
- , ;
- ( ).
( , – , ) ( 1): (edge-level authorization), (service-level authorization), (external entity identity propagation), (service-to-service authentication). , .
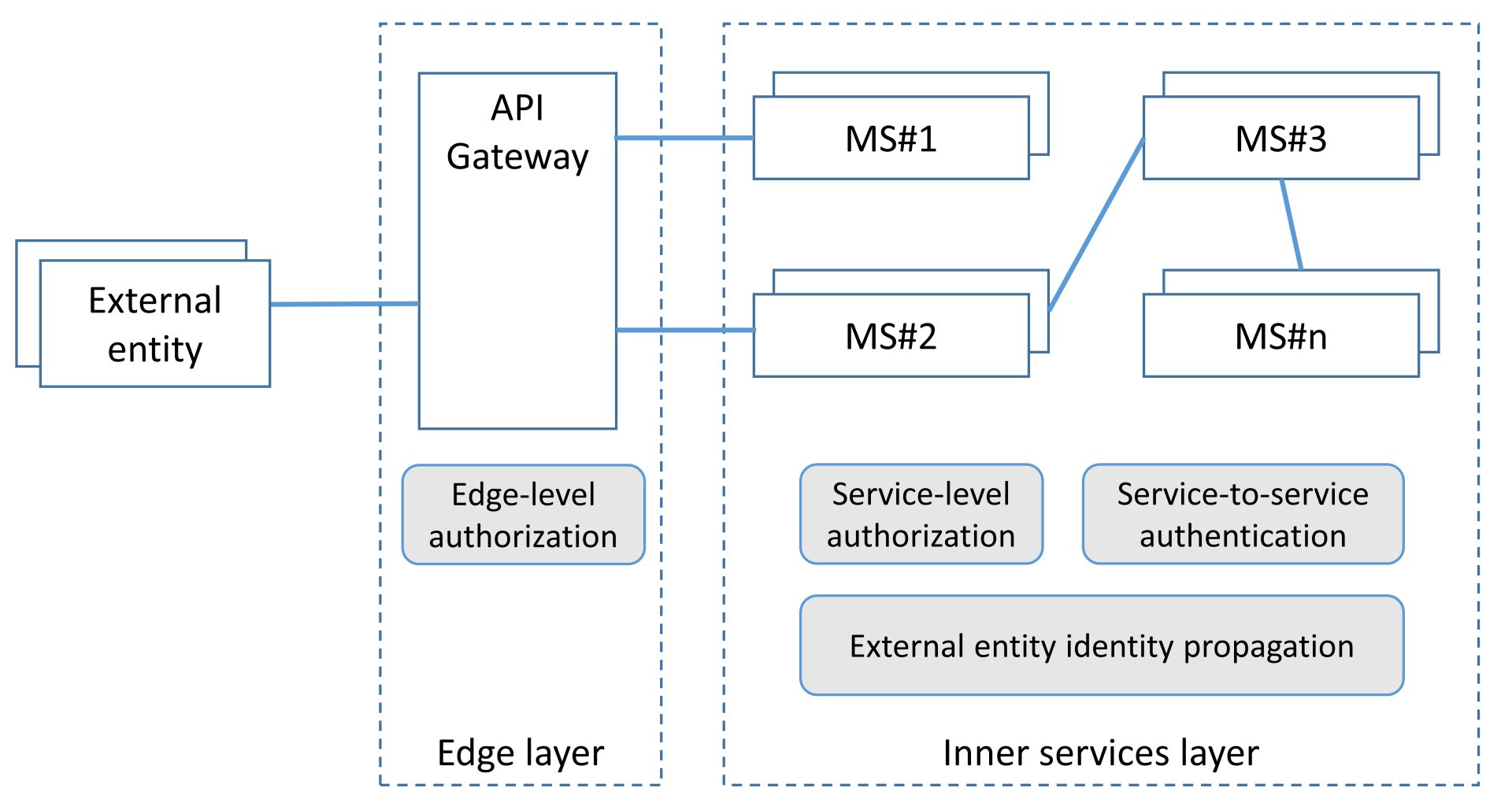
1.
.
(edge-level authorization)
( API). API , . NIST , , API.
:
- API- ( « »);
- API , " " (defense-in-depth);
- , API (operations), , , (, , - ).
: API . , (reference- (self-contained) , HTTP (, "Cookie" "Authorization"), mTLS.
( 2), NIST. :
- Policy Administration Point (PAP) , , ;
- Policy Decision Point (PDP) , ;
- Policy Enforcement Point (PEP) , ;
- Policy Information Point (PIP) , , , PDP .
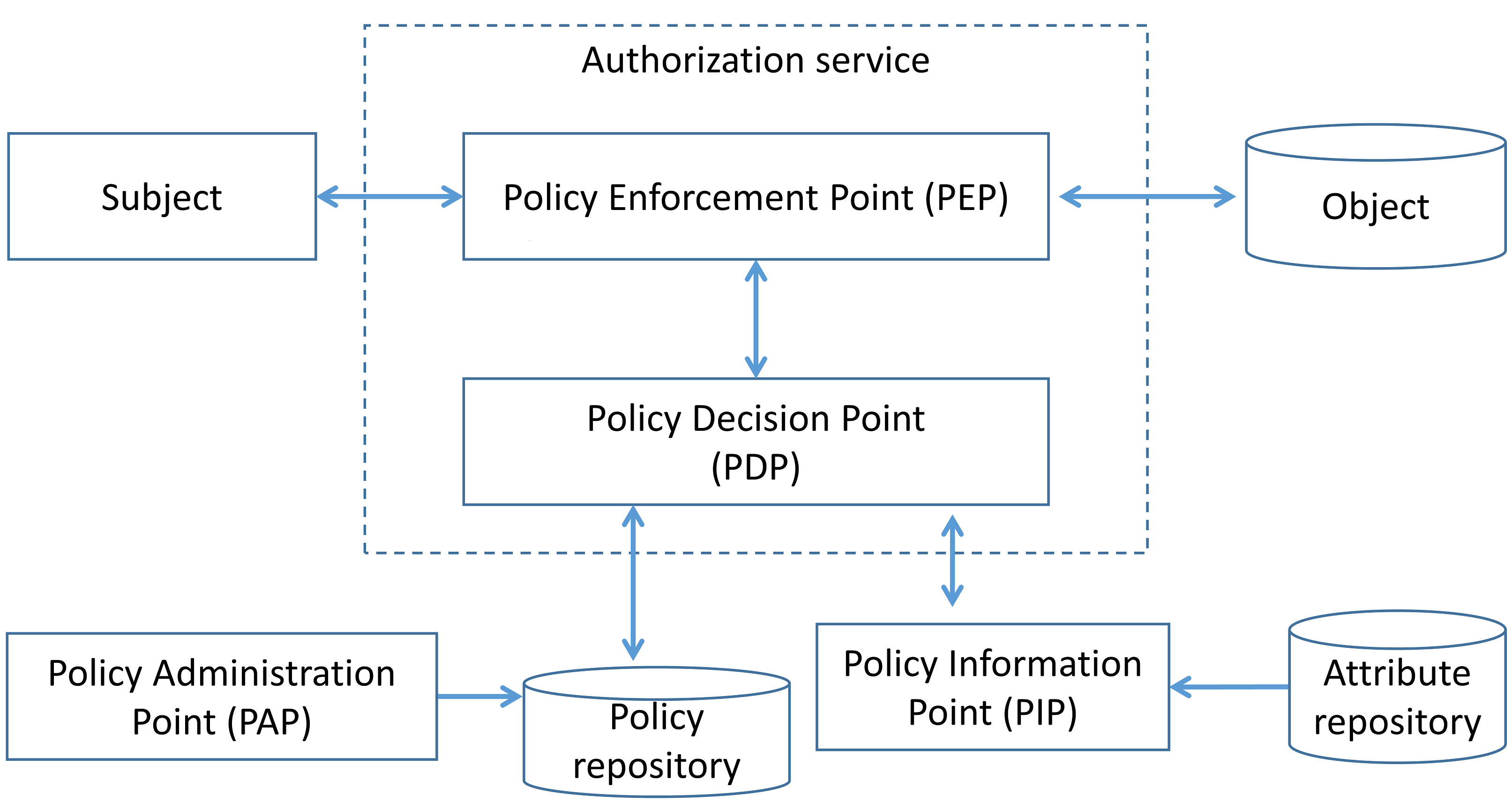
2.
. , , :
- ;
- ;
- .
PDP PEP (. 3). , , , ( 1). ( 2) (, ), ( 3) , , (enforce) ( 4).
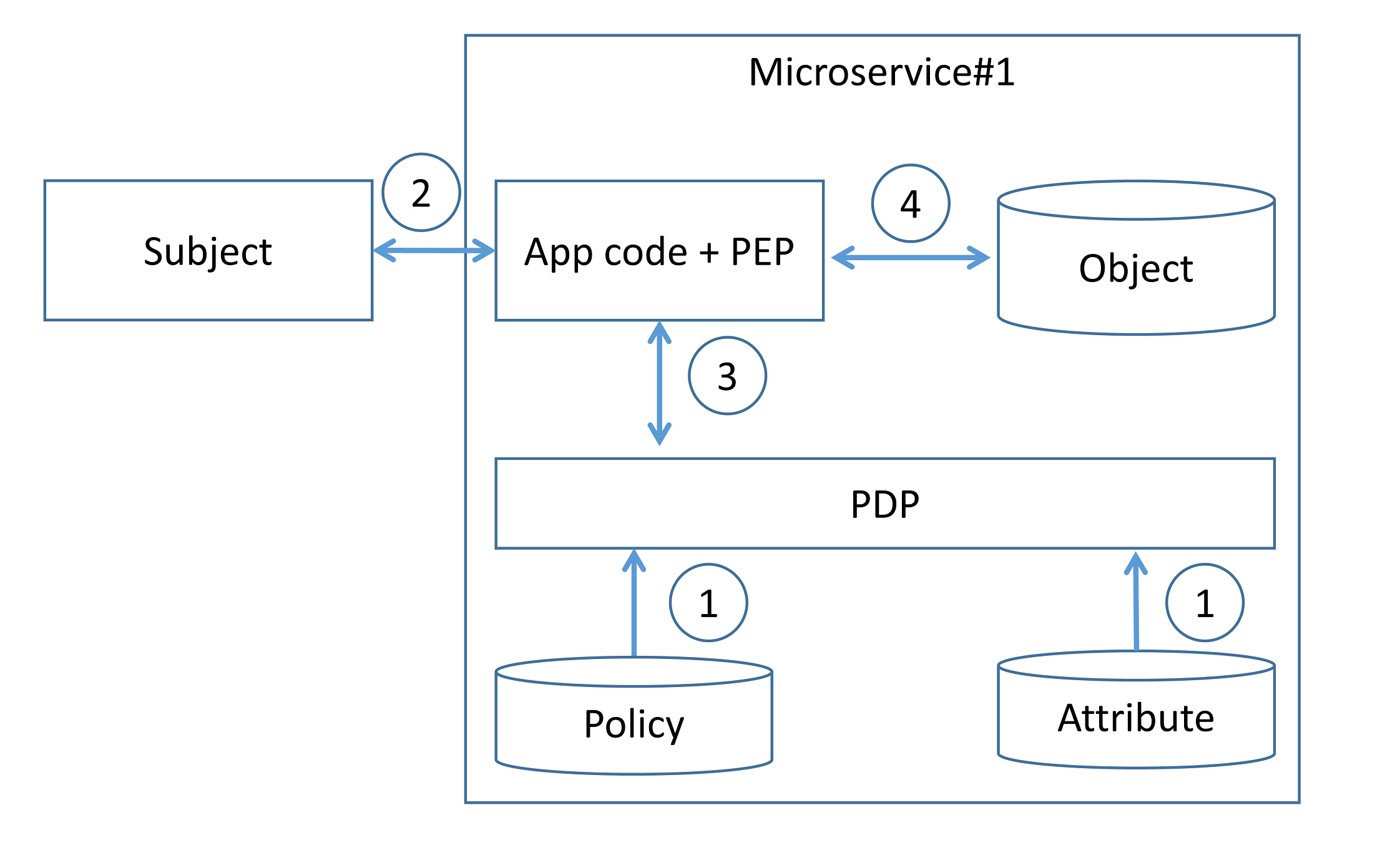
3.
. , , .
, :
- ( « , »);
- /, , ;
- - ( « , »);
- .
, , .
, ( 4). PAP ( 1) PDP , ( 2). ( 3), PDP , PDP , ( 4). PDP ( 5).
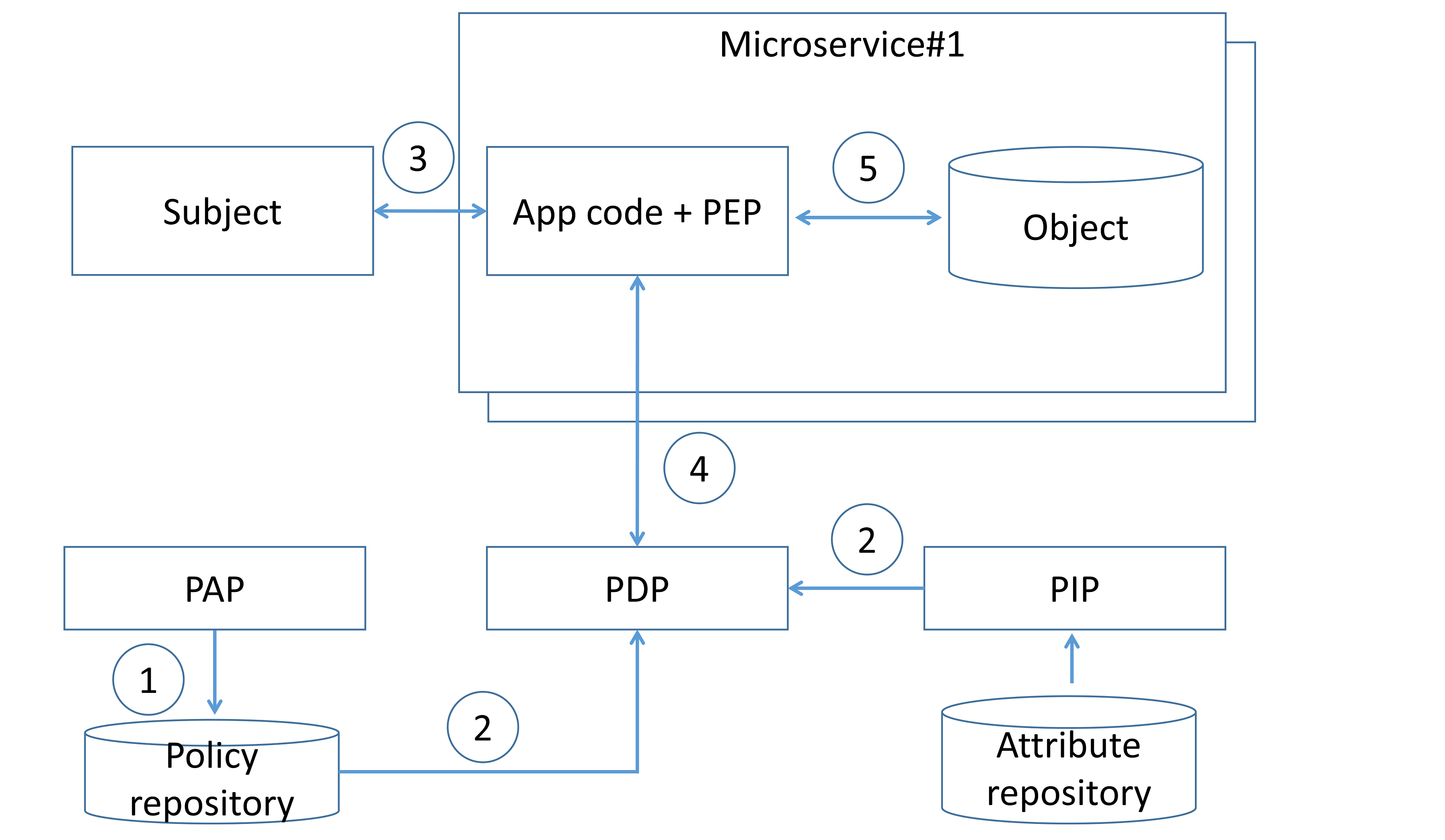
4. PDP
:
- , , ;
- , , , , ;
- , , , API, .
DevOps- . Extensible Access Control Markup Language (XACML) Next Generation Access Control (NGAC), . , XACML , , , DevOps-.
- PDP; .
, PDP - . (, API), " ".
, ( 5). PAP ( 1) PDP , ( 2). ( 3), PDP, PDP , ( 4). PDP ( 5).
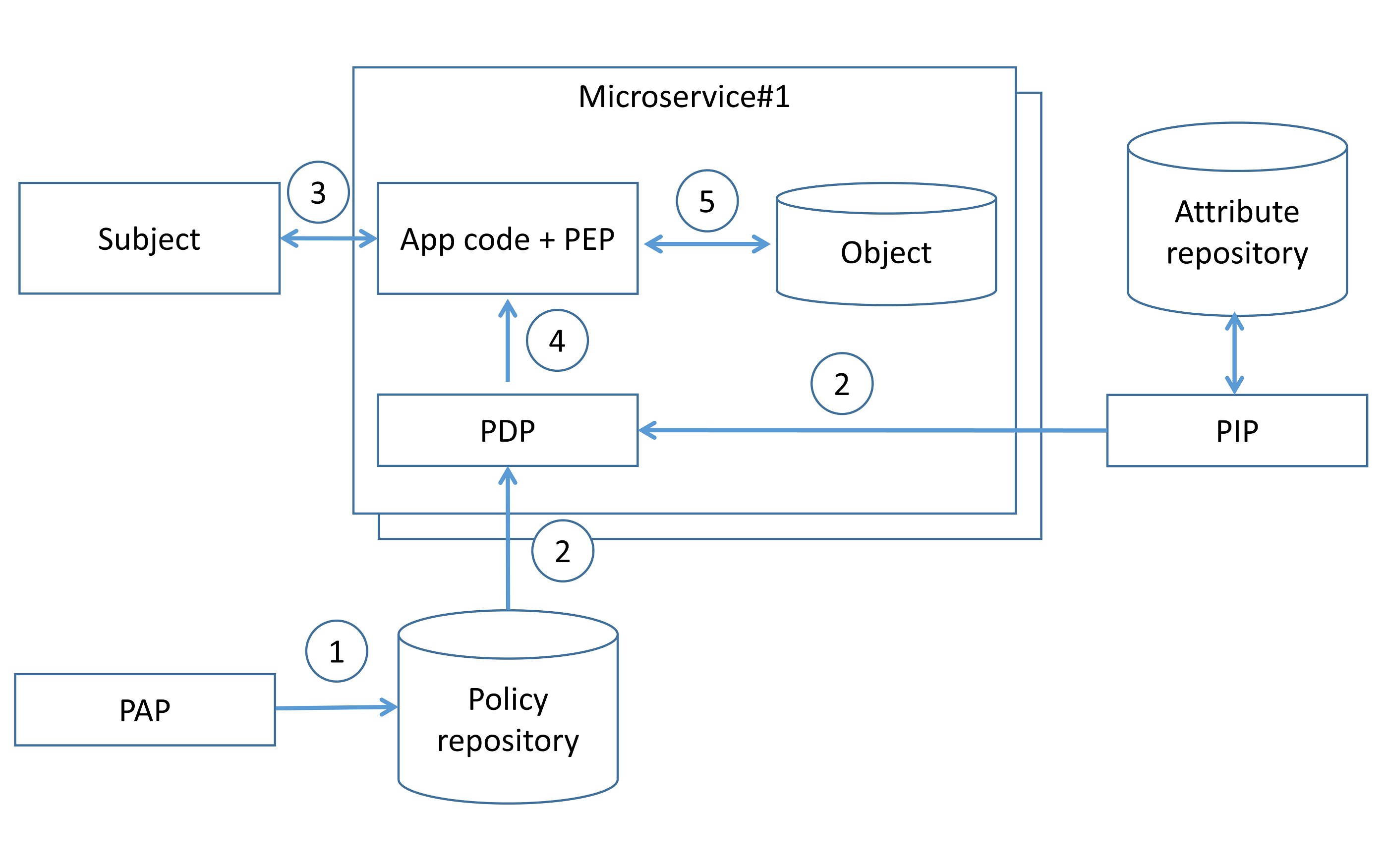
5 PDP
PDP «sidecar-». Sidecar , , , , .
PDP sidecar . PDP , . " " , , . .
“How Netflix Is Solving Authorization Across Their Cloud” " PDP" ( 6):
- — , ;
- , , ;
- ( Policy) , ( Aggregator), PDP;
- PDP () PEP.

6. PDP ()
, " PDP". , - PDP .
, :
- , , — ;
- (, ), " ";
- , — " ";
- , PAP (, PAP -);
- , , — " " .
:
- (mTLS);
- , , JSON Web Tokens.
mTLS , , . / , mTLS. mTLS . mTLS , .
. (microservice id) (scopes). , , , , , HTTP . TLS, .
(, Overcoming Security Challenges in Microservice Architectures) (, A Pragmatic Approach for Internal Security Partnerships), mTLS .
, .
, : « ?». , , , .
, , « ?» : «, . -». , «best practice» — pull requests OWASP.
, , (, ), .