Alexander Kolesnikov (virus analyst in an international company) invites you to the master class “Fundamentals of technologies necessary to understand vulnerabilities. OWASP TOP 10 classification ” , which will be held within the professional course. Alexander also shared an article for beginner bug hunters, where he reviews the TOP 10 Vulnerabilities of 2020 that were found by the HackerOne platform.

The idea is as follows - to prepare a laboratory bench to study the vulnerabilities in this top. You can read about how to launch and find an example application with a vulnerability here . The tasks will be solved before the exploitation of the vulnerability inherent in the application, the last step will be left to the readers.
TOP 10 vulnerabilities by HackerOne

— OWASP TOP 10. , OWASP TOP 10 2017 . . , :
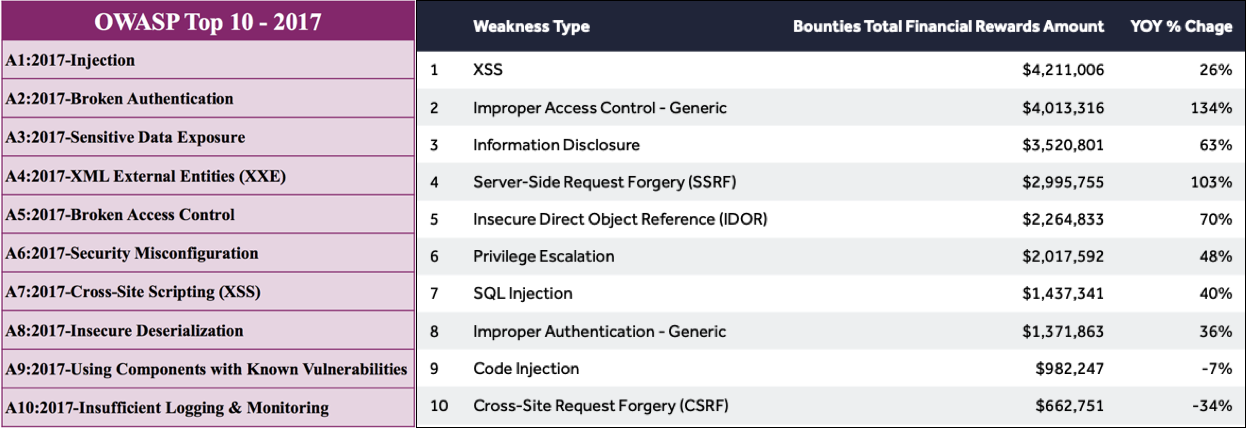
OWASP , HackerOne . HackerOne :
Injection
Broken Authentication
Sensitive Data Exposure
Security Misconfiguration
, 3 .
Injection
Injection — , . . , python .

, . HTTP BurpSuite Community, :

admin — «Login».
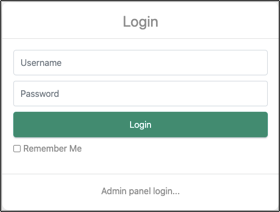
, . , . , . . «source.zip». , , /, .
, :
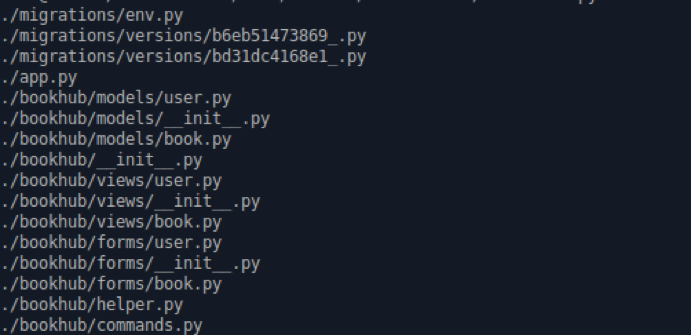
, - Flask. , 2 - debug release. debug - 5000. , :
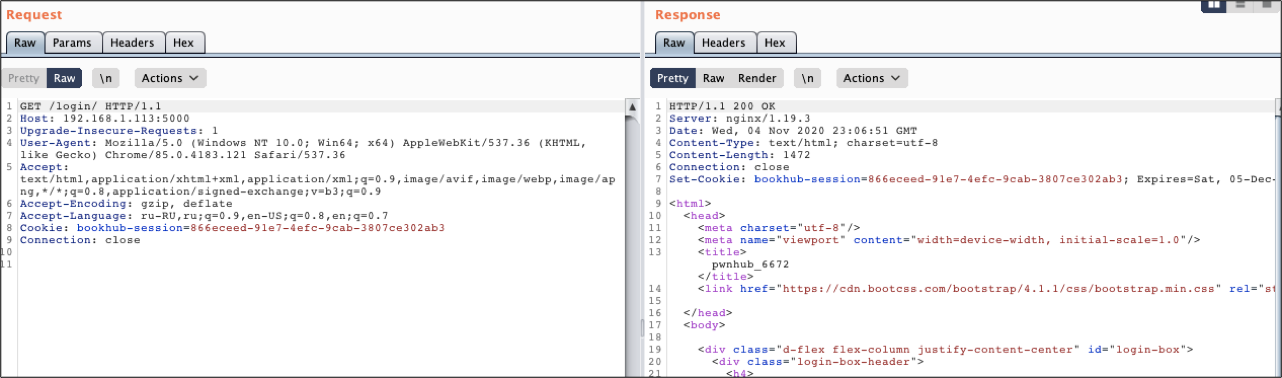
, . , . .
, :
.\views\user.py
, . , @login_required , - . , /admin/system/change_name/. , :

Lua Redis. , . Redis. python — pickle. .
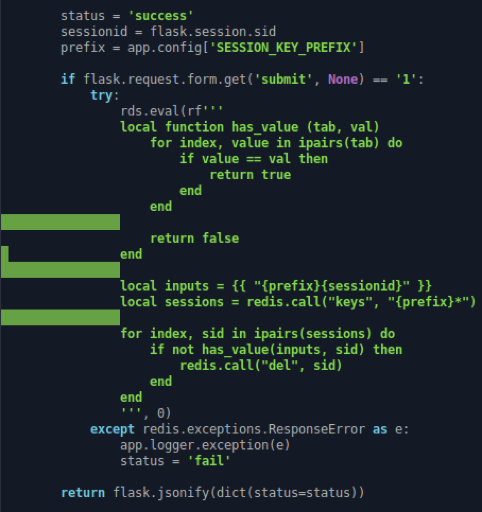
Security Misconfiguration
, , . Security misconfiguration — , ..
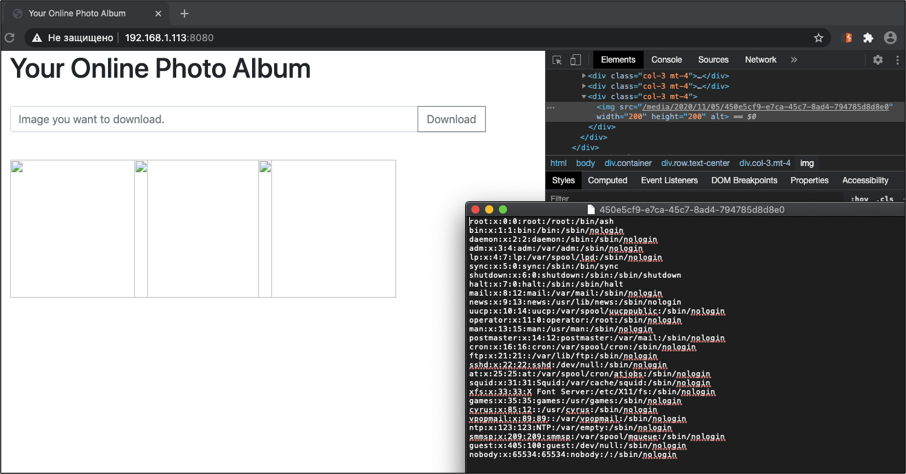
, , file:///etc/passwd. . :
, , . , . file:///proc/self/cmdline :
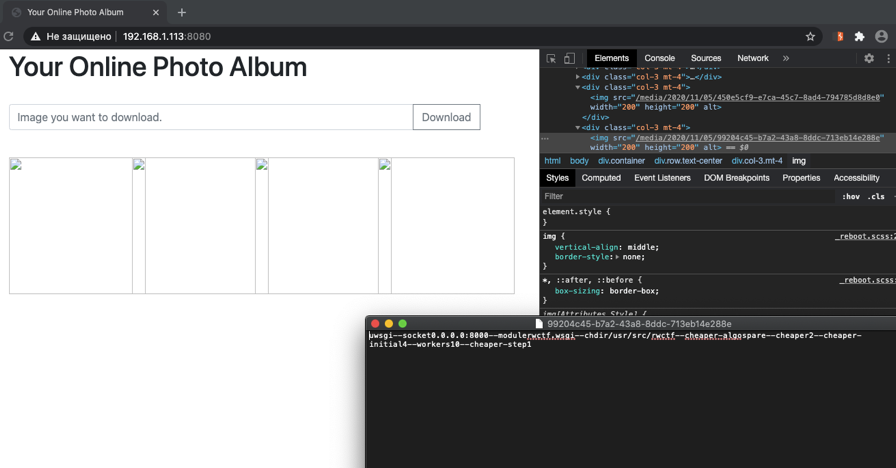
uwsgi- . 8000. - «/usr/src/rwctf». uwsgi, .
Broken Authentication, Sensitive Data Exposure
Broken Authentication - , . Sensitive Data Exposure - , . , ..
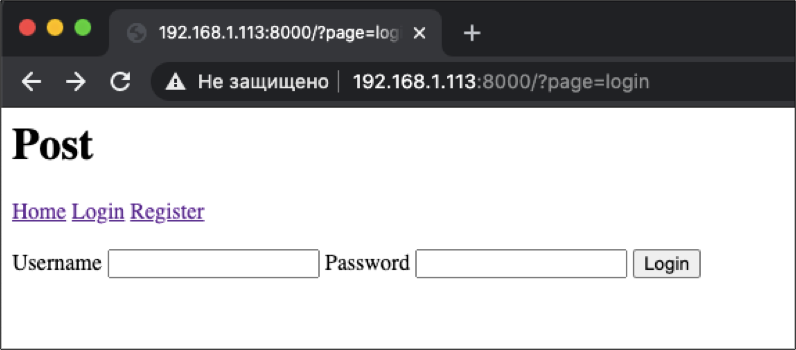
, . , . dirbuster, , . uploads, HTTP 403. c . : /uploads../:
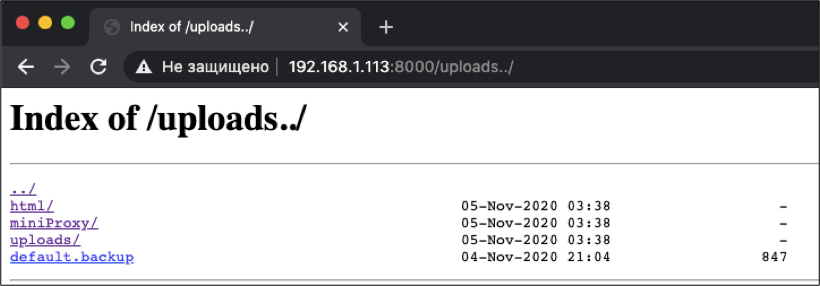
, . . . . .
, -. - .
Disclamer: .
. ? « -», - « ̆, ̆. OWASP TOP 10».