
Find out why your state needs cybersecurity training and how to arrange it without production downtime. Let's focus on the top six solutions for corporate safety training, compare their features and prices based on the ROI4CIO analytic table .
Can you imagine what the consequences would be if the personal and banking information of each of your employees were leaked? 4,000 employees at Scotty's Brewhouse, Indianapolis, USA, definitely can. In 2017, their entire staff fell victim to an email phishing scam: W-2 tax forms from across the company were sent to an impostor posing as a CEO.
Probably the loudest phishing attack ever was 110 million Target credit card records and customer credentials were stolen in 2013. The culprit was the compromised account of one subcontractor.
Another example of cybercrime is the Russian site tender-rosneft.ru, created in March 2017. I copied the design and content of the official resource, tender.rosneft.ru, there they posted information about the tenders. Thus, all careless people wishing to participate in the competition, once on the fake site, saw the contact details and payment details of the attackers. These are more sophisticated schemes - a potential client, having visited a fraudulent website, contacts a fictitious sales department, and the fraudsters issue a prepaid contract to the buyer. It is clear that customers do not receive any goods.
Commercial offers are often sent from a fictitious email address copying real organizations - this is how fraudsters sent requests on behalf of Rosagrotrade. By registering a fake domain name similar to the name of the company, criminals also get a mailbox with the same domain name from which the fraudulent mail is sent.
This type of fraud is common all over the world. In March 2019, 48-year-old Evaldas Rimasauskas was arrested in Lithuania, who stole $ 100 million from two American IT companies. Rimasauskas created a fictitious clone company of an Asian computer equipment manufacturer. On behalf of a company representative, he, having forged emails, forms, contacted the American clients of this company and convinced him to conclude contracts with him and transfer $ 100 million to the accounts of his company. Rimasauskas withdrew money through banks in six different countries, including Latvia, Cyprus, Slovakia, Lithuania, Hungary and Hong Kong.
Such a criminal scheme is known as "Nigerian letters" - surely many of you have remembered why: fifteen years ago, our e-mails were simply filled with heartbreaking messages from kings and presidents of different parts of Africa. By the way, before the spread of the Internet, such letters were sent by regular mail.
Sometimes classic Nigerian letters take on a rather interesting content. For example, in 2016, the British website Anorak reported that their editors received an email from a certain Dr. Bakare Tunde, a space project manager at the Nigerian National Space Research Agency. Dr. Tunde claimed that his cousin, Air Force Major Abaka Tunde, had been on the old Soviet space station for over 25 years. But for just $ 3 million, the managers of the Roscosmos corporation agreed to organize a flight of a manned spacecraft and return the Nigerian cosmonaut to Earth. The recipient of such a letter was required to “just” provide the details of his bank account so that Nigerian specialists could transfer the required amount to their Russian colleagues.As a reward, Dr. Tunde promised to pay $ 600,000.

All jokes aside, your company, and virtually every company in the world, can be vulnerable to malware, ransomware, spam, hacker attacks, and social engineering. Which can lead to either trouble, or a complete loss of reputation and ruin.
Why train cybersecurity staff?
The argument for cybersecurity training for employees is simple: If employees don't know how to recognize a security threat, how can they be expected to avoid, report, or eliminate it? They cannot. This is short. You can also look at convincing statistics.
For example, a 2019 cyber security study found that email security and employee training were cited as top challenges faced by cyber security professionals. This is confirmed by the fact that over 30% of employees surveyed by Wombat Security Technologies did not even know what phishing or malware was. In the United States, Business Email Compromise (BEC) results in annual losses of over $ 3 billion.
That being said, the affected companies almost always have firewalls and security software. This alone is not enough. Workers, not technology, are the most vulnerable to attack.
This does not mean at all that employees who fall into the trap are irresponsible. They make common human mistakes - trust fake identities, lure into bait, and are vulnerable to other tactics used by criminals to gain access to company information. But this happens if they are not prepared for this, did not participate in trainings and training programs on cybersecurity.
To protect themselves and the company from cyberattacks, employees need to receive training. By familiarizing them with security threats and the procedure for detecting a threat, you strengthen the most vulnerable links in your business chain.
Why is cybersecurity awareness so important?
In short, 90-95% of cybersecurity breaches are caused by human error. In addition, only 38% of international organizations say they are ready to deal with sophisticated cyber attacks. And another 54% of companies say they have experienced one or more attacks in the past 12 months, and this number is growing every month.
Today, the favorite tactic of cybercriminals is social engineering - psychological manipulation of victims in order to convince them to voluntarily or unknowingly surrender private data. Another, already announced earlier, is phishing - 95% of cyber attacks are the result of phishing scams, so learning the basics of phishing is essential.
Along with these two types of virtual fraud, malware also poses an ongoing threat - this involves downloading applications or programs designed to hack devices or provide network access to hackers.
Changing work patterns and the large-scale interference of the Internet in our lives necessitate training in cybersecurity skills for employees.
Remote work
In 2020, due to the introduction of quarantine to avoid the COVID-19 pandemic, teleworking has become a new reality for many. Work from home has become so prevalent that organizations are setting up separate teleworking policies. But even before the pandemic, 30 million people in the United States worked from home at least once a week.
Cloud-based remote work has improved the comfort level, but at the same time increased the risk of intrusions in the organization. Employees are responsible for the use of any personal endpoint devices and must restrict the use of office equipment to corporate purposes. Cybersecurity training teaches remote workers how to use devices when they are outside the enterprise infrastructure.
Internet of Things (IoT)
Employees connect personal devices to company networks or even use them for official work. Connecting personal devices to other machines and networks exacerbates vulnerabilities. The largest DDoS attack ever launched against a service provider using an IoT botnet, MIRAI.
Mobile devices pose a major threat to an organization's internal IT security, as many are not adequately protected. IoT attacks can be dealt with by managing and possibly minimizing the practice of “Bring Your Own Device” (BYOD) to the workplace, and ensuring that employee security policies are strictly enforced.
Strengthening government regulations
Cybersecurity education and training is no longer a personal choice. In many government regulations that emphasize the safe use of computers and networks, the employee awareness program has become critical. Government agencies and legislators are stressing the importance of businesses protecting their IT assets and digital information.
Who among the employees should improve their skills in cybersecurity?
Your employees are the first and foremost line of defense against online crime. Any employee with access to a work computer or mobile device must complete cybersecurity training. After all, almost anyone can become a target - personal phones can store data that can be used to access corporate networks; or, if an employee is the victim of identity theft, this unique information can be used to create false profiles that link to your brand, allowing for fraudulent activity.
What topics should be included in the training?
You are aware of why cybersecurity training for employees is critical. Now it would be good to understand how to implement this training. Let's start with the most important topics to be included in the curriculum.
For employees to be able to detect and prevent violations, they need a basic knowledge of the different forms of threat manifestation. For the most part, this includes spam, phishing, malware and ransomware, social engineering.
Spam detection materials should explain that spam occurs not only in e-mail, but also in messages and invitations on social networks. For example, a LinkedIn "invite" might contain a virus.
Phishing stories should be accompanied by examples of real phishing scams to help employees understand what a fake email looks like, who it might come from, and what information it might ask for.
Training should include tips to ensure that no malware or ransomware is being downloaded.
And, of course, social engineering should be a must. Social engineers disguise themselves as fake but trusted online identities and lure out the information they need.
The importance of passwords
Nowadays, passwords are needed everywhere - to unlock their devices, to sign in to accounts, and for every work-related application. Conceived as a security tool, this tactic has resulted in many people setting common, repeating passwords that are easy to remember and thus easy to guess. Online cybersecurity training should help you understand how important passwords are, and tell you about reliable programs that can generate and store passwords.
Email, Web and Social Media Policy
Employee email and social media habits can expose a company to malware that attacks corporate apps and social accounts, steals information and money. Therefore, it is very important that trainings include policies and guidelines on the use of email, the Internet and social media.
Company data protection
Each company has its own data protection policy, but do not assume that all of your employees are aware of this policy or that they understand it. Information security training for new employees should explain the statutory and legal obligations of data protection. Do not forget about regular refresher courses so that all employees remember the rules and know when they change.
How to identify and report cybersecurity threats
Employees are your eyes and ears. Every device they use, the email they receive and open, may contain clues about a lurking virus, phishing scam, or password cracking. But to truly mobilize them against attacks, training should help employees learn about seemingly unexplained errors, spam, and antivirus alerts. And be sure to educate them on who and how to report suspicious activity.
Way of teaching
Better not to settle for any ready-made training modules or basic web courses. It makes more sense to invest in professional cybersecurity experts who will work directly with your organization. This tailored training enables you to develop a complete virtual security strategy tailored to your unique corporate structure, data privacy and employee needs.
The aim of such training is always to change habits and behavior regarding safety, to create a sense of shared responsibility. It is not hard to understand that a one-time knowledge of the above topics is not enough to achieve this goal. Cybersecurity training should be done frequently, providing opportunities to practice safe online behavior in between sessions.
Raising awareness of online security threats should start from day one for new hires. It helps to include data protection policies and rules, Internet usage rules in the employee manual.
As the first line of attack and the first line of defense, employees need support. Don't get tired of reminding them - make them feel like superheroes. During your training, incorporate elements of gamification by encouraging and rewarding colleagues for their learning achievements.
And when a threat is identified before harm occurs, notify everyone in the company, showing how their training has helped the enterprise.
Now let's move on to looking at cutting-edge software solutions for training cybersecurity teams. Introducing the 6 Best Solutions from the ROI4CIO Analytical Grid... The product description is accompanied by a short list of characteristics by which the solutions are compared with each other. These are: phishing simulation templates, adaptive campaigns (smart scheduling), department / group level metrics and indexing, performance dashboard, risk-based campaigns, automatic audience targeting, cost per user per year.
Cofense PhishMe
Cofense PhishMe educates users about real phishing tactics through extensive research, threat intelligence, and advanced phishing protection resources.

Cofense offers a range of cloud-based solutions to protect businesses from cyber attacks through extortion, business email compromise and phishing.
PhishMe is a security education solution, one of the most popular platforms of its kind. It is an employee training and phishing simulation tool that aims to improve an organization's resilience to social engineering attacks.
Cofense PhishMe simulates active phishing threats to generate informed user behavior. This is the opposite of fish testing, which assesses vulnerability but does not change the behavior itself. The platform offers enterprises realistic simulations that are fine-tuned for specific types of social engineering attacks with varying difficulty levels. Along with training, Cofense additionally provides anti-phishing protection for the email network.
Cofense Playbooks allow you to customize a complete 12 month program including simulation scenarios, multimedia, and educational content. With Smart Suggest, the solution uses advanced algorithms to tailor scenarios based on current active threats, industry relevance, and your program.
Cofense checks each localized piece of content in the simulator to make sure it meets the needs of the audience - content is provided in 36 languages, including Russian.
The frequency of clicks on malicious content and suspicious activity are only part of the story. More important are employee responsiveness and resiliency metrics. Therefore, popular among Cofense PhishMe users is Cofense Reporter, a built-in one-click security incident response button. It turns employees into active advocates.
Suitable for: Medium to large organizations, corporate clients looking for powerful cybersecurity training along with technical phishing protection.
Interface
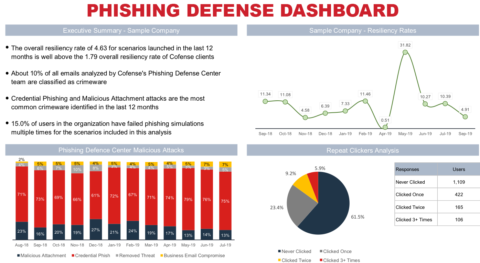
Product Feedback:
“ , — . , . , Cofense — , .”
, EMEA
Features
Phishing Simulation Patterns: Yes
Responsive Campaigns (Smart Scheduling): Yes
Department / Group Level Metrics & Indexing: N / A
Productivity Dashboard: Yes
Automatic Audience Targeting: N / A
Risk Based Campaigns: N / A
Price Per User per year: $ 12-25
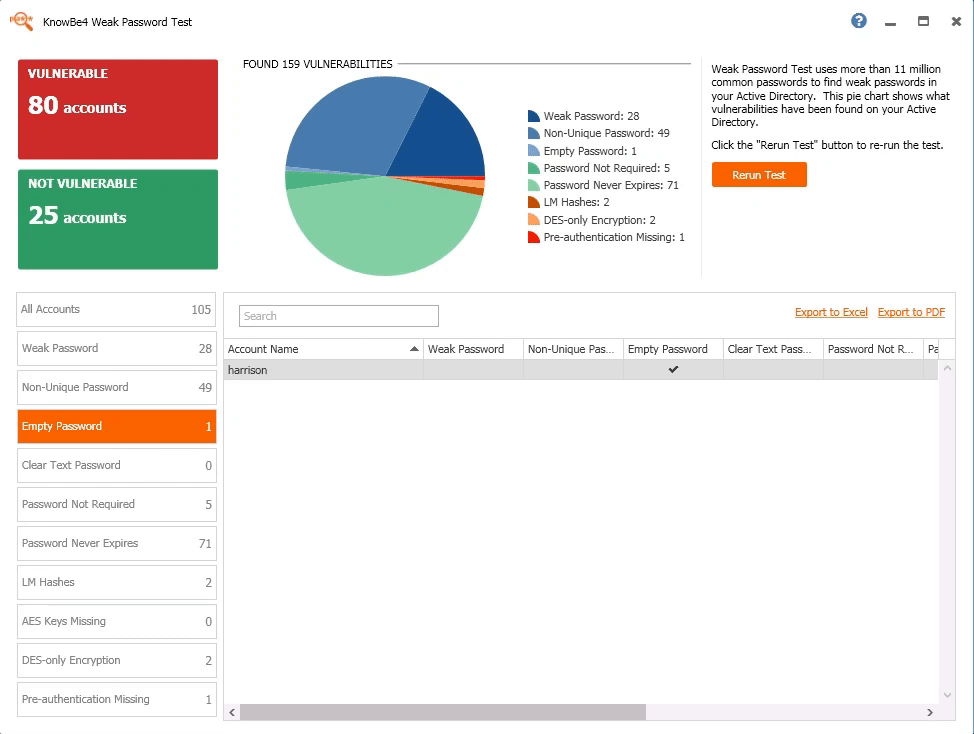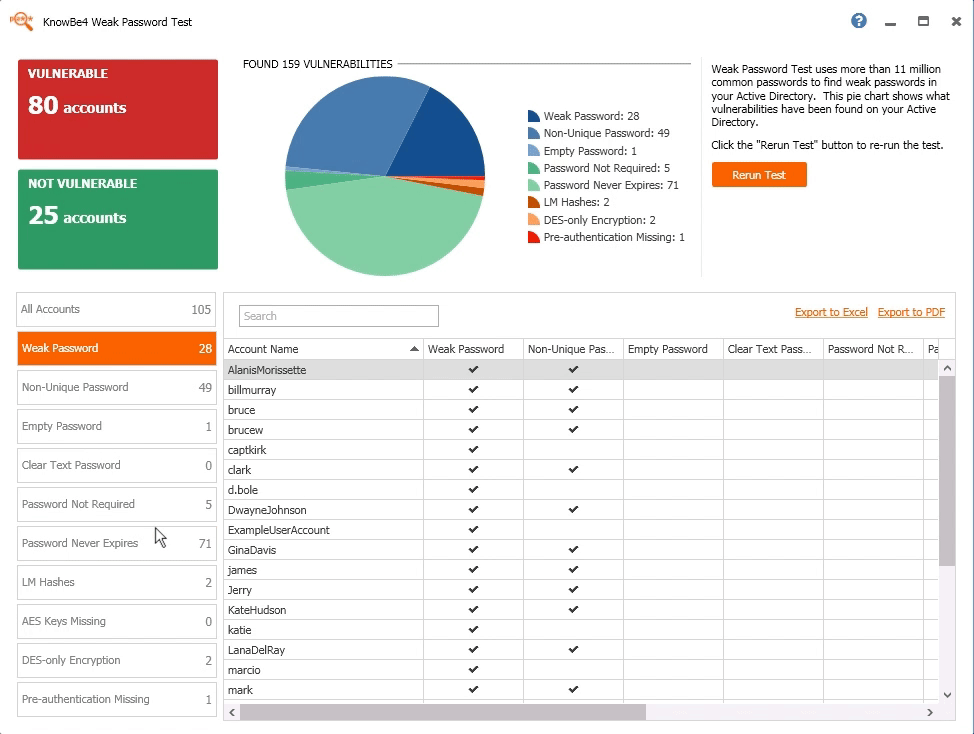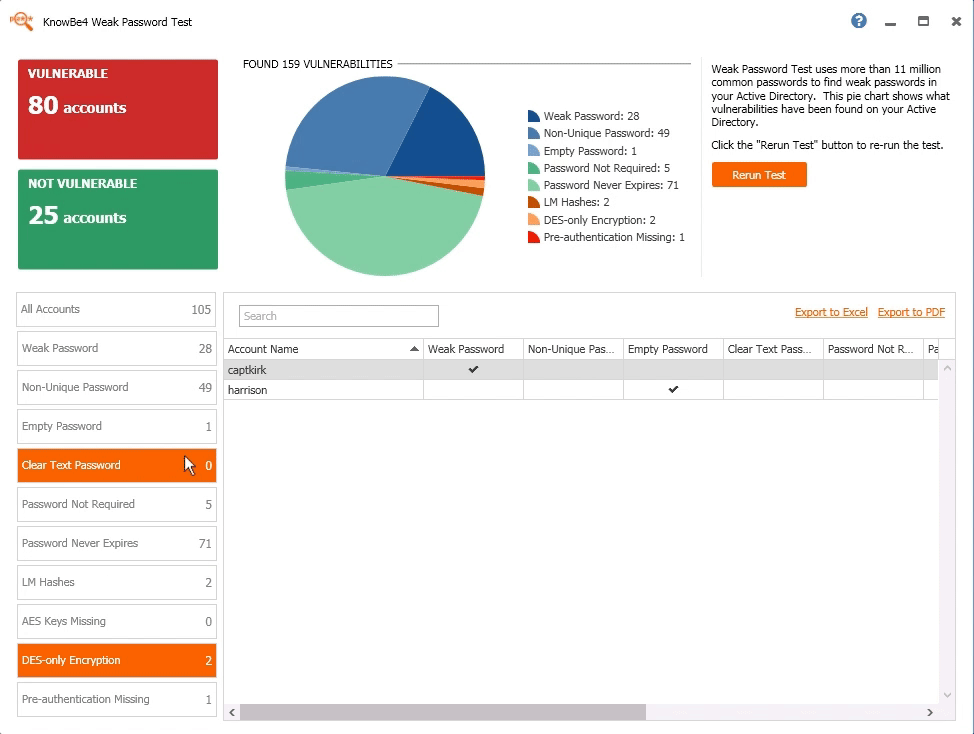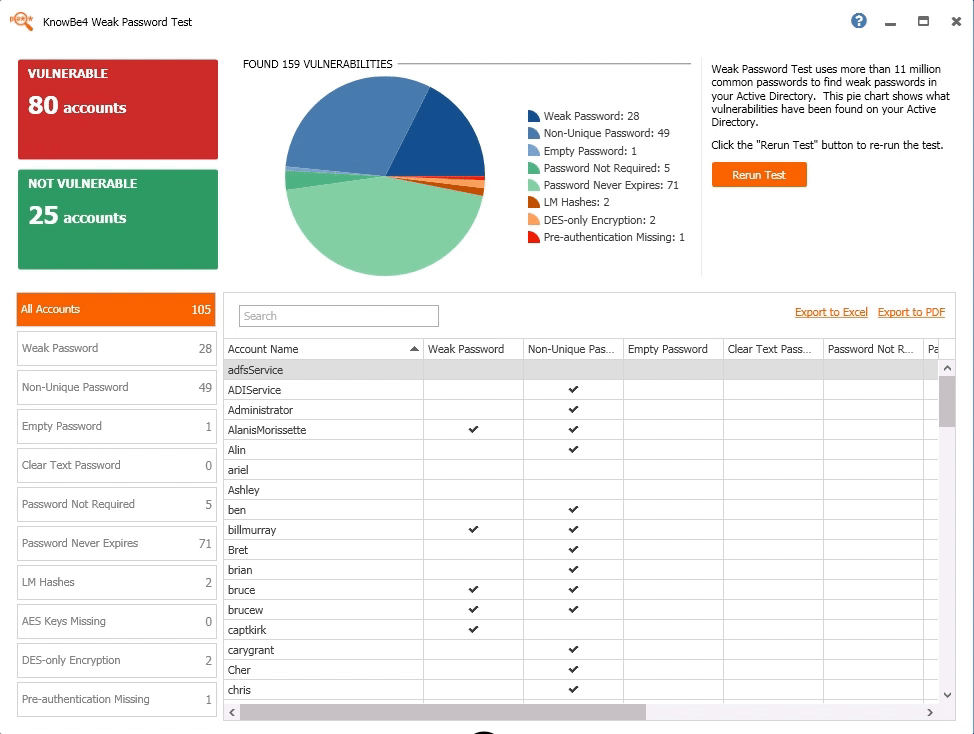
Knowbe4 Enterprise Security Awareness Training
KnowBe4 provides a comprehensive learning approach that includes basic mock attack testing, interactive training, and ongoing simulations of various forms of attack.

KnowBe4 has been a leader in Computer-Based Training (CBT) in Gartner's Magic Quadrant for years (a key IT market research company that publishes assessment reports using two linear progressive expert scales - “fullness of vision” and “ability to implement " ).
Before starting the training, KnowBe4 provides basic testing to assess the number of users in your company who are vulnerable to phishing, vishing (attacks via telephone communication, for example, defrauding confidential information from a payment card holder under various pretexts), smishing (phishing via SMS messages, for example, informing about a non-existent prize with a request to visit the site).
The company offers the world's largest library of security education materials, including interactive modules, videos, games and newsletters.
KnowBe4 platform integrates all functions in one graphical interface. Training campaigns start and simulate attacks in minutes, while teams are trained through fully automated phishing, vishing and smishing attacks, which include thousands of templates. These templates are fully customizable, with 4000+ highly realistic phishing emails to choose from, spread out over time.
During trainings KnowBe4 sends reports on the strengths and weaknesses of the enterprise. Both general and detailed statistics and graphs are available and can be easily included in management reports. They provide insight into the security performance of the entire organization.
KnowBe4 gives you three-level access to ready-made trainings - I, II and III. This includes modules, micromodules, videos, posters and games. The SaaS training platform is available with a subscription consisting of Silver, Gold, Platinum and Diamond tiers. What you get access to and how many employees you can train depends on the level.
Best For: Businesses that are fighting to end phishing attacks and want to educate their employees about cyber security. Product Feedback
Interface
:
“ KnowBe4. , . , KnowBe4 . — , , . , , .”
Azamat Uzhangaliyev, Group IT Network Engineer, TXT e-solutions
Features
Phishing Simulation Patterns: Yes
Adaptive Campaigns (Smart Scheduling): N / A
Department / Group Level Metrics and Indexing: Yes
Productivity Dashboard: Yes
Automatic Audience Targeting
Risk-Based Campaigns: Yes
Price Per User Per Year: $ 8-29.5
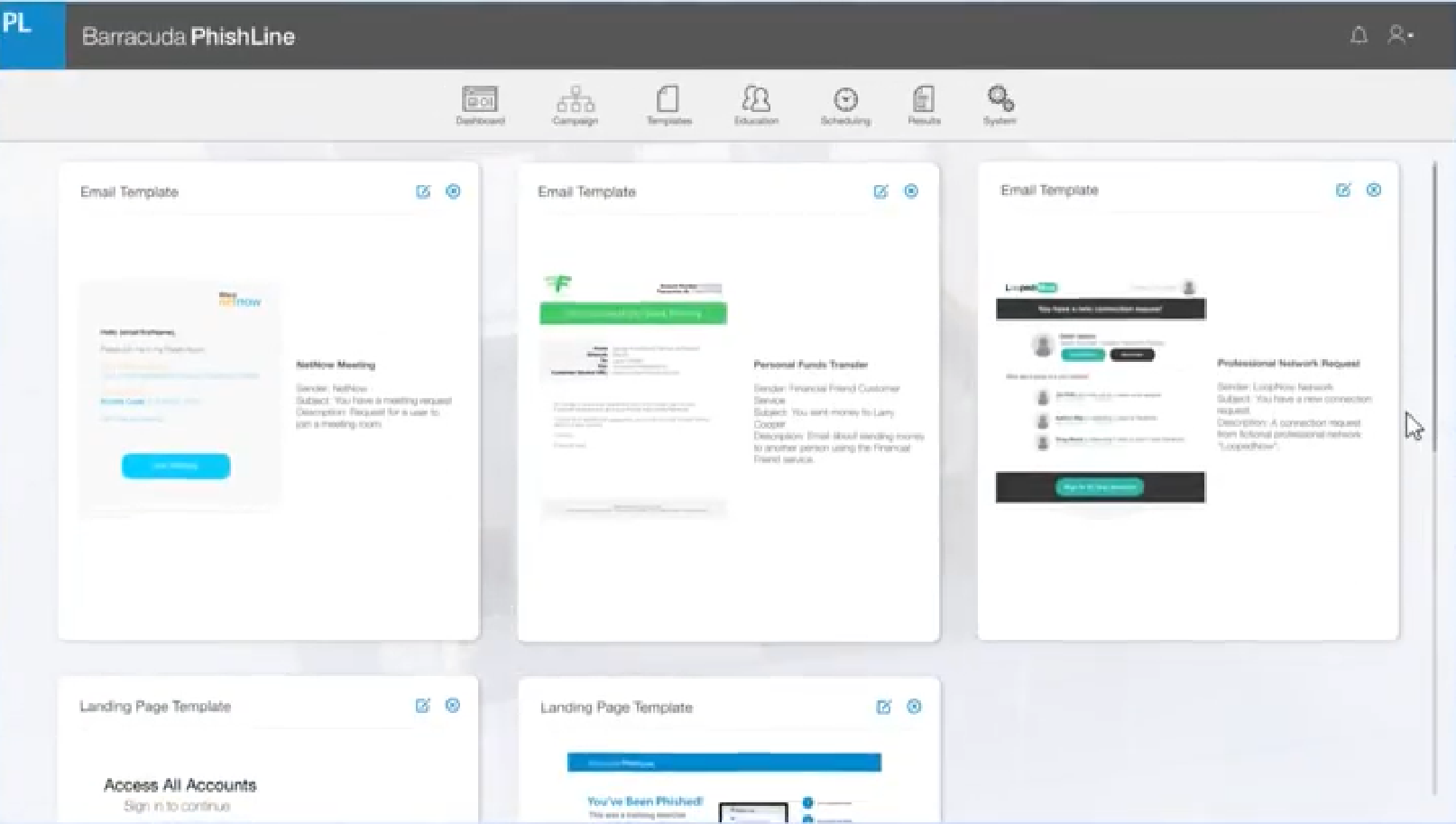
Barracuda phishline
A cloud-based learning tool that provides cybersecurity knowledge to defend against phishing and social engineering threats.

Barracuda is a global cybersecurity solutions provider offering a range of cloud-based products to protect businesses from cybersecurity threats.
Using PhishLine, Barracuda provides cybersecurity training to a wide range of corporate clients. PhishLine offers courses that include media content and phishing simulations. PhishLine pays great attention to reporting and analytics so that managers understand how employees perceive training.
PhishLine provides patented attack simulation with high variability - phishing, vishing, smishing and found physical media (USB / SD cards). There is no need to choose - you can use several templates at once.
With PhishLine, you train employees to recognize threats from different sources. PhishLine modeling and tutorials are easy to use and fully customizable. The solution provides a wide range of materials: choose from hundreds of easy-to-use simulation templates, landing pages, risk assessment surveys and training videos. The content can be used alone or integrated into mock phishing and social engineering campaigns.
While Barracuda's content lacks interactivity in places, the product stands out for its granular and customizable reporting that provides a practical understanding of security within an organization. The report includes vulnerability profiling, which collects information from over 16,000 data points. The platform offers an Outlook plugin that allows users to report suspicious phishing emails to IT departments.
Best for: Corporate clients who need full security awareness of their organization, as well as detailed reporting and analytics for submission to regulatory reviewers. Product Feedback
Interface
:
“ Phishline , . . Phishline . , , . — , .”
Features
Phishing Simulation Patterns: Yes
Responsive Campaigns (Smart Scheduling): N / A
Department / Group Level Metrics and Indexing: Yes
Productivity Dashboard: Yes
Automatic Audience Targeting: Yes
Risk Based Campaigns: Yes
Price Per User per Year: From $ 24
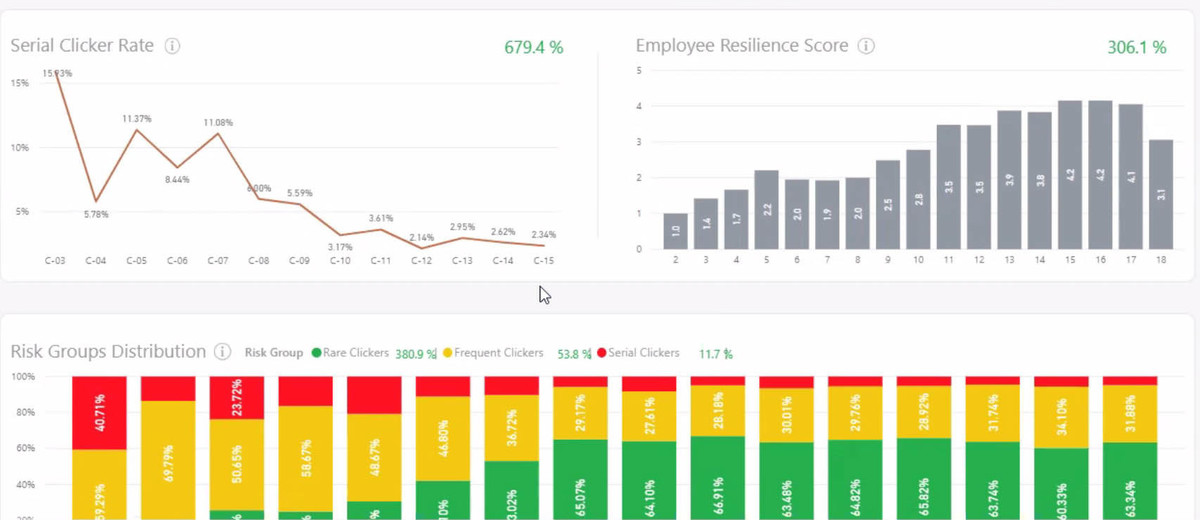
Cybeready BLAST
Cybeready guarantees corporate cybersecurity through machine learning-based training. This adaptive technology educates users about the dangers of phishing and other types of attacks without changing the way they work.

CybeReady offers training based on scientific evidence, artificial intelligence and machine learning. Their platform automates cybersecurity training, allowing employees to receive year-round training.
According to CybeReady, the use of big data and machine learning in the solution guarantees changes in employee behavior, not only in the short term, but also in the long term. The company claims that this training approach increases employee resilience to attacks by an average of five times.
Training is conducted only as needed and never takes more than two minutes. The training campaigns themselves are also set up within minutes, so administration of the CybeReady platform is kept to a minimum.
CybeReady is delivered in the cloud and delivered to organizations as a service. Setting up the platform only requires providing access to a custom employee email directory.
Initially, the program sorts users into logical groups based on location or work function. However, after the first training sessions, where some users either accept or ignore attacks, the groups change. Someone goes into the group of those who do not "click" on malicious emails, while others can fall into the category of "serial clickers", being drawn into every imitation of a scam. Based on these classifications, CybeReady modifies the type and frequency of attacks it simulates.
At the end of a campaign, or during a campaign, administrators can log into the CybeReady cloud portal to view reports on how training is helping users. The reports consist of several pages and are filled with auxiliary graphs showing changes in dynamics over time. The documents are also broken down by factors - the type of work and the division of the company, so it is easy to determine where the current vulnerability is and target it in the campaign.
Suitable for: Organizations of all sizes and corporate clients looking for easy-to-implement, automated, and effective cybersecurity training. Product Feedback
Interface
:
“ , , , . , . , , , .”
Yaron Weiss, Payoneer’s VP Corporate Security and Global IT Operations
Features
Phishing Simulation Patterns: Yes
Responsive Campaigns (Smart Scheduling): Yes
Department / Group Level Metrics & Indexing: Yes
Productivity Dashboard: Yes
Automatic Audience Targeting: Yes
Risk Based Campaigns: Yes
Price per user per year: $ 5-25
Proofpoint Threatsim
ThreatSim provides anti-phishing testing services. A customizable solution for simulating phishing, USB and SMS attacks allows you to assess the vulnerability of the enterprise in a matter of minutes and highlight the necessary vectors for employee training.

Proofpoint provides effective cybersecurity and compliance solutions to protect email, web, cloud and social media.
The company's ThreatSim Attack Simulation Product is a security training program focused on anti-phishing. Several formats are offered - including static and animated landing pages, short videos, and interactive tasks. A selection of static landing pages is available in 17 languages, allowing employees around the world to view messages in their own language.
The results collected during the simulation are grouped into reports that identify your organization's vulnerability to modern attacks, allowing you to proactively protect your organization's data. ThreatSim provides extensive analytics and specific records of employee responses to various attack scenarios. You will know if employees were caught in the attack via a mobile phone, tablet or computer, what browser they were using and where they were during the attack.
ThreatSim can be used as a stand alone assessment tool or paired with interactive training modules. ThreatSim phishing tool supports over a thousand templates in over 35 languages. The variety of templates takes into account three key testing factors: inline links, identity requests, and attachment downloads (.pdf, .doc, .docx, .xlsx, and .html).
Administrators can customize the content of any template or create their own. This flexibility allows organizations to quickly and easily create timely and relevant phishing tests.
Best for: Businesses of all sizes that need to educate employees and mitigate risks through advanced phishing threat modeling and security training. Product Feedback
Interface
:
“The variety of templates that were used to simulate attacks and the realistic appearance of these templates were truly impressive. The ability to customize your own templates has also proven to be extremely useful in making phishing emails slightly more difficult to detect, allowing you to spoof internal accounts and make plausible phishing emails. "
Features
Phishing Simulation Patterns: Yes
Responsive Campaigns (Smart Scheduling): N / A
Department / Group Level Metrics & Indexing: N / A
Productivity Dashboard: Yes
Automatic Audience Targeting: N / A
Risk Based Campaigns: Yes
Price Per User per year: N / A
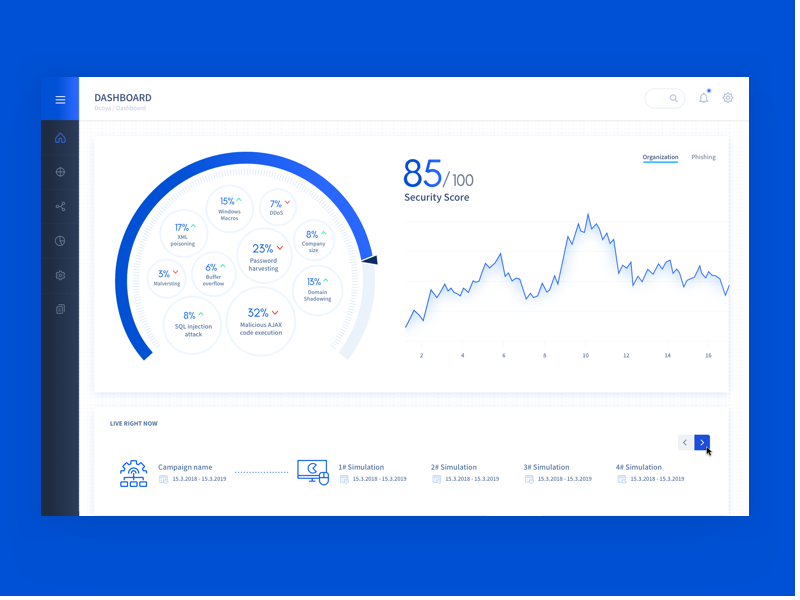
Dcoya Behave
Dcoya's learning solution takes into account employee diversity, behavioral psychology and marketing methodologies to practice and improve cybersecurity behavior.
The best defense is training:

Dcoya Behave's corporate cybersecurity training programs offer a personalized approach to cybersecurity training. Dcoya's solutions leverage machine learning algorithms to incorporate best practices in behavioral psychology and marketing into a fully automated learning program.
Dcoya Behave automates personal cybersecurity training, tailoring it for each employee individually. The solution simulates social engineering and phishing attacks, testing the savvy of your colleagues.
Dcoya Behave also automates employee segmentation, targeting phishing attacks against different departments, roles, or other groups in the company. The product tracks the start, finish, and results of simulations for individuals and teams, so administrators are always aware of progress towards cybersecurity and compliance goals.
Best for: Small and Medium Enterprises wishing to individually train their employees in cybersecurity.
Interface
Features
Phishing simulation templates: yes
Adaptive campaigns (smart scheduling): yes
Metrics and indexing at the department / group level: yes
Productivity dashboard: yes
Automatic audience targeting: yes
Risk-based campaigns: yes
Price per user per year: $ 5-25