
We will study digital risks, their types and figure out how to protect ourselves from them. Consider six globally recognized DRP (Digital Risk Protection) solutions, compare them in functionality and price, based on the ROI4CIO analytical table .
The necessity of a strong presence in the online world for the success and recognition of your brand has become a common truth. And this concerns not only artistic platforms, witty channel management of politicians and global corporations. Retail, advertising, and customer support are also shifting into the online space. The transition to the virtual world has become especially relevant with the introduction of quarantine in many countries in connection with the COVID-19 pandemic.
The efforts expended to increase the reach of the Internet audience and successful online campaigns are captivating with the results. But, unfortunately, the more successful and larger your online presence, the more dangerous it is to forget about its shadow side - digital risks. After all, online interaction with the audience attracts not only the desired attention - you become visible to all kinds of attackers: financially motivated cybercriminals, competitors trying to leak your secrets, hackers.
Understanding what threatens you, how to build digital protection and choose the best solution for collecting operational information and preventive actions against attacks will help protect your business from threats. Of course, the methods vary depending on the size and scale of the organization, but there are several fundamental concepts of digital risk protection that can guide the selection of collateral.
Types of digital risks
Digital Risk Protection is one aspect of a threat information management program. Consider the elements that make up the digital risk category.
Unauthorized Disclosure
Includes the theft or leakage of any confidential data — personal financial information of a retail customer or the source code of a technology company's own products.
Identifying Vulnerabilities
E-commerce platforms, criminal forums on the dark web or even on the open web are powerful sources of risk. A vulnerability identified by a group or individual who cannot influence it finds its way to someone who can. This includes the distribution of exploits in both targeted and non-targeted attacks.
Supply chain problems
Business partners and all vendors who interact directly with your organization do not necessarily follow the same security guidelines as you do.
Technology Risks
This broad category includes all of the risks that need to be considered when dealing with technology on which an organization depends. This includes:
Physical infrastructure : Countless industrial processes that are partially or fully automated by SCADA, DCS or PLC systems. Unfortunately, automation opens up networks for cyberattacks - an example of which is the STUXNET attack that disrupted an entire nation's nuclear program.
IT infrastructure: The most common source of digital risk, including all potential vulnerabilities in software and hardware. These risks are growing every day due to the connection to the Internet of Things.
Internet Public Presence : Points of contact with customers and community organizations - social media, email newsletters, or other marketing strategies - are potential sources of risk.
Risk from employees
Even the most secure and tamper-resistant lock can be easily opened if you have the key. With social engineering efforts, identity management and manipulation, and malicious insider attacks from disgruntled employees, even the most trusted cybersecurity program can be quickly undermined.
Ten use cases for digital risk protection
The threat landscape is constantly expanding, which means that cybersecurity teams are increasingly being forced to work to protect organizations. We've put together a dozen case studies to demonstrate the scope of risk protection services.
Phishing Detection
Phishing is an insidious problem, and cybercriminals love it because it is effective. DRP includes proactive measures that identify and stop attacks before they cause harm. By tracking various key phishing metrics - registered domains, changes in MX records and DNS reputation, the solution identifies malicious domains and quickly eliminates spoofed sites.
Vulnerability prioritization
Manually correlating threat intelligence with your organization's vulnerabilities is no longer realistic. Too many technologies used, too much data. DRP is an automated vulnerability collection that exploits data from anywhere. Then these arrays are structured in real time, allowing you to see what poses the greatest risk.
Darknet visibility
The attackers are smart and anonymous, but still visible. DRP monitors their activities across the Internet - how they scout targets, use suspicious tools, and collaborate with other hackers. An advanced DRP solution understands how cybercriminals think and how threats evolve, giving you the chance to be proactive. By the way, monitoring and tracking web activity on the darknet is a key part of how threats are typically detected and mitigated.
Brand protection
You've spent a lot of time and money building and building your brand. Alas, hackers also know how valuable it is. The DRP solution is designed to scan external sources for fraudulent uses of your brand. It monitors your domains, IP addresses, mobile apps and social media pages to identify intruders. And when suspicious activity is detected, it instantly sends alerts throughout your organization, to marketing, compliance, IT, and security.
Fraud detection
You have all sorts of perimeter defenses installed - firewalls, gateways, IDS / IPS, and malware detection systems, and you may even have taken steps to integrate and harden those systems. That's cool! The problem is that hackers bypass this protection anyway, using fraud instead. Therefore, the DRP solution should monitor attempts to create phishing sites or sell leaked credentials, bank account information of your customers and employees. Real-time instant alerts help prevent such actions before they happen, saving organizations millions in costs each year.
Identification of malicious mobile applications
Mobile devices and apps expand audience reach. But attackers may have already created rogue mobile apps that your marketing team most likely doesn't track or know. DRP should check various app stores, both legal and pirated, to detect suspicious apps and initiate their closure. This is possible if the solution has partnerships with app stores.
Protecting leadership
In the past, executives only needed physical safety. Alarms and security are installed in the offices for this purpose, sometimes bodyguards are assigned to the top management. Senior officials now face serious cybersecurity threats. So do investors, board members and advisors. The DRP program must scan online sources to find and stop attempts to tamper with or compromise their identity and data.
Automated Threat Mitigation
Given the magnitude of potential threats and the lack of expertise to mitigate them, automating the mitigation process is critical. The solution must turn data into intelligence, and intelligence into action: blocking and eliminating threats, resetting credentials, and creating security policies.
Monitoring Leaks and Confidential Data
Protecting customer data and intellectual property is critical. DRP searches for stolen credentials and confidential data, passwords and notifies about their detection. The best way to ensure DRP is acting according to up-to-date credential information is to integrate the solution with Active Directory and Microsoft Exchange. Thus, when a leak is detected, active credentials will be reset.
Third parties
As if protecting your own systems isn't hard enough, you also have to worry about external sources, which are also harder to control. These are the suppliers, partners and investors that are part of your digital footprint. Their cyber risk is yours too. Therefore, the DRP must assess the threats faced by third parties so that you can effectively manage your supply chain.
Why digital risk protection is an investment, not a cost
Digital Risk Protection is a proactive defensive strategy. It enables you to counter threats, avoid unnecessary costs, improve efficiency and recover losses. It is in these four areas that DRP offers ROI. Let's take a closer look.
ROI 1: Avoiding Risks
Like most other elements of a cybersecurity strategy, investments in a solution must be viewed in the context of the unwanted costs that a security breach can incur. But this is only one part of the benefit. One of the most valuable aspects of DRP is the visualization of an organization's own digital footprint - an essential element for protecting business and reputation.
ROI 2: Lower costs
DRP solutions automate many tasks related to the detection and monitoring of digital threats. Self-directed cyber defense on the ground only partially covers such tasks when compared to specially designed, constantly updated solutions. The best DRP services also cover Shadow IT (i.e. unauthorized domains, applications, or devices created or used without notifying the IT department) and Forgotten IT (e.g. old website landing pages and archived content), providing additional cost savings ...
ROI 3: Increased efficiency
The automation inherent in digital risk mitigation solutions identifies vulnerabilities faster and easier, increasing process efficiency. The identification and elimination of Shadow and Forgotten IT further optimizes the digital space of the enterprise, saving resources.
ROI 4: Revenue Generation
Successful cyberattacks, phishing emails, and fake sites for an organization have a direct negative impact on revenue, and of course, negatively impact reputation. Digital risk mitigation solutions help mitigate these risks as well, helping to quickly identify and remediate illegal or threatening activities.
Protection methods
Forrester identifies two main challenges for any organization seeking to reduce digital risk: first, identify what risks exist, and second, eliminate them. We agree with you - at first glance, the goals are obvious. But in reality, they assume a certain stance on security - more proactive than incident response. This proactive approach incorporates digital risk protection into a threat intelligence strategy.
The idea is not to build a wall around the city and stay away from anything unwanted, but to feel safe walking freely around the world where you know everything that surrounds you.
The Forrester report also identifies several critical qualities inherent in a DRP solution:
- . . -, , .
- , . , , - ; , ; .
- - . — , . — , .
Having considered all the advantages of implementing DRP and having familiarized ourselves with what to expect from the solution, let's move on to comparing the six leading products with each other. Let's take a brief look at the functionality, features, compare on the basis of the ROI4CIO analytical table by price and parameters: protection and verification of IP addresses, URLs, threats of the TTPs category, hash sums of files, domains, registry keys, card numbers, phone numbers, social networks; protection of mobile applications and brand; finding data leaks; data enrichment (threat ratings, threat tagging, additional information); ways of interaction; data format.
ZeroFOX Platform
With a global data collection engine, AI-powered analysis and an automated remediation system, ZeroFOX protects against cyber, brand and physical threats on social media and digital platforms.

ZeroFOX, the market leader in digital visibility and security, protects today's organizations from dynamic digital risks and physical risks on social, mobile, web platforms.
ZeroFOX detects and eliminates targeted phishing attacks, account compromise, data interception, and location threats. The patented ZeroFOX SaaS technology processes and protects millions of messages and accounts on LinkedIn, Facebook, Slack, Twitter, Instagram, Pastebin, YouTube, mobile app stores every day.
Working with the platform starts with setting up “entities” - everything that matters to your organization on social media and digital channels: brands, employees, executives and VIPs, products, locations and corporate pages. Entities have subsections that consist of profiles, names, keywords, images, domains, hashtags and more. Entity customization controls where and how ZeroFOX collects data. Customization also ensures that you only see data that is relevant to your organization.
Next, you determine what analysis is performed for each entity based on the respective use cases (for example, a brand will have different requirements than an employee). If any violations are detected, ZeroFOX sends out alerts. They appear in a filterable table sorted by risk rating, threat type, timestamp ...
Through a proprietary process, ZeroFOX works on behalf of the client to flag inappropriate content on social media. The product automatically sends complaints about specific violations directly to the Social Security Center for removal. In real time, it is possible to remove any inappropriate content from your corporate pages.
A recent update, ZeroFOX Enterprise Remote Workforce Protection, brings security and intelligence to collaboration platform threats that traditional cybersecurity tools lack.
Product review. Head of Security Department, Storage Company:
There is an urgent need for ZeroFOX because no one else does what this decision does. Working with ZeroFOX really opened our eyes. The best compliment I can give is that the process of working with the platform fully corresponds to the declared description, everything works.
Interface is

the IP-address: yes
the URL-address: yes
Threats category TTPS: yes
hash sums of files: yes
Domain: Yes
Registry Keys: Yes
Non-cards: yes
Phones: yes
Indicators of Social Networking: yes
Protection for mobile applications: yes
Brand Protection : yes
Data leakage: N / A
Data enrichment (threat ratings, threat tagging, additional and other additional information): yes
Interaction methods: API
Data format: JSON, STIX, TAXII
Price: from $ 390 per month
IntSights Threat Intelligence Platform (TIP)
IntSights Threat Intelligence Platform (TIP) helps organizations centralize data from various information sources to keep block lists up to date.

IntSights is revolutionizing cybersecurity operations by leveraging a comprehensive external threat defense platform to neutralize cyber attacks. Cyber intelligence capabilities allow you to continuously monitor the external digital profile of the enterprise on the network and the darknet to identify emerging threats, proactively respond.
The creation of such a specialized threat intelligence product that integrates with core security infrastructure has made IntSights one of the fastest growing cybersecurity companies in the world.
The IntSights Threat Intelligence Platform (TIP) centralizes and lists thousands of intelligence sources for orderly investigation and rapid threat blocking. Threats are prioritized in severity by bringing context to the communication channels. IntSights further provides specialized notifications, alerts and reports for the organization.
A visualized Threat Intelligence Platform Investigation Dashboard allows you to monitor and manage campaigns associated with known malicious assets and coordinate responses. For internal detection and response, the platform integrates with on-premises security systems such as firewalls, web proxies, and Active Directory, automatically informing security teams of threats and automated remediation capabilities.
The ability to connect what is happening outside the organization (on the Internet and the dark web) and what is happening inside the organization (internal data from security devices, networks, systems, devices and users) eliminates the need for extensive training and allows the entire security team to better understand processes.
. , SOC , Teva:
IntSights . , , , .
Interface is

the IP-address: yes
the URL-address: yes
Threats category TTPS: yes
hash sums of files: of N / A
Domain: Yes
Registry keys: of N / A
card numbers: yes
Phones: yes
Indicators of Social Networking: yes
Protection for mobile applications : N / A
Brand protection: yes
Data leakage: N / A
Data enrichment (threat ratings, threat tagging, additional and other additional information): yes
Interaction methods: API
Data format: N / A
Price: from $ 100,000 per year
Kaspersky Threat Intelligence
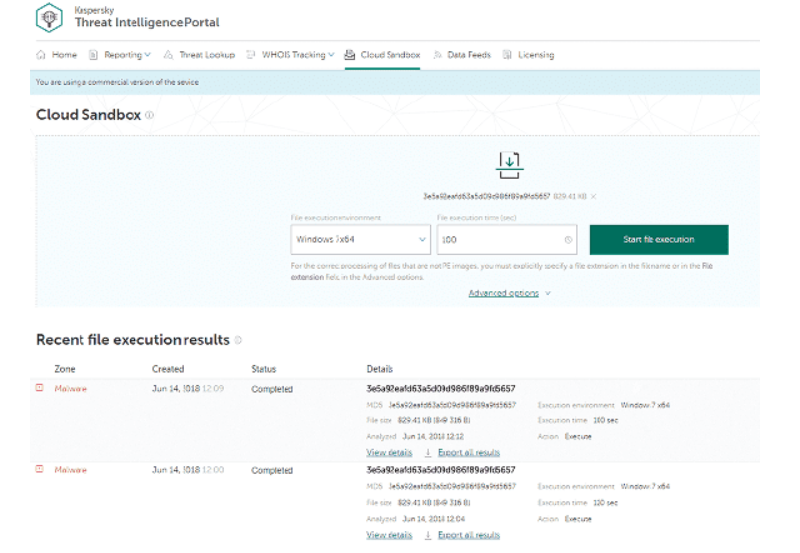
Kaspersky Lab has developed the Kaspersky Threat Intelligence (KTI) portal, which provides access to all the knowledge accumulated over 20 years of the company's experience. This provides security centers with the most up-to-date threat intelligence

Threat Intelligence is built on the expertise of Kaspersky experts who have gathered a complete picture of the current state of attacks against clients, identifying weak points in the network perimeter, cybercriminal threats, malicious activity and data breaches.
The service is available on the Kaspersky Threat Intelligence Portal, a single point of access to data on cyber attacks. Using this portal, SOC specialists receive not only up-to-date information about threats, but also access to the results of global research into the sources of targeted attacks. This allows you to prioritize signals from internal systems about unknown threats, minimizing incident response time, preventing system compromise.
The solution conducts network inventory using non-intrusive methods, identifying critical components of the customer's network perimeter, such as remote management services, unintentionally open and misconfigured services, and network devices. A specialized analysis of the available services leads to ranking of vulnerabilities and a comprehensive risk assessment based on many parameters - a baseline CVSS assessment, the availability of public exploits.
The service includes: Threat Data Streams, Customized Threat Reports, Company-Specific Threat Intelligence Reports, Country-Specific Threat Intelligence Reports, Financial Institutions Threat Intelligence Reports, APT Threat Intelligence Reports, Threat Lookup Service, Service Cloud Sandbox, CyberTrace service.
Through automated data collection through online content hosting services, public forums, social networks, channels and messengers, closed underground online forums and communities, the service provides detailed information on any compromised employee accounts, data breaches, planned or discussed attacks against them. organizations.
Digital Footprint Intelligence reports highlight cybercriminals not only against a customer but also against customers, partners and supplier infrastructure, and provide an overview of current malware or APT attacks across the region and industry. With the help of this information, the customer can look at their business from the point of view of an attacker and understand what he can learn about the IT infrastructure and the company's employees.
. , :
Kaspersky Intelligence Reporting — , . , -. IOC .Interface is
the IP-address: yes
the URL-address: yes
Threats category TTPS: yes
hash sums of files: yes
Domain: Yes
Registry Keys: Yes
Non-cards: yes
Phones: of N / A
Indicators of the social networks: of N / A
Protection of mobile applications : N / A
Brand protection: N / A
Data leaks: N / A
Data enrichment (threat ratings, threat tagging, additional and other additional information): yes
Interaction methods: https
Data format: JSON, STIX, CSV, OpenIoC
Price: from $ 100,000 per year
Group-IB Threat Intelligence
Group-IB Threat Intelligence is a subscription service that monitors, analyzes and predicts threats to organizations, partners and customers.

Group-IB is the official partner of Interpol, Europol and local law enforcement agencies. With over 15 years of experience and highly qualified experts, Group-IB uses its own infrastructure and its own external threat search system. Collecting massive amounts of data in real time, the platform uses proprietary algorithms and machine learning to quickly correlate data.
Group-IB's research activities in the field of data collection argue that the majority of threats directed against the financial sector come from Russian-speaking criminals, which is a specific area of the company's activities. The focus of the solution is not based on managing indicators of compromise, but on information about who is behind each attack.
The Compromised Data section of the platform shows elements such as source, threat, domain and money mules. In this dashboard, analysts can see how effective certain phishing pages are in compromising and what the page looked like when it was detected.
The Group-IB sandbox is designed to emulate an institution's workspace. It estimates the percentage of the file that is malicious and returns a video of how the file behaved in the Sandbox. Analysts also receive a brief description of the behavioral capabilities that the file and process tree has to show how it works.
The recently added Attacks feature provides a clear graph of all intersections from element to other domains of the original phishing page, IP addresses, SSL certificates, email, phone numbers and files.
Advanced Threats makes it easier for analysts to process the vast amount of information offered by offering a prioritized overview of cards with descriptions, timing of criminal campaigns from start to date, and activity information.
Product review. Financial company from Australia:
Unique data sources and access to proprietary resources are what sets Group-IB apart from other vendors. A professional team of analysts exceeded our expectations by quickly performing tailor-made investigations tailored to the context of the threat. The Threat Intelligence platform has been seamlessly integrated into our security system.
Interface is

the IP-address: yes
the URL-address: yes
Threats category TTPS: yes
hash sums of files: yes
Domain: Yes
Registry keys: of N / A
card numbers: of N / A
Phone numbers: of N / A
Indicators of Social Networking: yes
Protection mobile apps: N / A
Brand protection: yes
Data leakage: N / A
Data enrichment (threat ratings, threat tagging, additional and other additional information): yes
Interaction methods: API
Data format: STIX
Price:from $ 150,000 per year
Digital Shadows SearchLight
Minimizes digital risk by identifying unwanted impacts and protecting against external threats. Detects data loss, protects your online brand and reduces attack surface.

Digital Shadows is a globally renowned provider of solutions for tracking and managing an organization's digital risks, across the broadest range of data sources on the internet and the dark web.
The company's flagship product, Digital Shadows SearchLight combines the industry's most comprehensive data analytics with leading security experts. SearchLight provides information about threats from open sources, social networks. Users can access this information through RESTful APIs, email notifications, requests, and weekly intelligence summaries.
To identify potential harm, the solution provides a complete immersion into the dark web - this is the discovery of confidential company data, products and other assets that are sold on the dark web. The investigation and analysis tools used provide the analytics needed to protect assets and data.
With patented technology and analytic tools to detect compromised employee credentials and network loopholes, you can instantly find leaks, domain spoofs, and compromised emails.
SearchLight's cloud-based ecosystem allows it to integrate with other SIEM platforms to create a comprehensive security appliance.
Product review. Norm Laudermilch, CISO at Sophos:
Digital Shadows , . , , , Sophos.
Interface is

the IP-address: yes
the URL-address: yes
Threats category TTPS: yes
hash sums of files: yes
Domain: Yes
Registry Keys: Yes
Non-cards: yes
Phones: yes
Indicators of Social Networking: yes
Protection for mobile applications: yes
Brand Protection : yes
Data leakage: yes
Data enrichment (threat ratings, threat tagging, additional and other additional information): yes
Interaction methods: API
Data format: JSON, XML, STIX, CSV
Price:from $ 5600 per month
RiskIQ Illuminate
The RiskIQ platform provides visibility, understanding and control of exploits, attacks, and automates the detection of external threats to protect against targeted attacks.

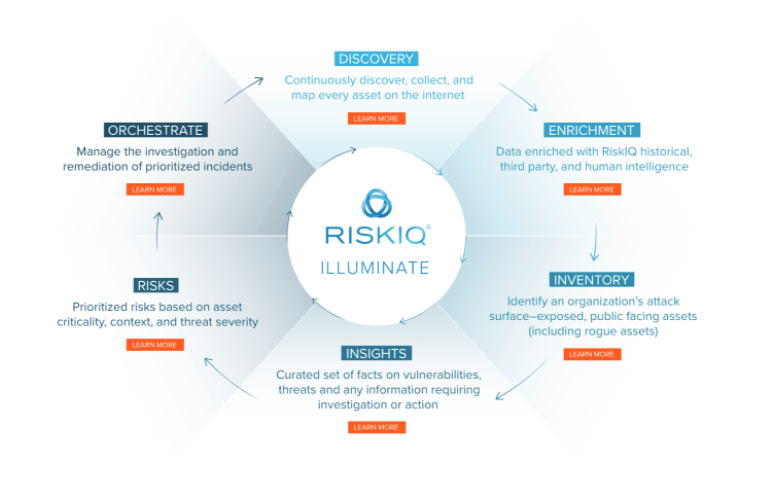
RiskIQ is another leader in digital threat management that provides complete detection, intelligence and remediation of threats associated with an organization's digital presence on the network. RiskIQ's vision and mission over the past ten years has been to capture, correlate and analyze the digital footprint of customers in the Internet infrastructure. With a solution from RiskIQ, you gain a unified view and control over the threats associated with the Internet and social networks, mobile devices.
The RiskIQ Illuminate platform is trusted by thousands of security analysts, security teams and CISOs. It is built on the basis of the broadest data set for optimal recognition and automation of mapping, monitoring surfaces susceptible to Internet attacks, reducing the impact of attacks, and accelerating the investigation of external threats.
Backed by 10 years of experience with Internet attacks, the platform measures all threats - from the dark web to the surface layers of the network and even the physical world. Illuminate generates the analytics you need to get actionable alerts in real time.
Product review. Robin Barnwell, Head of Security at PBB IT Security Standard Bank:
, RiskIQ, , .
IP address interface : yes
URLs: yes
Threats category TTPs: N / A
File hashes: yes
Domains: yes
Card numbers: yes
Phone numbers: N / A
Social media indicators: yes
Mobile app
protection : yes Brand protection : yes
Data leaks: yes
Data enrichment (threat ratings, threat tagging, additional and other additional information): yes
Interaction methods: API
Data format: JSON, XML, STIX, CSV
Price: N / A
Author: Natalka Cech, forROI4CIO