
VeraCrypt is a free fork of TrueCrypt used for end-to-end encryption on Windows, Mac OSX and Linux, and allows you to encrypt the system drive, a separate internal or external drive, or create virtual drives using container files.
In this article we will look at an interesting feature of VeraCrypt for creating an encrypted disk with a hidden partition, this method, also called the "ambiguous encryption" method, provides the possibility of plausible denial of the presence of a second volume, since without the correct password, it is not possible to prove the existence of the hidden volume.
Creating a key file
To work with an encrypted partition, the presence of a key file is not required, but if you protect the data to the maximum, then it will not be superfluous, for example, as another factor to ensure a sufficiently high resistance to forced attacks, also known as the "method of thermorectal cryptanalysis" ...
In this case, it is assumed that there are two key files on external media, one of which will be stored in a sufficiently safe place, for example, in a secure safe deposit box.
The second copy is destroyed when a threat arises. Thus, even if the presence of a hidden partition has become known, and the password has been extracted from it by force, access to the encrypted information will not be possible without a key file.
VeraCrypt has a key file generation tool that allows you to create a file with random data of a given size. To do this, start the Key File Generator from the Tools menu, set the required number of key files and their size, and generate entropy by making chaotic movements with the mouse. After that, save the key file (in our case, also making a copy of it).
Creating an encrypted partition
In order to create a hidden encrypted volume, you first need to prepare a regular (external) encrypted volume. To create it, run from the menu Tools - Volume Creation Wizard .
Select " Encrypt non-system partition / disk " to create an encrypted disk (in my case, it is a small SSD disk). If there is no separate disk, you can use " Create an encrypted file container ", because it will be further mounted as a virtual disk, all subsequent instructions are also valid for it. Set the
volume type to " Hidden Veracrypt volume"Volume Mode" Normal "(as we create a new volume). The placement volume select the drive on which the encrypted volume will be created, in the case of creating a file container will need to specify where to create the file.
Volume Creation Mode " Create and format " if the disk is empty, or " Encrypt in place " if there is already data on the disk that needs to be encrypted.
The encryption algorithm is left AES, because despite the possibility of choosing one of five encryption algorithms, AES is sufficient reliable and fast (VeraCrypt supports and enables hardware acceleration of this algorithm by default when using processors with AES-NI instruction set).
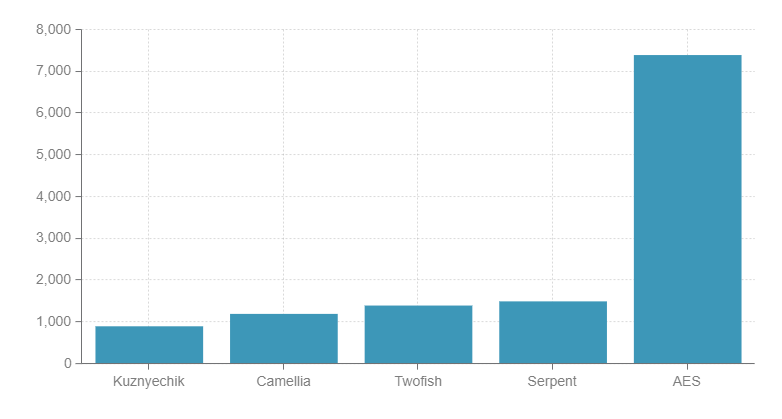
Average encryption / decryption speed in memory (12 threads, App.AES acceleration enabled, Mb / s, more is better):
Let's set a strong password (we described how to choose a strong password in this article).
Fun Fact: The password of the “most wanted hacker” who used full disk encryption, Jeremy Hammond, was his cat's name: “Chewy 123”;
Before formatting the volume, you will need to make a few chaotic movements of the mouse to create the required level of entropy for encryption. The "quick format" option should not be used as it is intended to create a hidden partition. If you are not supposed to store large files (> 4GB), it is recommended to leave the file system type FAT
Creating a hidden volume
In the volume wizard, select " Encrypt non-system partition / disk ". Volume mode " Hidden VeraCrypt volume ". Creation mode " Direct mode ". Let's select the device or container encrypted in the previous step. Enter the password you created earlier and click " Next ".
Let's indicate the type of encryption for the hidden volume. As above, I recommend leaving the default settings. At this stage, we can add the use of a key file as an additional protection measure.
In the next step, we will determine how much space to " take " from the main volume to create a hidden volume. The further process of setting up a volume is similar to setting up an external volume.
Mounting an external volume
Mounting a volume can take some time, this is due to a large number of iterations during key generation, which increases the resistance to attacks "head-on" tenfold.
To mount an external volume, click " Mount ", open " Options " and set the option " Protect hidden volume from damage during writing " and specify the password and key file for the hidden volume.
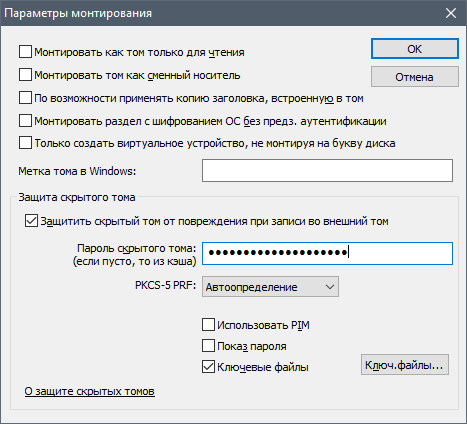
The security option when mounting the external volume must be enabled, since the hidden volume is part of the external volume, and writing to the external volume without protection may damage the hidden volume. In the event that you are forced to mount an external volume by force (against which this mechanism was created), then naturally you mount it as a normal volume, and VeraCrypt will not show that this is an external volume, it will look like a normal volume.
The outer volume can accommodate information that looks or is somewhat sensitive, while all the most valuable will be stored on a hidden volume.
Mounting a hidden volume
To mount a hidden volume, click "Mount", specify the password and key file for the hidden volume. When a hidden volume is mounted, VeraCrypt adds the " Hidden " mark .

Attack vectors
Forehead attack:
Brute-force attacks with a strong password are ineffective - this is the scenario for which the VeraCrypt developers were preparing, and in the presence of a key file, they are absolutely ineffective.
Extracting encryption keys:
In theory, once you gain access to a turned off computer, there is some chance of extracting encryption keys from memory or from the hibernation and paging file. To counteract such attacks, it is recommended to enable the option for encrypting keys and passwords in RAM in the Settings - Performance menu and disable the paging file and hibernation.
Hidden control:
Storing data in encrypted form will protect it in case of loss, confiscation or theft of the device, but if attackers gain hidden control over a computer over the network, for example, using malware with remote control capabilities, it will not be difficult for them to obtain a key file and password at the moment use. We will not consider options for countering these types of attacks, since the topic of network security is quite extensive, and is beyond the scope of this article.

