Threats
The term ACS appeared as soon as computer technology was introduced into control systems. The first simplest ACS consisted of only two levels: information gathering and decision making. Information came from the control object to the operator, who exchanged data with the computer and controlled the object. Here, computing power acted as an aid to human management and decision making.
Since the days of the first computers, automated process control systems have made a giant leap forward. But their feature is still an automated machine process followed by a person.
These systems are intended to be used exclusively in industrial processes. Being involved in critical infrastructures, process control systems are built on the basis of fault-tolerant, highly reliable computing technology. This is an industrial technology designed specifically for long-term, round-the-clock operation at industrial facilities. The consequences of failure or failure of the systems are a serious threat to equipment, to human life and health.
Despite such a responsibility for the continuity of the process, the need to increase the level of safety of the process control system has been discussed only recently. Virus attacks, which have become regular around the mid-2010s, attracted mass interest in the topic. For example, some of the attacks that have occurred over the past decade:
- 2012 Flame, , . . .
- 2014 , , .
- 2017 , , Triton, Trisis/HatMan.
Triton . , , . - 2018 . . Windows XP. HMI SCADA-, .
- 2018 . , . , .
- 2018 , «» , . , , .
, 13- , , «» - , , , ( ).
“ , , — SCADA-, — , . , . — , - , , , . « » – , . . , , . , , .”
- Alexey Kosikhin, Head of the Fuel and Energy Complex, Information Security Center, Jet Infosystems
Among the cyber threats inherent in ICS, three classes can be distinguished:
- man-made threats;
- anthropogenic threats;
- threats of unauthorized access.
Technogenic threats include the physical impact on the components of the APCS. By anthropogenic - intentional and unintentional actions of people engaged in service for automation systems, human errors, mistakes in the organization of work with the components of ACS. Threats of unauthorized access for APCS are considered in the presence of interaction of its components with the local computer network of the enterprise. Such a connection exists to transfer information about the state of the technological environment and control the impact on technological objects.
The interweaving of these factors affects the overall security of systems. This is the failure of even minimal security measures, and the use of Windows as the main operating system for workstations and servers, and weak discipline of employees.
Protection
The implementation of the information security system of the APCS is a complex task. Its solution depends on the implementation of the rules at all levels:
- administrative: formation by the management of a program of work on information security;
- procedural: defining rules and regulations for the personnel serving the network;
- software and hardware: access control;
- ensuring integrity;
- ensuring secure interconnection;
- anti-virus protection;
- security analysis;
- intrusion detection;
- continuous monitoring of the state, detection of incidents, response.
Vulnerability control systems are one of the most effective methods of countering industrial cyber threats. These are highly specialized programs designed specifically for industrial automation systems. They allow you to determine the integrity of the internal environment of the device, record all attempts to change the application program of the controller, changes in the configuration of network protection and control devices in power grids.
Many cybersecurity product developers point to the need for increased visibility within the network in the first place... Experience shows that this is really important. A network compromise unnoticed in time can work for months with unactivated exploits. Dedicated cyber threat detection and prevention tools not only detect vulnerabilities, but also identify zero-day threats.
Many information security risks are associated with outdated hardware and software - for example, there are SCADA systems that can only work with Windows NT or Windows 98. Some of these risks can be mitigated by modern virtualization technologies , but this is not always possible. Associated with this is another type of protection - insulation... SCADA and OPC (OLE for Process Control) servers, PLCs and other components of automated control systems must be isolated from the Internet.
Separately, it is worth highlighting platforms for creating a distributed infrastructure of false targets , DDP (Distributed Deception Platform). They allow you to deploy a network of fake decoy devices that are almost indistinguishable from real ones, which attracts attackers.
Now that we have a general idea of how ICS cyber security should work, we move on to the second part of this article. It will provide an overview of the practical security solutions presented in the comparison table .
For this article, we have selected just a few key points from the table, such as zero-day threat detection, integrations, anomaly detection and traffic analysis, device inventory, product features.
Solutions
Dragos Industrial Cybersecurity Platform
Dragos is a US company founded in 2016. Despite her “young” age, she has already received many world awards in the field of cyber defense of industrial systems.
They are a team of experts specializing in industrial security solutions and the Internet of Things. Their flagship product is exactly the platform, but Dragos also provides incident response services, threat analysis to your network, and cybersecurity training.
Dragos Industrial Cybersecurity Platform is an industrial network security solution that automatically finds and identifies network assets. The program scans assets, finding incorrect settings, configuration improvement opportunities.
If suspicious activity is detected, the platform provides step-by-step guidance for investigating and responding to an incident and troubleshooting tools.

Features:
Device inventory : yes
Zero-day threat detection : no
Anomaly detection : yes
Traffic analysis : yes
Integrations : SIEM
Supported systems : DCS, PLC
Feature : step-by-step security management guide from team experts, issued in a playbook.
CyberX OT
Prior to creating CyberX , her team had worked in the field of protecting critical US infrastructures. Their pride, in addition to Pentagon-level protection and cooperation with world market leaders, is a patented method of machine learning. It is thanks to him that their products instantly reveal any anomalies in industrial networks.

Work CyberX OT platform is based on five key elements: a behavioral analysis of assets to identify any unusual actions; monitoring of protocol violations; detection of malicious agents (including advanced threats); finding operational problems; identifying connections between machines that should not "communicate".
The solution is able to fully integrate into your security stack thanks to its open API. This integration will solve the security problem in both IT and industrial environments.
Features:
Device Inventory : yes
Zero-day threat detection : yes
Anomaly detection : yes
Traffic analysis : yes
Integrations : Firewall, CMDB, IDS / IPS, SIEM, SOC
Supported systems : DCS, PLC, RTU
Feature : Self-learning machine analytics that reduces false triggering to zero.
Cyberbit SCADASchield
Since 2015 Cyberbit has been supplying cybersecurity solutions to the market. The company specializes in attack emulation and training for information security teams, endpoint protection, industrial network protection, orchestration and automation of security systems.
SCADAShield provides unprecedented network visibility, detection of known and unknown anomalies and errors in operational technology. And with 7 layers of deep packet inspection (DPI), the solution breaks out of operational limits.
The visualization of your entire network is real-time and includes IP and non-IP devices.
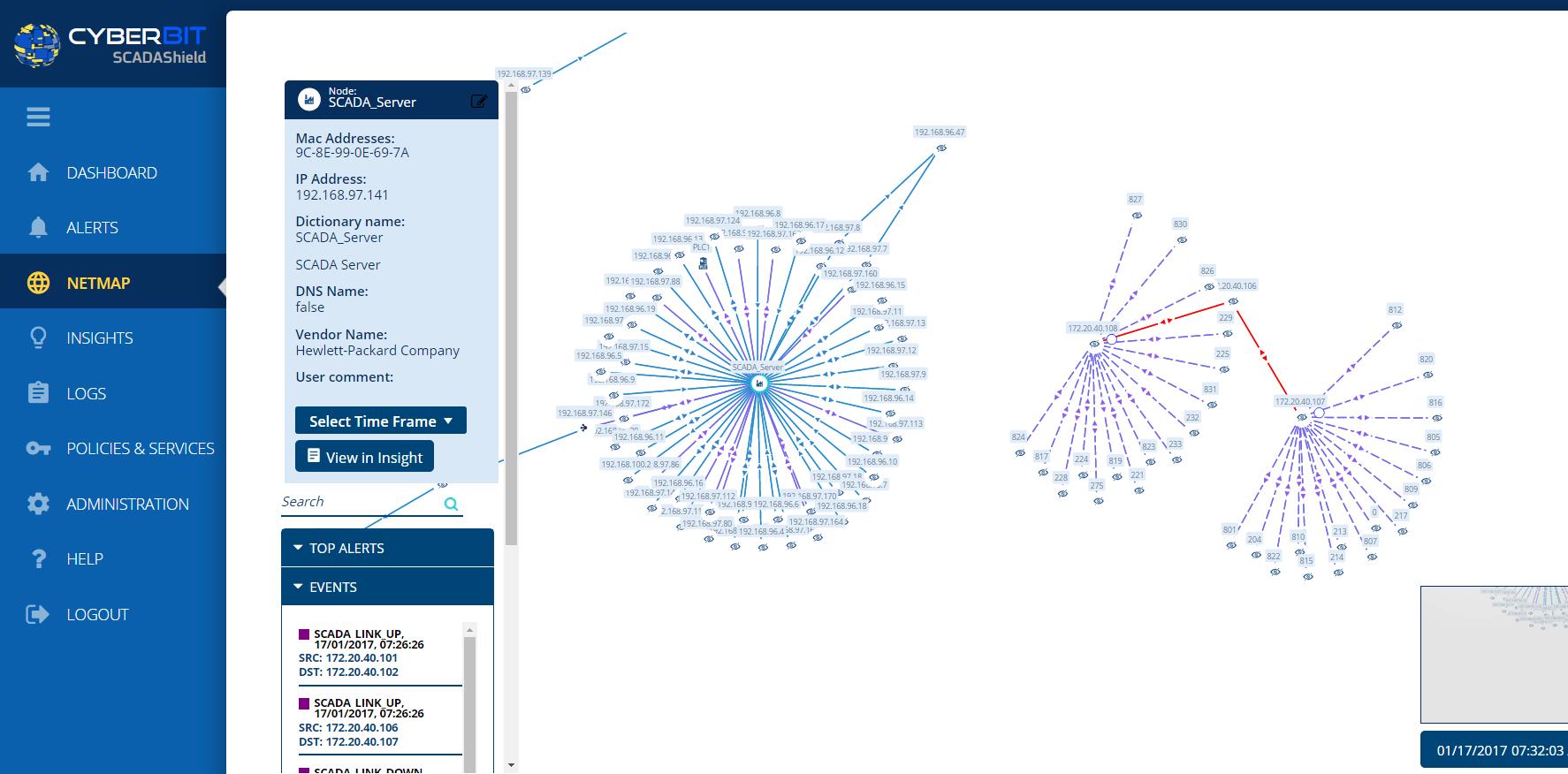
Features:
Device Inventory: No
Zero-Day Threat Detection: Yes
Anomaly detection: yes
Traffic analysis: no
Integrations: Cyberbit EDR, SIEM
Supported systems: N / A
Feature: formation of a map of information flows between network assets, automatic generation of rules
Claroty Platform
Claroty's mission is to protect industrial networks. This is a team made up of professionals from various fields of expertise: there is a former admiral for cybersecurity of the US Army, and a space designer, and an insurance specialist.
The Claroty Platform provides security teams with exceptional visibility into industrial control networks and real-time monitoring. The monitoring is able to recognize advanced threats and identify network vulnerabilities in time.
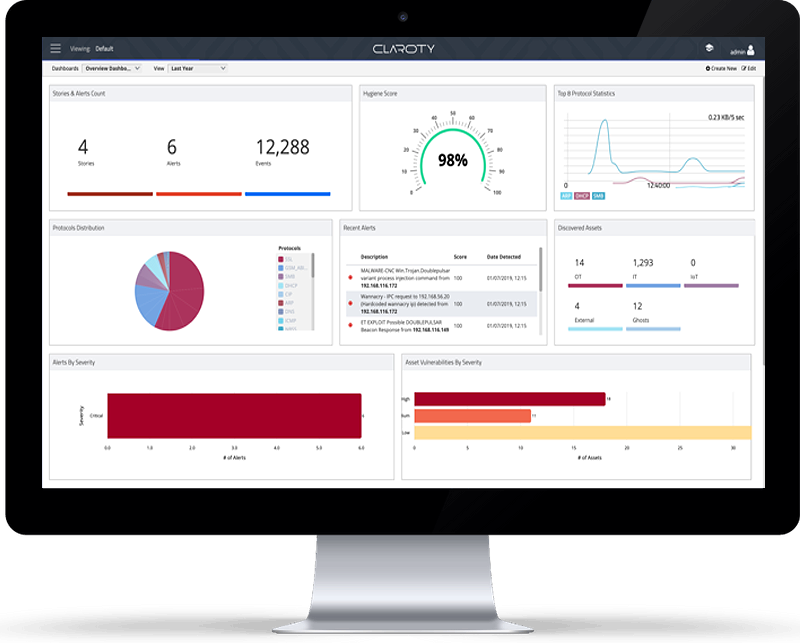
The platform enables network segmentation, control and provision of secure remote access, granular access policies, and session recording.
Features:
Device Inventory: Yes
Zero-Day Threat Detection:yes
Anomaly detection: yes
Traffic analysis: no
Integrations: SIEM, SOC
Supported systems: HMI, PLC
Feature: remote access control, fast and accurate response to security incidents
Veracity Cerebellum
Veracity's goal is to make your industrial network resilient and secure. The company supplies a local, centralized solution for optimal network configuration, management and monitoring.
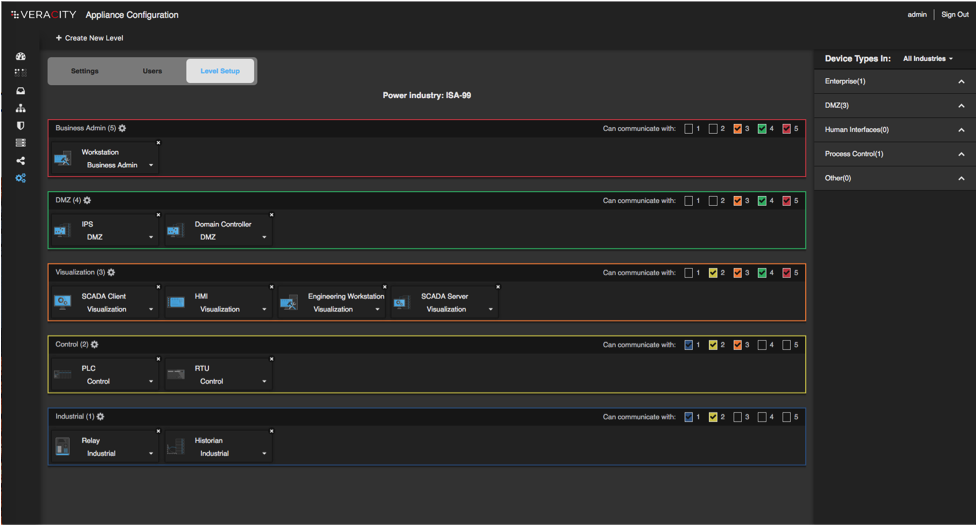
The flagship product, Veracity Cerebellum , is designed to be similar to the human cerebellum. The function of the cerebellum is to receive signals from the spinal cord, brain, sensory systems and, based on the data, regulate body movements.
The Veracity Cerebellum platform performs similar functions in industrial networks. It reacts to sensory input and manages the pre-engineered response of the manufacturing process.
Features:
Device Inventory: Yes
Zero-Day Threat Detection:no
Anomaly detection: yes
Traffic analysis: yes
Integrations: OT
Supported systems: N / A
Feature: creation of security models from templates or from scratch, advanced network device management (including quarantine), network segmentation and allocation of safe zones
Waterfall Unidirectional Security Gateways
Waterfall Security Solutions has been protecting critical industrial networks since 2007. The Unidirectional Security Gateway is their proprietary solution for secure integration and communication between IT and OT networks. This solution allows for cloud-based remote monitoring and diagnostics, protects against unauthorized access. At the same time, it is devoid of vulnerabilities that exist when connecting through a firewall.
Unidirectional Security Gateways provide hardware-based network perimeter protection. The solution consists of a hardware component ( TX module - fiber optic transmitter, RX module - optical receiver) and software component (industrial application software connectors).

This configuration allows one-way transmission and replication of server information from the OT network to the external network, while preventing the spread of any virus, DOS attack, human error, or any cyber attack.
Features:
Device Inventory: No
Zero-Day Threat Detection: No
Anomaly Detection: Yes
Traffic Analysis: Yes
Integrations: IT / OT
Supported Systems: N / A
Feature: Server Replication, Industrial Device Emulation, Industrial Data Cloud Conversion
Nozomi Networks Guardian
Nozomi Networks offers a unified solution for real-time cyber risk management. High accuracy and minimal false positives are achieved through innovative use of artificial intelligence and machine learning. Nozomi Networks Guardian's
technologies enable it to automatically map and visualize your entire industrial network, including assets, connections and protocols. The solution monitors network communications and behavior for risks and provides the information needed to respond quickly. The Integrated Security Infrastructure includes built-in integrations for asset management systems, ticket and identity management systems, SIEM. Features: Device Inventory: Yes
Zero-day threat detection: yes
Anomaly detection: yes
Traffic analysis: yes
Integrations: IT / OT, SOC
Supported systems: N / A
Feature: scalability, network visibility, advanced anomaly and threat recognition, self-learning
Indegy Industrial Cybersecurity Suite
Founded with the goal of securing industrial networks, the Indegy team boasts a unique combination of cybersecurity expertise and hands-on industrial control knowledge.
The company's leadership and research teams include security, industrial operations and defense experts, including several graduates from Israel's elite cybersecurity units.
Deployed as a network or virtual appliance, the Indegy Industrial Cybersecurity Suit provides comprehensive security tools for Information Security personnel and OT engineers.
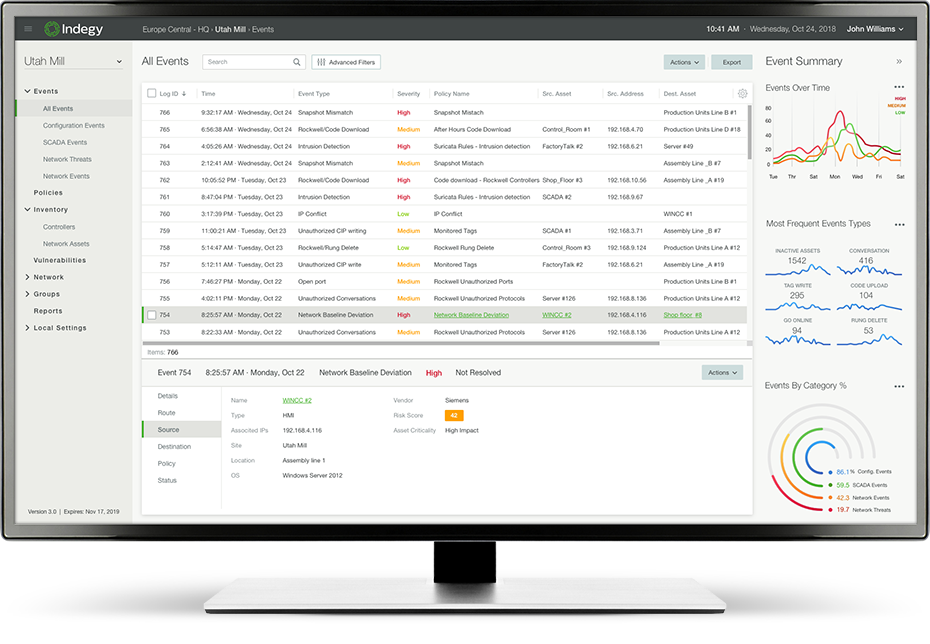
The platform provides asset tracking, threat detection and mitigation, vulnerability management, and device integrity. It is able to protect the network not only from malicious interference, but also from unintentional human errors.
Features:
Device Inventory: Yes
Zero-Day Threat Detection: No
Anomaly Detection: Yes
Traffic Analysis:
Integrations: CMDB, SIEM
Supported Systems: DCS, PAC, PLC, RTU
Feature: Agentless network connection, custom policy alerts and mail, active detection technology to ensure device integrity
ICS CyberVision
Sentryo was founded by two entrepreneurs and veterans in the information security industry. They now apply their years of experience in the software, hacking and cybersecurity environment to the industrial cybersecurity world.
The company has developed unique AI algorithms to provide complete information about industrial assets. Their artificial intelligence is capable of identifying vulnerabilities, detecting anomalies in real time, and working with the IT team to fend off cyberattacks.
ICS CyberVision uses a unique OT language to automatically label every asset and network activity. This allows you to immediately see device functions, system brands, protocols used, OT or IT behavior, and network information.

The solution allows you to group assets and define their "industry impact" so you can prioritize actions against your security goals.
Features:
Device inventory: yes
Zero-day threat detection: no
Anomaly detection: yes
Traffic analysis: no
Integrations: firewall, CMDB, SIEM, SOC
Supported systems: N / A
Feature: passive monitoring without impacting the system, contextualized events, grouping and prioritization assets in the network by their impact on security
Forescout Platform
Forescout , founded in 2000, develops in its own lab solutions for device visibility, behavior control and cybersecurity for any type of network device. Their team is committed to improving the ability of organizations to identify, understand and manage threats from an ever-expanding ecosystem of devices.
Forescout Platform is a unified security platform that allows you to gain complete situational awareness of the corporate environment and organize actions to mitigate any risks.
The product allows you to enforce adaptive, granular policies and
quickly view results using your existing physical and virtual network infrastructure.
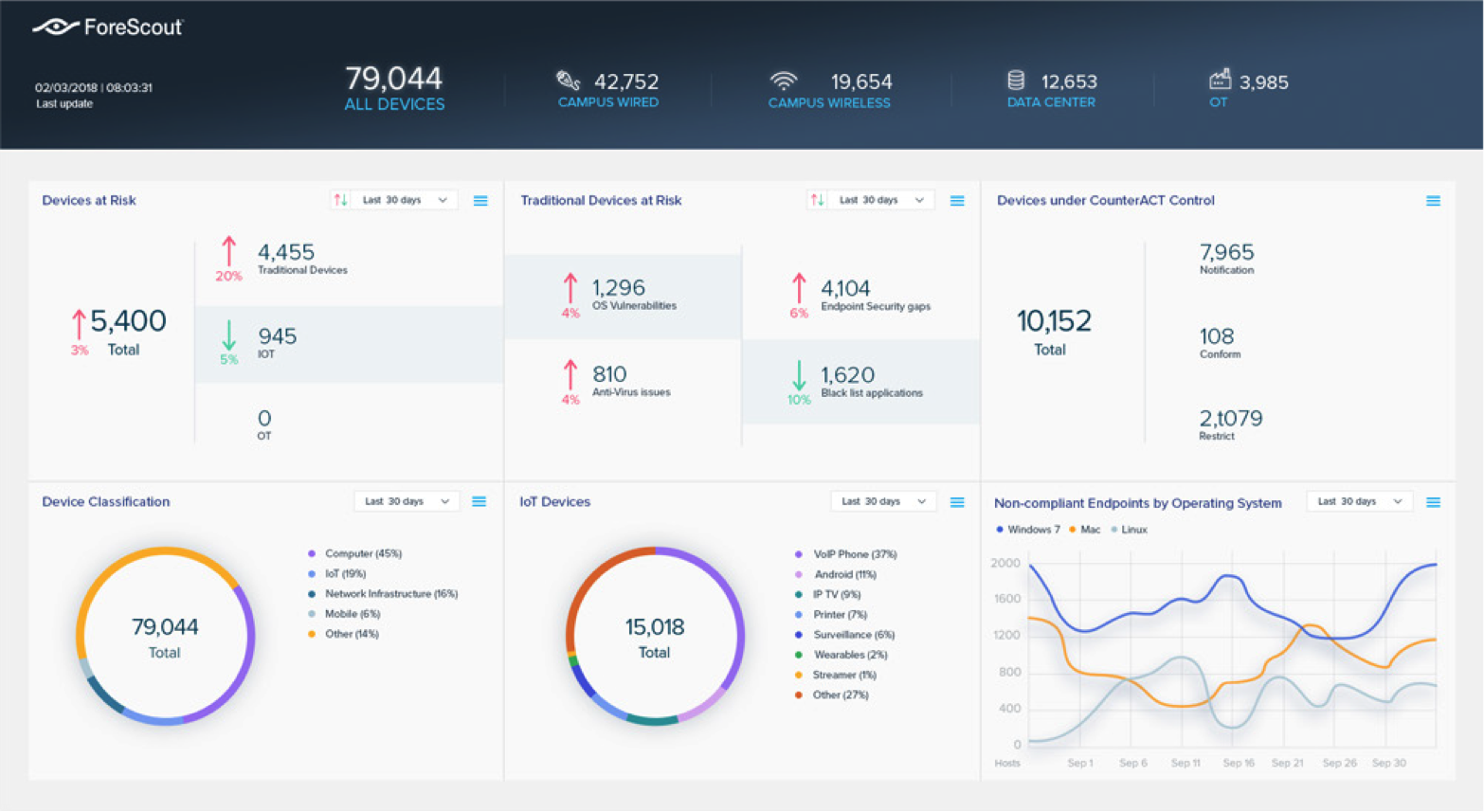
The platform scales to 2 million devices per deployment across enterprise infrastructure, data center, cloud and OT networks.
Features:
Device inventory: yes
Zero-day threat detection: no
Anomaly detection: yes
Traffic analysis: no
Integrations: CMDB
Supported systems: N / A
Feature: scalability, dynamic device segmentation, fix incompatible devices during connection
After reviewing all products, you can conditionally group like this:
- , — CyberX OT, Indegy Industrial Cybersecurity Suite, ICS CyberVision, Cyberbit SCADASchield;
- , — Forescout Platform;
- , Nozomi Networks Guardian Veracity Cerebellum;
- , — Dragos Industrial Cybersecurity Platform, Claroty Platform;
- hardware perimeter protection - Waterfall Unidirectional Security Gateways .
You can see a more detailed list of functions of each of the solutions in the comparison table , and create your own comparison table with the solutions you are interested in here .
Author: Natalka Chekh, for ROI4CIO