
DoH and DoT protection
Are you in control of your DNS traffic? Organizations invest a lot of time, money and effort in securing their networks. However, one area that is often overlooked is DNS.
A good overview of the risks posed by DNS is the Verisign presentation at the Infosecurity conference.

31% - DNS .
. Palo Alto Networks Unit 42, 85% DNS , , . DNS NGFW.
DNS, DNS . . DNS-. DNS, , . , , DNS . . Garmin, , 10 .
NGFW DNS-over-TLS (DoT) DNS-over-HTTPS (DoH), DNS .
DNS?
DNS
(DNS) (, www.paloaltonetworks.com ) IP- (, 34.107.151.202). -, DNS- DNS-, IP-, . DNS- IP-, .
DNS , . DNS DNS- . DNS Man-in-the-Middle, , DNS ( ) .
DNS:
DNS-over-HTTPS (DoH)
DNS-over-TLS (DoT)
: DNS- ... . TLS (Transport Layer Security) , , , DNS, , DNS.
DNS . , , . , DoH DoT.
DNS over HTTPS (DoH)
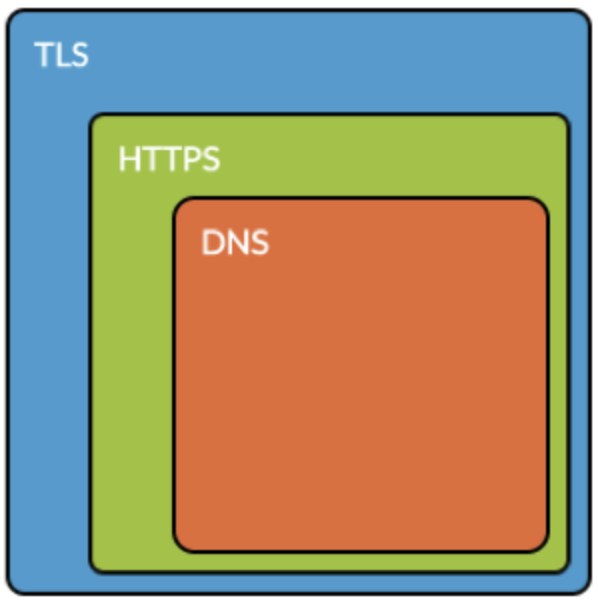
DoH 443 HTTPS, RFC , , « DoH HTTPS », « DNS» , , ( RFC 8484 DoH, 8.1 ). DoH TLS , HTTPS HTTP/2, DNS HTTP.
, DoH
HTTPS- DoH, ( ) DNS, DoH, , DNS . DoH HTTPS.
Google, Mozilla DoH , DoH DNS. Microsoft DoH . , - , DoH . ( , : PsiXBot Google DoH , PsiXBot DNS Godlua .) , , DoH , DoH (C2) .
DoH
DoH NGFW HTTPS DoH ( : dns-over-https).
-, «dns-over-https», :

( HTTPS) NGFW «» «dns-over-https», DoH , HTTPS DoH (. Applipedia Palo Alto Networks «dns-over-https»).
DNS over TLS (DoT)

DoH , DoT , , DNS ( RFC 7858 , 3.1 ).
DoT TLS , DNS, , 853 ( RFC 7858, 6 ). DoT , , , .
, DoT
Google DoT Android 9 Pie , DoT, . DoT , , 853 .
DoT
DoT , :
Configure NGFW to decrypt all traffic for destination port 853. By decrypting traffic, DoT will appear as a DNS application, to which you can take any action, for example, enable Palo Alto Networks DNS Security subscription to control DGA domains or existing DNS Sinkholing and anti -spyware.
Alternatively, the App-ID engine can completely block the 'dns-over-tls' traffic on port 853. It is usually blocked by default, no action is required (unless you specifically allow the 'dns-over-tls' app or port traffic 853).