
Selectel: ( ). , .
?
We studied this topic in detail, but could not find specific laws (we are talking about US legislation - ed.). If you can identify the articles of laws that govern the collection of browser fingerprints in your country, please let us know.
But in the European Union there are laws and directives (in particular, the GDPR and the ePrivacy Directive) that govern the use of browser fingerprints. This is perfectly legal, but only if the organization can prove the need for such work.
In addition, user consent is required to use the information. However, there are two exceptions to this rule:
- When a browser fingerprint is required for "the sole purpose of transmitting a message over an electronic communications network."
- When browser fingerprint collection is required to tailor the user interface of a specific device. For example, when you surf the web from a mobile device, the browser fingerprint collection and analysis technology is used to ensure that you get a customized version.
Most likely, similar laws apply in other countries. So the key point here is that a service or site needs user consent to handle browser fingerprints.
But there is a problem - not always an obvious question. Most often, the user is shown only the banner "I agree to the terms of use." Yes, the banner always contains a link to the conditions themselves. But who reads them?
So usually the user himself gives permission to collect browser fingerprints and analyze this information when he clicks on the "agree" button.
Test your browser fingerprint
Okay, above we discussed what data can be collected. But what about a specific situation - your own browser?
In order to understand what information can be collected with its help, the easiest way is to use the Device Info resource. It will show you what a third-party observer can get from your browser.
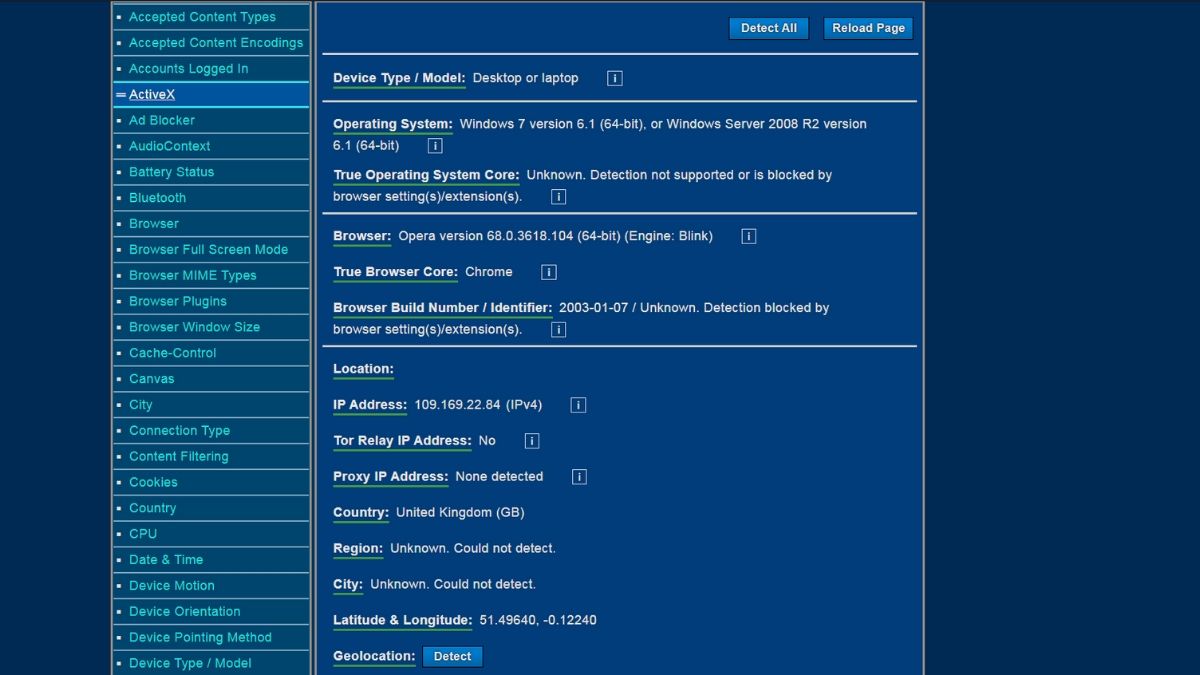
See this list on the left? That's not all, the rest of the list will appear as you scroll down the page. The city and region are not displayed on the screen due to the use of VPN by the authors.
There are also a few other sites that help you run your browser fingerprint test. This is Panopticlick from EFF and AmIUnique , an open source site.
What is browser fingerprint entropy?
This is an assessment of the uniqueness of your browser fingerprint. The higher the entropy value, the higher the uniqueness of the browser.
The entropy of the browser fingerprint is measured in bits. You can check this indicator on the Panopticlick website.
How accurate are these tests?
In general, they can be trusted because they collect exactly the same data as third-party resources. This is if we evaluate the collection of information point by point.
If we talk about assessing uniqueness, then not everything is so good here, and here's why:
- Test sites do not consider random fingerprints, which can be obtained, for example, using Brave Nightly.
- Sites like Panopticlick and AmIUnique have huge archives of data that contain information about old and outdated browsers whose users were tested. So if you take the test with a new browser, you will likely get a high score for the uniqueness of your fingerprint, even though hundreds of other users are using the same browser of the same version as you.
- Finally, they don't account for screen resolution or browser window resizing. For example, the font may be too large or small, or the color may make the text difficult to read. Whatever the reason, the tests don't take that into account.
In general, fingerprint uniqueness tests are not useless. They are worth testing in order to find out your level of entropy. But the best thing is to simply assess what information you are sending out.
How to protect against collection of browser fingerprints (simple methods)
It should be said right away that it will not work to completely block the formation and collection of a browser fingerprint - this is the basic technology. If you want to protect yourself 100%, you just need to not use the Internet.
But the amount of information that is collected by third-party services and resources can be reduced. Such tools will help here.
Firefox browser with modified settings
This browser is good at protecting user data. Recently, developers have protected Firefox users from third-party fingerprint collection.
But the level of protection can be increased. To do this, go to the browser settings by entering "about: config" in the address bar. Then we select and change the following options:
- webgl.disabled — «true».
- geo.enabled — «false».
- privacy.resistFingerprinting — «true». . .
- privacy.firstparty.isolate — «true». cookies first-party .
- media.peerconnection.enabled — , , VPN, . WebRTC IP.
Brave Browser
Another user-friendly browser that offers strong privacy protection. The browser blocks all kinds of trackers, uses HTTPS wherever possible, and blocks scripts.
In addition, Brave allows you to block most of the browser fingerprint collection tools.
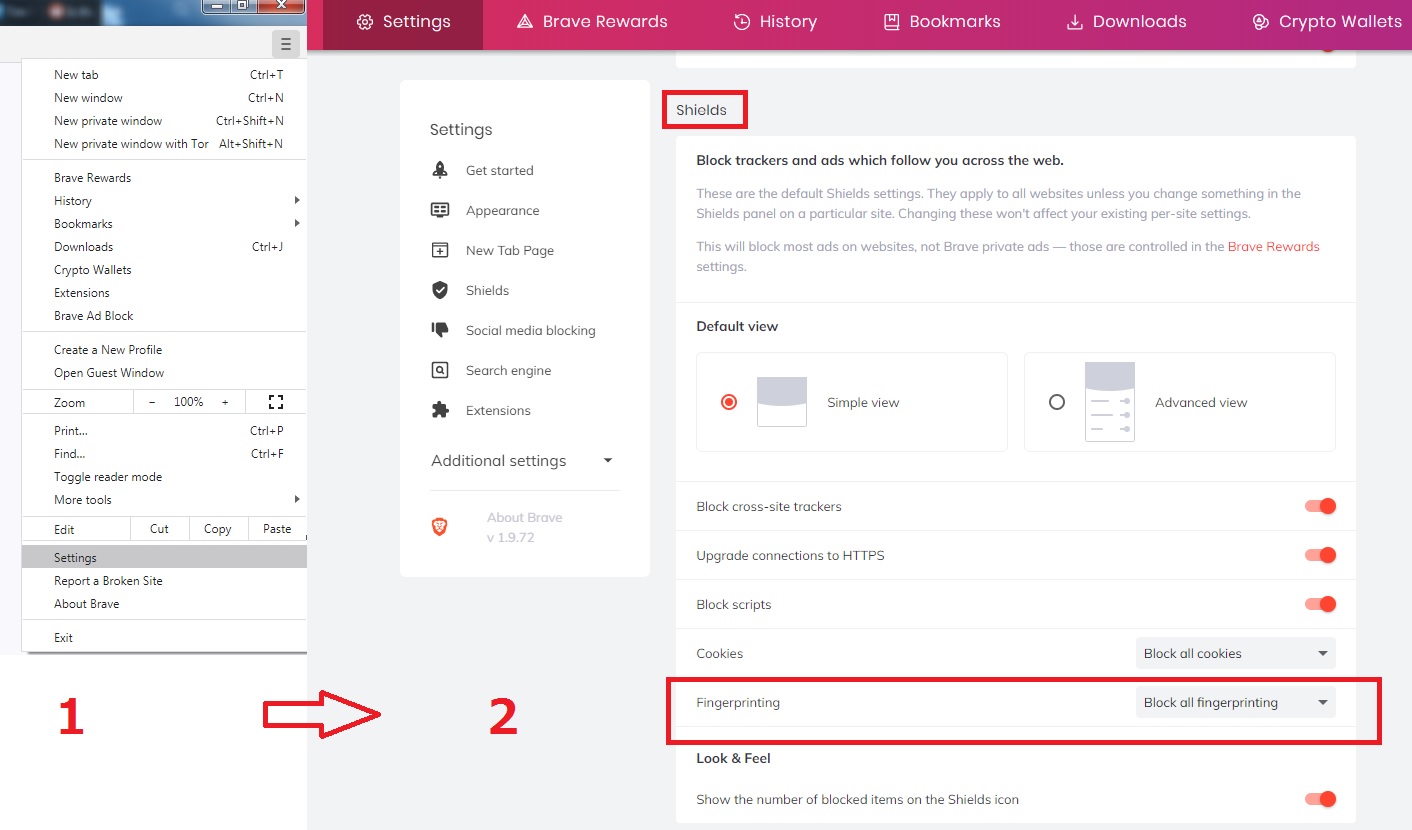
We used Panopticlick to estimate the entropy level. Compared to Opera, the result is 16.31 bits instead of 17.89. The difference is not huge, but it is still there.
Brave users have come up with a ton of ways to prevent browser fingerprint collection. There are so many details that it is impossible to list them in one article. All details are available on the project's Github .
Dedicated Browser
Extensions Extensions are a sensitive topic as they sometimes enhance the uniqueness of a browser fingerprint. Whether to use them or not is up to the user.
Here's what to recommend:
- Chameleon - modification of user-agent values. You can set the frequency "once every 10 minutes", for example.
- Trace - protection against different types of collection of prints.
- User-Agent Switcher - does much the same as Chameleon.
- Canvasblocker - protection against collecting digital prints from canvas.
Use one extension rather than all at once.
Tor browser without Tor Network
On Habré it is not necessary to explain what a Tor browser is. By default, it offers a number of tools to protect personal data:
- HTTPS is everywhere and everywhere.
- NoScript.
- Blocking WebGl.
- Blocking canvas image extraction.
- Changing the OS version.
- Blocking information about time zone and language settings.
- All other functions to block tracking tools.
But the Tor network isn't as impressive as the browser itself. That's why:
- She works slowly. This is because there are about 6 thousand servers, but about 2 million users.
- Many sites block Tor traffic - for example, Netflix.
- There are leaks of personal information, one of the most serious happened in 2017.
- Tor has an odd relationship with the US government - a close collaboration. In addition, the government financially supports Tor .
- You can connect to the attacker's node .
In general, it is possible to use the Tor browser without the Tor network. This is not so easy to do, but the method is quite affordable. The goal is to create two files that will disable the Tor network.
This is best done in Notepad ++. Open it and add the following lines to the first tab:
pref ('general.config.filename', 'firefox.cfg');
pref ('general.config.obscure_value', 0);
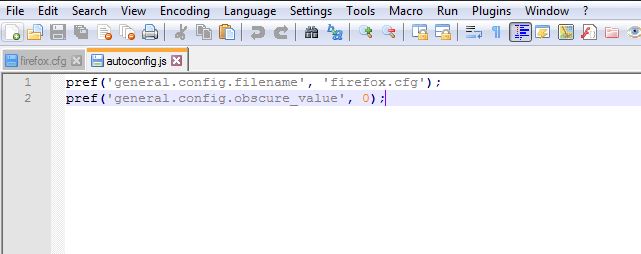
Then go to Edit - EOL Conversion, select Unix (LF) and save the file as autoconfig.js in the Tor Browser / defaults / pref directory.
Then open a new tab and copy these lines:
//
lockPref ('network.proxy.type', 0);
lockPref ('network.proxy.socks_remote_dns', false);
lockPref ('extensions.torlauncher.start_tor', false);
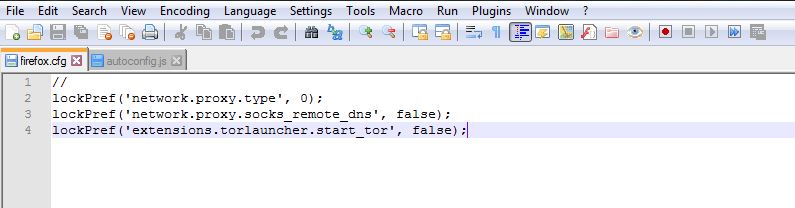
The file name is firefox.cfg, it must be saved in the Tor Browser / Browser.
Everything is now ready. After launching, the browser will show an error, but you can ignore this.
And yes, disconnecting the network will not affect the browser fingerprint in any way. Panopticlick shows an entropy level of 10.3 bits, which is much less than with the Brave browser (it was 16.31 bits).
The files mentioned above can be downloaded from here .
In the third and final part, we will talk about more hardcore methods of disabling surveillance. We will also discuss the issue of protecting personal data and other information using a VPN.
