 The interesting news last week was a set of vulnerabilities in Apple's infrastructure, which were discovered by a team of five within three months. For 55 vulnerabilities, including 11 critical, the IT giant will pay independent researchers 237 thousand dollars. This amount is the result of a partial analysis of the reports, the total reward may exceed 500 thousand dollars. The record aggregate payment corresponds to the danger of the discovered problems: several bugs made it possible to hack accounts of the iCloud cloud service, gain access to closed Apple resources and even the company's local network.
The interesting news last week was a set of vulnerabilities in Apple's infrastructure, which were discovered by a team of five within three months. For 55 vulnerabilities, including 11 critical, the IT giant will pay independent researchers 237 thousand dollars. This amount is the result of a partial analysis of the reports, the total reward may exceed 500 thousand dollars. The record aggregate payment corresponds to the danger of the discovered problems: several bugs made it possible to hack accounts of the iCloud cloud service, gain access to closed Apple resources and even the company's local network.
For an outside observer, the event is interesting for the most detailed description of 11 critical vulnerabilities published in the blogresearch team leader, Sam Curry. All vulnerabilities in one way or another relate to the company's network services: one of the reports even mentions that the attackers did not even have iPhones and iPads directly at hand. According to Sam Curry, Apple employees fixed all the problems very quickly, some within hours after submitting the report.
The sprint to hack Apple began by scanning the company's servers accessible from the Web. At the same time, it became known that the company entirely owns the range of IP addresses 17.0.0.0/8. Already at this stage, 22 nodes surfaced with the CVE-2020-3452 vulnerability in Cisco VPN servers: it can be used to read arbitrary files. Among the 11 critical vulnerabilities, two of the most interesting are worth noting.

First, the researchers managed to hack the forum of the closed program AppleDistinguishedEducators. The forum used the Jive Intranet software , to which the unified Apple authorization system was bolted. To access the forum, you had to leave a request on the server. As it turned out from the analysis of requests after filling out the form, the server retained a rudiment of its own authorization system Jive, on which the application system was running. Each application essentially created a new account on the forum, with the default password ### INvALID #%! 3. Indeed, after all, the login then occurs through Signin with Apple, the correct design of the internal Jive accounts could not have been dealt with.
This was a mistake on the part of those who set up the server. Sam Curry and his colleagues naturally found a way to use the standard login system, but were unable to enter the forum because their account did not receive administrator approval. They ran an enumeration of all three-letter logins, and one of them worked - with the same default password. So the researchers entered the forum, then looked at the list of users, identified the administrators and logged in in the same way under an account with extended rights. After some experimentation, they were able to execute arbitrary code on the server. It seems to be "hacked the forum and that's it," nothing interesting. But the arbitrary code execution opened up access to the LDAP service and a fairly large portion of Apple's internal network.
The second interesting vulnerability was found in the iCloud service, more precisely in the mail client, or more precisely, in its web version. Here, the researchers were aiming for an XSS vulnerability - a way to execute code with access to a user's personal data so that it could be stolen in the worst case for the victim. And she was found! First of all, it turned out that new messages arrive in the web client as a piece of data in the JSON format, and then they are processed locally. After a number of experiments with the "style" tag, it became possible to execute an arbitrary script in the following configuration:
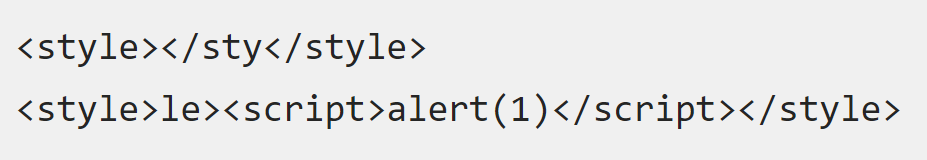
This opened access to any iCloud services from the victim's browser. For a successful attack, it was enough to send a prepared email message. If the user opens it in a web client, a malicious script is executed. The hackers' PoC model turned out to be elegant and evil: since we have full access to iCloud on behalf of a logged in user and we received it through an email client, let's download a bunch of victim's photos, send them to our mail, and at the same time send an infected message throughout address book. If this hole was found not by researchers, but by cybercriminals, another massive leak of private data could have occurred (with the amendment that not everyone uses the web client, of course). PoC on video:
Other critical vulnerabilities include compromising industrial manufacturing control system DelmiaAlpriso, executing arbitrary code on the server to receive and process content from publishers, and obtaining access keys to servers hosted by AmazonWebServices. In this story, it is precisely the detailed description of vulnerabilities by researchers that is valuable, since vendors are not interested in such disclosure of information and are usually limited to dry phrases like “under some conditions, code execution is possible”.
What else happened
ArsTechnica reporters write about an "unrecoverable" vulnerability in the T2 chip in Apple desktops and laptops. They managed to hack this hardware security system using the conditional porting of the Checkm8 exploit used to jailbreak iOS devices.
Combined with another previously discovered vulnerability in T2, the new hole has the potential to bypass key security mechanisms such as fingerprint authentication and data encryption. The scale of the consequences has not yet been precisely determined: in its current form, the set of exploits can be applied only locally, the vulnerability does not survive a reboot, and they have not shown examples of practical data theft.
Researchers at ImmersiveLabs founda way to steal personal data from Fitbit smartwatches and fitness bracelets through a malicious application.
British
Facebook is changing the rules of the bugbounty program and is trying to motivate researchers to work on finding vulnerabilities on the social network constantly. In exchange for money: seniority in the program turns into bonuses for payments for discovered holes.

Microsoft experts are investigating a Russian-language (see screenshot above) ransomware Trojan for Android known as MalLocker. The malware does not encrypt data, but it blocks access to the device and uses a publicly available "machine learning" module (!) To automatically resize the picture to fit the screen.