About 15 years ago, when the Internet was issued by cards and measured in hours, it was a common thing for us to visit for games, books and films. Many had one single disk, necessarily partitioned into c: and d:
But no one thought about exactly which files lying on the hard disk were available on the connection computer. Of course, after all, you came to a friend and thought that you would finally get fresh anti-virus databases. the person wrote out an upgrade special, and the purpose of the visit was a film in the translation of a goblin. And he received from you a selection of the necessary bodies of viruses from the university or photos from tests.
Complete trust, right? Nobody copied cookies or icq correspondence, etc. And then there were no secrets. It all looks like our hard drives are big flash drives. And so it is! Like a USB flash drive, you can forget or lose your hard drive / phone / laptop.
As a student, this would be a terrible event, but more financially.
And if today your devices or cloud accounts fall into the wrong hands, what will you worry about?
I am no longer a student, and I will worry not only about the loss of my devices, but also about corporate secrets, access, correspondence and contacts. If someone uses my account and writes the most frequent contacts a typical, for some social. networks, the request "translate by Friday" or "grant temporary access", then someone may be led, and this is a great sadness.
I think my further text for most people from IT (and not only) is not relevant, but it will be useful to someone, I hope
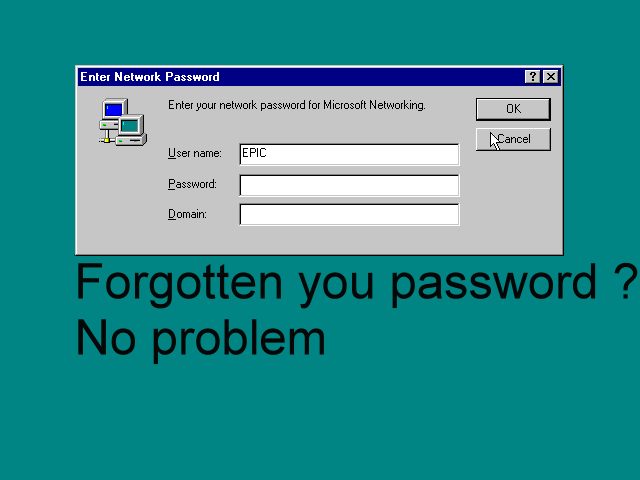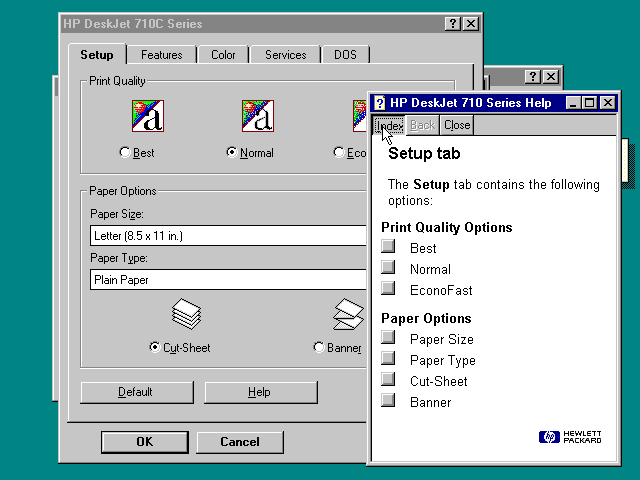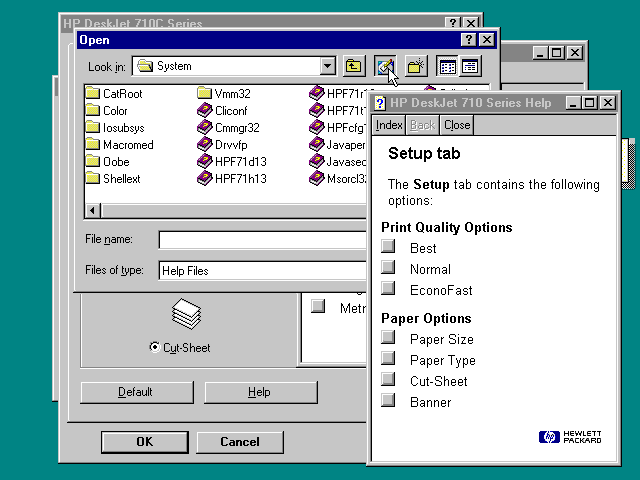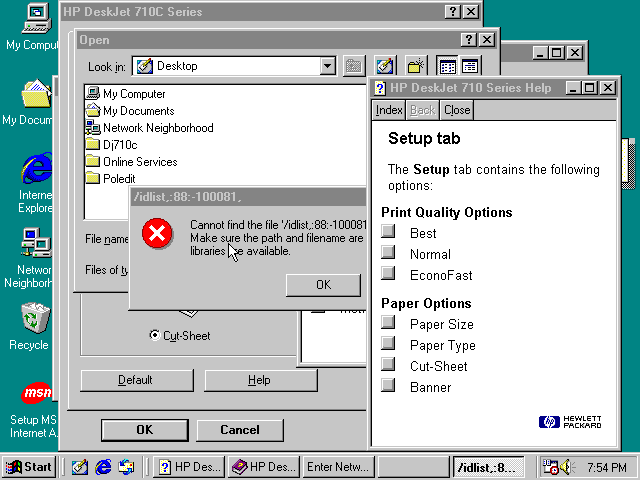
Your computer is a big flash drive
Have you forgotten your laptop in a cafe and think that if no one knows your password from your favorite dozen / makosi, then he will not be able to read your files?
In vain
Try to remove the disk from the laptop and connect it to the stationary computer with the second screw, see your files? I have bad news for you - other people's eyes will be able to see them too, in exactly the same way)
There is a very simple protection option - file encryption by pcm ( we are talking about EFS ), it will not work quickly, and not very reliable (if someone can change the password for your account, but more on that later)
– , VeraCrypt, BitLocker, Windows 10, Mac OS
100%, , , – .
, , , , , , )
, , ?
Trusted Platform Module ( – ), – / CPU, , , .
, TPM – manage-bde -status
, dell,, , . , )
,

:
–
. , , Mac Book, – , . – )
– Live CD (, ). , - cookies/ovpn/password.txt/*.config… / , .. .
: Live CD exe- , , ( ) . , , – ( Live CD)
( ) – , , 2-5
Windows Linux
Windows Vista ( SuSE) . , , . - , IE, CTRL+O, * explorer.exe . . , , , Windows 98
, - ( ) BIOS )
:
( 3 ) ( )
: , , , ? , .. !
, ?
: , , – ,
: , ( ). , , , . , . ? . + ?. , – , !
! – , ))
, () – , . -.
, , / ? -, , ? , - …
- , , - )
, , (.. - ). , .. GitHub/Google , , . – . -
(2FA)
, : , )
:
- - /
( SMS Google Authenticator)
:
Google – https://myaccount.google.com/signinoptions/two-step-verification
GitHub – https://github.com/settings/security
GitLab – https://gitlab.com/profile/account
: , facebook, vk, firefox, twitter, 2FA – )
, . , , . , , , )
?
, , https://haveibeenpwned.com/
, , , https://monitor.firefox.com/ , , - .
, https://t.me/dataleak , , .
–
, , , ?
? , , , , .
https://www.techradar.com/best/password-manager
. /, , .
https://qwertycards.com/, . , , ;)
- https://sansys.github.io/cryptocard/

, , . , , - , , - about:logins ? - , , , . , .
https://support.mozilla.org/ru/kb/ispolzovanie-master-parolya-dlya-zashity-sohranyon
, , – , , , , .
? .
, , - WannaCry, , .
± , , https://www.techradar.com/best/best-antivirus
( ), !
« », .. « - »
– , , ! . -, , . : . ? , , , … ?
, WannaCry , .. Microsoft , -. ,
, , , ? , ? .. - – ?
PGP, thunderbird.net
– , email, , .
.
, .
, , mailvelope.com
protonmail.com – . , ( ).
, : , , – .
gmail , , Facebook
PGP Facebook

? – - ( ), . – - /
fakemail.net ( temp/fake email) )
, email-relay, relay.firefox.com, Apple ID
– , . ( ) , «! 2 », , - , , .
– ? !
– , , ( ) . – , .. , – . 5 XSS . API ( PHP), 20-30 . sqlmap, ...
SQL- 500. – 5 . email- . , users – ( ), , .
, : , , . – ?
, – , .. – , , ( ) , , ?
? .
, , , ). – , , , ( ), , .
, , , ( – / , ), , , , ( – , )
, , , , , , , – , , 300. ( ) . – .
, $N ( ), – . , , , 10, - , . – , , , , .
: , email ,
, «» « »
,
– , )
, , - , ;)
,
, , , , )
Wi-Fi
, , – Wi-Fi, :
< + free>
+ /,
, , ,
«, »
-
- , OTP , ,
, .. , , / , , . HTTP ( ), HTTPS, HSTS ( )
– , DNS IP? DNS-, , Wi-Fi. . , MitM , , DNS , .. ± )
– Wi-Fi , :
VPN , - . : protonvpn.com WARP ( /)
DoH, , , )
DNS- - , 1.1.1.1 ( , - DHCP)
– nextdns.io, .
VPN Kill Switch ( -) – , VPN-, , VPN
/ , - -/, )
, Wi-Fi ? - provider-kvartira-123? ? ? / + Google Authenticator, - + , ?
, SID -, , , , - , HP-Laser Jet 5…
– ? mac-, + - airodump-ng , – , .
, , , Wi-Fi , … – , )
– ? ?
, , . , , ICQ Sniffer – , HTTP-, SSL, / . , VPN )
Phishing
, – , , :
- blogger.com
(-) , // , PDF/Word-, , , .
? , . - , – . MS Office LibreOffice PDF-, .
: « », « , » .., .. – - , «». , – . « №5 » , ? ,
, , , / .
. https://habr.com/ru/company/solarsecurity/blog/502576/
, nextdns – 30 ,// - – , !
. : site.ru, boss.name@site.su – , ), : , , , – . , bank.ru?redirectTo=/page10.
redirectTo , . Open Redirect, . , , - ( ). – , 10 ,
//- ? «, ! , , , , , ? !».
N … , , setup.exe 550 , … , - . setup - , – , . windows , Virtual Box.
100 , ? – , - . : ( , «») – - - )
? .
, , ?

https://www.virustotal.com –
GitLab
, , - - , ,
// /., – .
, , . – 2019.mynet.ru. *.mynet.ru – , 2019.mynet.ru . , .
, : Chrome - Firefox – . , .. FB , -.
(//) , . , .. - , https://mybrowseraddon.com/useragent-switcher.html.

uBlock - , .. https://github.com/gorhill/uBlock
( ) NoScript js-. , , JS, , , . , .. - XSS , ..
, - ? ? , , .
, cookies, Cookie AutoDelete, . , . , – /, ;)
: , , . . CanvasBlocker . , , , , .
, .. , habr mitm , -
– . , , . , N , , . History Cleaner
– - ?
, , . . startpage.com – , , ( ), , )
, , ! , . HTTPS EveryWhere – URL HTTPS, , HTTP .
, 100 , ? - , - ( /), - , ( /). , - , ? Auto Tab Discard – , Cookie AutoDelete , . , , « ».
/ , , . , . « » , . , , , – . )
, VPN, , , .. - . ! : /, , , , , , – ? , , .. = .
Information technologies today are an integral part of each of us, a part of our personal and corporate life. As a consequence, proper hygiene must be present in it too. It is worth remembering that your infrastructure is protected only as much as the weakest part of it is vulnerable.
There is a stupid bold recipe: make a nude photo, put it in the root of the disk, in the home directory, in the mail, in the cloud, in the phone and think about protecting it)
Perhaps after that you will be like this:
