In this case, several UEFI images were detected with malicious code already embedded. This code has only one function - it adds the file contained inside to the Windows startup folder. The further attack develops according to a typical cyber espionage scenario, with theft of documents and sending other data to C&C servers. Another unexpected nuance of this study: the malicious code in UEFI uses sources that were previously publicly available as a result of hacking into the infrastructure of the Hacking Team company.
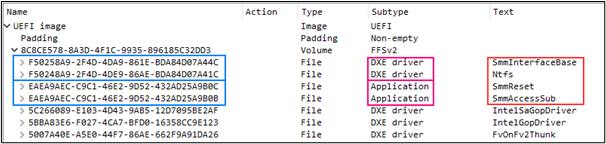
Four modules were found in infected UEFI images as shown in the screenshot above. Two perform service functions, including those responsible for launching malicious code at the right time (right before the operating system boots). Another is the driver for the NTFS file system. The main malicious module contains the IntelUpdate.exe file, which is written to the SSD or hard drive in the Windows autorun directory.

Two service modules and a driver appear to be borrowed from the Vector-EDK code. This is a bootkit, the source code of which was made public after a massive data leak from the Hacking Team company. This organization, which develops methods of attacks on computer systems commissioned by government agencies, was itself hacked in 2015, as a result of which both internal correspondence and an extensive knowledge base got into the public domain.
Unfortunately, the researchers were unable to identify the UEFI infection method. Among several dozen victims of MosaicRegressor, only two affected computers had a modified base loader. If you rely on the same leak from the Hacking Team, then it offers manual infection by connecting a USB flash drive to the computer, from which UEFI is loaded with a makeweight. The deleted UEFI patch cannot be ruled out, but it would require hacking the download and installation process of updates.
The spy module installed on the attacked computers connects to the command center and downloads the modules necessary for further work. For example, one of the mechanisms takes recently opened documents, packs them into an archive with a password, and sends them to the organizers. Another interesting point: both traditional methods of communication with control servers and work through a public mail service using the POP3S / SMTP / IMAPS protocol are used for communication. Both the loading of modules and the sending of data to the organizers of the attack take place via mail.
What else happened
The Register recalls the end of support by the mail server manufacturer Microsoft Exchange 2010. The authors of the article note that 139,000 servers are currently available from the network, and security updates will soon be discontinued. Threatpost writes that a vulnerability discovered in January in the Microsoft Exchange control panel (versions 2013–2019) has not yet been closed on 61% of servers.
A backdoor was found in the HP Device Manager software for managing thin clients of this company , or rather, a service account forgotten by the developer.
Despite Google's efforts, Joker malware variants continue tofrom time to time undergo verification of the Google Play app store. The malware, as a rule, subscribes victims to paid services without their knowledge.