
Our Incident Response Team is tracking an unprecedented number of Emotet malware infections. Emotet has three times our previous record of active concurrent investigations. This post will look at indicators of compromise, measures to address them, and how Varonis can help you detect and stop Emotet during each phase of an attack.
Emotet Review
After a long hiatus, in spring 2020, the TA542 attacker (also known as the “Mummy Spider”) returned with a new massive spam campaign that uses multiple botnets around the world and uses an improved arsenal of malware.
Emotet, originally known as a banking Trojan, was first detected in 2014. Its main goal was to intercept banking credentials using man-in-the-browser attacks. To date, Emotet has evolved into a self-updating, versatile malware suite that also acts as a downloader for payloads like Qbot and Trickbot (which Ryuk and Mimikatz download in turn).

Since Emotet is polymorphic, specific IOCs (Indicators of Compromise) such as downloader URLs, C2 IP (Command and Control IP) / port combinations, and spam patterns change frequently. This feature makes rule-based detection a game of cat and mouse, exacerbated by the fact that there are three different Emotet botnets, each with their own infrastructure. You can find the wonderfully detailed Emotet IOC daily journal maintained by the Cryptolaemus team.
Once online, Emotet uses a variety of methods to distribute, escalate, ensure resilience, and move data outside of the company. In addition, Varonis threat behaviors can detect early signs of an Emotet breach as well as abnormal post-intrusion behavior.
Primary compromise
The Emotet infection vector is a phishing campaign supported by three global botnets: Epoch 1, Epoch 2, and Epoch 3 (E1, E2, E3 for short). Each Epoch has its own C2 framework, update schedule and spam patterns. A phishing email usually contains macro-enabled attachments or malicious links designed to infect new hosts and add them to your cluster.
During the latest wave of infections, malicious Emotet emails contained password-protected ZIP attachments . This is done with the expectation that email filters will pass the password-protected archive without scanning and will not detect malicious macro-enabled documents. This approach is called "Operation Zip Lock".
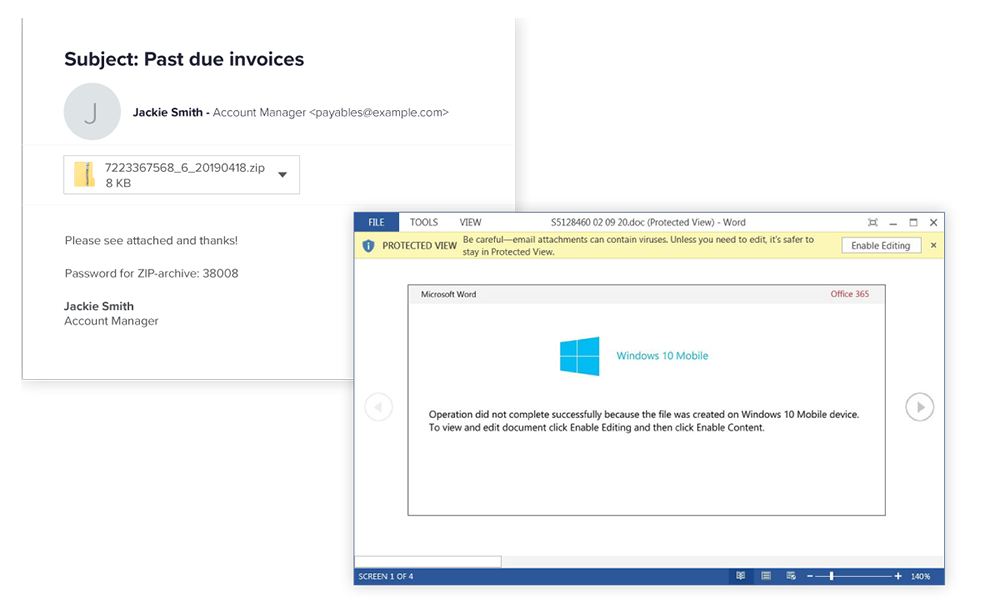
The password is usually indicated in the body of the letter in plain text, for example:
Zip file attached to email: Very urgent information from 09/24/2020.zip
The password for the document is LQWMFXu
When fixing a spike in the number of letters with password-protected ZIP attachments, it is recommended to place such letters to quarantine. However, keep in mind that Emotet also uses Directly Attached Office documents.
Malicious spam campaigns were detected in many languages: English, Dutch, French, German, Italian, Japanese. Epochs are probably geo-referenced (for example, E3 is common in Japan).
Building on success
Emotet outputs stolen emails and contact lists of victims to a C2 server using HTTP POST requests . The botnet then uses this data to impersonate the sender and "reply" to existing conversations. This can be done either by changing the sender, or, if there is full control over the victim's machine, by sending an email directly on behalf of the victim.
This technique makes Emotet spam very persuasive and increases the likelihood that a new victim will open a malicious attachment.
Varonis monitors Microsoft Exchange and Exchange Online mailboxes and can detect malicious file attachments that match a dictionary of known patterns used in Emotet spam patterns. With the help of the Edge module that controls the proxy, it is possible to detect when a user clicks a link in the body of an email, which leads to the download of the malicious Emotet downloader.
Varonis analyzes all actions with a mailbox (send / receive / open / delete, etc.) and this allows you to quickly identify accounts that have been compromised and started sending spam campaigns (internal or external). A User Behavior Profile is generated across all monitored platforms: minor deviations in mail behavior, combined with suspicious logon events, network connections, and data access, provide accurate alerts with fewer false positives.
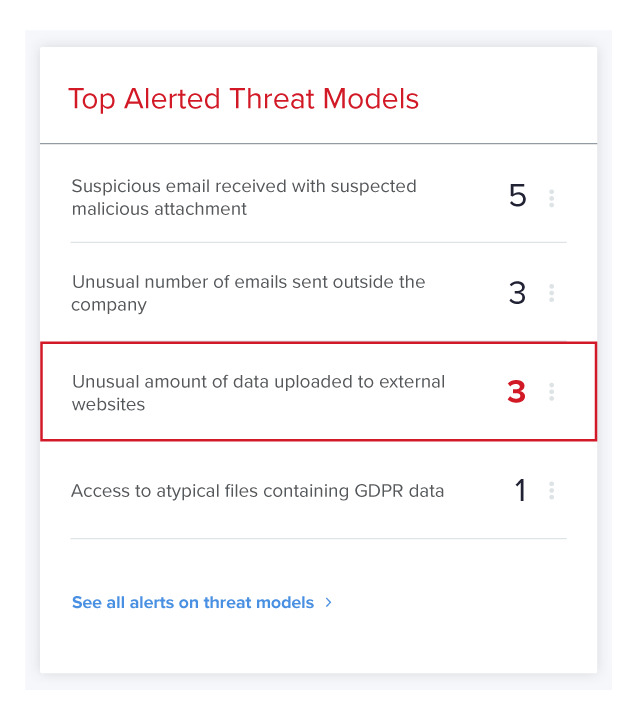
Varonis Edge can detect theft of email messages and Outlook contacts. In practice, we have seen this data output thanks to the company's proxy coverage - Emotet used HTTP POST commands. If a DNS covert channel is created in the future, it will be covered by DNS-based exfiltration models.
Connections to C2 servers can be discovered in several ways. First, if a connection is made to a domain with a bad reputation, Varonis will warn and flag those connections. Second, Varonis detects when attackers are hiding their traffic in a large number of connections ("white smoke") using the domain generation algorithm (DGA). Third, Varonis behaviors are detected when attackers use DNS as a covert channel to hide their commands or data transfers in the form of DNS queries. Finally, Varonis will alert you to unusual web activity, such as the use of new or unusual user agents, abnormal or first access of an account to the internet, or unusual uploading of data to an external resource.

Spread
Emotet has many modules that can be dynamically loaded from its C2 server to extend malware functionality. There is a spam module, an email theft module, a banking module, etc.
One of the modules to watch out for is the distribution module , which allows you to do this with SMB exploits such as EternalBlue (MS17-010) and by accessing hidden administrative balls (ICP $, C $ and Admin $). We recommend patching all machines that are still vulnerable to EternalBlue and disabling admin shares.
Although SMB is the primary distribution method for Emotet, researchers at BitDefense have discovered a new distribution technique that scans Wi-Fi networks using the WlanEnumInterfaces function in wlanAPI.dll and tries to propagate to connected devices.
Malware will try to crack password-protected Wi-Fi networks using the built-in password list. If successful, it forwards the SSID and password combination of the network back to the C2 server and makes another brute-force attack, this time aimed at clients on that network.

Privilege escalation
Attackers obtain credentials from privileged accounts using well-known open source tools, looking for passwords stored in plain text, and collecting credentials from Active Directory. After obtaining administrator credentials, an attacker can add one or more users to the Domain Admins group.
By monitoring file system activity, Varonis quickly determines when known penetration tools are being saved to disk or when a user searches file shares for files with passwords or other sensitive data. Any user account usually has access to much more data than it should, so such searches are often fruitful - more on that below.
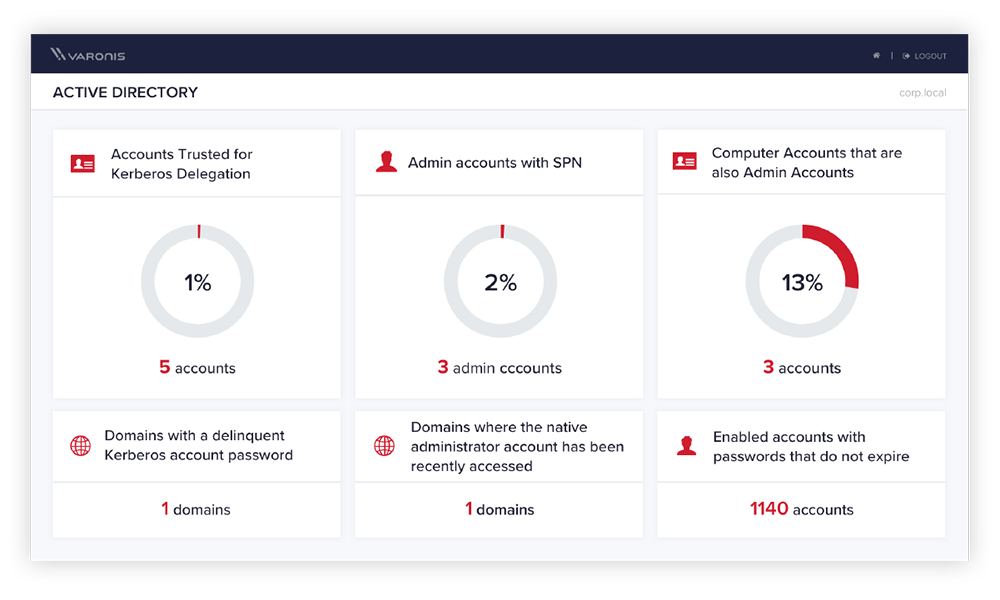
Emotet is well known for downloading other types of malware like Ryuk , which in turn downloads hacking tools like Mimikatz to collect credentials and escalate privileges. Varonis analyzes activity in Active Directory to detect credential collection (such as Kerberoasting) and other attacks. To reduce the likelihood that these attacks will be successful, Varonis displays potential weaknesses (for example, administrative accounts that have SPNs) in the control panel. Reducing the attack surface in AD and on file shares makes life harder for attackers. Varonis will also notify you when the account is added to the admin group.
The Last Frontier
If signs of infiltration, proliferation, and elevation of privileges have not been noticed, it is important to ensure the critical level of protection of the largest data stores by protecting Windows and UNIX servers, NAS, SharePoint and Exchange devices (both on-premises and in Office 365).
Varonis analyzes file system activity across platforms that provide auditing through their APIs, such as Office 365 and NAS devices from NetApp, EMC and others. On platforms where enabling native auditing might cause performance issues or insufficient auditing, such as Windows, UNIX, Exchange, and SharePoint, Varonis uses its own battle-proven agents to capture operations.
If a user begins to access an unusual amount or amount of data compared to their normal behavior, Varonis will detect this through one or more behavioral patterns. If the user starts encrypting files, this will also be detected - many of our customers automate the handling of such an incident using scripts, disabling the account and killing active sessions.
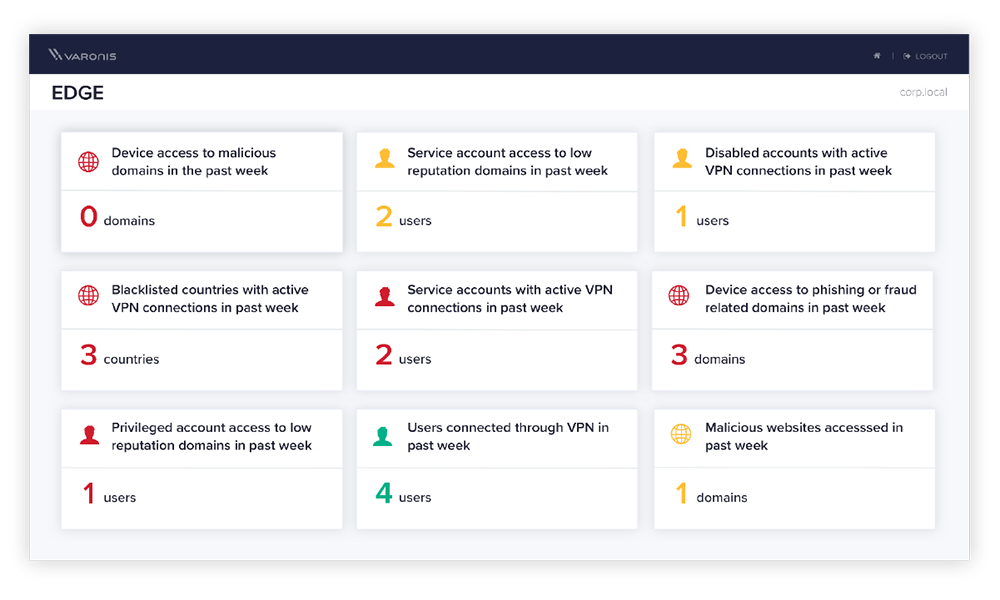
Varonis identifies where data access is redundant, that is, users have access they don't need. There is a possibility of automatic removal of redundant access rights (both direct and by removing an account from security groups). Restricting access to sensitive data will reduce risks and make it difficult for any attacker to work.
Conclusion
The Emotet botnet is the world's largest and most sophisticated malware distribution weapon. It's difficult to predict which weapon the TA542 will use next, or which APTs will share their weapons. What we do know is that Emotet campaigns come in spikes and vary greatly in nature, so it is extremely important to have a layered approach to protection, including patch management, anti-phishing training, mail filtering, user device protection, and the approach. data-centric on a par with the infrastructure as a whole.
Comprehensive detection can give your organization an edge, but reducing the attack surface (increased security) is just as important. Varonis' data protection technology builds detective control rings from data to Active Directory, DNS, VPN and proxies. Varonis also highlights potentially vulnerable accounts and easily accessible data so you can fix the situation before attackers take advantage of it.