Introduction
One way to make some internal (home) services available from the Internet is through a VPN. You can, of course, publish individual ports via ssh, but for more complete communication it is better to use other solutions. I already wrote about ZeroTier, and about OpenVPN, and received reproaches that I undeservedly forgot about Wireguard ...
One way or another, I began to miss the VPN client (including Wireguard) on a stand-alone server, I needed to connect (in this case with vNet in Azure, although this is not essential) the entire home network with several resources. And I decided that it was time to do it through a router, for a full-fledged site-to-site.
Although Keenetic has learned to support Wireguard on new firmware, I haven't found one for the old Ultra. It didn't work with OpenWRT either (there is for Ultra II, but my model is too old). So I decided it was time to upgrade. And, since Mikrotik RouterOS rolled out beta version 7 with Wireguard, I decided it was time to study this miracle.
The reality turned out to be somewhat more complicated than I expected, but everything worked out. And now I will describe the main points that I could not find anywhere, and which I had to reach myself.
Highlights
I took MikroTik hAP ac2. The model is old, no frills, but it does everything it needs.
Although I had never dealt with Mikrotik before, I launched it quickly enough. There were some difficulties with the fact that in setting up the DHCP Server it was not enough to set the Network for IP addresses to be distributed from this network. It turned out that there is also a separate IP Pool. But these are trifles. So pretty quickly I started configuring Wireguard.
Of course, nothing worked. Moreover, "on the other side" I did not even see incoming packets.
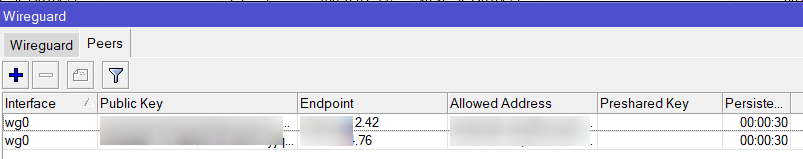
Then I noticed that only the IP address is indicated in the Endpoint field, but there is no port. I tried to specify it explicitly, but it broke off. The field turns red and fails validation.
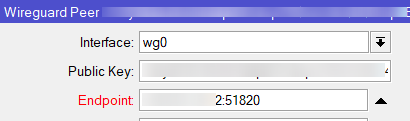
. , RouterOS, , , . -, , . , , . .. /interface wireguard peers . add . interface, public-key allowed-address. , :
add allowed-address=192.168.66.128/25,10.10.0.0/16 endpoint=66.166.166.42:51820 \
interface=wg0 persistent-keepalive=30 public-key="=".. . , .
, wg0 web-. WinBox, . , -, . , Linux IP . . :
/ip address
add address=192.168.66.253/24 interface=wg0 network=192.168.66.0That's all. There are instructions on the net how to install Wireguard on Mikrotik with OpenWRT. But as for me, this is a perversion. But you can raise it in your native RouterOS in a few minutes. When you already know how. Works great, no complaints at all.
PS Of course, I changed the addresses. But allowed-address=192.168.66.128/25also add address=192.168.66.253/24not a mistake. I just have a connection to two servers. Half of the class C network on one server, half on the other.
PPS Why Wireguard and not OpenVPN? For example performance:
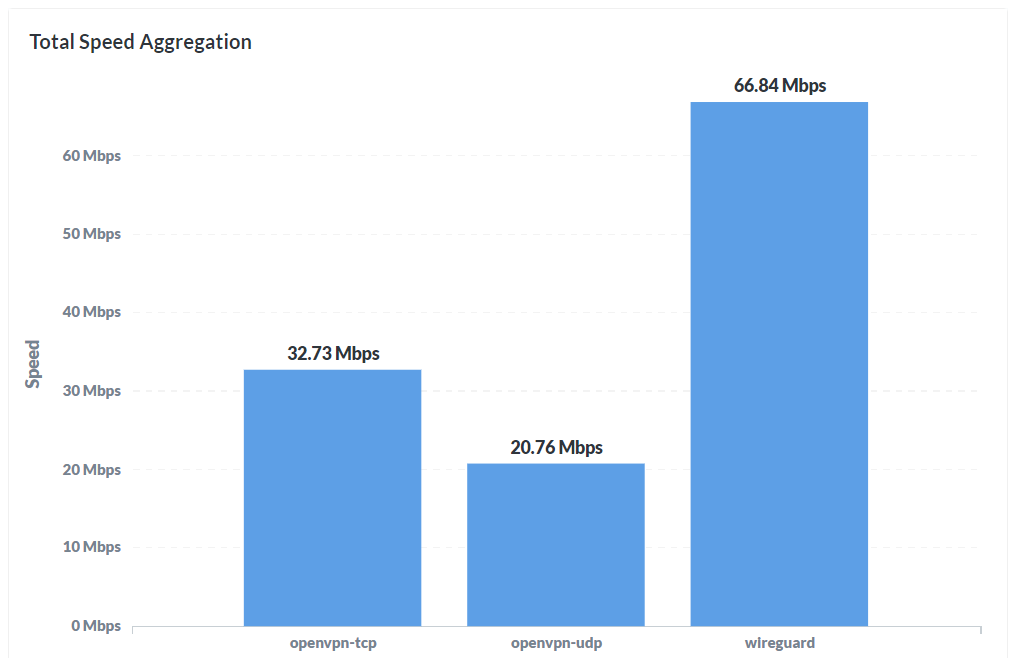
https://blog.entrostat.com/openvpn-vs-wireguard-network-performance-tests/
And also the ease of setup and a little bit of trivia.