With network access to a domain controller on the corporate network, an attacker can change the password on the server and gain complete control over the corporate infrastructure. A multi-stage attack on less critical Windows servers is also possible with the same end result. The unofficial name - Zerologon - was given to the vulnerability due to the specifics of the attack: it starts with attempts to establish a connection using a sequence of data of all zeros. An incorrect implementation of the AES encryption algorithm allows you to log in to the server from a maximum of 256th attempt, which in practice takes a couple of seconds.
The vulnerability was tackled outside of Microsoft last week. An unofficial patch for Windows Server 2008 R2 has been released. There is also an official patch for this OS , but from January this year it will be installed only by those who have purchased the extended support package for the old release.
In addition, the problem was solved in the Samba code. The vulnerability is relevant only for those installations where the Samba server is used as a domain controller. Since this construction assumes following the specifications of the Netlogon protocol (and the error is in them, this is not an accidental software bug), Samba was also among the victims.
Sources:
- Microsoft Vulnerability Overview Bulletin
- Instructions for system administrators
- , Secura
- Windows Server 2008 R2
- Samba
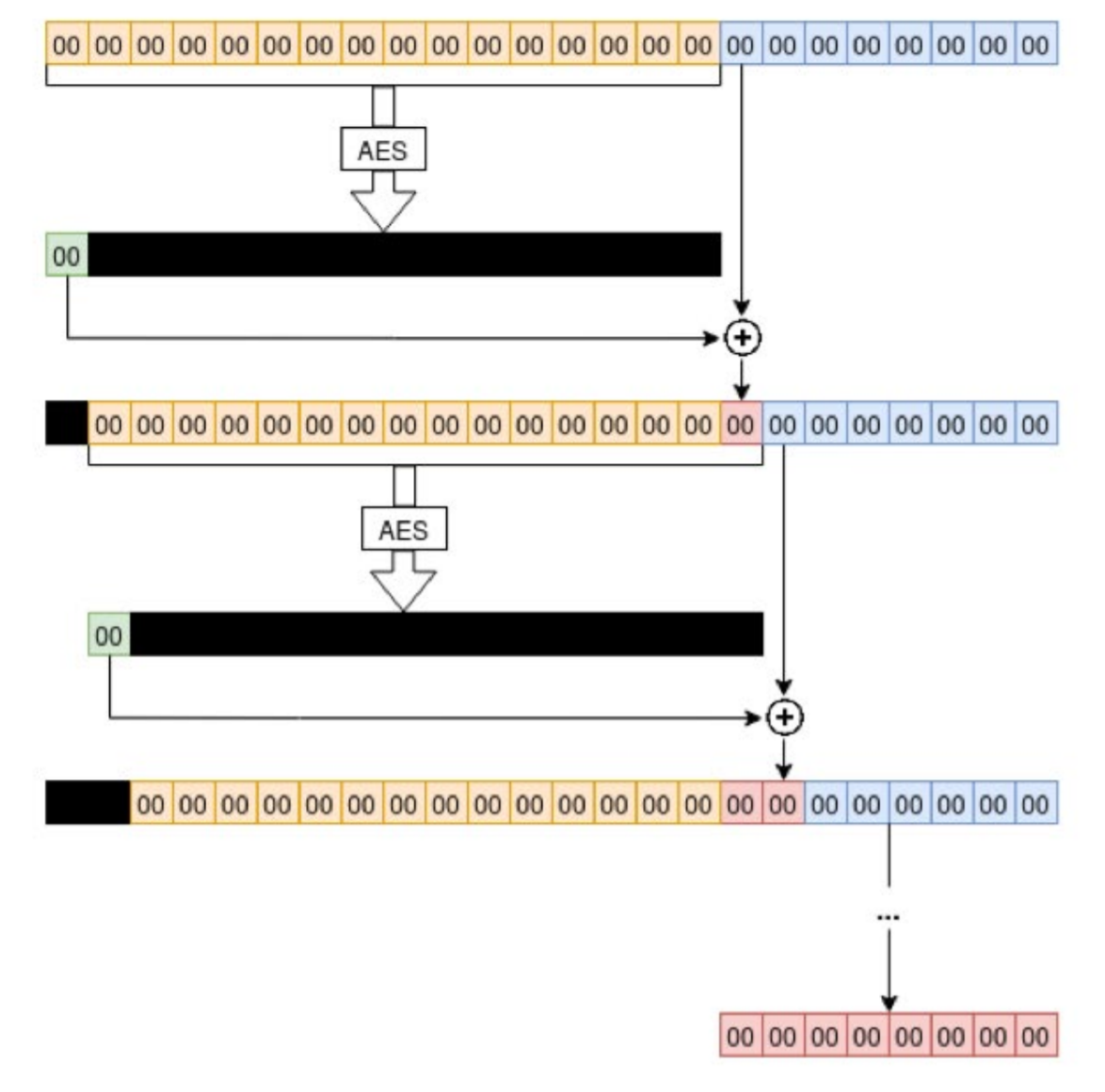
The seriousness of the problem is underscored by the directive of the American Cybersecurity Agency on the need to urgently roll a patch in the infrastructure of federal agencies. As follows from the description of the vulnerability provided by the pioneers - Secura, the source of the problem was the incorrect implementation of the AES encryption algorithm in the non-standard CFB8 mode .
Authorization of two systems via the Netlogon protocol involves the exchange of two arbitrary numbers of 8 bytes, the so-called session keys. The AES-CFB8 encryption process uses these random keys and an initialization vector (IV), another unique 16 byte sequence. More precisely, it must be unique: the Netlogon spec states that IV always consists of zeros.
Researcher Tom Turworth discovered the following: if you give the algorithm as input a session key of eight zeros and make 256 login attempts, in one of them the combination of a zero key and a zero initialization vector will give a zero ClientCredential. Knowing this, we can log in to the server, like any computer in the domain. At this stage, the attacker still cannot exchange encrypted data, but this is not necessary: the server will easily establish a session without encryption, apparently in order to support old operating systems. As a result, it becomes possible to log in as an administrator of the attacked server and change the password in Active Directory.
In practice, the attack process requires additional steps, but if you have network access to the domain controller (when accessing the local network), they are quite simple. Two weeks ago, an exploit for the vulnerability was made public, and there are already reports of real attacks on Windows servers.
Judging by the data from Microsoft's instructions for administrators, the vulnerability will be closed in two stages. On the first, starting from August 11 (if you installed the patch, of course), old systems that can only connect to the domain using the vulnerable protocol will be able to do this. In this case, the well-knownmethod of attack, but there may be other, more sophisticated methods. In the second phase, starting February 9, 2021, supported servers will drop connections without encrypting data by default. In other words, some organizations add headaches to administrators to identify and update legacy systems. In any case, it is necessary to close the vulnerability, the cost of hacking is too high.
What else happened:
The source codes of Windows XP and other old Microsoft operating systems have leaked . The archive of 43 gigabytes appeared in the public domain last week. The completeness and quality of the leak has not yet been properly appreciated. Perhaps this will lead to the discovery of new critical vulnerabilities in Windows XP, which no one will fix anymore. On the other hand, even the known bugs of this OS make it insecure, the leak in this case does not change anything.
A critical vulnerability in Firefox for Android allows you to remotely launch a browser that will open an arbitrary URL. The release of desktop Firefox 81 and ESR 78.3 closes another set of critical bugs.
DiscoveredTrojan for Android that intercepts messages with one-time authorization codes and steals data for accessing the Telegram messenger and Google services. Another banking Trojan for Android uses TeamViewer to remotely control a device.
Sophos is investigating a scam campaign offering “early access” to iPhone 12. Scam starts with iMessage and ends with credit card theft.
Check Point Software has published a study on a critical vulnerability in the Instagram app for iOS and Android. Arbitrary code execution was made possible by a bug in the library that decodes JPEG images.