
SAM Seamless Network reports that over 200,000 companies that use SSL VPNs out of the box are vulnerable to attacks like MitM. Attackers, when connecting, can provide a valid SSL certificate and trickery into the company's corporate network. An example of an attack is presented under the cut, as well as recommendations for securely setting up an SSL VPN.
“We quickly discovered that the default SSL VPN was not as secure as it should be, vulnerable to MitM attacks,” said Niv Hertz and Lior Tashimov of SAM IoT Security Lab.
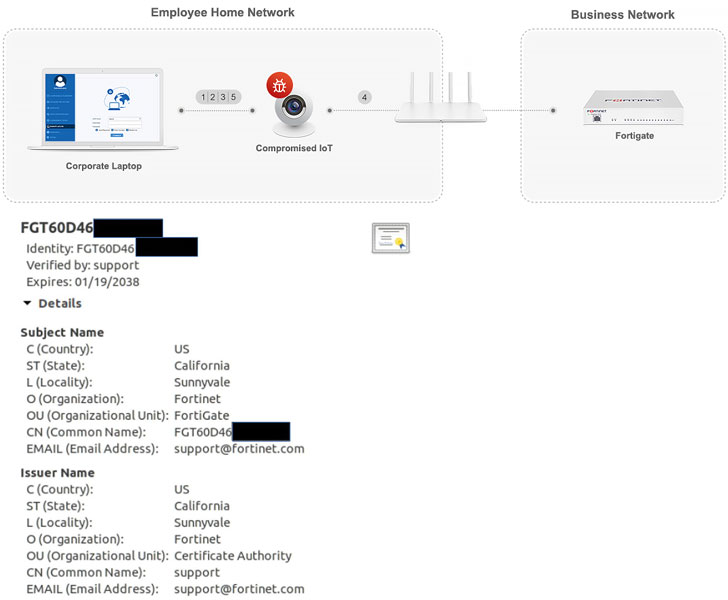
According to them, the SSL VPN client only checks if the certificate was signed by Fortinet (or another trusted CA). Thus, an attacker could provide a certificate intended for another FortiGate and launch a man-in-the-middle attack.
To simulate the attack, the researchers used a compromised IoT device that launches a MitM attack shortly after the VPN client initiates a connection. The device then steals credentials before transmitting them to FortiGate and compromises the authentication process.
SSL certificate verification, which helps to authenticate a website or domain, works in a slightly different way. The process checks the validity period of the certificate, the digital signature, the CA that issued this certificate, and the Subject field of the certificate. If the certificate is valid, its digital signature is correct, the certificate was signed by a trusted CA, and the Subject field contains the name of the website or domain - the connection is allowed.
The problem, according to researchers, is companies' use of self-signed SSL certificates that come with the hardware by default.
Given that every FortiGate comes with a Fortinet-signed certificate, this certificate can be tampered with by a third party, allowing attackers to capture traffic to FortiGate and decrypt its contents. Below is a video with an example of decrypting traffic transmitted by a VPN client, which resulted in the receipt of the user's password and his OTP.
The main problem is that although the serial number of the device is used as the Subject field in the certificate, it seems that the client does not check the server name at all, which allows such attacks to be carried out.
Currently, FortiGate issues a warning when using an embedded certificate: "You are using a standard embedded certificate that will not be able to verify the server's domain name (your users will receive a warning)." It is recommended that you purchase a certificate for your domain and use it. "

In a statement to The Hacker News, Fortinet said, “The safety of our customers is our top priority. This is not a vulnerability. The devices are designed to be easy to operate out of the box and then customize to individual customer needs. ”
Fortinet also strongly recommends adhering to existing documentation and paying attention to all warnings during the configuration process to avoid putting the company at risk.
Recommendations for hardening SSL VPN are as follows:
- Use external authentication servers;
- Don't use the built-in default SSL VPN certificates;
- Use multi-factor authentication;
- User certificates can be used as a second factor;
- Determine the minimum supported TLS version and cipher suites;
- Carefully create security policies and profiles for remote users.
You can read more about these security measures here .
We, as an integrator specializing in Fortinet solutions, closely follow all the news related to it, and focus on the most important and interesting. In order not to miss anything, subscribe to our updates in social networks:
→ Vkontakte group
→ Yandex Zen
→ Our website
→ Telegram channel