
On Habré, the issue of information security of smart devices has been raised more than once. In an effort to quickly release a new model into the series, many manufacturers are paying insufficient attention to the digital protection of their gadgets. As a result, this leads to curious situations - for example, a discarded smart light bulb can provide attackers with access to a corporate WiFi network.
The problem is not only with the bulbs. They hack smart refrigerators, thermostats, and even entire cars. But this time a very harmless device - a coffee maker - was hacked. Martin Chron, a researcher at Avast, studied the software and hardware of the Smarter coffee machine. The results of the study are very interesting . Read more about them under the cut.
What is this device?
The $ 250 device connects via WiFi to a phone with an app. Accordingly, you can remotely set different operating modes of the coffee maker, select the types of drinks. In general, this is a common device for its class.

Martin Chron, having purchased the device, drank coffee and decided to assess the security of Smarter. It immediately turned out that the device is susceptible to hacking out of the box.
How bad is it?
As it turned out, when turned on, the coffee maker works as a WiFi hotspot. This is necessary to connect the gadget to the application on the user's smartphone. The problem is that the connection is not secure. There is no encryption at all, so it was not difficult for Martin to learn how the coffee maker and smartphone interact wirelessly.
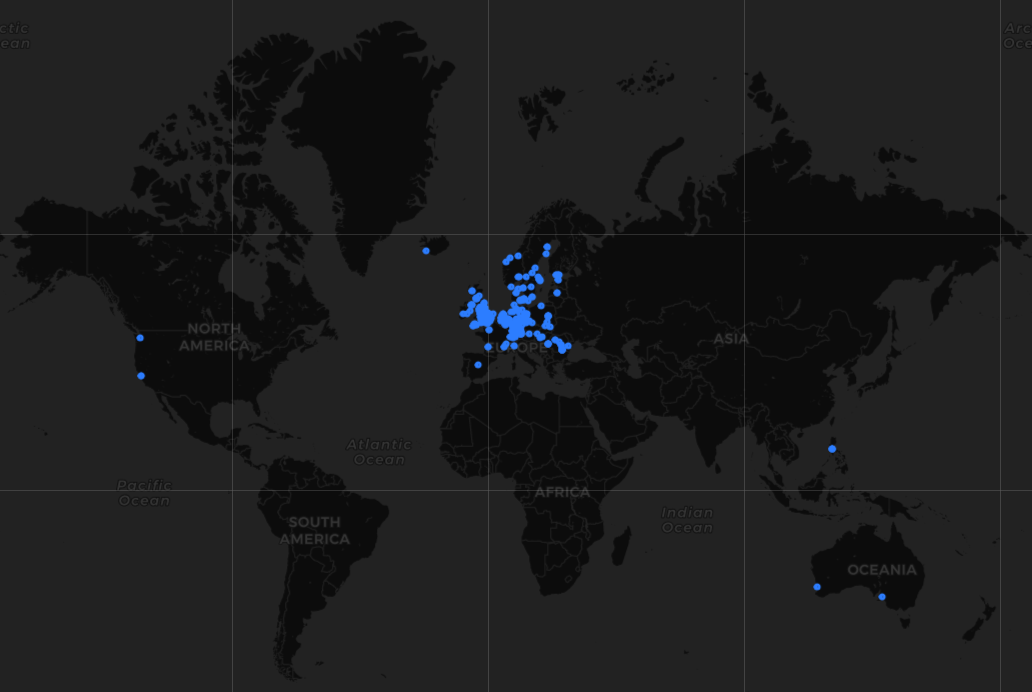
Vulnerable Smarter coffee makers around the world
He found out that the firmware update of the device goes over the air. It is saved directly in the application, and then transferred from the smartphone to the coffee maker.
After that, Martin reverse-engineered the firmware, learning that it was unprotected data that was immediately loaded into the flash memory of the coffee machine. In general, you can download anything you want. But there is a small problem - you need to know which commands the device will understand.
To do this, Martin took apart the device and examined its insides.
Iron in Smarter
The main thing that needed to be found out is what processor is used in the coffee maker. By the way, even 10 years ago, a phrase like “coffee maker processor” would have puzzled most readers. But now it is in the order of things.
So, after disassembling the coffee maker, Martin saw this.
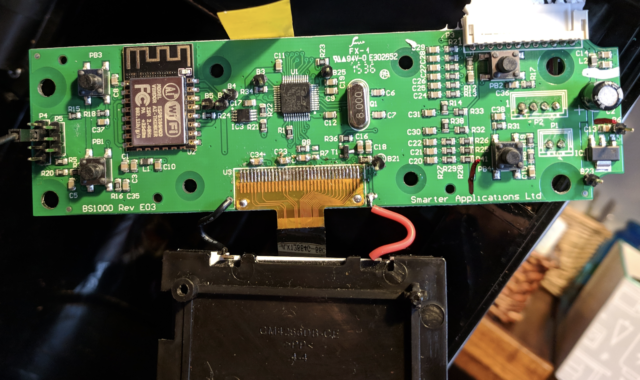

1 - ESP8266 with AT modem firmware, 2 - STM32F05106 ARM Cortex M0 - main chip, 3 - I2C EEPROM, 4 - debug ports and software interface
After examining the hardware, the researcher realized that he can use the most important functions, such as activating heating, installing an update (or whatever the coffee maker considers to be an update), as well as activating the beeper. Below you can see exactly which functions can be accessed.

Now the researcher had enough information to write a script in Python to install third-party software that cheats the coffee maker. The device thinks it is undergoing a scheduled update.

Well, after the "update", you can please other users of the coffee maker with messages like this.

The operation of the device can be completely blocked by using various functions. Any intruder within the range of the coffee maker's WiFi can do this. Imagine, for example, an office with such a device and visitors who can do whatever they want with a coffee machine. What exactly? For example, this:
In order to do all of this, Martin modified the firmware of the coffee maker he was studying. He added it to the Android application (with iOS, everything would be a little more complicated). And then the only thing left to do was to "update" the device with custom firmware.
When turned on, the coffee maker always broadcasts the SSID with the value "Smarter Coffee: xx", where XX is the part of the device's MAC address.
What's next?
You can lock the coffee maker and demand a ransom for unlocking. Of course, in this case, you won't get much, but you never know, suddenly, in the company under attack, there are many of the same type of coffee makers and all of them can be disabled at once.
With more effort, an attacker could program a device to attack an internal network, including a router, PCs, laptops, and all other devices that are connected to that network. Moreover, this can be done without any special problems - hardly anyone will pay attention to the activity of the coffee maker.
And by the way, Martin's custom firmware blocks all subsequent ones - it will not work to update the coffee maker in a standard way. You need to either connect to the service port or update the firmware in some other way.
How dangerous is all this?
If we talk about coffee makers, then not very much. You can simply refuse to use the products of Smarter or other companies (it is unlikely that Smarter is the only one that does not use encryption).
But if you imagine how many different smart devices are now working around the world without being protected, then it becomes uncomfortable. All these smart locks, eyes, bulbs, telephones, thermostats, kettles, etc. If attackers take them seriously, the consequences can be dire. From the trivial hacking of a device in order to play around, to stealing property or obtaining corporate secrets, all this becomes possible for cybercriminals.
How to fix the situation? There are several ways:
- Manufacturers are beginning to pay attention to the problem with information security and protect their devices. This is the most unlikely way, because, as mentioned above, companies are not interested in maximizing device protection, but in getting their products to market faster, making them user-friendly.
- Do not use smart devices in offices, homes and apartments. This is unlikely, because smart gadgets have become part of our everyday life and it is unlikely that a person who began to actively use them will voluntarily refuse them.
- Use third-party methods and methods of protection. For example, connect devices to virtual LANs when using an isolated SSID from the computer network.
How do you protect your smart devices from hacking? Perhaps you have encountered similar cases? Let's discuss in the comments.
