
In truth, technical methods of unlocking mobile devices are not an end in themselves for a computer forensic scientist. Its main task is to access data stored in memory. Therefore, if the researcher manages to extract information from the device bypassing the set PIN-code or picture password, the need for unlocking usually disappears. On the other hand, if an expert still extracts data at the physical or logical levels, then he can get information that will help him to unlock the device in the future. In this article, Igor Mikhailov, a specialist at the Group-IB Computer Forensics Laboratory, continues to talk about the ways that forensic experts can bypass the blocking of a mobile device. The first part can be viewed here...
: , . — , . , . , .
Of course, the technical capabilities for unlocking are closely related to the characteristics of a particular device: its manufacturer, model, operating system version, installed security updates, etc. A forensic scientist should consider these points when trying to unlock a mobile device. Let's start with Apple.
Unlock Apple Mobile Devices
Method 21: using hardware and software systems GrayKey and UFED Premium
Now on the market there are two software and hardware complexes designed to select PIN codes and extract data from blocked Apple mobile devices.
The first device is the Grayshift GrayKey [23]. According to the developer of the device, it can be used to recover the PIN code of almost any iPhone with any version of iOS.
This is how one of the famous GrayKey images presented to the public looks like:

Only two pins are not enough to connect the investigated devices. I'll explain why below.
The second password cracker is Cellebrite's UFED Premium, announced on June 14, 2019 [24].
Probably, UFED Premium can exist in the form of a set of programs (by analogy with UFED 4PC) or specialized hardware device (by analogy with UFED Touch).
Both devices are available only to military and police structures in a number of countries. Information about the capabilities of both complexes is limited. This is due to the fact that Apple is strongly opposed to the extraction of data from its devices and is constantly introducing new developments in its products to prevent forensic experts from extracting data from such devices.
It is known for certain that the companies GreyShift and Cellebrite take some time (from several weeks to several months) in order to bypass new developments by Apple that prevent access to the memory of locked mobile devices.
The PIN code of Apple mobile devices can be cracked using a brute force attack. If successful, such password selection takes less than a day, but it can take six months or more. Accordingly, connecting only two mobile devices to GrayKey seriously limits the researcher's options, given that PIN recovery is time-consuming.
Security recommendation: digital passwords 4-6 characters long are relatively acceptable in terms of search terms. Even 7-8 digits already greatly complicate the task of brute-force password brute-force, and the use of a strong alphanumeric password makes this task unsolvable in a reasonable time.
Method 22: using the IP Box hardware complex
To recover the PIN code of locked Apple mobile devices running iOS 7-8.1, you can use a family of hardware devices that usually use the IP Box combination in their names. There are many hardware implementations of such a device, ranging from hundreds to thousands of dollars. For example, a variant of such an implementation is the IP Box iPhone Password Unlock Tool [25]. This is how the result of PIN code recovery using this device looks like:

A number of companies that develop software for mobile forensics have implemented this functionality in their designs. Susteen went further and implemented a similar device in the form of the Burner Breaker robotic complex (the PIN code of the locked mobile device is picked up by the robot) [26]:

As stated by the manufacturer of IP Box iPhone Password Unlock Tool, it will take no more than 17 hours to select a 4-digit PIN code for a locked Apple mobile device.
Security tip: Your iOS 7 device needed to be replaced a few years ago.
Method 23: PIN recovery
For younger iPhone models (up to iPhone 5c inclusive), it is possible to brute force the PIN-code by brute force attack. For example, this can be done using Cellebrite's UFED Physical Analyzer or Elcomsoft's iOS Forensic Toolkit.
When a device is in DFU mode, it is loaded with a series of exploits that allow it to take control of the device before launching its own operating system.
The appearance of the iOS Physical window with data extraction and PIN recovery options for a connected iPhone 4:

When you select the "Password code recovery" option, the PIN-code of the locked device will be selected. The result of PIN code recovery looks like this:

Prospects for extracting data from blocked Apple mobile devices
On September 27, 2019, a Twitter user under the pseudonym axi0mX announced the checkm8 exploit. He exploited a vulnerability that compromised information on millions of Apple devices (from iPhone 4s to iPhone X) [27].
Due to the fact that on iPhone 4S, iPhone 5, iPhone 5C there is no hardware ability to limit the number of attempts to brute-force the PIN-code of a locked device, these devices are vulnerable to software that can be used to sequentially brute-force the PIN code values in order to recover it.
The August release of Elcomsoft IOS Forensics Toolkit contains the implementation of such an attack for devices: iPhone 5 and iPhone 5c.
In addition, security researchers from the PANGU group reported a SEPROM vulnerability [28] in the A8-A10 chips (iPhone 6, 6s, 7), which, in theory, would also disable PIN guessing. Security
recommendation: Currently only A12 and A13 (iPhone XR, XS, 11, 11Pro) devices can be considered safe devices. Do not forget that if the old vulnerable device is connected to the same iCloud with the new secure one, then through the old device you can get iCloud data from the new one.
Elcomsoft IOS Forensics Toolkit brute-force:
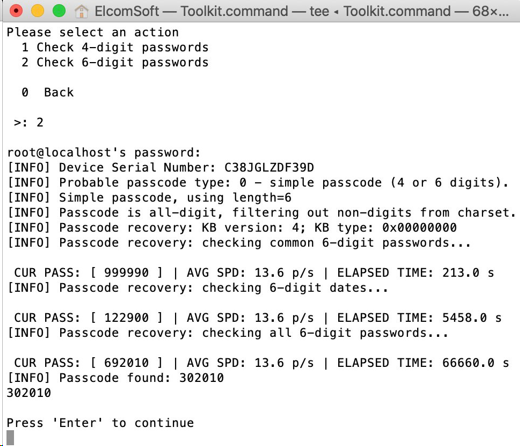
Method 24: using lockdown files
If an Apple mobile device has been connected to a Windows or MacOS computer at least once, iTunes will automatically create files on it that will help a researcher retrieve data from a locked device.
These files are located in the following paths:
- Mac OS X: \ private \ var \ db \ lockdown
- Windows 2000 and XP: C: \ Documents and Settings \ All Users \ Application Data \ Apple \ Lockdown
- Windows Vista, 7, 8, and 10: C: \ ProgramData \ Apple \ Lockdown
For successful data extraction, the researcher must move these files from the computer of the owner of the mobile device to his workstation (in the same folder). The data can then be retrieved using any forensic tool or iTunes.
It is important to note that if an Apple mobile device is running iOS version 9 or later and has been restarted after being locked, the researcher will not be able to use this approach.
Security recommendation: Do not connect iOS devices to computers that do not have full disk encryption with strong password installed.
Unlocking mobile devices running Android operating system
For mobile devices running the Android operating system, there are a number of methods that allow you to access data without knowing a PIN or pattern. We will describe both these methods and ways to recover your PIN or pattern.
Method 25: unlock device using AT commands of the modem
On some mobile devices, the AT-modem can be activated by default. Typically, these are mobile devices manufactured by LG Electronics Inc. in 2016-2017, but there may be devices manufactured by other manufacturers.
This allows the researcher to control the operation of the mobile device using AT commands. For example, you can use these commands to retrieve a memory dump from a device that is in Firmware Update mode. Or unlock the device with a single command. Using AT commands is the most forensically correct way, as it does not change the data in the device's memory.
To unlock a mobile device, it must appear in the list of Windows devices on the investigator's computer as LGE Mobile USB Modem.
Locked LG smartphone connected to researcher's computer in LGE Mobile USB mode:
Then you can issue an AT command using the terminal or use specialized software (for example, Oxygen Forensic Suite Expert).
Displaying a locked LG smartphone in Oxygen Forensic Suite:
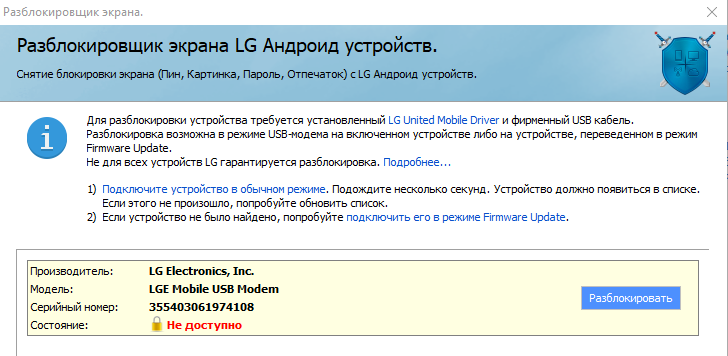
If you click the "Unlock" button in the program interface, the device will be unlocked:

The use of AT commands in mobile forensics is described in more detail in the work “Unlocking The Screen of an LG Android Smartphone with AT Modem Commands” [29].
Protection recommendation: change the device to the current one.
Method 26: access data of a rooted device
Sometimes a rooted device can be accepted for research, that is, a device on which the researcher already has superuser rights. On such a device, the researcher has access to all data: files and logical partitions. Thus, the researcher can extract the files containing the PIN or picture password and try to restore their values or delete them and thus unlock the device.
In addition to the described method, a physical dump of a mobile device, in which the researcher can find files containing a PIN or graphic code, can be generated in the following ways:
- Chip-off method (extraction of a memory chip and reading information from it directly)
- JTAG method (using the Joint Test Action Group interface, which is used to debug programs)
- In-System Programming (ISP) ( )
- Emergency Download Mode ( Qualcomm)
- AT-
Using exploits, the researcher can extract part of the file system of the device under investigation. If this fragment of the file system contains files containing a lock PIN or pattern, the researcher can try to restore them.
Files gesture.key, settings.db, locksettings.db, gatekeeper.password.key
Information about the PIN or graphic code is saved in the following files located under the path / data / system / :
- gesture.key (gatekeeper.pattern.key in newer firmware)
- password.key (or gatekeeper.password.key)
- locksettings.db
- locksettings.db-wal
- locksettings.db-shm
- settings.db
- settings.db-wal
- settings.db-shm
Deleting these files or changing the hashed password values in them may unlock the mobile device.
Security recommendation: This method (gesture.key) is applicable to older devices where there was not yet a separate area for storing cryptographic data and it was stored simply in the file system. This method will not work in new devices.
Method 27: delete the file containing the lock code
The easiest way to unlock your mobile device is to delete the file containing the lock code. To do this, USB debugging must be enabled on the device, which, unfortunately, does not always happen.
If the researcher is lucky and USB debugging is activated, he can delete the file containing the password with the given sequence of commands [30]:
adb devices
adb shell
cd /data/system
su
rm *.key
rm *.key
adb rebootAn alternative option is to enter a command that will delete the gesture.key file :
adb shell rm /data/system/gesture.keyAfter rebooting, the device will either be unlocked immediately, or a lock screen will appear, which you can simply swipe up or to the side.
Another method to remove a lock is to change the values of the database cells that contain passwords. To do this, execute the following sequence of commands [30]:
adb shell
cd /data/data/com.android.providers.settings/databases
sqlite3 settings.db
update system set value=0 where name=’lock_pattern_autolock’;
update system set value=0 where name=’lockscreen.lockedoutpermanently’;
.quit
An alternative option is provided by the user nstorm1 on the w3bsit3-dns.com forum. He suggests to enter the following sequence of commands [31]:
adb shell
cd /data/data/com.android.providers.settings/databases
sqlite3 settings.db
update secure set value=0 where name='lockscreen.password_salt';
update secure set value=0 where name='lockscreen.password_type';
update secure set value=0 where name='lockscreen.lockoutattemptdeadline';
update secure set value=0 where name='lock_pattern_visible_pattern';
update system set value=0 where name='lockscreen.lockexchange.enable';
.quitProtection recommendation: similar to the previous one.
Method 28: installing custom firmware
If the researcher is unlucky and the mobile device does not have USB debugging enabled, then he can try to install custom firmware to gain access to files containing lock codes (passwords), or delete them.
The most popular are custom firmwares:
- CWM Recovery (ClockworkMod Recovery) is a modified unofficial firmware that is released for most devices running Android. It has much broader capabilities than native firmware. On some devices it is installed instead of the native firmware, on other devices it is installed in parallel.
- The Team Win Recovery Project (TWRP) is also a modified unofficial firmware that is released for most Android devices. It has much more features than native firmware. On some devices it is installed instead of the native firmware, on other devices it is installed in parallel.
Some custom firmware can be installed from a microSD card. Instructions for flashing them into mobile devices can be found on the corresponding Internet sites.
Having flashed CWM Recovery into a mobile device, you need to mount the DATA partition using the command:
mount /dev/nandd /data
After gaining access to the device files, you need to execute the sequence of commands described in method 27 [32].
If you managed to flash TWRP on your mobile device, then you need to go to the TWRP section called Advanced and select File Manager. Next, using File Manager, you need to go to the data disk in the system directory, then delete files that may contain a PIN or a picture password (gesture.key, settings.db, locksettings.db, gatekeeper.password.key files, etc. .).
The gatekeeper.password.key, gatekeeper.pattern.key, locksettings.db, locksettings.db-wal, locksettings.db-shm files displayed in the TWRP File Manager interface:
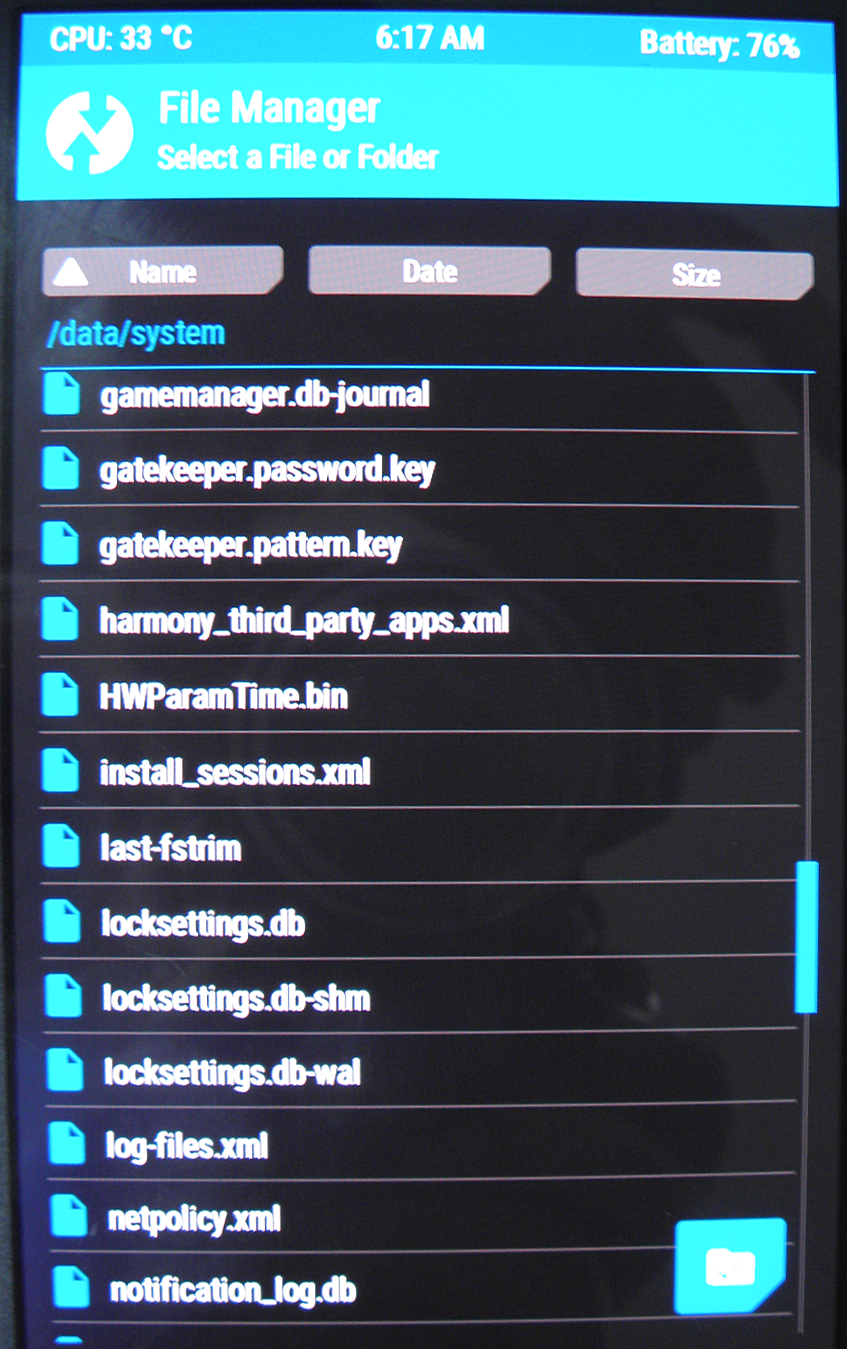
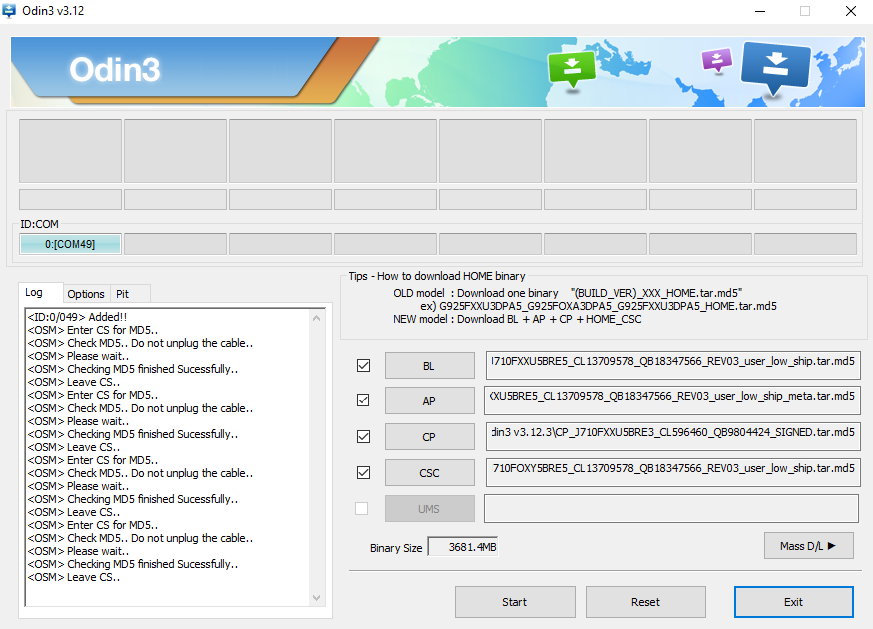
Custom firmware can be flashed to Samsung mobile devices using Odin. Different versions of the program have their own instructions for flashing mobile devices.
Uploading custom firmware to your Samsung SM-J710 mobile device using Odin3:
Mobile devices equipped with MTK chip (for example, Meizu, Xiaomi, Lenovo, Fly, Elephone, Blackview, ZTE, Bluboo, Doogee, Oukitel, UMI and other Chinese manufacturers) can flash custom firmware using the SP Flash Tool [33] ...
Security recommendation: Use devices with full-disk or per-file encryption, with Android version 9.0 and higher, with security patches dated July 2020 and newer.
Method 29: recovering PIN from file
If a researcher cannot extract a file containing a PIN-code or a graphic code from a locked device, he can try to recover the code stored in the file.
For example, using Andriller, you can recover the PIN stored in the gesture.key file.
Fragment of the main Andriller window:

A hash can be extracted from the file containing the picture password (gesture.key), which can be decoded using rainbow tables into a sequence of numbers that are the values of the picture code. An example of such an extraction is given in Android Forensics: Cracking the Pattern Lock Protection [34].
Recovering a graphic pattern from the gatekeeper.pattern.key file is currently difficult, as there are no publicly available tools and research papers that would highlight approaches to analyzing the data in this file.
Method 30: using specialized programs
Using specialized programs (or hardware and software systems - for example, UFED Premium, which was described above), you can extract the file system of the device under investigation, a physical dump, and also remove (and after research - restore) the screen lock code. The illustration below shows the UFED 4PC program window with extraction options for Samsung SM-J710F. It displays the entire completeness of the extraction methods available to the researcher. UFED 4PC can be considered the civilian version of UFED Premium.
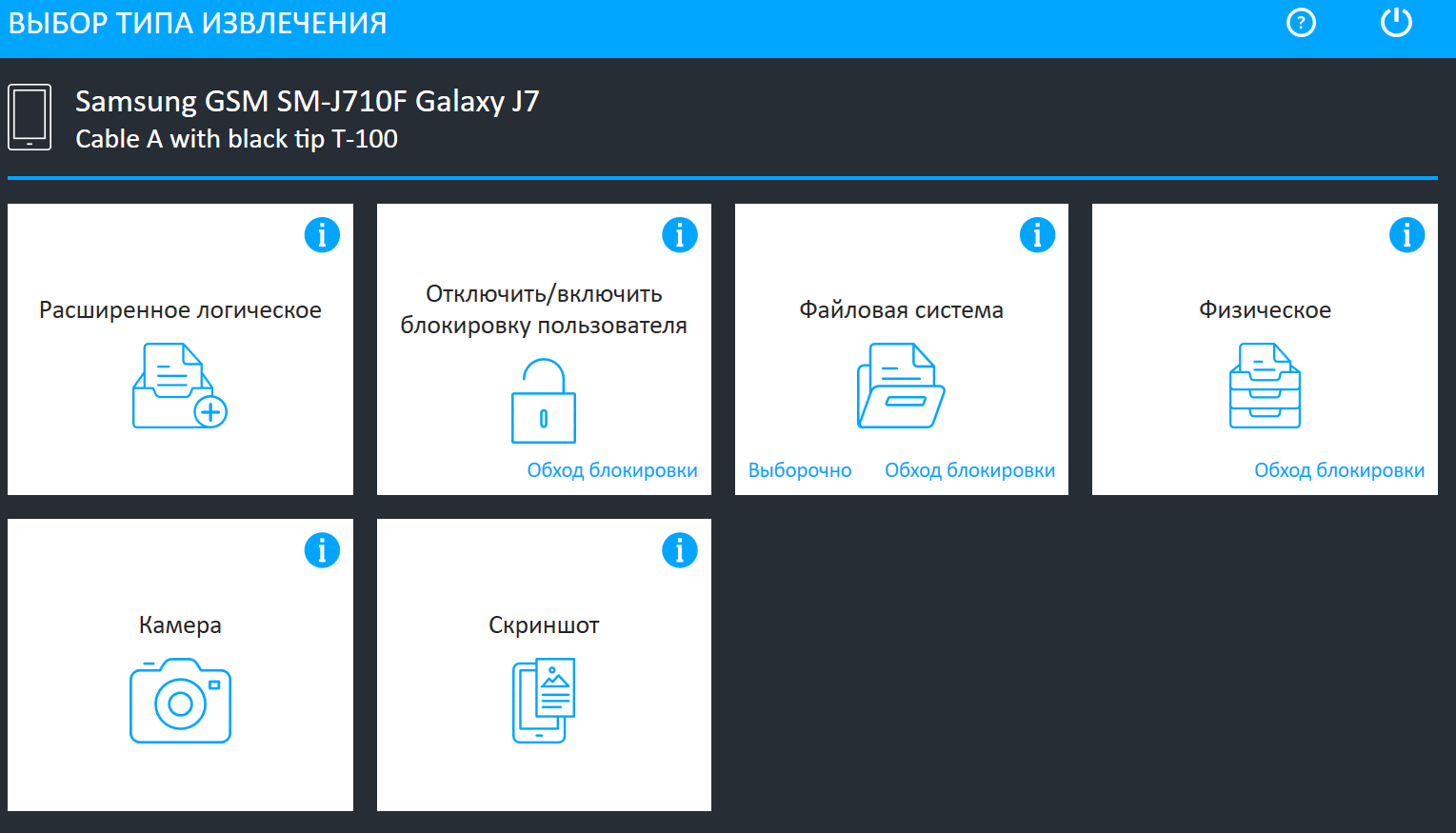
Thus, the researcher can disable / restore the screen lock on the smartphone, as well as extract the device file system or make a complete copy of the device memory bypassing the lock.
Protection recommendation: as a rule, such software and hardware systems exploit vulnerabilities in the bootloader or processor of the device and are not available to the civilian user. At the moment, almost all Kirin, Exynos and older versions of Qualcomm processors are vulnerable.
conclusions
The smartphone today is the main source of data about the personal life of its owner. Realizing this, mobile device manufacturers are constantly improving the security of the data they store. From a technical point of view, the security of top-end iOS and Android mobile devices is at a high level. Even minor software damage to the device can lead to a complete loss of access to the data in the device.
Many of the methods described are relevant only for older versions of iOS and Android. For example, starting from version 6.0, Android uses file system encryption, and from iOS 11.4.1 - the USB Restricted Mode mechanism (a protective mechanism that disables any data exchange through the Lightning port built into the device).
The competition between mobile device manufacturers and researchers seeking access to data is akin to a competition between specialists in the development of armor and projectiles. Increasing the security of stored data requires researchers to study more deeply the protective mechanisms of mobile devices, which leads to curiosities. An example is the development of the Checkm8 exploit for Apple devices. Apple has steadily increased the security of its mobile devices, which has hampered the activities of researchers. An in-depth analysis of the protective mechanisms of this manufacturer led to the discovery of a vulnerability in the BootROM, that is, in the device code that is responsible for the initial boot. Checkm8 allows you to get superuser rights on all Apple devices released from 2011 to 2017 (including all models from iPhone 4s to iPhone X),and for all existing versions of the iOS operating system. This vulnerability is fatal: to fix it, Apple needs to recall millions of devices around the world and replace the BootROM code in them.
Social methods for unlocking mobile devices will continue to be relevant until manufacturers develop other ways to identify device owners that prevent the use of social engineering.
If we talk about device security, then at the time of publication of the article, relatively safe devices can be considered:
- Devices on Apple A12 and A13 processors with iOS 13.6.1 and a password greater than 6 characters.
- Devices based on Qualcomm 865 and 865+ processors with Android 9.0 and higher with security patches dated July 2020. This must use a password and not use photo unlock and a camera-based fingerprint sensor.
Sources
22. Introducing GrayKey
23. GrayKey – iPhone
24. UFED Premium
25. IP-BOX iPhone Password Unlock Tool
26. The Burner Breaker
27. . heckm8, iPhone
28. Team Pangu demonstrates an unpatchable SEP vulnerability at MOSEC
29. Oleg Davydov. Unlocking The Screen of an LG Android Smartphone with AT Modem Commands
30. Kevin Arrows. How to Delete Your Android Security PIN
31. |
32. / . settings.db sqlite3
33. SP Flash Tool
34. Android Forensics: Cracking the Pattern Lock Protection
23. GrayKey – iPhone
24. UFED Premium
25. IP-BOX iPhone Password Unlock Tool
26. The Burner Breaker
27. . heckm8, iPhone
28. Team Pangu demonstrates an unpatchable SEP vulnerability at MOSEC
29. Oleg Davydov. Unlocking The Screen of an LG Android Smartphone with AT Modem Commands
30. Kevin Arrows. How to Delete Your Android Security PIN
31. |
32. / . settings.db sqlite3
33. SP Flash Tool
34. Android Forensics: Cracking the Pattern Lock Protection
An extremely topical Telegram channel Group-IB t.me/Group_IB about information security, hackers, APT, cyber attacks, scammers and pirates. Investigations step by step, practical cases using Group-IB technologies and recommendations on how not to become a victim. Connect!