Searching for leaks and vulnerabilities in your products is not only interesting and useful, but also necessary. It is even more useful to involve external specialists and enthusiasts in such searches, who do not have the same blurry eyes as employees. Therefore, at one time, we at QIWI launched the bug bounty program - researchers wrote to us about vulnerabilities and received rewards, and we closed these vulnerabilities.
Several times we were sent the publicly available code in the form of links to repositories with sensitive information. The reasons for the leaks could be as follows:
the developer wrote a test code example for himself using the configurations of a "production" service - not a test environment;
admin uploaded scripts for automation and database migration - potentially sensitive information;
the trainee unknowingly posted the code to his public repository, believing that it was not risky.
At the same time, such leaks can come from both developers working in the company and from those who have already quit. For example, there have been cases when an employee who is no longer working for the company posted code in an open repository that he once took home to work with in his free time. It would seem - it sounds harmless, but inside such a code there could well be passwords from a database, network configuration or some kind of business logic - in general, information sensitive for a company that should not be publicly available.
As practice shows, most companies are already well protected from external threats - and it is an internal leak that can cause the greatest harm. Moreover, such a leak can happen both maliciously and by accident - and this is exactly what we said above.
— : Firewall, SOC, IDS/IPS , — . , , — .
. , , .
QIWI Leak-Search — , Github .
— .
, : - , -, , . , — .
, . . -, , .
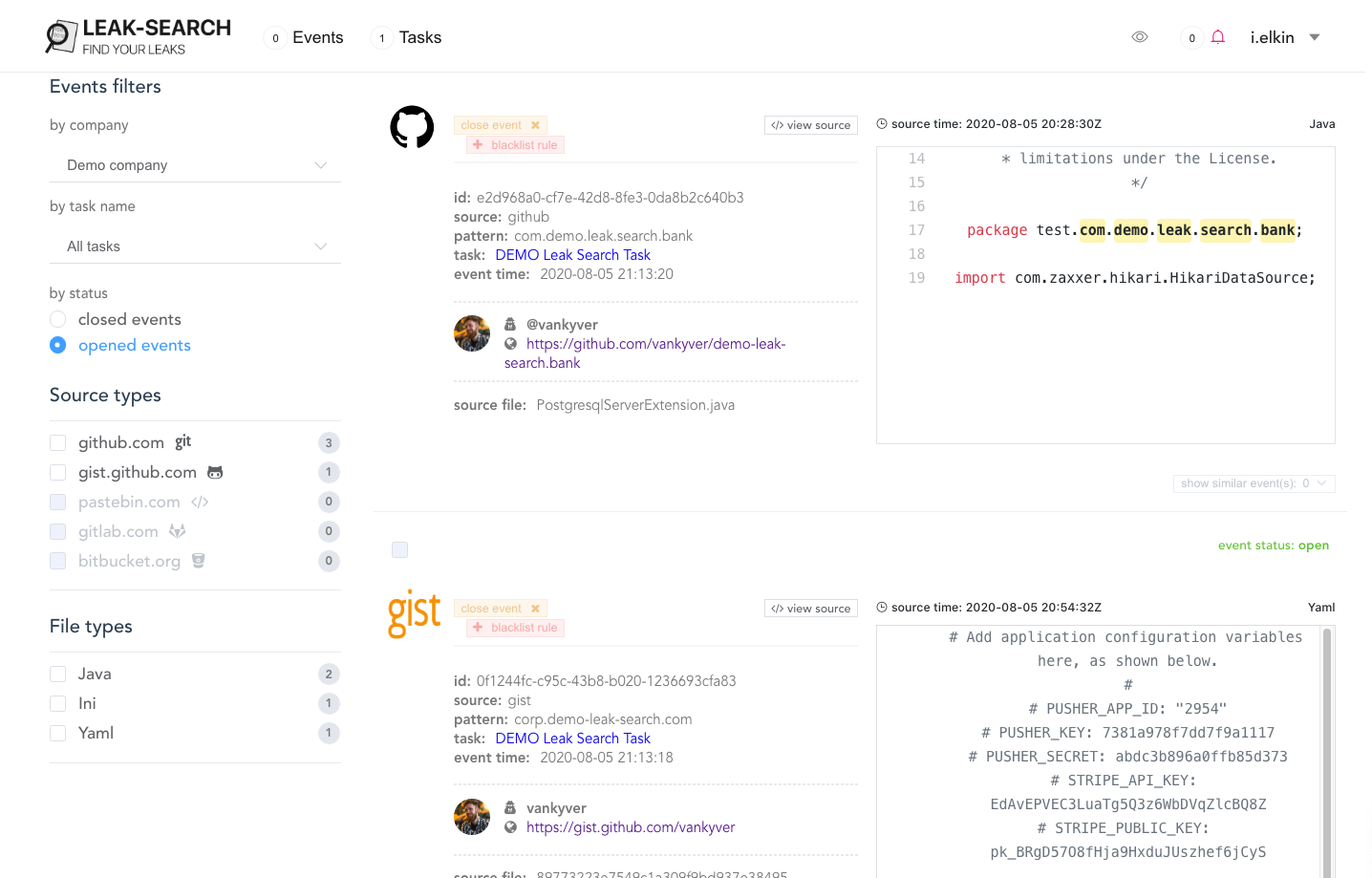
Leak-Search , , , . Fortune . , , , .
, . -: , , . , - , : , — .
, Leak-Search. “” ERP- — ? - “” IoT- — , ? “ ” — . .
QIWI Leak-Search
— . — , -, — , , . .
, , — , , , , , — .
, — . , - , — , .
. , , , .
Leak-Search , . :
— — smtp, Dockerfile, proxypass, Authorization;
— — com.qiwi.processing.common;
— — int.qiwi.com, 10.4.3.255;
— , — QIWISECRET_KEY, qiwiToken.
, , . - — , .
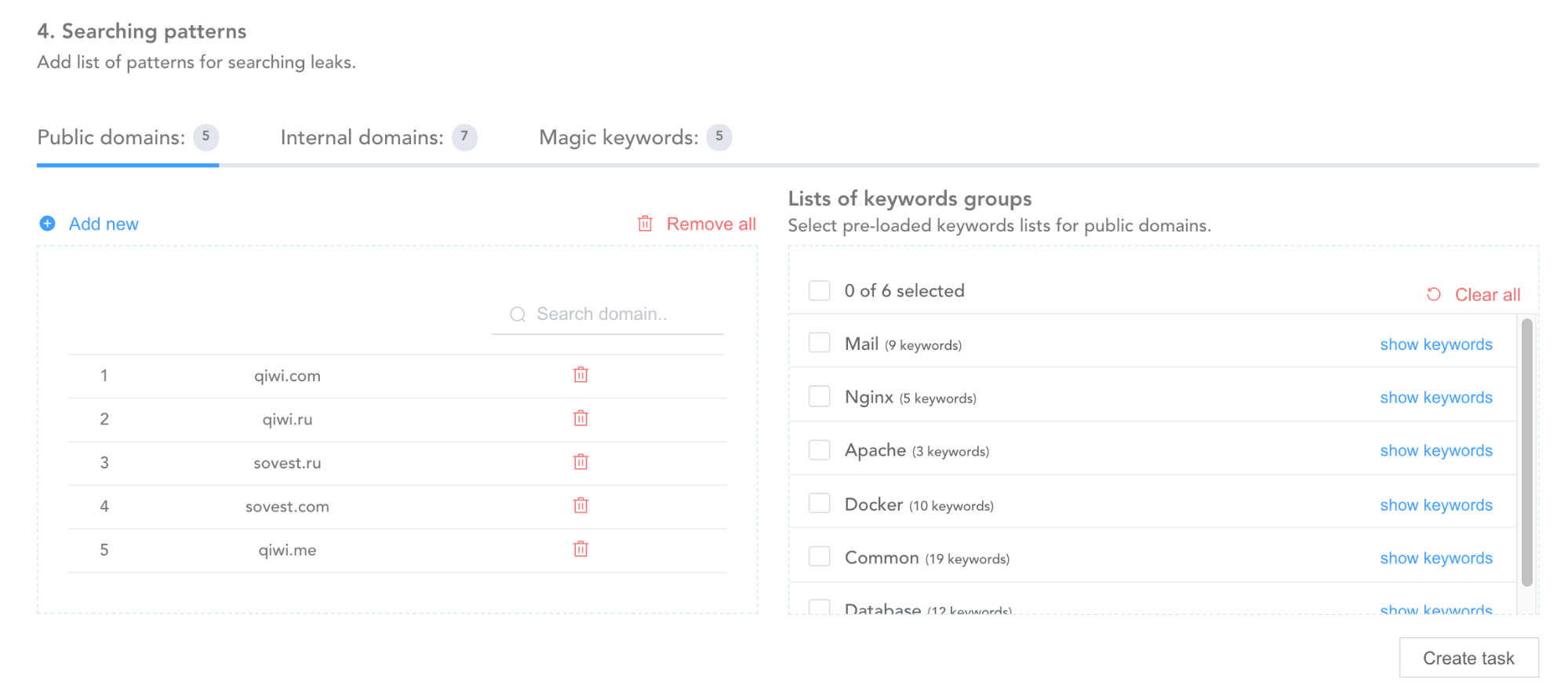
. , . Open Source: - . .
, , — «» .
StackOverflow — , , . . , , Github. , .
, , , - , , - Github — , . .
, ? , , . , , .
— killer feature . Leak-Search : , . -, . -, , , .

, , open source, , Github, . , Leak-Search “” .
, . Github — Leak-Search Gist. - Pastebin Gitlab, BitBucket. API.
, , — false positive, false negative. , .
“ ” . , , — , .
, Leak-Search . . Leak-Search , — .
, , Leak-Search , “”. — , , , -, .
, . , , . , — .
, , , , , IT, .
- , , — , .