 Over the past two weeks, it became known about two vulnerabilities in the Bluetooth wireless standard. First, on September 9, the Bluetooth SIG issued a warning about the BLURtooth attack family. In theory, a vulnerability in the Bluetooth 4.2 and 5.0 specifications allows for a MitM attack. In practice, this requires many conditions to be met, such as connecting (with limited rights) to the target device.
Over the past two weeks, it became known about two vulnerabilities in the Bluetooth wireless standard. First, on September 9, the Bluetooth SIG issued a warning about the BLURtooth attack family. In theory, a vulnerability in the Bluetooth 4.2 and 5.0 specifications allows for a MitM attack. In practice, this requires many conditions to be met, such as connecting (with limited rights) to the target device.
The vulnerability was discovered at the junction of two Bluetooth connection options - the traditional Basic Rate / Enhanced Data Rate and the energy efficient Bluetooth Low Energy. In order not to log in twice using different protocols, long-term shared keys are generated in devices that support both BR / EDR and BLE. The specification allows rewriting keys if a more reliable data transfer mode is required. But as a result, a connection can be established with the device either without proper authorization, or the connection protection is easily hacked.
The second vulnerability, dubbed BLESA, was found in the Bluetooth Low Energy specification. It allows you to connect to other devices without authorization, simulating the procedure for reconnecting after a disconnection.
In practice, it looks like this: a device is connected to the smartphone (for example, a fitness tracker), then the connection with it is cut off and the attacker's device is connected to the smartphone. Additional authorization is not required, and it is easy to intercept the identifier of a legitimate device, since this data is transmitted in clear text. The ease of reconnecting the device turned out to be a security hole.
Sources of
BLURTooth:
- Carnegie Mellon University CERT report ;
- Bluetooth SIG Bulletin ;
- news on the Bleeping Computer website;
- news on Habré.
BLESA:
- news ;
- research work ;
- news on Habré with PoC video.
Information about these attacks is disclosed in completely different ways. A scientific work has been published about BLESA with a detailed description of the attack process. About BLURtooth - only two short messages without details. Perhaps this is due to the fact that a patch has already been released for BLESA (at least for Apple devices), and patches for Android and the universal Bluez stack are also being prepared.
BLURtooth is still a problem without a solution. Although these attacks have one thing in common: they are not very likely to be used in practice due to the need to stay close to the victim and dubious (at least unexplored) prospects from the point of view of data theft.
Both vulnerabilities in the future may become the stage of a more serious attack on IoT devices, especially since it will not be possible to update the Bluetooth stack everywhere.
What else happened
Kaspersky Lab specialists published a report on the evolution of threats in Q2 2020. Interesting: the growth in the number of malicious attacks on "gaming" topics, in particular - phishing and the distribution of malware associated with the Steam platform.
In a remote work environment, such attacks can lead not only to theft of in-game or real money, but also to infiltration of the working infrastructure if the victim uses the same computer for playing and working.
Another study by Kaspersky Lab focused on a zero-day vulnerability in Internet Explorer 11. Paired with another hole, not so dangerous in itself, a browser bug provided complete control over the target system.
A sad but predictable case: in Germany, a ransomware attack on a hospital infrastructure resulted in the death of a patient.
On Wednesday September 16, the developers updated the Drupal CMS, including a critical XSS vulnerability fix .
An interesting case happened with the Discount Rules for WooCommerce WordPress plugin. Two serious vulnerabilities were patched only on the third attempt.
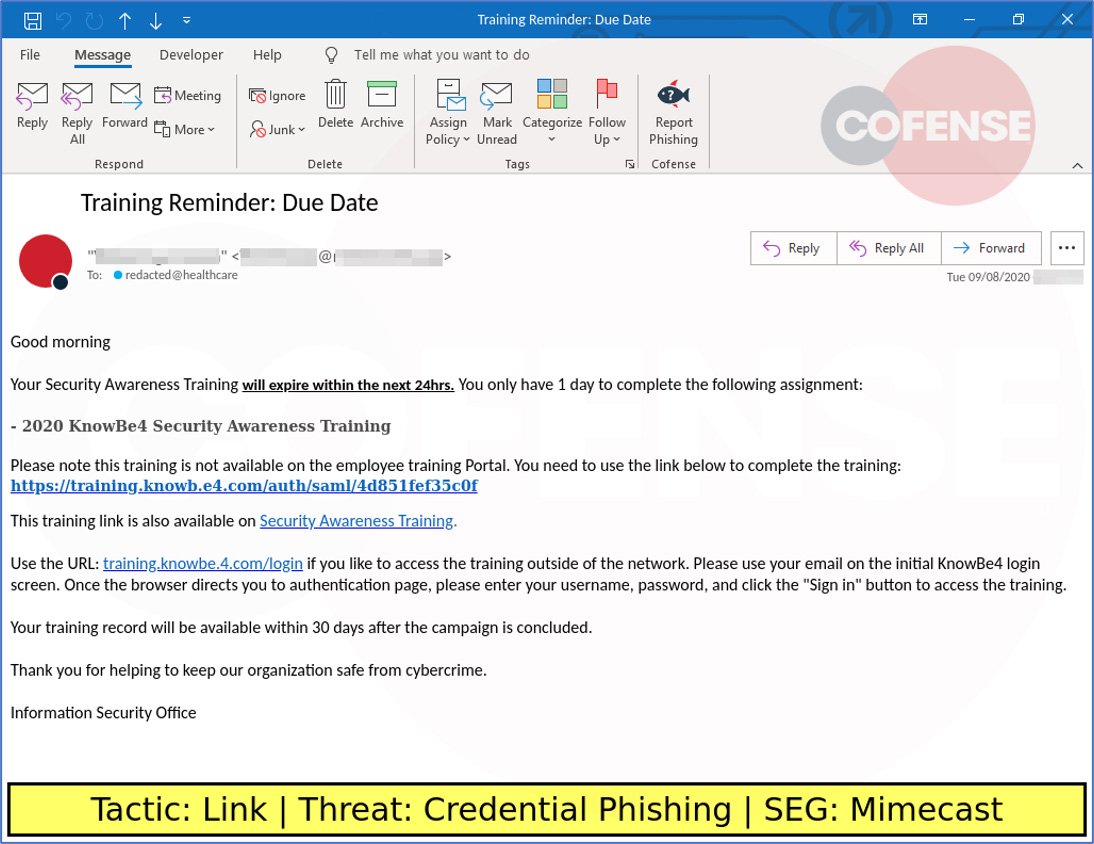
Bleeping Computer reports on a phishing attack disguised as information security training.
Google is banning stalkerware on Google Play. More precisely, it is impossible to observe the user covertly: if there are such functions, the user must be warned that his movements and actions will be monitored.
The exploit for the Zerologon vulnerability in Windows has appeared in the public domain . The patch for this hole was released back in August this year.