
General trends
Exploitation of the COVID-19 theme
In the second quarter of 2020, cybercriminals actively exploited the topic of the pandemic in attacks using social engineering (unexpected, right?). As a rule, malicious emails imitated the official mailing list with information about the coronavirus, which significantly increased the effectiveness of such attacks during a period of general panic and tension. Moreover, hackers used not only massive viruses (ransomware, banking Trojans, RAT, etc.), but there were also cases of using the pandemic by APT groups. They attacked almost all industries and types of customers (from SMB to enterprise and state corporations).
An example of a phishing email allegedly from the US Centers for Disease Control and Prevention:

Dharma ransomware and RDP attacks
During the pandemic, many companies organized remote operation, mainly via RDP. Who could do
In addition, at the end of March 2020, an announcement appeared on the shadow forums about the sale of the source code of the Dharma ransomware for $ 2000. And already in April and May, we were faced with investigations of incidents in which an attacker (and, judging by the results of the investigation, these were several different attackers) penetrated the victim's infrastructure by trying the password from the local administrator account using the RDP protocol. After that, he decided to bypass the antivirus in a simple but effective way: he launched several dozen copies of the ransomware in different shells. Most of the files were detected and deleted by the antivirus, but one undetected sample was enough for successful encryption. An intruder's attempts to bypass protection are visible in the antivirus logs:

This fact suggests that someone bought the source code for Dharma and uses it skillfully, covering the encryptor with various wrappers.
Using legitimate services
The trend has continued to use exploits in the public domain to compromise non-updated web services. The same ShellShock, for example, is still often used in attacks on the public sector. Similar vectors are found in attacks on energy and fuel and energy sectors. E-commerce and banks, on the other hand, are pretty good at building protection for their own web applications, so they rarely encounter such problems.
In one of our investigations, we came across a combination of vulnerabilities in the JBoss Web Application Server. As a result of their exploitation, the attacker placed a shell (jcmd.war) on the server, and used an SSRF vulnerability in the WebLogic server to send commands to this shell:

The commands were powershell scripts that performed various actions on the system and sent commands via a DNS tunnel to the legitimate site ceye.io, created by information security specialists for testing corporate systems:

On the site, something similar appeared in the attacker's account:
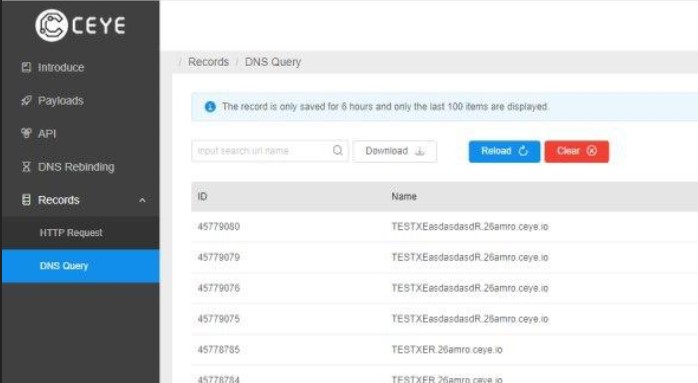
As a result, he was able to get the result of command execution by collecting response fragments manually or using a script.
Basic attacks and typical attackers
Below are the attack vectors used by attackers with low
Vulnerability in Citrix CVE-2019-19781
The RCE-class vulnerability found in Citrix NetScaler at the end of 2019 is one of the loudest and most easily exploited in recent years. After the news and PoC were released to the public, the scale of the problem immediately became apparent: tens of thousands of systems were found vulnerable around the world.
For our part, we also record massive attacks on organizations in the credit and financial sector, fuel and energy complex, energy and industry. In particular, in one of our own investigations, we came across the fact that this vulnerability became an entry point for an attacker into the infrastructure. By installing a web shell on the Citrix NetScaler system, he was able to maintain access for seven months.
The traces of exploitation of the CVE-2019-19781 vulnerability look like this:

New RTM skin
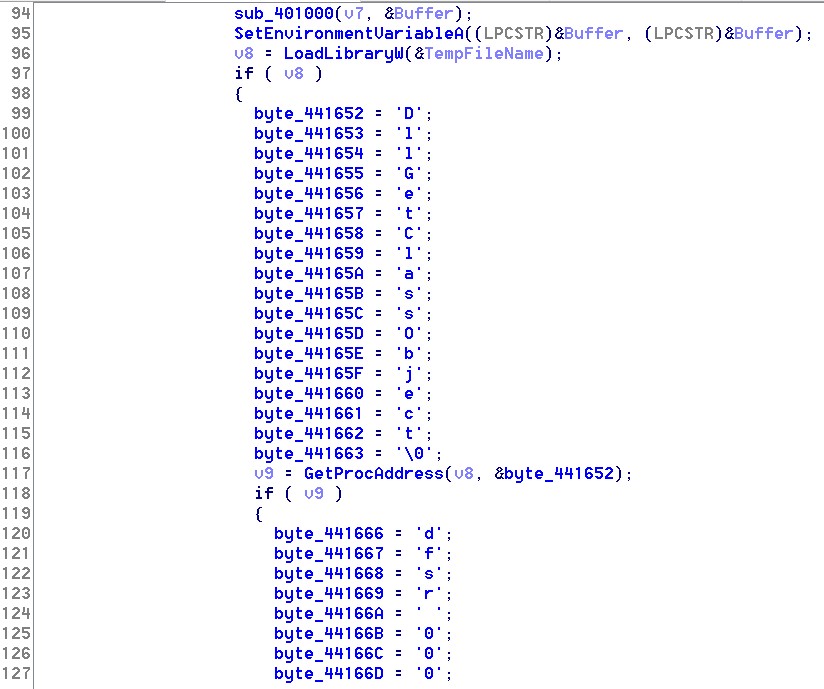
The cybercriminals began sending out the well-known banking Trojan RTM in a new shell, which has a fairly simple structure and works in three stages. Below is the first wrapper layer that decrypts the shellcode and passes control to it.

Next, the shellcode, which has approximately the same simple structure, decrypts and launches an executable file, which then decompresses RTM using the RtlDecompressBuffer function and launches it:
As you know, in recent years, RTM has been the leader in the Russian space in terms of the number of phishing mailings. The attacks are aimed at maximum capture of infrastructure and anchoring in it, followed by an attempt to monetize through the withdrawal of funds.
Resume Emotet Activity
The Emotet downloader, which was practically not used in Russia for the whole last year, was activated again in July 2020 and this time it was distributing the QBot banking trojan. We record it with our customers from different industries: energy, public sector, credit and finance. At the same time, one of the Qbot modules allows you to steal mail messages, which the operators distributing Emotet then use for phishing mailings. This greatly increases the level of trust of recipients and increases the chance of infection.
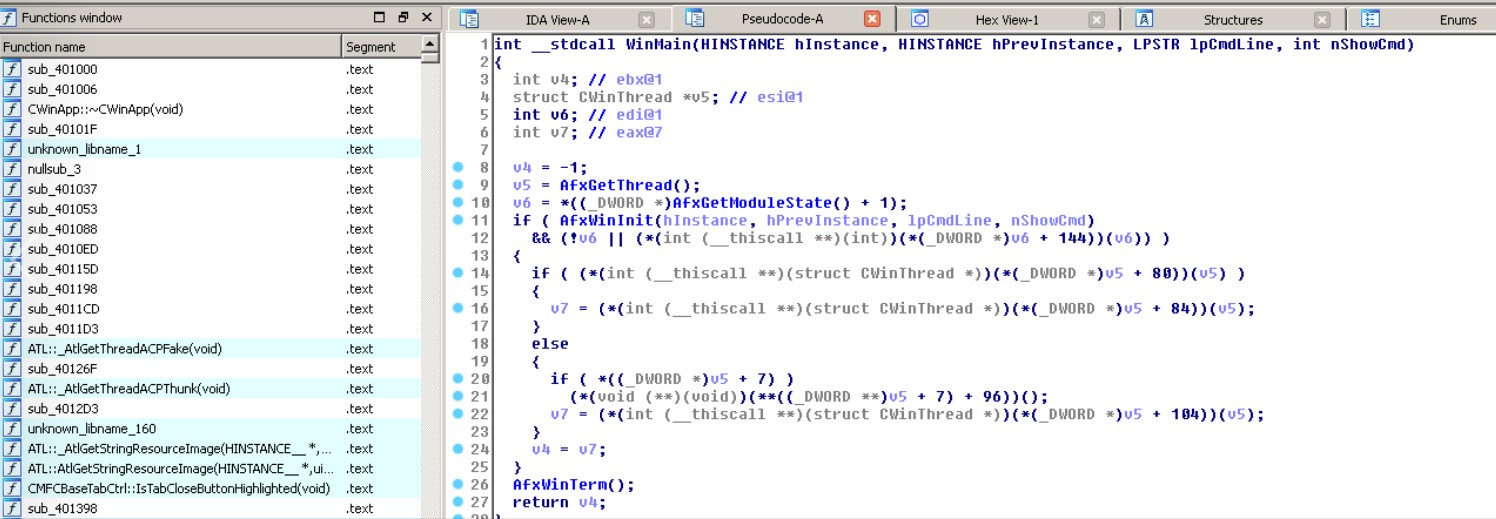
The malware spread in a shell disguised as an MFC application.
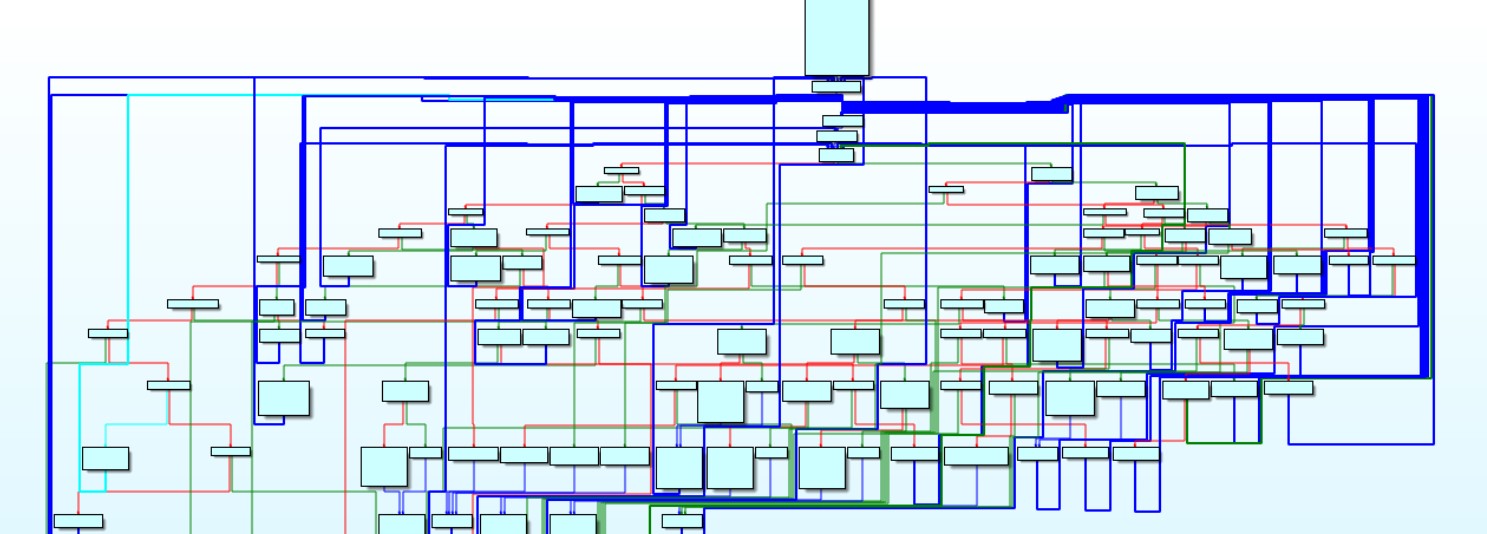
One of the protective layers uses control-flow obfuscation.
MassLogger stealer mailings
We have recently registered a new MassLogger stealer at one of our foreign customers. And even if it is not sent out often, it has already hit the radars of information security specialists. By the way, he has not yet been noticed in mailings to Russian companies.
The virus is a .NET executable file, protected by a shell with multiple virtual environment checks and obfuscated. There are three main obfuscation methods used: control-flow obfuscation, string encryption, and dynamic delegate initialization.
An example of control-flow obfuscation is shown below:

At the beginning of execution, one of the resources is decrypted, which contains a special dictionary. The key is the token of the field of one of the classes, and the value is the token of the function, the delegate of which is to initialize this field. Further, many functions are called through these dynamically initialized fields.
Below is a code snippet where the dictionary is filled and the fields are initialized by delegates:

The MassLogger family is capable of sending data collected from a victim's computer in three ways: to a control panel (http), to an FTP server, or to a mailbox. The virus configuration contains the necessary credentials for FTP and mail server (depending on the used sending method). In this aspect, MassLogger bears similarities to some other .net stealers: Hawkeye, Agent Tesla. Below is a code snippet with filling in the configuration:
NetWire Mailing List in Visual Basic Shell
In a wide variety of industries, RAT NetWire mass mailings have been recorded in a shell written in Visual Basic. We have seen both native code and p-code variations. The task of the shell is to check for a virtual environment, debug and load NetWire from certain hardwired addresses. In the past year we have seen many different families of stealers in a similar shell, but this sample includes more obfuscation and virtual environment detection techniques.
A typical code snippet of this VB packer is shown below:
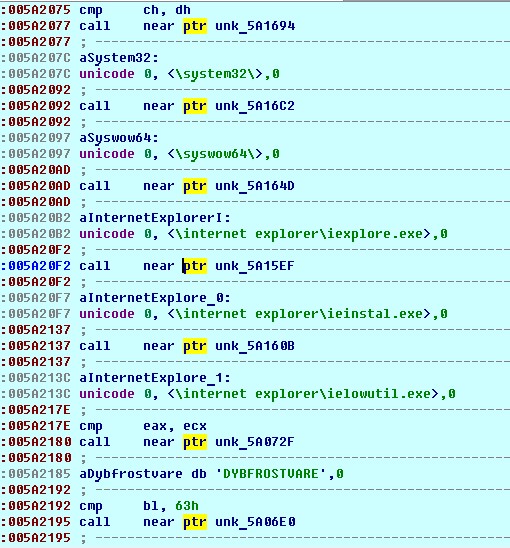
An example of detecting unwanted services using a computed hash of the service name (for example, "VMware Tools" or "VMware Snapshot Provider"):

Zloader mailing lists using Excel 4.0 macros
Some of our customers from the credit and financial sector have registered Zloader malware mailings. Users received an Excel document, upon opening which certain formulas were launched in cells that perform the necessary actions, including anti-analysis and downloading malware. The formulas themselves have been scattered across a huge sheet of paper to make them harder to spot and analyze. It is worth noting that Macro 4.0 technology is considered obsolete and is now almost never used.
Advanced factions and sophisticated tools
For advanced cyber groups, the key task is not just to penetrate the infrastructure, but to stay inside it as long and inconspicuous as possible, long-term control and access to confidential data (cyber espionage). During the reporting period, they operated as follows.
Another method for hiding Mimikatz
In one of our investigations, cybercriminals of a sufficiently high technical level used an interesting technique to bypass the antivirus and launch Mimikatz. Mimikatz in encrypted form was placed in a shell that took two parameters from the command line: a key and an initialization vector. Then, using the CryptoPP library, Mimikatz was decrypted, and control was transferred to him. Below is a fragment of the code with the installation of the key and the vector, as well as with the preparation of the buffer for decrypting the data:

As a result, the anti-virus protection was silent when the Mimikatz utility was started and the attacker was able to obtain the credentials.
New hacker group TinyScouts
In the summer of 2020, we identified a new cybercriminal group that attacked banks and energy companies. TinyScouts is distinguished by a high level of technical skills and variability of the attack scenario. We wrote more about TinyScouts here .
That's all. New investigations went to the
Igor Zalevsky, JSOC CERT
Cyber Incident Investigation Department Head Asker Jamirze, JSOC CERT Technical Investigation Expert