Dear friends, in previous articles we talked about information security fundamentals , for laws protecting personal data and critical information infrastructure , security in the credit and financial sphere , as well as analyzed the basic standards for the management of the risks of information security and discussed class IRP systemdesigned to automate the response to information security incidents. As we know, in incident handling, detailed analysis of security events from devices is one of the key steps. In this publication, we will look at configuring the Windows OS audit subsystem, the principles of analysis and centralized collection of audit logs from Windows devices and sending them to the IBM QRadar SIEM system, and also show how you can use standard Windows tools and the Sysmon utility to set up a simple response system for information security incidents. Forward!

, (, ) , , , . : «» , , , . Microsoft (Baselines) Microsoft Security Compliance Toolkit, , . CIS Microsoft Windows Server Benchmark CIS Microsoft Windows Desktop Benchmark, , , , , Windows. «», , ( ) Windows.
, Microsoft Windows, Microsoft Windows Server 2008 Vista, , (Advanced Audit Policy Configuration). , , «» , «: (Windows Vista ))» (Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings).
Windows
, .
|
|
| EventID | |
|
| , | 4776 | - NTLM-. |
Kerberos | , | 4771 | Kerberos-. | |
4768 | Kerberos, . | |||
: , IP- nltest /dbflag:2080ffff - %windir%\debug\netlogon.log | ||||
|
| 4741 | Active Directory; , 10 , , . | |
| , | 4728 | . | |
4732 | . | |||
4756 | . | |||
| , | 4720 | . | |
4725 | . | |||
4740 | . | |||
4723 | . | |||
4724 | . | |||
|
| 4688 | . | |
4689 | . | |||
: , « - Windows - - - -> ».
: PowerShell- PowerShell-, « - Windows - - Windows - Windows PowerShell» « » ( «*») « PowerShell» ( check-box « »). PowerShell- EventID=4104,4105,4106 Microsoft-Windows-PowerShell/Operational, PowerShell- EventID=800 Windows PowerShell. | ||||
/ |
| 4634 | . | |
4647 | RDP-. | |||
: Logon Type, (, , , ..). | ||||
| , | 4624 | , - NTLM Kerberos-. | |
4625 | , - NTLM ; Kerberos- EventID=4771. | |||
4648 | , , runas, «» Mimikatz. | |||
: (Logon Type), (, , , ..). (Status/SubStatus), - , , .. | ||||
| , | 4778 | RDP- . | |
4779 | RDP- . | |||
| 4672 | . | ||
|
| , | 5145 | , \\C$\ . ransomware, . |
| , | 4698 | « », . | |
|
| 4719 | . | |
4906 | CrashOnAuditFail. | |||
: ( CrashOnAuditFail) « - Windows - - - » «: , ». | ||||
| 4610 4614 4622 | , . | ||
4697 | , . | |||
, EventID=1102, , . , « - Windows - - - » « : NTLM: NTLM » « ». EventID=8001 Microsoft-Windows-NTLM/Operational - . allow list -, , . NTLM- , .
, Windows - - .
Windows Event Forwarding, IBM QRadar
, . Windows Event Forwarding, Microsoft Windows Server 2008 / Vista , - ( Windows Server 2008 Vista, Windows Server 2012R2 ) - WinRM (Windows Remote Management, WS-Management) .. «» ( XPath-, , ). ( Pull/Collector initiated), ( Push/Source computer initiated). , Push WinRM , - WinRM , . , Windows-, - SOAP-, WinRM ( HTTP-Kerberos-session-encrypted), HTTP- . HTTPS SSL- , . , .
Windows-, : -> - -> IBM WinCollect -> SIEM- IBM QRadar.
:
1. - winrm qc, ( WinRM TCP:5985 ). , winrm qc Windows Remote Shell (WinRS) WinRS. WinRS « / / Windows / Windows / -> » (Computer Configuration / Administrative Templates / Windows Components / Windows Remote Shell / Allow Remote Shell Access -> Disabled), winrm set winrm/config/winrs @{AllowRemoteShellAccess="false"}
2. - wecutil qc, « Windows» (Windows Event Collector). Windows Firewall TCP:5985.
3. WinRM: « » «» « Windows» (Windows Remote Management (WS-Management)).
4. WinRM - winrm enumerate winrm/config/listener, IP-, TCP:5985. winrm get winrm/config WinRM. winrm, « / / Windows / Windows» (Computer Configuration / Administrative Templates / Windows Components / Windows Remote Management).
5. WinRM NT AUTHORITY\NETWORK SERVICE (SID S-1-5-20) BUILTIN\Event Log Readers (« »). « Windows» (WinRM) « Windows» (EventLog).
6. , -. « / / Windows / / ...» (Computer Configuration / Administrative Templates / Windows Components / Event Forwarding / Configure the server address...) - :
Server=http://servername.domain.local:5985/wsman/SubscriptionManager/WEC,Refresh=60
60 – ( ) . - WinRM.
7. -: (eventvwr.msc) «» (Subscriptions). « », . « » (Source Computer Initiated, Push). « » (Select Computer Groups), Active Directory , . , « » (Select Events) XPath- ( Security):
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">*</Select>
</Query>
</QueryList>
8. , TCP:5985 -. - eventvwr.msc «» -, « Windows – » (Windows Logs – Forwarded Events) -.
9. - SIEM IBM QRadar. - IBM WinCollect.
(Managed) WinCollect . , WinCollect IBM QRadar, IBM - WinCollect RenderedText, EN-US wecutil ss SubscriptionName /cf:RenderedText /l:en-US ( SubscriptionName - , .7 ). , - WinCollect IBM QRadar TCP:8413 TCP/UDP:514.
10. WinCollect -, SIEM- IBM QRadar ( Microsoft Security Event Log, Target Destination TCP-syslog-, check-box Forwarded Events).
-, Windows- -, IBM QRadar . , SIEM- Windows, .
Sysmon
, Sysmon Microsoft Windows Sysinternals, . , , , , , WMI- . , - . - (IoCs, Indicator of Compromise) CyberThreat Intelligence, QVTI IBM QRadar, VirusTotal. XML-, Sysmon. XML-, , https://github.com/ion-storm/sysmon-config https://github.com/SwiftOnSecurity/sysmon-config .
Sysmon :
1. https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon
.
2. xml- Sysmon.
3. sysmon x64 :
C:\folder\sysmon64.exe -accepteula -i C:\folder\sysmonconfig-export.xml , sysmonconfig-export.xml – , sysmon64.exe – -.
.
4. Microsoft-Windows-Sysmon/Operational , 100 .
, Sysmon , C:\Windows\sysmon64.exe . , footprint Sysmon 5-10% 100 .
XPath-
, Windows, . , , ( , - Log Management SIEM-). , Windows (eventvwr.msc), «» check-box « ».
, XPath (XPath queries). , , Windows ( « Windows» -> «» / Security), « ». , XML, check-box « ». XML- ( , XPath ) .
, «», radio-button « XML», «-» .
XPath .
1. Security - Username:
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">*[EventData[Data[@Name='TargetUserName']='Username']]
</Select>
</Query>
</QueryList>2. Sysmon - , 443:
<QueryList>
<Query Id="0" Path="Microsoft-Windows-Sysmon/Operational">
<Select Path="Microsoft-Windows-Sysmon/Operational">*[EventData[Data[@Name='DestinationPort'] = '443']]</Select>
</Query>
</QueryList>3. - EventID=4624 Username:
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[System[(EventID=4624)]]
and
*[EventData[Data[@Name='TargetUserName']='Username']]
</Select>
</Query>
</QueryList>4. - Logon Type = 2, :
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[System[(EventID=4624)]]
and
*[EventData[Data[@Name='TargetUserName']='Username']]
and
*[EventData[Data[@Name='LogonType']='2']]
</Select>
</Query>
</QueryList>5. - Suppress . (EventID=4624) , (SID S-1-5-18/19/20) (Logon Type = 4/5), «», (Advapi) (Negotiate NTLM):
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">*[System[(EventID=4624)]]</Select>
<Suppress Path="Security">*[EventData[(Data[@Name='TargetUserSid'] and (Data='S-1-5-18' or Data='S-1-5-19' or Data='S-1-5-20') and Data[@Name='LogonType'] and (Data='4' or Data='5'))]]
or
*[EventData[(Data[@Name='LogonProcessName'] and (Data='Advapi') and Data[@Name='AuthenticationPackageName'] and (Data='Negotiate' or Data='NTLM'))]]
</Suppress>
</Query>
</QueryList>IRP- Windows
, Windows , . , Windows «», - « » Windows, .
, Windows , . , , PowerShell/VBS/Batch-, . . « » (taskschd.msc), , «» . «» , drop-down « », radio-button «». « », , , XML XPath-.
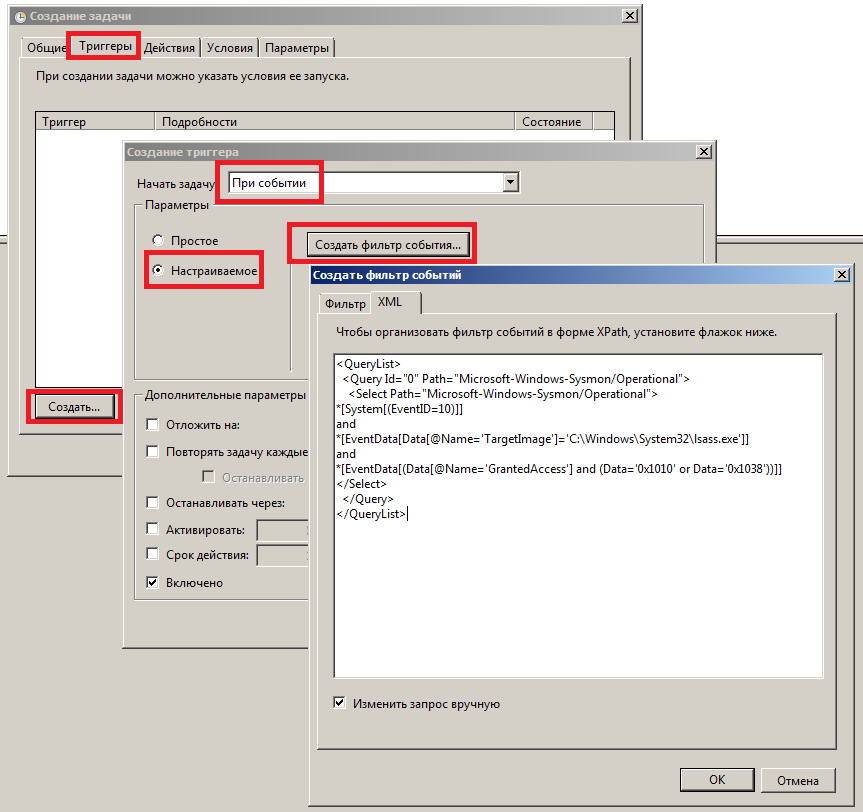
, Username, , :
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[System[(EventID=4624)]]
and
*[EventData[Data[@Name='TargetUserName']='Username']]
and
*[EventData[Data[@Name='LogonType']='2']]
</Select>
</Query>
</QueryList>: lsass.exe, NTLM- - Windows, Mimikatz :
<QueryList>
<Query Id="0" Path="Microsoft-Windows-Sysmon/Operational">
<Select Path="Microsoft-Windows-Sysmon/Operational">
*[System[(EventID=10)]]
and
*[EventData[Data[@Name='TargetImage']='C:\Windows\System32\lsass.exe']]
and
*[EventData[(Data[@Name='GrantedAccess'] and (Data='0x1010' or Data='0x1038'))]]
</Select>
</Query>
</QueryList>, Windows , , XPath-, . , , Sysmon , TI-, XPath-, Windows Event Forwarding, , ( ) , Windows.