
Good afternoon, colleagues! We continue the series of articles dedicated to information security solutions from Group-IB. In the previous article, we briefly highlighted a comprehensive solution to protect against complex cyber threats from Group-IB. This post will focus on the Threat Detection System (TDS) Sensor module. Recall that TDS Sensor is a module for in-depth analysis of network traffic and detection of threats at the network level, as well as for integration with various subsystems, included in the TDS software package. In this article, we will consider the product from the point of view of the functional part and implementation architecture.
TDS Sensor

TDS Sensor is a TDS product module designed to analyze incoming and outgoing data packets. Using its own signatures and behavioral rules, Sensor can detect interactions of infected devices with attackers' command centers , general network anomalies, and unusual device behavior. The databases of signatures and ML-models are constantly updated - based on investigations by forensic experts and on the basis of information from cyber intelligence systems.
Since the TDS Sensor is an anti-APT solution , it is geared towards detecting targeted attacks and network anomalies. This is not an IPS class solution, it is not intended for port scan detection, brute force detection or SQL injection attempts. Organizations that need protection against targeted attacks already need to have IPS / IDS solutions within their infrastructure. A distinctive feature of anti-APT solutions is the detection of attempts to transfer some data outside the perimeter, communication with the attackers' command centers (Command & Control, CnC), and the transfer of malicious files. Therefore, signatures are designed specifically for this specific traffic. Let's look at an example of a targeted attack scheme for clarity.
APT attack
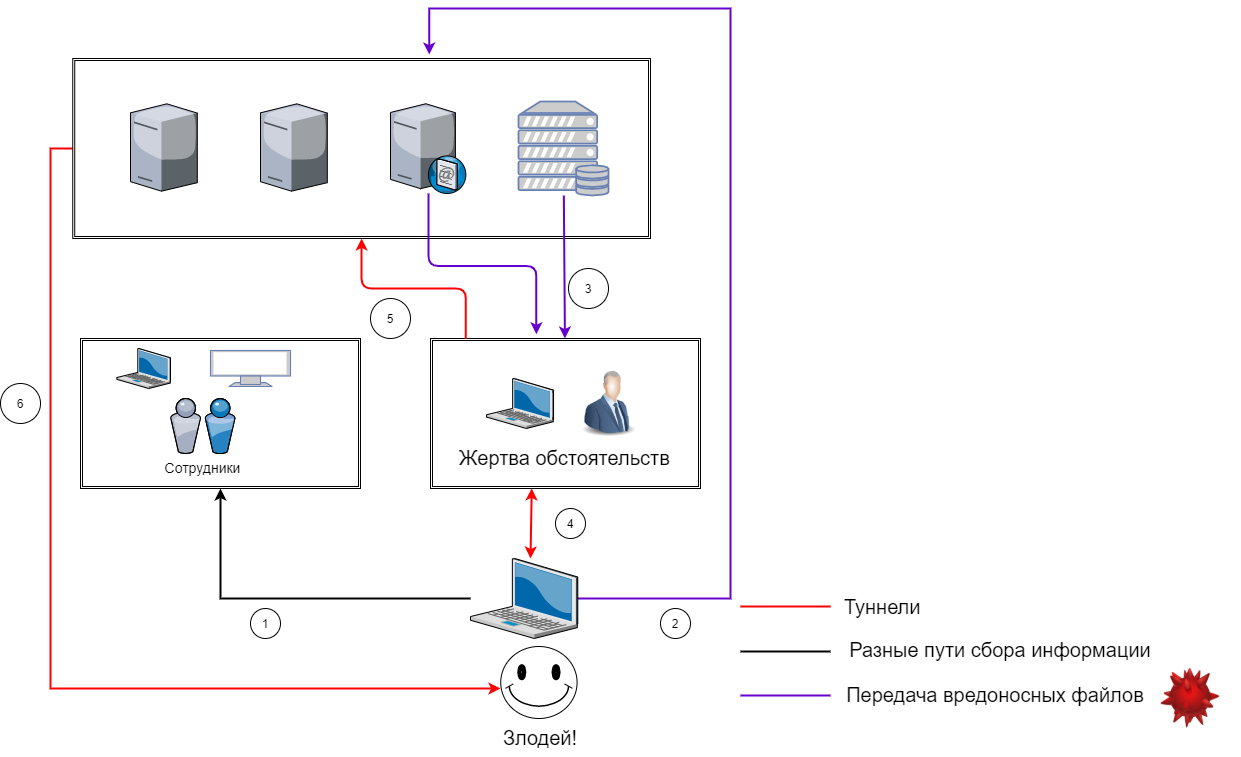
APT attack scheme:
- The attacker collects data about the organization and its employees, which he wants to penetrate. The most commonly used methods of social engineering and data from various open and closed Internet sources;
- , . , . , — , . ;
- . shell code, . . , , IPS/IDS , ;
- The malware executes and communicates with the attacker's command and control server (C&C). Moreover, this traffic may look legitimate, for example, an https session or an ssl tunnel;
- Next comes the propagation of the attacker's actions over the network, up to access to valuable information assets of the organization;
- And finally, the attacker gains access to the data, to which he has been trying all this time. It will also look like legitimate traffic.
Now let's look at how you can protect yourself from the above methods:
- Conduct digital literacy training for company employees. Also conduct simulated attacks for training both employees and information security specialists. As well as countering information leaks outside the controlled area by organizational and technical methods;
- (NGFW) anti-APT . , “” , . . , , ;
- , , . . . , , , , ;
- C&C . IPS/IDS . 2 : antibot anti-APT . , ;
- — NGFW ( , ) anti-APT ( ). . . , , . anti-APT.
From all of the above, the conclusion suggests itself that in order to counteract such attacks, a high level of information security in an organization, a well-built traffic inspection architecture, is required . Nevertheless, there is a possibility of a successful attack, which is why anti-APT solutions are gaining popularity more and more. Let's put forward the main functionality that the anti-APT solution should cover:
- Revealing the interaction of infected devices with the cybercriminals' command centers (signatures + database of C&C domains);
- Detection of the spread of viruses and exploits in the corporate network (signatures + detection of anomalies);
- Virus detection (scanning files in an isolated environment);
- Detection of malicious activity on hosts (agent solutions at local locations).
The solution for the third and fourth points will be discussed in subsequent articles, TDS Sensor covers cases 1 and 2 .
Next, let's look at the functionality of the TDS Sensor and its capabilities to detect malicious activity.
TDS Sensor Testing
As a generator of malicious traffic, we will use Kali linux, which will attack the user's network. The stand looks like this:

Distribution of malware and exploits on the corporate network
In order to test exploit detection, as an example, I took a host scan with the Openvas scanner in full and very deep ultimate format. This configuration adds dangerous plugins (an attempt to exploit various vulnerabilities) that can cause possible failures in the service or system.
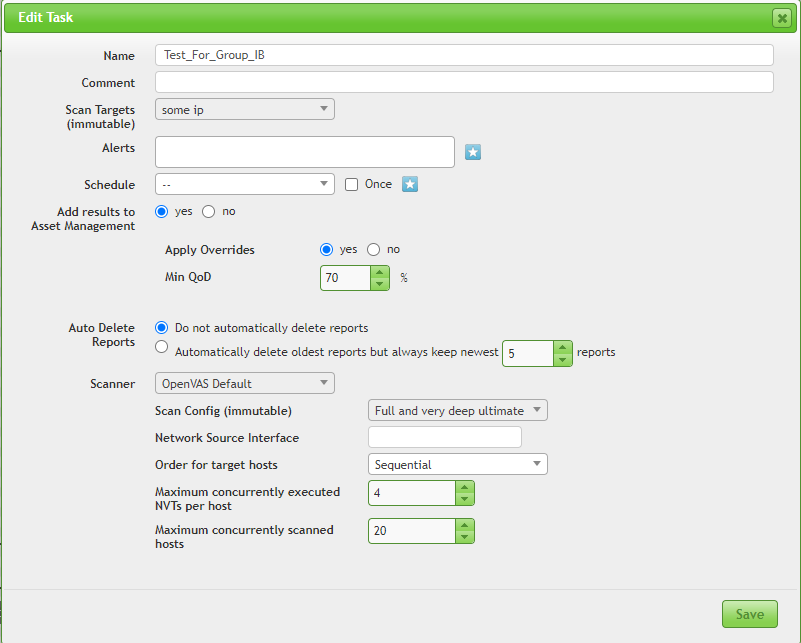
We look in TDS Huntbox to see if the TDS Sensor has been triggered and if any incidents have been detected (the picture is clickable): An exploit has been detected - EXPLOIT Possible ETERNALBLUE Probe MS17-010 (MSF style), you can read more details here . You can also perform a test from Group-IB . To do this, go to the website threattest.group-ib.tech
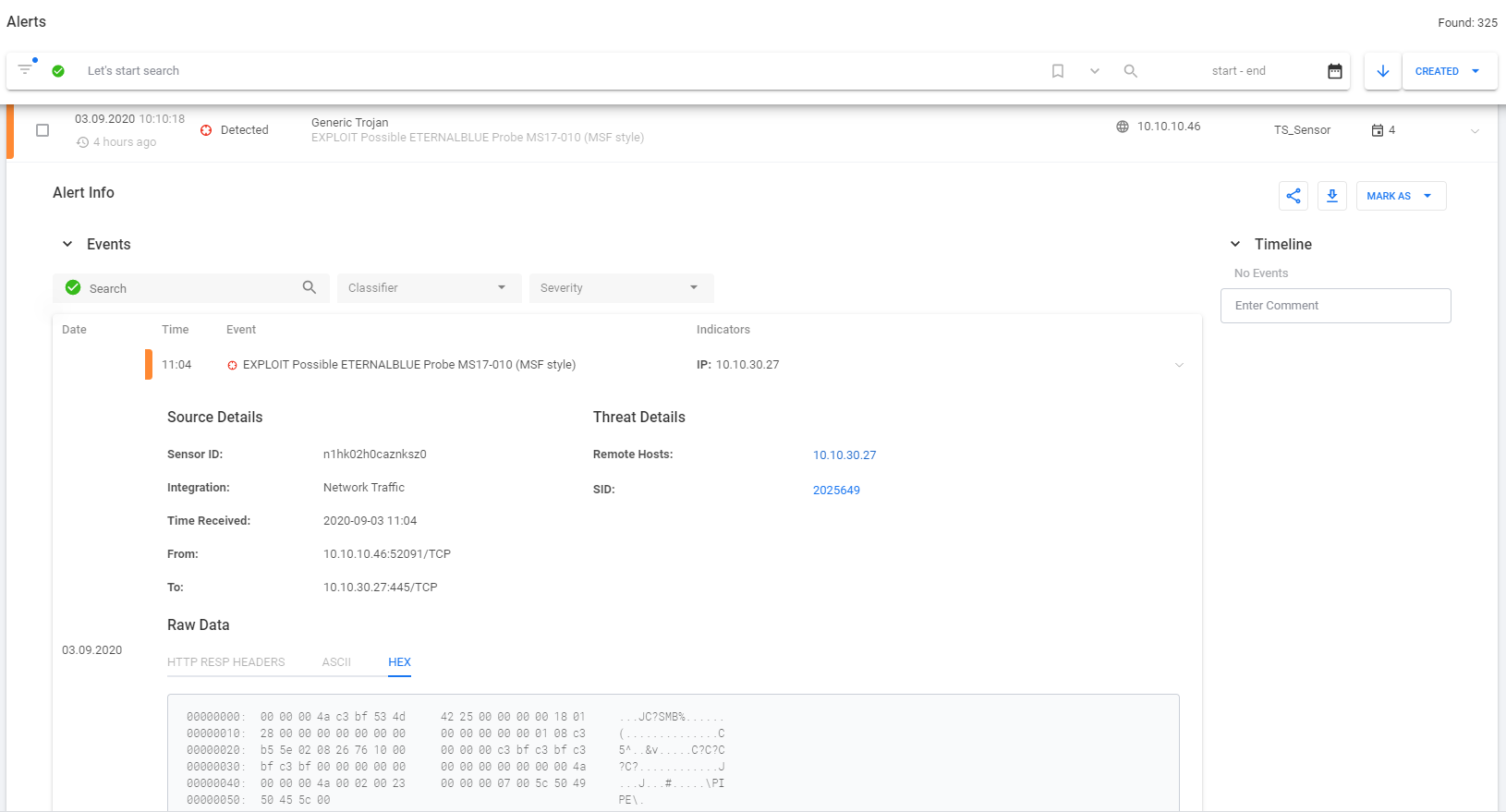
from the layout and start checking. A description of harmless malware is provided in the console:

We look at the reaction to TDS Huntbox (the picture is clickable): You can see a more detailed description (the picture is clickable):
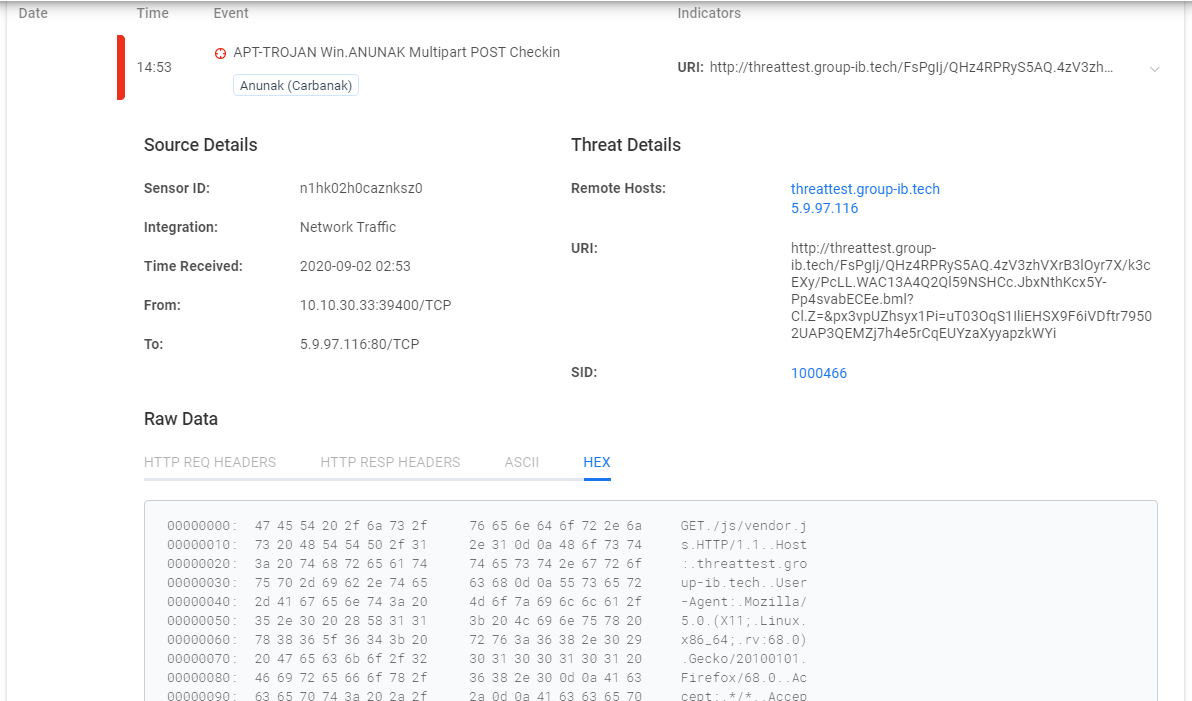
Interaction of infected devices with cybercriminal command centers
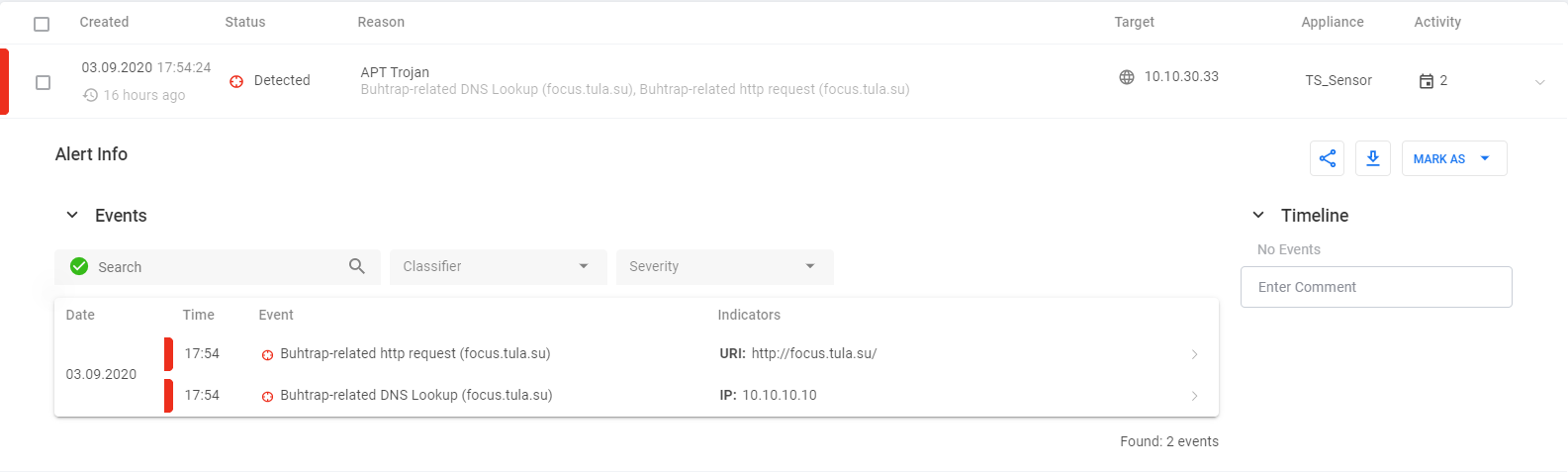
As a test, let's just try to switch to a domain used as CnC centers that belong to one or another group.

We check on TDS Huntbox if there was an incident (the picture is clickable): As you can see, the system first recorded a request to the dns server - DNS Lookup, and then went to a malicious site. When piloting a system, it is important to install TDS in an organization's infrastructure with valid threats, not just synthetic tests. An important part of the project is the correct arrangement of modules in the infrastructure, further we will consider several typical installation schemes.
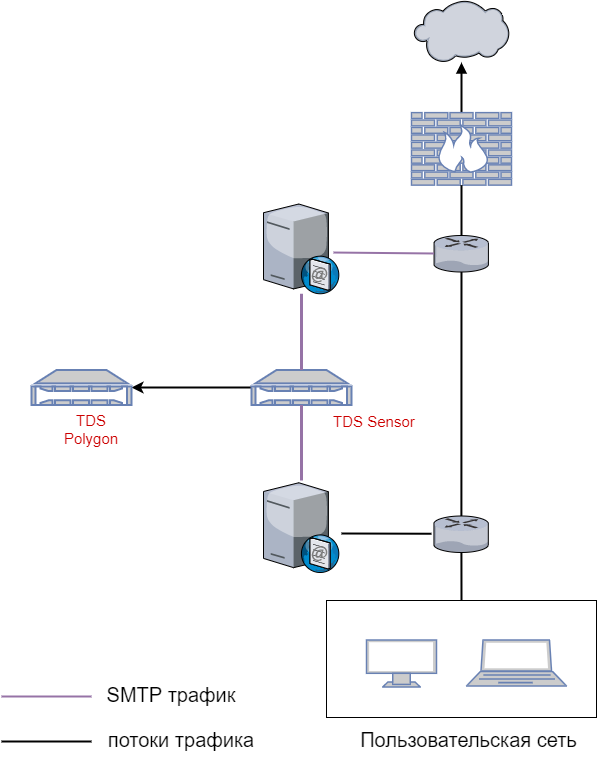
Implementation architecture
A typical scheme of operation of all TDS modules is shown in the picture below:

As you can see, almost all traffic from critical segments is mirrored on the TDS Sensor. This module is a constituent subsystem of the entire solution and covers the most dangerous sections of the network, through which a malicious file is more likely to arrive - checks mail, file storages, internal and external traffic. The device operates in mirroring mode, so the solution cannot influence the processes involved in legitimate traffic. Next, let's look at the use cases.
Checking mail
Several methods of receiving emails for behavioral analysis are supported:
- receiving letters via SMTP;
- receiving letters using the blind copy mechanism (BCC)
Receiving emails via SMTP
TDS Sensor acts as a Mail Transfer Agent (or SMTP Relay), receiving a copy of all incoming mail via SMTP, or standing in the cut between mail servers. In the latter case, it becomes possible to block emails with malicious attachments.
Receiving letters using the blind copy mechanism (BCC)
With this integration, an additional mailbox is created to which all incoming mail is copied. TDS Sensor connects to the prepared mailbox and collects letters for analysis.
File storage analysis

The mode implies behavioral analysis of stored and / or modified files inside file storages using TDS Polygon. The connection to the storage is implemented using the TDS Sensor module and supports two options for working with file objects:
- scanning all stored objects, including mutable ones or objects to which access is requested;
- scanning only mutable objects or objects to which access is requested - from the moment of integration.
Before changing the object and / or before sending this object on request to the user, TDS Sensor downloads the file and sends it for analysis to TDS Polygon. Upon receipt of the verdict, the analyzed object is either shifted back to the file storage, or, if a positive verdict is received (the file is malware), the object is deleted.
The following integration protocols are currently supported:
- WebDav;
- SMB;
- FTP;
- NFS;
Analysis of encrypted traffic
During APT attacks , the user receives an infected document or follows a phishing link with a high probability using the https protocol. Then the Trojan or shell code contacts the command center and downloads malware or provides a window to infiltrate the infrastructure, also over an encrypted connection. Accordingly, ensuring the information security process is impossible without opening https connections. Mirroring encrypted traffic on the TDS Sensor will not allow you to understand what is being transmitted in the session. Therefore, a TDS Decryptor is required , which will take over the decryption of sessions and transmission of traffic to the TDS Sensor.

TDS Decryptor is built into the client's network streams in such a way as to detect the initiation of SSL / TLS sessions, replace certificates (Man-in-the-Middle) for them and provide decryption of SSL traffic, thus increasing the visibility and control level of the protected infrastructure traffic. TDS Decryptor supports modern encryption algorithms and standards, including GOST (GOST2012-GOST8912-GOST8912, GOST2001-GOST89-GOST89);
You can also integrate TDS Sensor with other information security solutions:
- Integration with ICAP-proxy / DLP *;
- Integration with SIEM and other systems for analyzing information security events.
- Integration with monitoring systems (SNMP monitoring)
A very interesting feature of the system is the integration with the ticket system in CERT-GIB:
- ;
- Group-IB ;
- , .
:
In this article, we examined the capabilities of the TDS Sensor to detect APT attacks. It is worth mentioning that using this module alone does not provide full protection against APT attacks; solutions are needed to scan all files in an isolated environment and agent solutions. The use of all system modules and their correct implementation into the infrastructure allows you to close the threat of targeted attacks at all levels. All that remains is to quickly respond to all critical incidents.
In the future, we plan to publish detailed reviews for each TDS module separately, with various test examples. So stay tuned ( Telegram , Facebook , VK , TS Solution Blog ), Yandex.Zen . You can also watch the jointwebinar from TS Solution and Group-IB on the protection of industrial facilities.