
Synchronization of the messenger with contacts from the address book (contact discovery) is a very convenient function. When a new person installs the application, a large list of contacts is automatically added to it, and if someone installed the messenger for the first time, a notification about this comes to all his friends. Unfortunately, this feature can be used by government agencies and other attackers to track down people. The existing methods of protection are not yet very effective.
The scale of the leaks was estimated by experts from the University of Würzburg and the Darmstadt University of Technology (Germany), which conducted the largest study in history.with crawling of phone numbers in three messengers: WhatsApp, Telegram and Signal. The results are disappointing: WhatsApp and Signal are leaking user numbers on a large scale.
Although Telegram has very tight limits on the number of API requests, it is also not completely secure.
Closed Set Intersection Protocols
To search through contacts without disclosing information, cryptographic protocols for the intersection of private sets (private set intersection) are used. This technique computes the intersection of the input set of one side ("client") with the input set of the second side ("server") so that the client only knows the set of intersections and the server only knows the size of the input set of the client.
However, these protocols are currently not efficient enough for mobile applications with billions of users. In addition, PSI still does not solve absolutely all privacy issues, since it cannot prevent brute-force attacks.
Leaked social graph
At last year's USENIX Security 2019 computer security conference, a report was presented proving that many mobile messengers (including WhatsApp) make it easier to find contacts by uploading everything to the server.contacts from the user's address book, and subsequently store them on the server, even if no match is found. Thanks to this, the service can notify the user about new registered contacts, as well as build a complete social graph for each person. These columns are supplemented with information from other sources. The main privacy issue is that contact information can be leaked to the public and used for fraud, discrimination, blackmail, damage to reputation, or police investigations. The server can also be compromised, which leads to the disclosure of confidential information, even if the developers of the messenger themselves did not sell the accumulated base.
To protect against this threat, some mobile apps (including Signal) hash contacts. Unfortunately, the low entropy of phone numbers makes it easy to reverse (decrypt) hashes , so this protection is ineffective.
Crawling
But the main method of collecting contact information is crawling . Since the services usually have no restrictions on the registration of new users, you can register any number of fake accounts with a random set of contacts in the address book. Thus, you check the presence of each phone number in the database - and collect available information on their owners.
Services are not able to completely block such an attack, since users must be able to request information about contacts from the server. The only defense method is to limit the number of requests (see the table below in the section describing the attack).
With the help of crawling, a user base is collected. In addition to the phone number, this database may include other information that the user has indicated about himself and opened for everyone to see. What information will be included in the database depends on the privacy settings. Since the vast majority of users do not change the default settings, this aspect is also under the control of the messenger developers.
Previous scientific work has shown that by tracking the metadata of users in messengers (time of appearance on-line), it is possible to build accurate models of behavior .
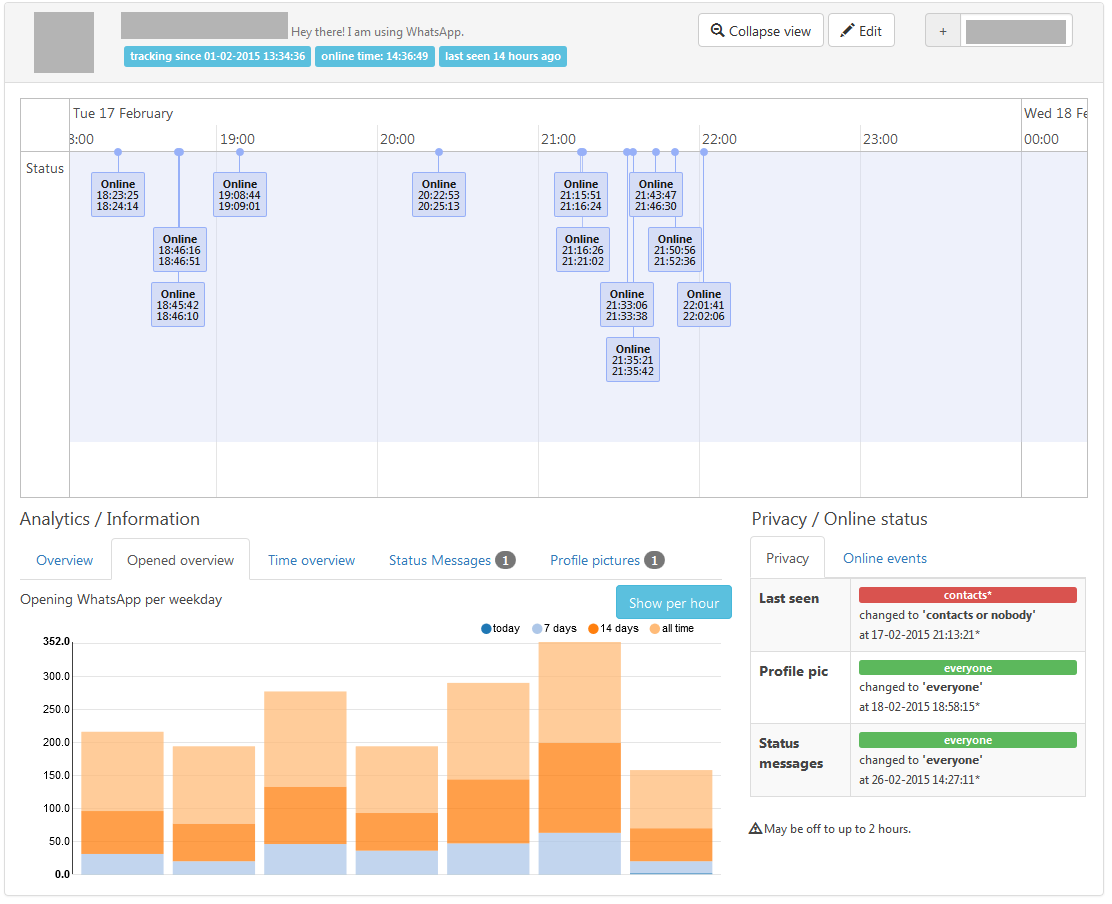
Comparison of this information with other social networks and publicly available data sources allows third parties to build even more detailed profiles .
In commerce, such knowledge is used for targeted advertising or fraud, from a personal point of view - for blackmail or planning a crime, and from the point of view of the state - to prosecute citizens . This is how the Hong Kong authorities calculated users who are members of the Telegram protest groups. The data of several thousand users of the Telegram channel were published in Russia in 2019 (as the investigation showed, the source of the data is the Ministry of Internal Affairs).

It is known that the Insider Telegram de-anonymization program works for crawling Russian users. The developers say that the enumeration of numbers allowed to compile a database of more than 10 million users. The service allegedly shows which phone number corresponds to the Telegram account.
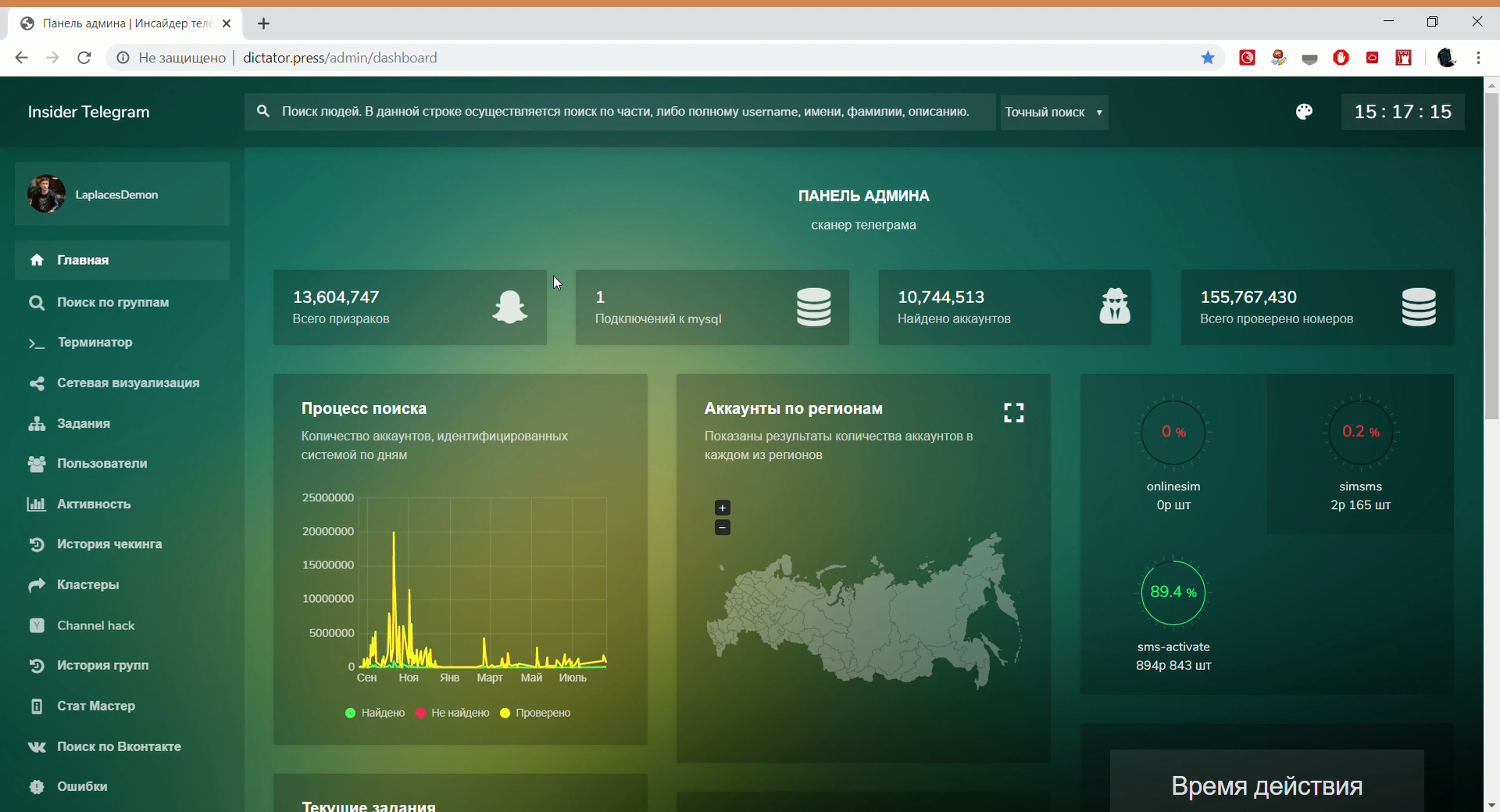
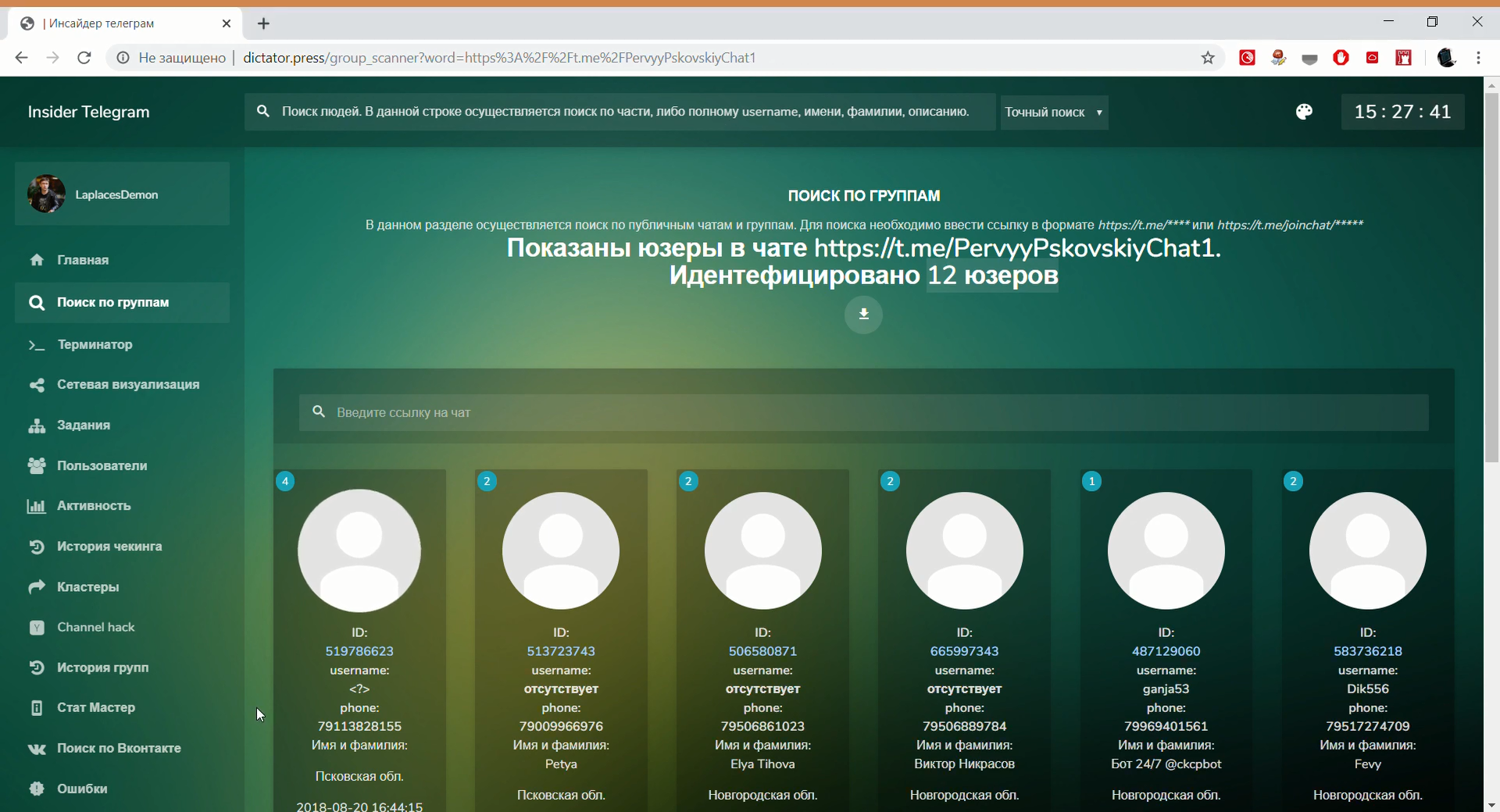
Insider Telegram works as part of the Laplace Demon system (only for legal entities and government agencies), there are rumors about a similar Cryptoscan system and other developments.
There is evidence that the power structures of Belarus are also beginning to use similar crawling techniques as in Russia, since Telegram has now become the main communication tool for citizens.
Attack on messengers: results
German researchers in their scientific work have demonstrated two types of attacks on instant messengers:
- hash reversal: creation of large dictionaries with all possible hash values for all phone numbers in the world, brute force in hashcat, rainbow tables of a new design.
- : 10% WhatsApp 100% Signal. .
| Signal | Telegram | ||
|---|---|---|---|
| 60 . | 120 . | 5 . + 100 | |
| UI Automator | () API | API | |
| 46,2 | 505,7 | 0,1 | |
| 10% | 100% | 0,02% | |
| 9,8% | 0,5% | 0,9% | |
| 5,0 | 2,5 | 908 | |
| () | 49,6 | 2,5 | 4,6 |
| : | |||
| — | |||
| — | |||
For crawling, the researchers used modest resources:
- free application Hushed for registering customers with new phone numbers;
- VPN subscription for changing IP addresses;
- one laptop with emulators of multiple Android devices.
To crawl WhatsApp contacts, an official application was launched in the emulator, with the interface of which the UI Automator framework interacted. To begin with, 60,000 phone numbers were inserted into the device's address book. If one of them is registered with WhatsApp, then their profile data was retrieved. New WhatsApp accounts were manually registered via fake Hushed phone numbers.
Communication with Telegram was carried out through the official TDLib library , which is released for many languages and platforms. Any application can be passed off as a Telegram client if you integrate the TDLib library and get an authentication token, which is done with minimal effort.
A Python script was written for Signal to send registration requests and search for contacts.
The researchers found out the limits on the number of requests in each messenger, as well as a number of other interesting facts. For example, that the Telegram API discloses confidential metadata, including about phones that are not registered in Telegram and about the number of users who have this unregistered number in their address book (see the description of the variable
importer_countin the Telegram API documentation ).
WhatsApp and Telegram transmit contact information in clear text (via encrypted channels). WhatsApp stores the numbers of registered users on servers in clear text, and hashes the numbers of unregistered users in MD5.
Signal does not store contacts from users' address books on the server. Instead, each client periodically sends hashes of all their contacts to the server to check against the database of registered users. But these hashes are easy to decipher.
conclusions
In a scientific paper, the researchers quantified the efforts made by attackers to collect sensitive user data on a large scale. Unfortunately, this is still possible even with relatively modest attack resources.
Now 50% of WhatsApp users have a photo of their account posted in the public domain, and 90% have their “About me” information open. Interestingly, 40% of users of the secure and private messenger Signal have fully open WhatsApp profiles.
Prior to the publication of this work, the results were sent to WhatsApp, Signal and Telegram. Signal has acknowledged the problem, reduced request limits, and promised to implement other anti-crawling methods. Facebook paid researchers a bounty for the vulnerabilities it found and deployed improved protection for syncing WhatsApp contacts. Finally, Telegram has developed additional countermeasures against data scraping within the established limits. Now the system is trying to determine the crawling of the base of numbers by specific criteria - and blocks it after 20-100 matches instead of 5000.
Today Telegram is the best messenger to fight users crawling. Following the 2019 Hong Kong protests with personal data leaks of protest group usersTelegram has tight limits and timeouts that make crawling a very difficult technical task.
According to the authors, currently the most effective protection measure for users is to revise their privacy settings. It is highly undesirable to leave the default values. For maximum security in conditions of government surveillance, it is better to register an account in the messenger with a fake number.
Advertising
Secure VDS for ordering which you need only your email, no other personal data! We use the latest branded hardware, each server is reliably protected from DDoS attacks.
