
At hacker contests and CTF (Capture The Flag) games, sometimes steganography puzzles come across: you are given a picture in which you need to find a hidden message . Probably the easiest way to hide text in a PNG image is to write it in one of the color channels or in the alpha channel (transparency channel). To identify such "bookmarks" there are special tools such as stegsolve , pngcheck and stegdetect , sometimes the contestants have to manually tinker with the filters in GIMP or Photoshop.
However, progress does not stand still - and recently, other methods of hiding data are increasingly used, for example, PNG-filling. Let's see how this is done.
Let's start with a little theoretical introduction to the "invisible" parts of PNG.
Alpha channel
When a picture is displayed on a computer screen, colors are created by combining red, green and blue components. These three color planes are called channels. They are usually written as RGB.
In addition to these three channels, PNG can have a fourth channel called alpha (denoted by the letter A) to determine the transparency level. The resulting RGBA image determines the visible colors and the degree of transparency.
In most graphics formats, the alpha channel is a value from 0% to 100% (or 0 to 255 in bytes). A value of 0% (black) denotes the place in the image where full transparency should be - here the RGB value is ignored, and the background under the image is fully visible. An alpha value of 100% (white) means that the RGB channels are completely opaque. Intermediate values determine how much to blend the background with the RGB pixel value.

PNG Alpha Gradient
The alpha gradient values are typically used to blend an image onto another image or web page. Alpha gradients are available in PNG, WebP, ICO, ICN, and other raster formats. GIF format only supports boolean (a pixel is either transparent or not).
The alpha channel is just one of the options for placing hidden text. Let's move on to PNG padding to write data directly to a binary file.
PNG content by columns
The PNG format is quite simple . Each file starts with a standard eight byte signature, here it decimal values
137 80 78 71 13 10 26 10. The first byte is selected outside of ASCII so that no editor will accidentally mistake the image for a text file. The next three bytes correspond to the letters P, N, G. Then a DOS line break (13 10), a DOS end-of-file marker (26) to keep the type program from printing out all the binary garbage, and a Unix newline marker.
After the header, chunks with a standard structure begin. First comes the IHDR block indicating the width and height of the image, the color space, the number of bits per pixel, the compression method, the filtering method, and the presence / absence of interlaced coding. Four bytes are allocated for the width and height, one byte for the other parameters.
This is followed by an optional tEXt block with text metadata, such as the name of the program that generated the PNG file. You can write plain text information into text blocks.
IHDR and tEXt are followed by IDAT blocks with compressed RGB or RGBA values for bitmap pixels. When rendering PNGs, it is processed by IHDR, a buffer is allocated in memory for the image, the data is extracted from the compressed format and written to the buffer pixel by pixel. The PNG file ends with an IEND block.
At the end of each block there is a CRC checksum for that block, which is calculated using the standard algorithm .
Typically PNG images contain 8 or 16 bits of information per RGB or RGBA channel, i.e. three to eight bytes per pixel. In this format, all the bytes are occupied with useful information about color and transparency, so that at the end of each line of the graphic image, we have no place to write arbitrary data.
But for steganography tasks, you need to know that PNG also supports lower color depth: 1 bit (2 colors), 2 bits (4 colors), and 4 bits (16 colors). In such a situation, it turns out that information about several pixels is stored in one byte. This is where the theoretical possibility for "horizontal" filling of PNGs with extraneous data appears. If the width of the picture in pixels is not a multiple of eight, then the last byte of the line contains unused bits, which together form a whole unused "column of pixels".
In the case of a 1-bit image, at the end of each line there may be up to 7 free bits that will not be processed by the parser. In the case of a 2-bit image, there are up to 3 free bits in the last byte. FotoForensics online toolfinds such unused "pixel columns" in PNG images .
However, PNG images with shallow color depth are very rare, so this method of steganography can be considered exotic. If you come across a PNG image with 2, 4, or 16 colors, this fact alone is suspicious and can initiate a check for PNG filling on columns.
A completely different matter is PNG-filling outside the borders of the picture. This is a simpler method of steganography that allows you to hide much more information in the image.
PNG -fill outside the picture
PNG post-pixel padding is often used in various games, puzzles and contests, not just hacking. This is how this method works:
- Take a PNG image (with any color depth).

- .

- PNG, .
- hex-.
- IHDR. IHDR.
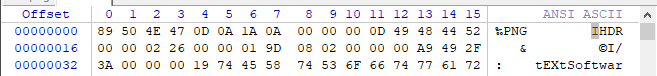
- IHDR — , — . c
00 00 01 9D(413 ), ,00 00 01 7E(382 ).
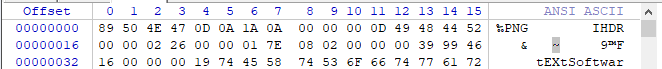
- CRC ( PNG CRC , IHDR), . CRC , PNG- IHDR.
.

Please note that the secret data remained at the bottom of the image. The file size has not changed: 335,906 bytes. It's just that the parser does not process these pixels now - and the bottom of the picture is not shown on the screen.
It is easy to guess that in the "secret" part of the picture, you can hide not only a text inscription, but also arbitrary data. For example, we can write a password-protected RAR archive there. The secret message picture can be published on Habrastorage or any other shared hosting. The message will be received only by the person with whom you have previously agreed on the method of transferring information and agreed on a password. In this way, malware can transfer payload through Habr and other public hosting services.
Advertising
VDS for hosting sites is about our epic ! All servers "out of the box" are protected from DDoS attacks, automatic installation of a convenient VestaCP control panel. Better to try once;)
