The topic is more than relevant: in the second quarter, millions of schoolchildren and students were forced to switch to online classes. Accordingly, the number of attacks both on users of distance learning platforms and on the platforms themselves has grown. In a study by Kaspersky Lab, it is impossible to separate educational services from general conferencing systems, so the report also provides insight into attacks on platforms such as Zoom and Google Meet.
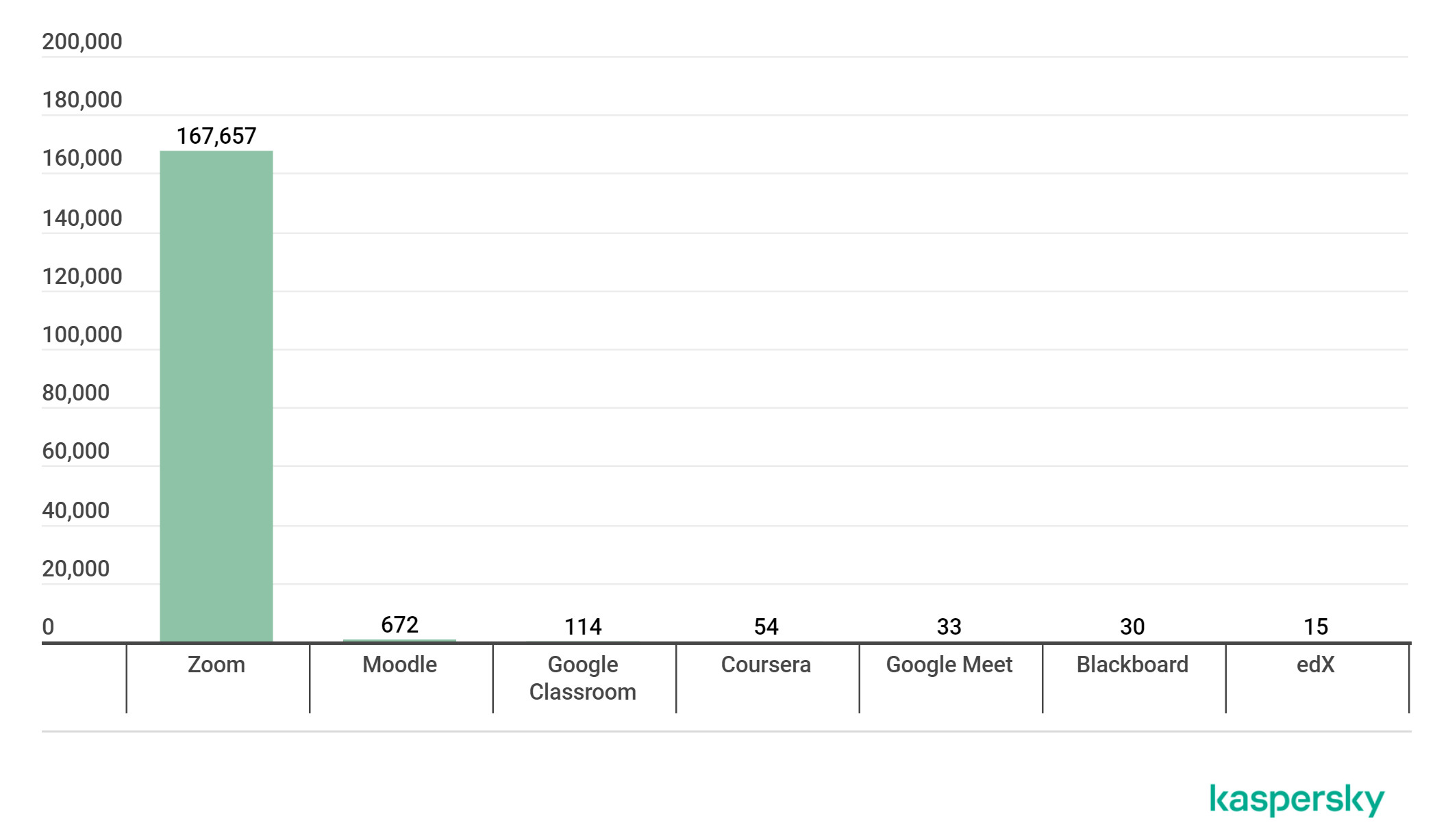
In addition to the Zoom and Google platforms, Kaspersky Lab specialists studied Moodle, Coursera, Blackboard and other educational services. The graph above shows the problem from an interesting angle: it is the number of blocked malicious programs that got on users' computers under the guise of software for a specific service.
Zoom, with its absolute leadership, breaks the schedule - the number of attacks on its users in the first half of 2020 has grown by 1400 times. In addition, the number of DDoS attacks on the services themselves has increased five times. The number of phishing attempts for conferencing passwords and training programs has also increased significantly.
Most often, fake Zoom clients install adware on victims' computers, but there is a chance of getting a Trojan or backdoor. Attackers do not even need to use malware to attack. The study provides examples of plausible phishing pages, including for proprietary online platforms at major universities.
Testimonies from university professors in the full report show that using online platforms is not easy in itself. Not to mention the growing safety risks for students, teachers and educational institutions in principle.
What else happened
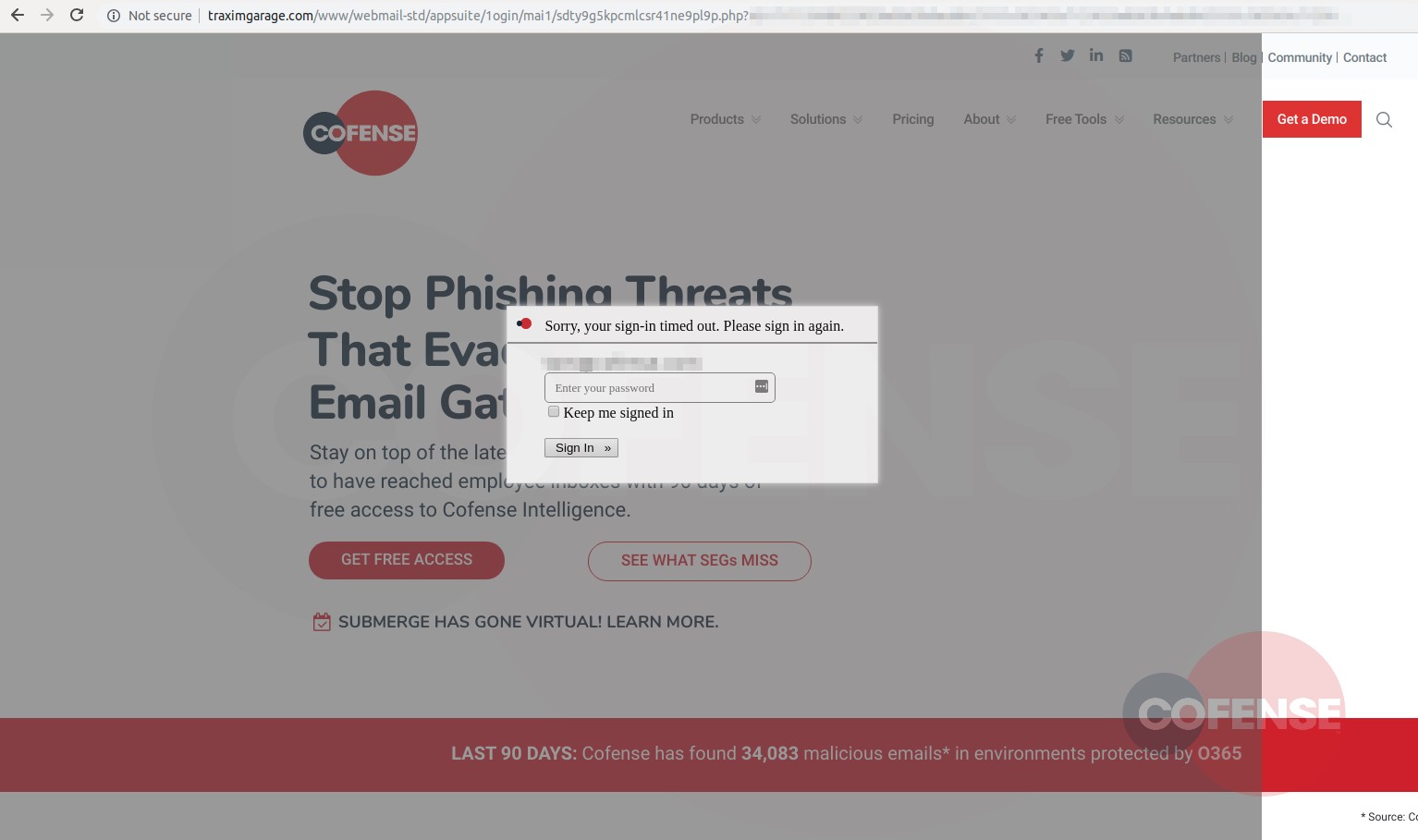
Cofense's research fits well with creative phishing . They found a slightly more plausible than usual method of stealing corporate email passwords using a cloud-based system (typically Office 365). The attack starts with a traditional fake email with a link, but clicking on it opens a phishing page, where the organization's real website is loaded in the background. In some cases, the e-mail of a potential victim has already been inserted into the input field.
Apple moderators accidentally " approved " the intrusive adware Shlayer to run on computers running macOS (see also the news on Habré). Also, Google Play has recently been removed from the app storesix Joker spy programs.
The cyber group Magecart, which specializes in stealing credit card data after an attack on online stores, began using the Telegram messenger as a communication channel with the C&C server.
Microsoft representatives announced the Video Authenticator service to combat deepfakes. It will not be available directly to end users - at least not a word about it in the announcement. The service is trained on the DeepFake Detection Challenge dataset. A recent competition of algorithms based on the same dataset showed average results - advanced designs identified a maximum of 65% of fakes. Vulnerability
fixed in File Manager WordPress plugin with 700 thousand installationsbut attacks on unpatched pages continue.
The WhatsApp messenger closed the six vulnerabilities. The news of this appeared on a new site, where Facebook developers plan to continue to disclose such information. One of the vulnerabilities allows you to find out the user's IP address - you just need to send a prepared sticker, which will start downloading a picture from an arbitrary site.
A critical vulnerability was found in the Cisco Jabber messenger , which allows executing arbitrary code on a victim's computer by sending a special message.
Google increasesthe budget of the bug bounty program, which should answer the question: "How can attackers use Google services to harm?" Mail, Forms, Disk and other corporate solutions are regularly used to send spam and distribute malware.