To get acquainted with the new electronic voting system and understand what role blockchain technology plays in it and what other components are used, we are starting a series of publications devoted to the main technical solutions used in the system. We propose to start in order - with the requirements for the system and functions of the participants in the process
System Requirements
The basic requirements that apply to any voting system are generally the same for both traditional face-to-face voting and remote electronic voting, and are defined by Federal Law No. 67-FZ of 12.06.2002 (as amended on 31.07.2020) “On Basic Guarantees electoral rights and the right to participate in a referendum of citizens of the Russian Federation ”.
- Voting in elections and referendums is secret, excluding the possibility of any control over the expression of the will of a citizen (Article 7).
- The possibility of voting should be provided only to persons who have active suffrage in that voting.
- One voter - one vote, "double" voting is not allowed.
- The voting process must be open and transparent to voters and observers.
- The consistency of the cast vote must be ensured.
- It should not be possible to calculate the subtotals of a vote before its completion.
So, we have three participants: a voter, an election commission and an observer, between which the order of interaction is determined. It is also possible to single out the fourth participant - the bodies that carry out registration of citizens on the territory (first of all, the Ministry of Internal Affairs, as well as other executive authorities), since active suffrage is associated with citizenship and place of registration.
All of these participants interact with each other.
Interaction protocol
Consider the voting process in a traditional polling station, with a ballot box and paper ballots. In general, simplified form, it looks like this: a voter comes to the polling station and presents an identity document (passport). A precinct election commission works at the precinct, a member of which checks the identity of the voter and his presence in the voter list, which was compiled earlier. If a voter is found, a member of the commission issues a ballot to the voter, and the voter signs for receiving the ballot. After that, the voter goes to the voting booth, fills out the ballot paper, and puts it in the ballot box. To ensure that all procedures are strictly observed in accordance with the law, observers (representatives of candidates, public observation institutions) are monitoring everything.After the completion of voting, the election commission, in the presence of observers, shall count the votes and establish the voting results.
The properties necessary for voting in the traditional voting system are provided by organizational measures and the established procedure for the interaction of participants: checking voter passports, personal signature for ballots, using voting booths and sealed ballot boxes, the procedure for counting votes, etc.
For an information system, which is a remote electronic voting system, this interaction procedure is called a protocol. Since all interaction with us is becoming digital, this protocol can be considered as an algorithm that is implemented by individual components of the system, and a set of organizational and technical measures performed by users.
Digital interaction imposes certain requirements on the algorithms being implemented. Let's look at the actions performed on the traditional site in terms of information systems and how this is implemented in the DEG system we are considering.
Let's say right away that blockchain technology is not a "silver bullet" here that solves all issues. To create such a system, it was necessary to develop a large number of software and hardware components responsible for different tasks, and connect them with a single process and protocol. But at the same time, all these components interact with the blockchain platform.
System components
From a technical point of view, the DEG system is a software and hardware complex (hereinafter PTC), which combines a set of components to ensure the interaction of participants in the electoral process in a single information environment.
The scheme of interaction of the components and participants of the DEG PTC system is shown in the figure below. Clickable
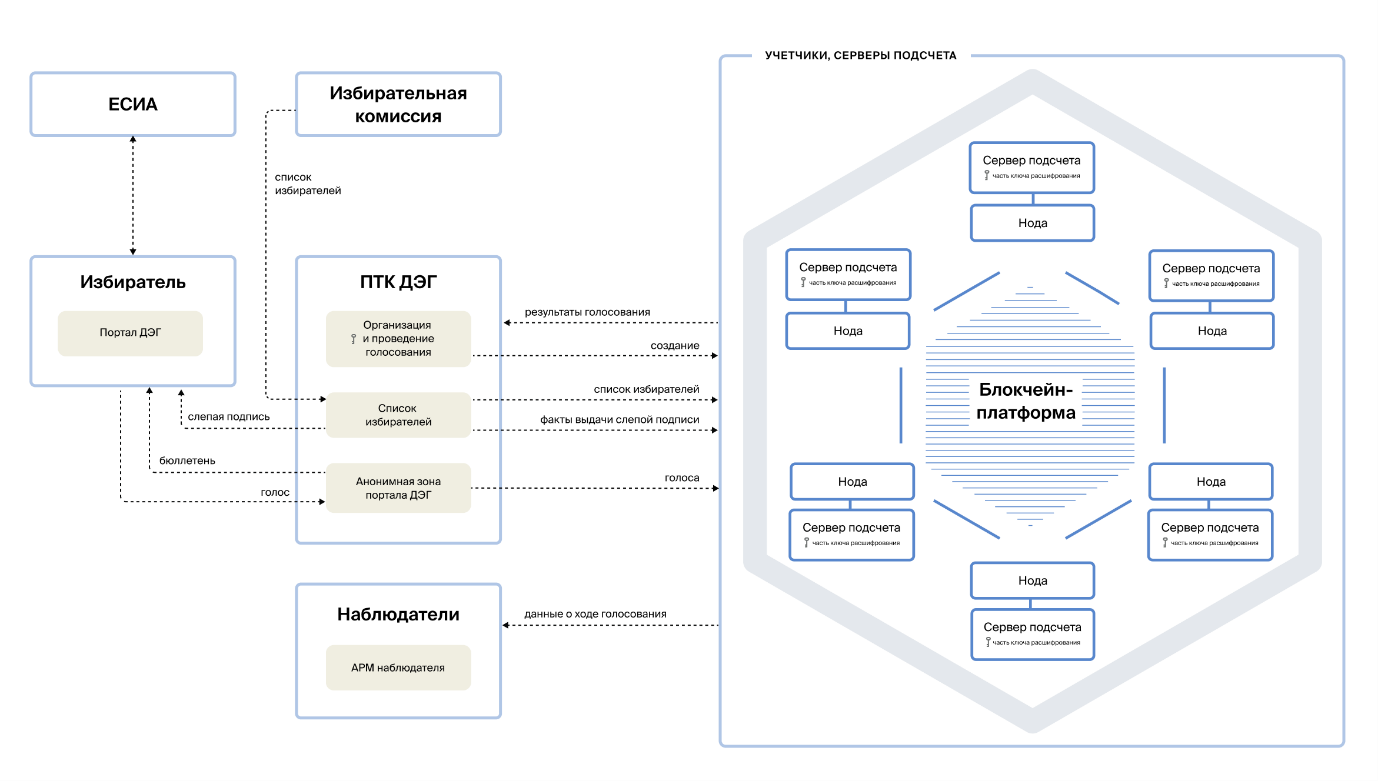
Remote voting process
Now let's consider in detail the process of remote electronic voting and its implementation by the components of the DEG software and hardware complex.
According to the Procedure for remote electronic voting, in order to be included in the list of participants in remote electronic voting, a voter must submit an application on the State Services portal. At the same time, such an application can only be submitted by those users who have a confirmed account and have been successfully matched with the register of voters, participants in the referendum of the GAS "Vybory" system. After receiving the application, the voter data is again checked by the CEC of Russia and uploaded to the "Voter List" componentPTK DEG. The upload process is accompanied by the recording of unique identifiers in the blockchain. Members of the election commission and observers have access to viewing the list using a special AWP located in the premises of the election commission.
When a voter visits a polling station, his / her authentication (comparison with passport data) and identification in the voter list takes place, as well as a check that this voter has not received the ballot before. Here is an important point - it is impossible to establish whether the voter dropped the received ballot into the ballot box or not, only the fact that the ballot has already been issued earlier. In the case of PTK DEG, a voter's visit is an appeal of the user to the DEG Portal- this is a site located at vybory.gov.ru As in the traditional precinct, the site contains information materials about the ongoing election campaigns, information about candidates and other information. To carry out identification and authentication, the ESIA of the State Services Portal is used. Thus, the general identification scheme is preserved both when submitting an application and when participating in a vote.
After that, the anonymization procedure begins - the voter is given a ballot paper that does not contain any identification marks: it has no number, it has nothing to do with the voter to whom it was issued. It is interesting to consider the option when the polling station is equipped with electronic voting complexes - in this case, anonymization is performed as follows: instead of a paper ballot, the voter is asked to choose from the stack any card with a barcode, with which he will approach the voting device. The card does not contain any information about the voter, only a code that determines which ballot paper should be provided by the device upon presentation of such a card. With fully digital interaction, the main task is to implement such an anonymization algorithm so that, on the one hand,it was impossible to establish any user identification data, and, on the other hand, to provide the opportunity to vote only to the user who was previously identified in the list. To solve it, the DEG software and hardware complex uses a cryptographic algorithm, known in the professional environment as a "blind electronic signature". We will describe it in detail in the following publications, as well as publish the source code, you can also collect additional information from publications on the Internet by keywords - "cryptographic protocols of secret voting" or "blind signature"We will talk about it in detail in the following publications, as well as publish the source code, you can also collect additional information from publications on the Internet using keywords - "cryptographic protocols of secret voting" or "blind signature"We will describe it in detail in the following publications, as well as publish the source code, you can also collect additional information from publications on the Internet using keywords - "cryptographic protocols of secret voting" or "blind signature"
Then the voter fills out the ballot in a place where it is impossible to see the choice made (closed booth) - if in our information system the voter votes remotely, then the only such place is the user's personal device. To do this, the user is first transferred to another domain - to the anonymous zone . Before moving on, you can bring up the VPN connection and change the IP address. This domain is where the newsletter is displayed and the user's choice is processed. The source code that is executed on the user's device is initially open - you can see it in the browser.
After the choice is made, the ballot is encrypted on the user's device using a special encryption scheme, sent and recorded in the "Distributed storage and vote counting" componentbuilt on a blockchain platform.
One of the most important characteristics of the protocol is the inability to find out the voting results before its completion. In a traditional precinct, this is ensured by sealing the ballot box and monitoring by observers. In digital communication, the best solution is to encrypt the voter's choice. The encryption algorithm used excludes the possibility of disclosing the results before the completion of voting. For this, a scheme with two keys is used: one (public) key, which is known to all participants, is used to encrypt the voice. It cannot be decrypted with the same key, you need a second (private) key. The private key, on the other hand, is shared between electoral participants (members of election commissions, public chambers, counting server operators, and so on) in such a way that each separate part of the key is useless.You can start decryption only after the private key has been collected. In the system under consideration, the key sharing procedure includes several stages: sharing a part of a key within the system, sharing a key outside the system, and generating a common public key. We will show in detail the process of encryption and working with cryptographic keys in the following publications.
After the key is collected and loaded, the totals are calculated for their further fixation in the blockchain and subsequent announcement. A feature of the system under consideration is the use of homomorphic encryption technology. We will describe this algorithm in detail in future publications and talk about why this technology is widely used to create voting systems. And now we will note its main feature: encrypted ballots recorded in the accounting system can be combined without decryption in such a way that the result of decrypting such a combined ciphertext will be the summed value for each choice in the ballots. In this case, the system, of course, implements mathematical proofs of the correctness of such a calculation, which are also recorded in the accounting system and can be checked by observers.
Below is a diagram of the voting process. Clickable

Blockchain platform
Now that we have analyzed the main features of the implementation of the remote electronic voting system, we will answer the question from which we started - what role does blockchain technology play in this and what tasks does it solve?
In the implemented remote voting system, the blockchain technology solves a certain range of problems.
- The basic task is to ensure the invariability of information within the framework of voting, and, first of all, the votes of voters.
- Ensuring the transparency of execution and the immutability of the program code implemented in the form of smart contracts.
- , : , , , .
- , , .
- , , .
Thus, we see that without the use of this technology, it is practically impossible to achieve the necessary properties in the voting system, as well as trust in it.
The functionality of the blockchain platform used is enriched with the use of smart contracts. Smart contracts check each transaction with encrypted ballots for the authenticity of electronic and "blind" signatures, as well as perform basic checks on the correctness of filling in an encrypted ballot.
At the same time, in the considered system of remote electronic voting, the "Distributed storage and counting of votes" component is not limited only to blockchain nodes. For each node, a separate server can be deployed that implements the basic cryptographic functions of the voting protocol - counting servers.
Counting servers
These are decentralized components that provide a procedure for distributed generation of a ballot encryption key, as well as decryption and counting of voting results. Their tasks include:
- Providing distributed generation of a part of the ballot encryption key. The key generation procedure will be discussed in the following articles;
- Checking the correctness of an encrypted ballot (without decrypting it);
- Processing of ballots in encrypted form to form the final ciphertext;
- Distributed decryption of final results.
Each stage of the cryptographic protocol execution is recorded in the blockchain platform and can be checked for correctness by observers.
To give the system the necessary properties at various stages of the voting process, the following cryptographic algorithms are used:
- Electronic signature;
- Blind signature of the voter's public key;
- El Gamal encryption scheme on elliptic curves;
- Zero knowledge proof;
- DKG (Distributed Key Generation) Pedersen 91;
- Private key sharing protocol according to Shamir's scheme.
The cryptographic service will be discussed in more detail in the following articles.
Outcome
Let's summarize some intermediate result of consideration of the remote electronic voting system. We briefly described the process and the main components that implement it, and also identified the means of achieving the properties necessary for any voting system:
- . . , .
- . , , . « » .
- . , . .
- . . -.
- . , .
- . , « ».