Introduction
Against the backdrop of the coronavirus pandemic, the popularity of cloud services has increased, allowing you to play video games. These services provide the computing power needed to run games and broadcast gameplay to users' devices in real time. The most obvious advantage of such a system is that players do not need to have powerful hardware. To start the service client and pass the time for self-isolation, a quite budget machine will be enough: all calculations take place on a remote server.
One of such cloud platforms is GeForce NOW from NVIDIA. According to Google Trends, worldwide searches for this service peaked in February. This correlates with the onset of restrictions in many countries in Asia, Europe, North and South America and other regions. At the same time, for Russia, where the self-isolation regime began later, in March, we see a similar picture, but with a corresponding delay.
Given the high interest in GeForce NOW, we decided to consider this platform from a security perspective.
Exploring the platform
At the time of our research, GeForce NOW was available in two versions - free and by subscription. Their difference is that when using the service for free, you must wait until a free virtual environment becomes available. In the case of the paid option, the virtual machine starts with a higher priority, and the player usually does not need to wait. In terms of security, both versions of the service are the same. For any violation of the rules for using the platform, the cloud runtime is immediately turned off, and the account of the offending gamer may be blocked.
The menu contains a list of games supported by the service. To play, you need an account from one of the digital content stores to which this or that game is already linked (if it is paid, then you need to buy it in advance). In this study, we're looking at the GeForce NOW and Steam store bundle.
When you click on the "Play" button in the main application window, a remote virtual environment is launched and streaming in real time from the server side to the user's device.
If the selected game has already been purchased, it will run in full screen mode, and other features of the virtual environment should not be available to the user. However, if the game settings allow you to select the windowed mode of operation in it, then we have the opportunity to access the Steam library. Another way to get into it is to choose a game that is not in the library yet.
It is already clear that we can execute arbitrary code if we exploit a vulnerability in a game supported by the service. The only limitation is that the exploit must be delivered over the network. Various scenarios are possible here. For example, if the exploit creates an executable module on disk, the service can theoretically prevent the payload from executing by tracking the creation of the executable file as the kiosk user (this is a standard user in GeForce NOW service virtual machines). On the other hand, if the shellcode is executed as a result of exploiting a vulnerability, the service will not be able to defend itself.
To conduct a full exploration of the environment of the virtual machine environment, we do not need to access cmd.exe or powershell.exe. But how do you get it? After wandering a little through the Steam library menu, we find a way that will allow you to run an arbitrary executable exe file already in the system. For this we will use the "Add a third-party game ..." function.
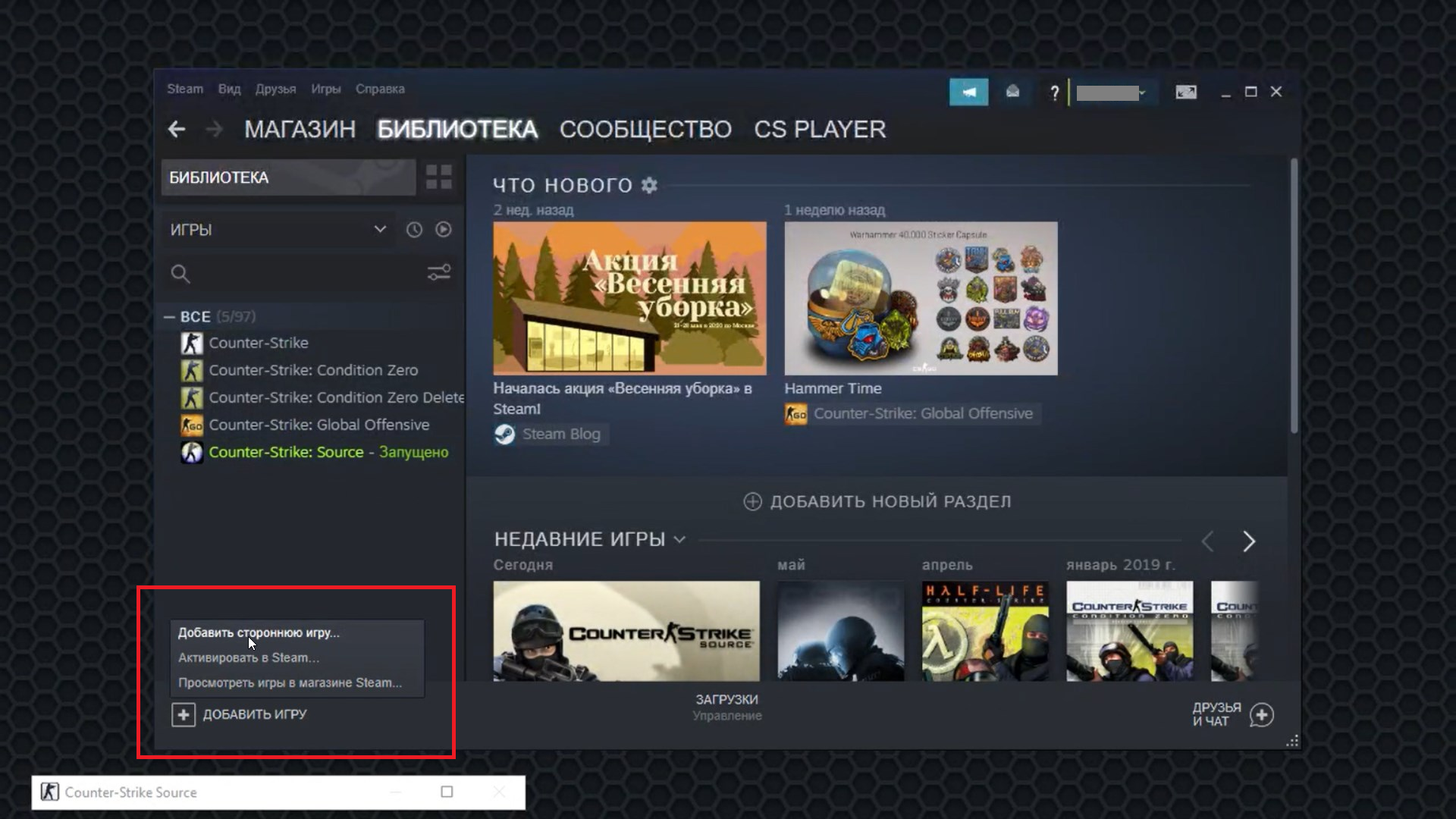
Normally, adding cmd.exe to the library as a third-party game would not be a problem. However, this feature is disabled in GeForce NOW, and clicking on the Browse button in the screenshot below does nothing. Nevertheless, you can choose one of the existing applications (and at the same time see what programs are installed in the bowels of the virtual machine). For example, let's choose the 7-Zip archiver (other programs are also great).

After adding 7-Zip to the Steam library, the program parameters can be changed. Here we fix the path to the cmd.exe file we need. Done! We launch our third-party "game" and get a working shell:

Now we can look around and find out where we are at all. Launch winver:

As it turned out, the service virtual machine is running on Windows Server 2019.
As a result, we can already do what is not provided by default with GeForce NOW virtual machines. But what else can we do, and how dangerous will it be?
According to the FAQ on the NVIDIA Vulnerability Reporting page, gaining access to cmd.exe on a GeForce NOW Service VM is not a vulnerability. This is due to the fact that in a virtual environment the user has minimal rights, and there is also filtering of launched applications. So, for example, after starting powershell.exe, the runtime will immediately stop.
Thus, for our research to be taken seriously, we need to solve two problems:
1) deliver the payload to the virtual machine, and
2) launch it by bypassing the application whitelist.
In the process of solving the first problem, we tried the popular LOLBINs for downloading, such as regsvr32, bitsadmin, etc. In all cases, the virtual machine crashed:
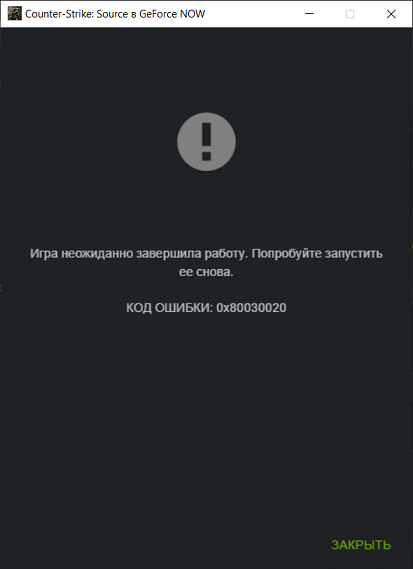
But the decision came by itself. GeForce NOW is a service for games (including multiplayer) where a game client can connect to a game server and download sounds, models, maps and other files from there. Therefore, we need to choose a game that will deliver an arbitrary file to the client. At the same time, we do not need to worry about the file extension, since we have access to the shell, and we can move the downloaded file to where we can use it.
But what about the app whitelist? After all, even if we manage to put a third-party application into a virtual machine, when it starts, it will crash. One of the solutions to this problem is to find an application from the trusted list for which we can implement dll hijacking. The most obvious goal is the gameplay.
So, let's try to implement this idea using the example of Counter-Strike: Source (hereinafter we will abbreviate it as CS: S). The first thing we do is create our own CS: S server, which will serve up a dll file under the guise of, say, a model (d.mdl). Next, we launch GeForce NOW to play CS: S and go to our server, from which a previously prepared "model" file is loaded onto the virtual machine. Now we minimize the game and run cmd.exe. Move the d.mdl file to "Counter-Strike Source / bin / user32.dll" and restart the game with the console command. Success: We ran arbitrary code in the context of a trusted process.
And they even recorded a video:
Conclusion
Despite the fact that attacks on service users are potentially possible, they are still unlikely. In addition, the risks for other users of the service will be minimal. The fact is that for each new gaming session, a clean virtual environment is launched in GeForce NOW. After the player has finished the session, the virtual machine is shut down and "reset". Therefore, even if the vulnerability is successfully exploited, the malicious code will be able to work only as long as the compromised virtual machine is running. And in order to attack other users, attackers will need to get out of the virtual environment using an exploit such as Virtual machine escape. Such exploits are rare and difficult to implement. But if successful, it is not just individual users that are at risk, but everyonewho launched a gaming session after the initial compromise of the service through one of the GeForce NOW virtual machines.
However, a simpler and more realistic attack scenario is to use a compromised virtual machine to mine cryptocurrencies, conduct DDoS attacks, and perform other illegal activities that require computing power.
After our contact, NVIDIA confirmed the problem and released a fix for their service.
Chronology of events:
18.04.2020 — NVIDIA
20.04.2020 — NVIDIA PSIRT
13.05.2020 — NVIDIA PSIRT ,
21.08.2020 — NVIDIA PSIRT , 30.08
02.09.2020 —
03.09.2020 — NVIDIA
04.09.2020 — NVIDIA
07.09.2020 — .