A source
S in IoT stands for SecurityWe have already written about Shodan more than once, including here. I would like to suggest once again running through the capabilities of this wonderful tool and the principles of its operation. I want to make a reservation right away that the situation with this search engine is quite classic for researchers in the field of information security - the tool can be used both with good intentions and strongly outside the law.
Disclamer:
Using the search engine itself is not punishable. Successfully entering an open control panel of an oil terminal node somewhere in Singapore and experimenting with opening the dampers are already punishable. Unfriendly people can come and knock. Therefore, be prudent and respect other people's space. We are against using Shodan for anything other than research purposes or analyzing our own systems.
I propose to once again go through the capabilities of this search engine, the peculiarities of its syntax and try to find something interesting. And let's not print War and Peace on other people's network printers.
People are careless
Channels became gigabit, tools like ZMap appeared, which allow scanning the entire array of IPv4 addresses in a few minutes. And still, there are still a lot of people who are sincerely sure that if you do not tell anyone about the raised service, then you can not bother with its protection.
Unfortunately, very quickly, first, automatic bots will come to you, and then real people, if something interesting is found. I forgot to turn off vsftpd in due time, which I raised for a while. As a result, a month later, I was surprised to notice that text files with spam, some small encrypted archives, and similar joys regularly appear and disappear inside.
If the problem were limited to junior admins and ordinary people who can forgive some carelessness and lack of qualifications, then I simply cannot justify companies that deliberately embed backdoors into their hardware products. The popular Hikvision and Dahua IP cameras are classic examples . There were similar stories with D-link routers, Huawei and other manufacturers.
And with the advent of the Internet-of-Things, with its “safe” approaches to implementation, everything becomes completely sad. Here you have smart bulbs without passwords that work with the external Internet via HTTP. Or even robotic vacuum cleaners that will be used to attack your internal infrastructure, as happened with Dongguan Diqee... It's generally fun - the vulnerabilities CVE-2018-10987 and CVE-2018-10988 allowed getting root rights, taking over control of the device, driving to the desired point and receiving an image from the device's infrared camera.
A similar story happened with LG Hom-Bot , where an attacker could intercept control and use an innocent vacuum cleaner as a point to invade someone else's network.
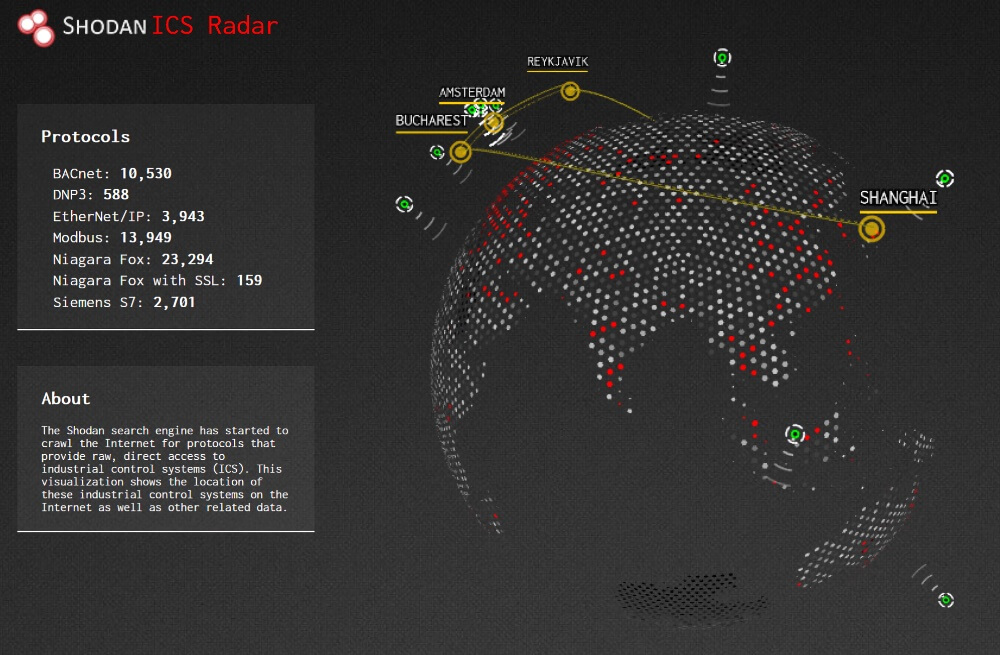
How Shodan Works
Things changed a lot when Shodan came along. Well, okay, in fact, everything remained the same leaky, but at least there was an opportunity to assess the scale of a particular disaster and try to reach the vendor to close the vulnerability. Shodan is essentially a hybrid of nmap -sV across the entire IPv4 range and search engine results. Crawlers scrupulously scan the entire Internet, try to connect to open ports, and fingerprint the service behind these ports.

An example of a search result for "vuln: cve-2014-0160".
In combination with search, this makes it possible to quickly estimate the number of vulnerable software versions after the publication of the next vulnerability.
The data for each post is stored in a structure that the developers call banner. This is how it looks:
{
"data": "Moxa Nport Device
Status: Authentication disabled
Name: NP5232I_4728
MAC: 00:90:e8:47:10:2d",
"ip_str": "46.252.132.235",
"port": 4800,
"org": "Starhub Mobile",
"location": {
"country_code": "SG"
}
}Depending on the amount of information received, a banner can contain many more fields that can be filtered and searched. By default, only the data field is searched, which is partly for security reasons. The data field will be very different in different banners, depending on the type of application, server or device.
HTTP/1.1 200 OK
Server: nginx/1.1.19
Date: Sat, 03 Oct 2015 06:09:24 GMT
Content-Type: text/html; charset=utf-8
Content-Length: 6466
Connection: keep-aliveThis is what a typical data field for an HTTP server would look like. You can see the main parameters and version.
Copyright: Original Siemens Equipment
PLC name: S7_Turbine
Module type: CPU 313C
Unknown (129): Boot Loader A
Module: 6ES7 313-5BG04-0AB0 v.0.3
Basic Firmware: v.3.3.8
Module name: CPU 313C
Serial number of module: S Q-D9U083642013
Plant identification:
Basic Hardware: 6ES7 313-5BG04-0AB0 v.0.3And this is how a much more unusual industrial controller Siemens S7 looks like. At this stage, it already becomes a little scary from what devices can stick around the Internet and get into search results. On the other hand, security through obscurity hasn't helped anyone yet.
A typical use case assumes that you give a general query to the data field, and then refine your search with numerous filters. The format of the request looks something like this:
nuclear reactor filtername1:value filtername2:value filtername3:value
Note that there is no space after the colon. In this case, at first, all records containing "nuclear reactor" in the general data field will be selected, and then all the listed filters will be applied sequentially to narrow the search objects.
A complete list of filters is available here . At the same time, some part is available only for paid accounts, for example "tag" and "vuln".
Trying to search
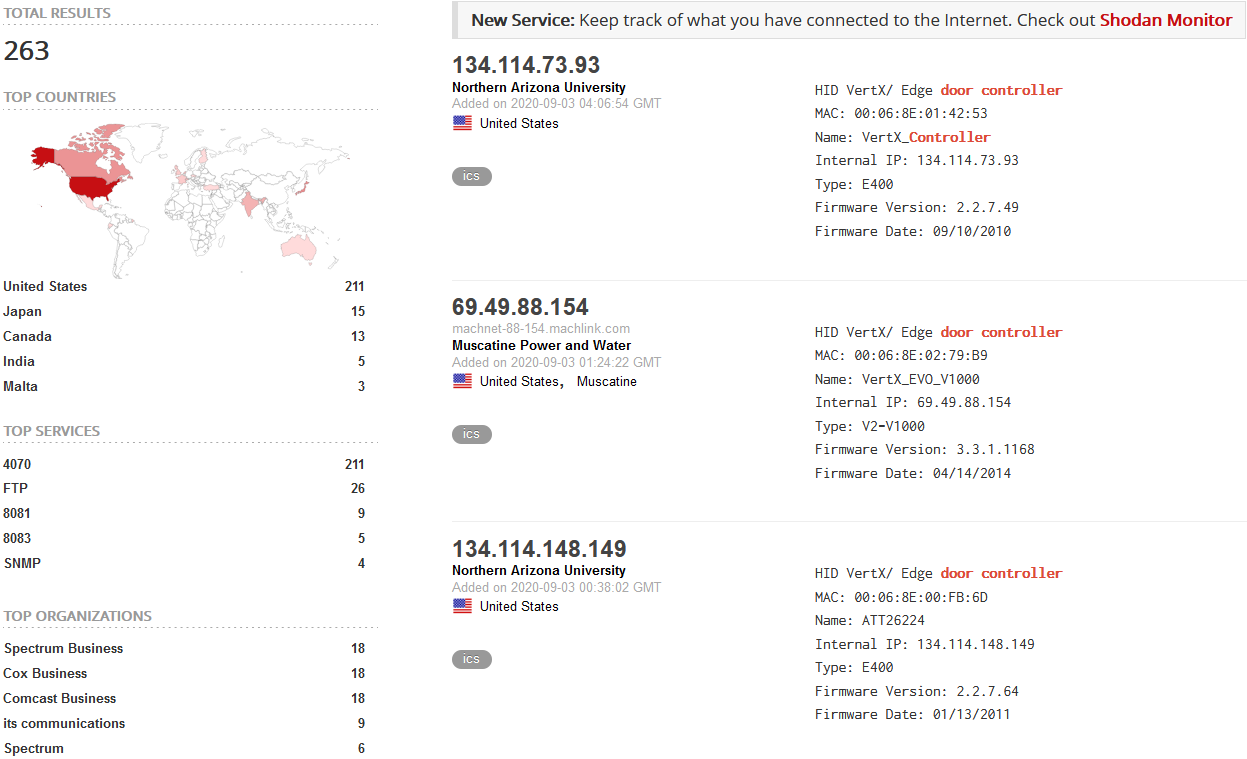
Let's try something like a door controller.
It's wonderful. Now let's look at all the HID VertX controllers owned by Spectrum Business.
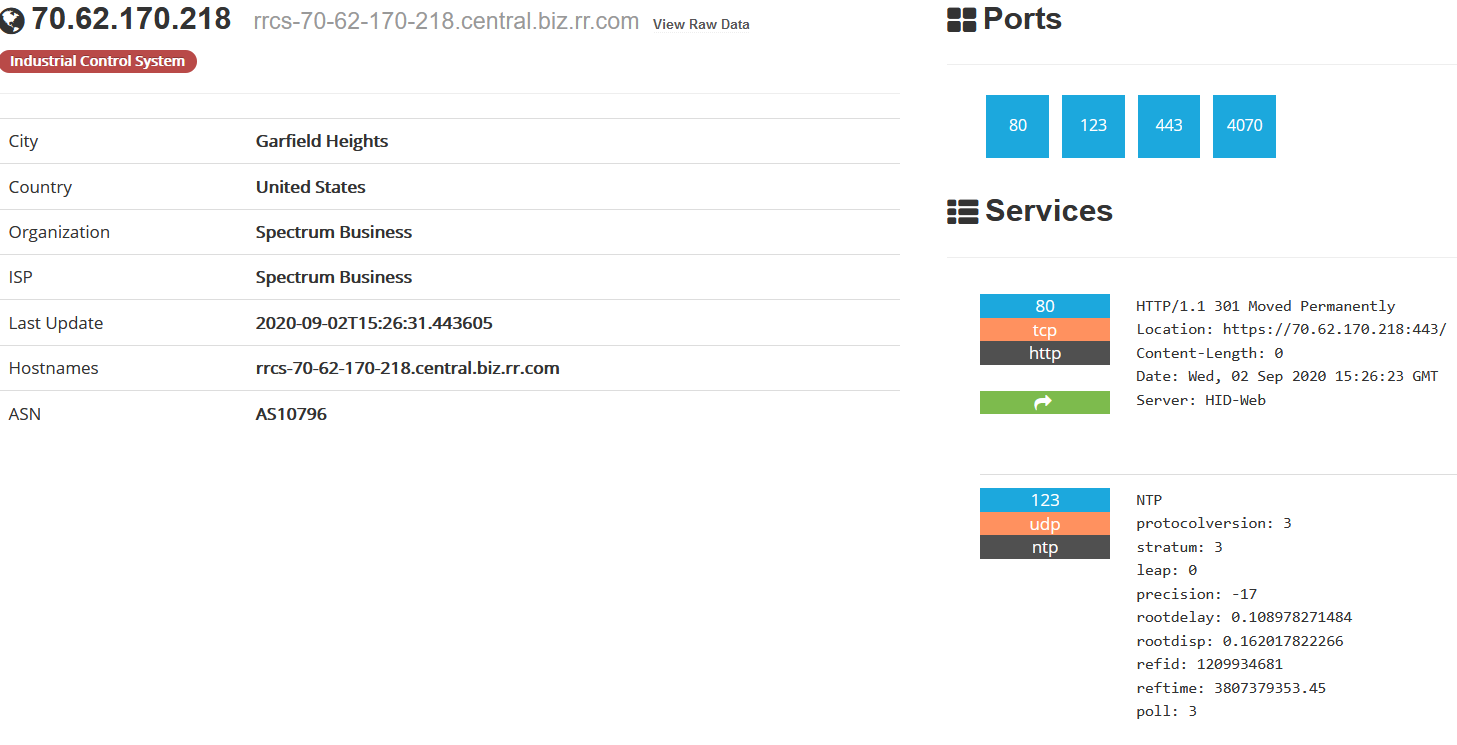
door controller org:"Spectrum Business"After that, by clicking on a specific host, a brief summary of the data collected on it is expanded. Or you can see the full output of the raw data.
Raw data by 70.62.170.218
Property Name Value
area_code null
asn AS10796
city Garfield Heights
country_code US
country_code3 null
country_name United States
data.0._shodan.crawler 4aca62e44af31a464bdc72210b84546d570e9365
data.0._shodan.id e85c3c1b-54ff-4194-8dc1-311da6851e5d
data.0._shodan.module http
data.0._shodan.options.referrer 5ee031c4-75c3-423f-99b8-5c06dd97cf14
data.0._shodan.ptr True
data.0.data
data.0.domains ['rr.com']
data.0.hash 0
data.0.hostnames ['rrcs-70-62-170-218.central.biz.rr.com']
data.0.http.host 70.62.170.218
data.0.http.html null
data.0.http.html_hash null
data.0.http.location /
data.0.http.redirects []
data.0.http.robots null
data.0.http.robots_hash null
data.0.http.securitytxt null
data.0.http.securitytxt_hash null
data.0.http.server null
data.0.http.sitemap null
data.0.http.sitemap_hash null
data.0.http.title null
data.0.port 443
data.0.timestamp 2020-09-02T15:26:31.443605
data.0.transport tcp
data.1._shodan.crawler 4aca62e44af31a464bdc72210b84546d570e9365
data.1._shodan.id 458e8be2-04df-4db7-8499-8e378792584e
data.1._shodan.module http
data.1._shodan.ptr True
data.1.data HTTP/1.1 301 Moved Permanently Location: https://70.62.170.218:443/ Content-Length: 0 Date: Wed, 02 Sep 2020 15:26:23 GMT Server: HID-Web
data.1.domains ['rr.com']
data.1.hash -788227878
data.1.hostnames ['rrcs-70-62-170-218.central.biz.rr.com']
data.1.http.host 70.62.170.218
data.1.http.html
data.1.http.html_hash 0
data.1.http.location /
data.1.http.redirects []
data.1.http.robots null
data.1.http.robots_hash null
data.1.http.securitytxt null
data.1.http.securitytxt_hash null
data.1.http.server HID-Web
data.1.http.sitemap null
data.1.http.sitemap_hash null
data.1.http.title null
data.1.port 80
data.1.timestamp 2020-09-02T15:26:24.253885
data.1.transport tcp
data.2._shodan.crawler 70752434fdf0dcec35df6ae02b9703eaae035f7d
data.2._shodan.id b7f280e3-cffc-4ddd-aa4b-1f9cd9e4d2be
data.2._shodan.module vertx-edge
data.2._shodan.ptr True
data.2.data HID VertX/ Edge door controller MAC: 00:06:8E:41:AB:81 Name: EdgeEHS400 Internal IP: 70.62.170.218 Type: EHS400 Firmware Version: 2.1.1.101 Firmware Date: 2018-05-03-11
data.2.domains []
data.2.hash -764264635
data.2.hostnames []
data.2.opts.raw 646973636f76657265643b3039313b30303a30363a38453a34313a41423a38313b456467654548533430303b37302e36322e3137302e3231383b313b4548533430303b322e312e312e3130313b323031382d30352d30332d31313b
data.2.port 4070
data.2.tags ['ics']
data.2.timestamp 2020-08-26T20:59:09.260224
data.2.transport udp
data.2.vertx.firmware_data 2018-05-03-11
data.2.vertx.firmware_version 2.1.1.101
data.2.vertx.internal_ip 70.62.170.218
data.2.vertx.mac 00:06:8E:41:AB:81
data.2.vertx.name EdgeEHS400
data.2.vertx.type EHS400
data.3._shodan.crawler 4aca62e44af31a464bdc72210b84546d570e9365
data.3._shodan.id 43663d5e-db76-4cba-8f14-6c1bf417ddd3
data.3._shodan.module ntp
data.3._shodan.ptr True
data.3.data NTP protocolversion: 3 stratum: 3 leap: 0 precision: -17 rootdelay: 0.108978271484 rootdisp: 0.162017822266 refid: 1209934681 reftime: 3807379353.45 poll: 3
data.3.domains ['rr.com']
data.3.hash -1317347992
data.3.hostnames ['rrcs-70-62-170-218.central.biz.rr.com']
data.3.opts.raw 1c0303ef00001be60000297a481e2359e2efff9972f64603e2f0016cc6b1f800e2f0016ceef1bb83e2f0016cef0fb34d
data.3.port 123
data.3.timestamp 2020-08-25T21:30:20.877776
data.3.transport udp
dma_code 510
domains ['rr.com']
hostnames ['rrcs-70-62-170-218.central.biz.rr.com']
ip 1178512090
ip_str 70.62.170.218
isp Spectrum Business
last_update 2020-09-02T15:26:31.443605
latitude 41.4344
longitude -81.6373
org Spectrum Business
os null
ports [80, 123, 443, 4070]
postal_code null
region_code OH
tags ['ics']
What else can you find interesting
In fact, what they just did not find. Both the control of the turbines of the hydroelectric power station, and the controller for the control of the cooling systems of the municipal ice rink. Here are some interesting and relatively harmless options.
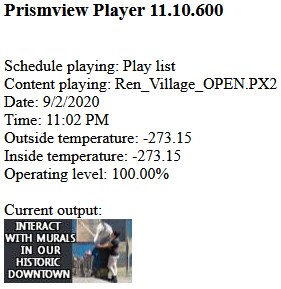
"Server: Prismview Player"Shows outdoor advertising panels. And forever temperature sensors show absolute zero.
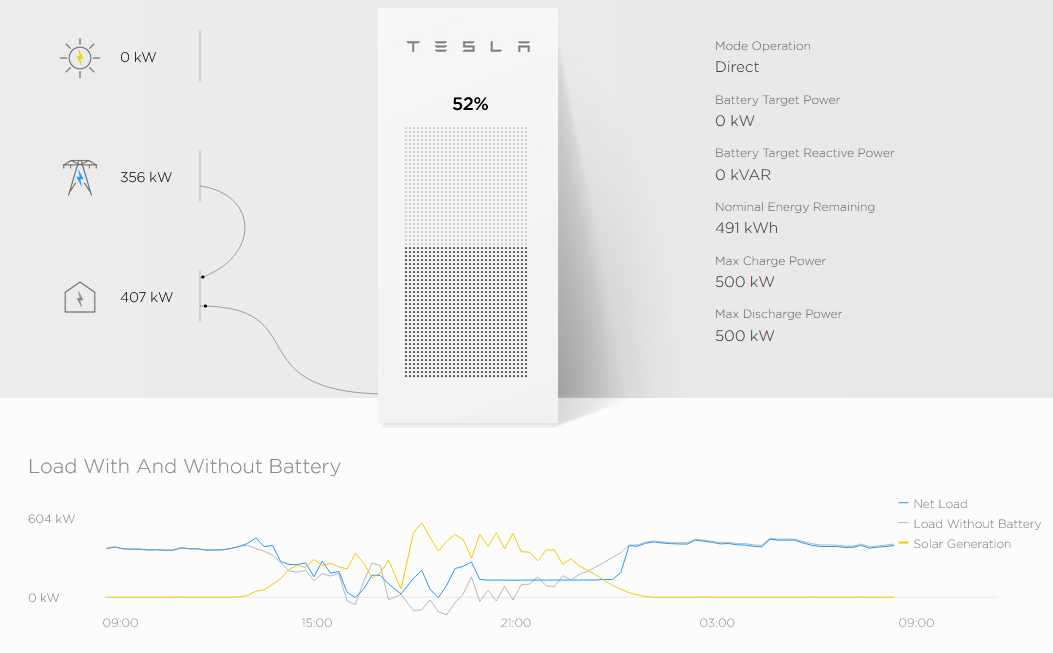
http.title:"Tesla PowerPack System" http.component:"d3" -ga3ca4f2Shows the current status of the Tesla PowerPack .
The internet is not the safest place
In fact, the lists available are simply endless. You can find the control panels of wind turbines and someone's media centers in Vietnamese, sticking out on the Internet. Stick to a few basic rules yourself and everything will be fine.
- If the device can work offline - do not expose it to the Internet
- If you really need to expose the device to the Internet, you don't need to forward access to it directly. Use a VPN to connect to your network
- —
- ,
