
Hello, Habr!
Today we will talk about how the provider's vulnerabilities were found, let's say: example.ua
Well ...
Let's start!
First stage: Analysis
First, you need to collect as much information as possible about our victim. After all, as you know, you cannot close all the holes.
Let's start by looking for possible subdomains and connected DNs.
Launch Sublist3r.
During the scan, I came across the domain of their mail service mailer.example.ua from which letters were sent to clients.

On it there was the possibility of free registration, which I immediately took advantage of.
Second stage: Testing the service
"If the doors are open, then they are waiting for us inside!"
After a while, on this service, several XSS and CSRFs were found with the possible possibility of capturing an account and the most delicious IDOR.
While studying the service, I discovered the ability to create my own custom mailings and edit others.
Also, in addition to this, I could view other people's mailings in which very sensitive data were encountered.
There were already quite serious holes for account hijacking and private information disclosure, but curiosity drove me forward and I continued my excavations.
Shell Upload
The site has the ability to upload your own files, but with some restrictions.
Let's try to fill the shell!
I tried to fill in a simple php shell, it loaded successfully but I could not find the file path. When I tried to send a letter with this file, I got an error in the Yii2 code, apparently the service is based on this framework.
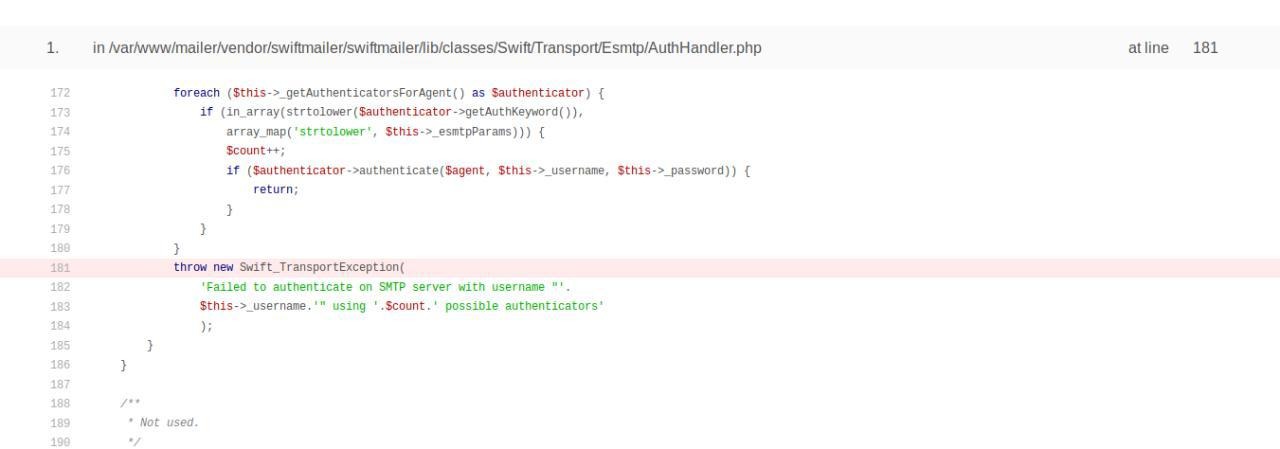
A bit of black witchcraft and this limitation was circumvented.
I generated the shell using the Weevely utility and renamed the file shell.php.jpg, which usually helps to fool most of the not-so-smart upload filters. After sending such a letter, there was no longer an error.
But I still couldn't find my way to my shell.
Attempts to iterate over directories led me to / images /
which contains all the uploaded files on this service.
Quick search by name and I find my shell!
We connect and ...

On this you can hand over the vulnerability. There are exits to the provider's database, customer lists, site sources and many other nice things.
I passed a report describing the vulnerability to the site administrators, and they decided to completely disable this service. That's all, thank you for your attention!
Author:xalerafera
Edit & rewiew: AlexShmel