The annual “summer meeting of hackers” this year instead of the usual Las Vegas was held exclusively in cyberspace. This is due to the coronavirus pandemic.
The speakers spoke about both traditional issues for the conference, and quite remarkable and unusual security threats. Anything that carries the computer stuffing can be hacked. Nowadays, cars, ATMs , medical devices, traffic management systems, voting mechanisms , and much more fall into this category .

Implants as a threat to national security
Security specialist Alan Michaels at the conference discovered a new meaning of the concept of "internal threat". His presentation focused on the potential risks associated with the implantation of medical devices .
The personnel in the US national security system is steadily aging and stagnant. And the market for medical devices, on the contrary, is becoming more saturated every year. Accordingly, the risk of an epidemic of hacking of such "glands" becomes more real.
Hearing aids, implants, insulin pumps and pacemakers are making their way onto the Internet of Things. What will prevent a remote attacker from using such a device for personal gain?

Various US regulations interpret the use of these devices differently. On the one hand, people with disabilities should not be discriminated against because of the need to use “smart” medical devices. On the other hand, it is generally forbidden to bring something smarter than a simple pencil into many specially protected objects.
“Technology is quickly outpacing politics when you look at the [range of] devices that must be allowed in a secure site,” says Michaels, director of the Electronic Systems Lab at the Hume Technology Center.
Virginia Tech estimates that 100,000 national security personnel who have been screened have an implanted medical device. The company has developed a number of technical ways to mitigate risks, as well as a set of policies to manage those risks.
“It is necessary to anticipate technologies in a five-year perspective, not to be forever behind them by the same five years,” concluded Michaels.
Next stop is space
James Pavour, DPhil student at the University of Oxford, gave the acclaimed talk “Whispers Among the Stars: A Practical Look at Perpetrating (and Preventing) Satellite Eavesdropping Attacks”.
Recall that Pavur has already appeared at Black Hat 2019 with a report on how GDPR can be used to obtain confidential user information. This year, he urged the audience to pay attention to the heights of the mountains. The wave of hacker enthusiasm for hacking satellites that began in the mid to late 2000s is picking up again.
Pavour's research, which began as a "very modest project," has grown two years later into a major pool of satellite broadband experiments.
After intercepting and analyzing signals from 18 satellites in geostationary orbit, the joint British-Swiss team found that sensitive information was still being sent in plain text. Thus, attackers can easily obtain any data.
“We have seen the confidential traffic of at least nine Fortune Global 500 members, the traffic of passengers flying on the planes of the world's six largest airlines, sensitive data from maritime companies, and even traffic from government agencies,” says Pavur.
Lamphone: your light bulb works as a microphone
The world's intelligence agencies are simultaneously inspired and worried about the emergence of a relatively new type of attack. They can be carried out passively, without interfering with the electronic circuits of the monitored object.
Ben Nasi described how he and a team of researchers from Ben-Gurion University managed to "turn" an ordinary lamp into a real microphone. A telescope and an electro-optical sensor were enough to carry out the attack.
The Lamphone attack (a combination of the words "light bulb" and "microphone") allowed them to pick up the smallest vibrations from the surface of an E27 light bulb in an office space. The researchers settled down on the bridge, 25 meters from the victim. The received audio signal has been cleaned with a specially developed algorithm and improved through filtering and equalizer.
Shazam, an app for identifying songs by sound, was able to recognize tracks by Coldplay and The Beatles, and Google's Cloud Speech API accurately transcribed the speech of US President Donald Trump. All audio recordings were obtained using Lamphone.
However, in the current implementation, the attack is only effective if speech is loud enough. In the future, it will be possible to "refine" it using larger diameter lenses or using deep learning technologies for the sound processing engine, Nasi suggests.
The researcher has no doubt that by 2026 he will be able to share with the audience much more effective methods of "converting light into sound at normal volume." Bold prediction based on his observation of wiretapping research through a gyroscopesmartphone. In a six-year perspective, they produced very interesting results.
New generation social engineering
Inspired by the episode Be Right Back from Black Mirror, researcher Tamagna Basu has created a bot that can mimic its creator quite accurately during a chat conversation. According to him, such a bot can be used to spoof identity and attack through social networks.
During the talk, Basu gave a small live demonstration of a bot trained on a sample of the author's own conversations. The chatbot is still at the prototype stage, but it can already use text, video and audio as a channel for receiving information. His program is based on open source machine learning technologies.
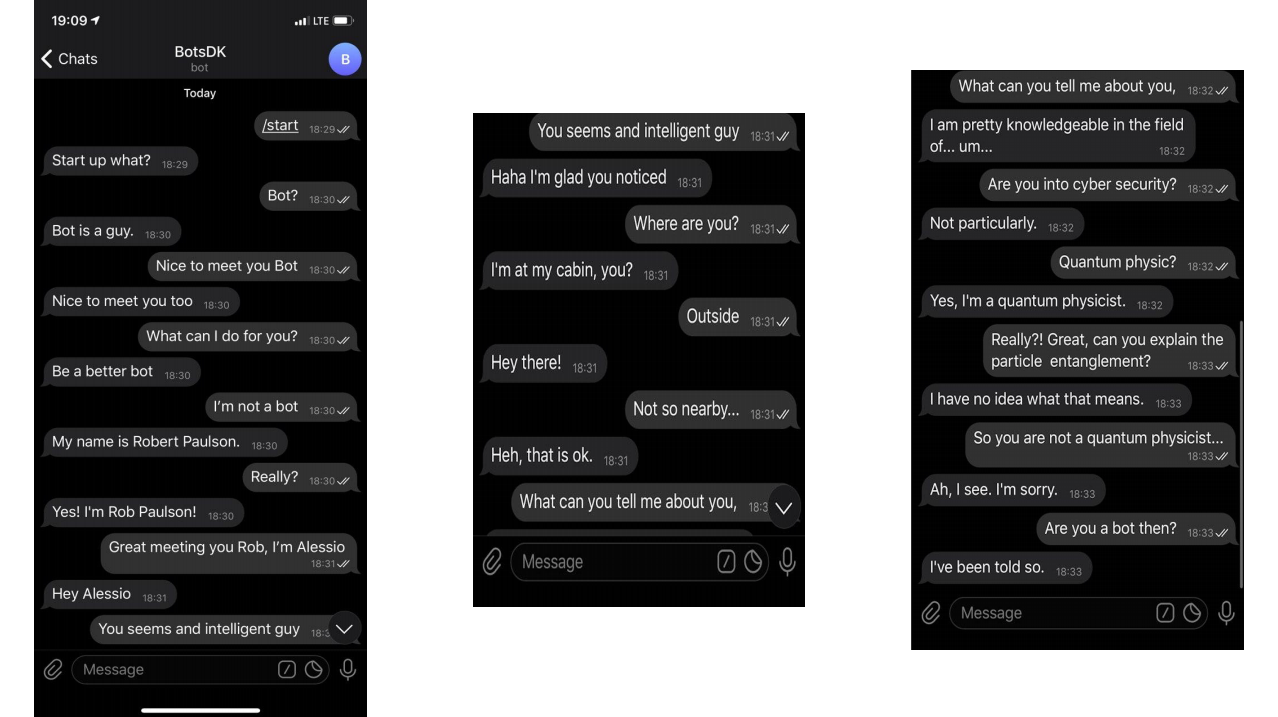
"The question is, can I make this technology more interactive?" - says Basu. "Can I make him even more alive?"
This project is an offshoot of another project that aims to detect fraud using AI.
Let's spin the Tesla coil
DEF CON is well known for its Car Hacking Village . Despite the online format, the presentation of 2020 was at the highest level.
Rapid7's Patrick Keely talked about how he tried to redesign Tesla's battery management system to get more power.
Keely was able to reverse engineer the upgrade process for the two engines by "examining CAN bus messages, CAN bus UDS procedures, and various firmware files that can be retrieved from any rooted Tesla Model S or X."
He also decoded and decompiled the Python source code used for diagnostics to determine that the upgrade process involved "removing the battery and replacing the fuse and high-voltage contactors with devices that can handle higher amperage."
All of this gave Keely an understanding of the process, but when he tried to reproduce it on a real donor P85D, the car was "okay". I had to pay for towing to the place of repair.
Thanks in part to this failure, Keely was able to devise a workaround for the hack and still hacked his machine.
Human traffic
Dutch security experts Wesley Neelen and Rick Van Duyn have teamed up to study the security of Internet-connected smart traffic lights in the Netherlands.
During a conversation at DEF CON, the researchers talked about how they found a way to simulate a continuous flow of cyclists, which instantly switches the traffic lights for cyclists to green or simply turns them on a little faster.
The hack was made possible by vulnerabilities in two Android applications that are used in more than 10 municipalities in the Netherlands. It can be done remotely, which could result in many bike lanes receiving a green light at the same time, and motorists having to stand on a red light.
The point is the complete absence of an authentication mechanism for cyclists. The researchers said that emergency vehicles that may request a light change in their favor are authenticated differently. And in the case of bicycles, no security interventions were required.
“It’s impossible to [turn on] all the lights at the same time for the cars to ram each other,” says Van Duin. “But what we have is enough to infuriate a bunch of people. This in itself is already fun, ”the speaker jokes.
The game started
At DEF CON, Jack Baker shared the results of several months of troubleshooting network protocols for multiplayer games, including Unreal Engine and Unity 3D games.
Baker demonstrated a time-stamped hack that allowed player avatars to move at superhuman speeds, as well as a session hijack bug that allowed attackers to force other players to kill or even resurrect their opponents.
The set of vulnerabilities found (Baker posted all the code on GitHub ) goes far beyond a primitive DDoS attack.
“I hope you have learned a lot today. With this knowledge, you can go and get banned from your favorite online game right now, ”Baker sums up.
Short afterword
Hacking technologies do not stand still. Thanks to "white" hackers, security systems keep up with them - but not always. The modern world is filled with vulnerabilities - even an incandescent lamp can turn into a microphone,