And so, there was a person who offered to generate a database for creating a password literally with his own hands, without the participation of software. Only absolute random, driven by gravity.
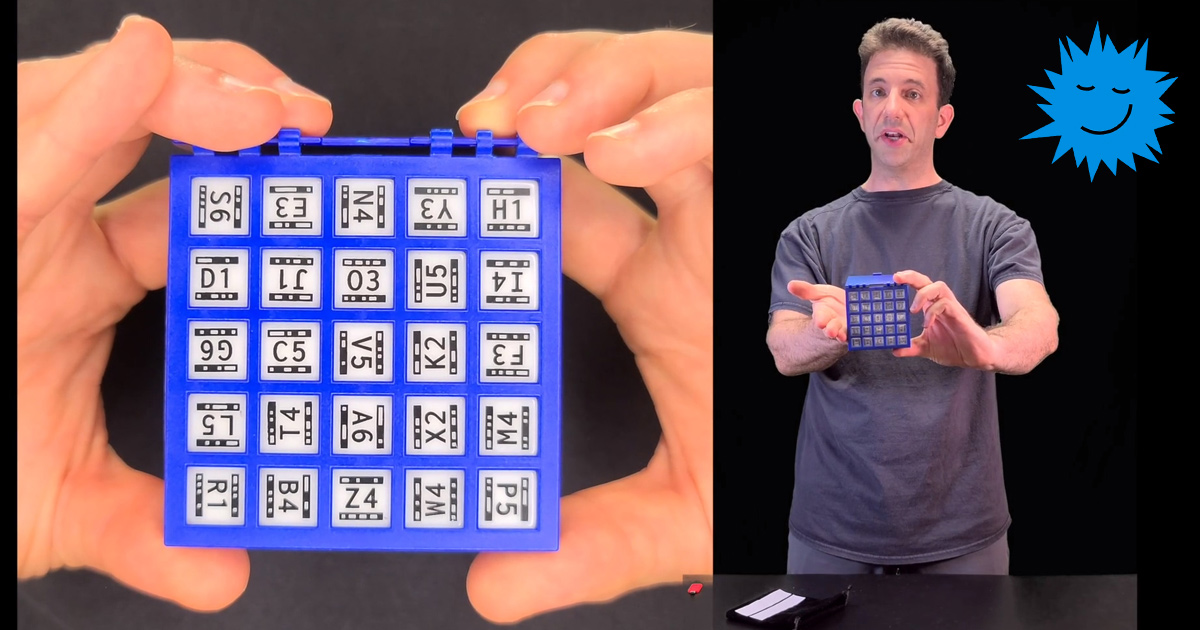
The man's name is Stuart Schechter, and he is a computer scientist at the University of California, Berkeley. Despite the increasingly complex algorithms and the attraction of more and more new methods for generating ciphers and passwords, Schechter proposed an extremely elegant in its simplicity way of generating a character base for the subsequent creation of a master password. The scientist created a set of 25 hexagonal bones, on the edge of each there is a pair of a random number and a letter of the Latin alphabet. He named his creation as simply as the idea itself looks like - "DiceKeys".
The scientist suggests the following procedure.
You take a set of 25 bones and a special storage box. Shake the bones, pour them into the box and help all the knuckles with your hands to lie down in special cells of the body. That's it, the base for your password is ready!
How this works is demonstrated by Schechter himself in the video below:
After the throw, it is proposed to scan the result obtained with a special smartphone application, which will create a master password using the received data. And voila, you are beautiful.
The set includes a box for cubes, the cubes themselves and a randomizer bag (for users with large hands, probably an optional accessory).
Why does Schechter's solution seem extremely interesting to us against the background of randomly generating 128, 196 or 256-bit passwords in the same KeePass or another manager?
First, a machine-generated password will never be completely random, because there is no absolute software randomizer.
Second:the password can "leave" you even in the process of generating it on the machine (after all, usually you generate a password where you will use it), which means it will be compromised even on takeoff.
Third: in order to protect not only the password from attackers, but also the very principle of its generation, we need another password or an isolated machine (which is the next level of paranoia), so here we find ourselves in a vicious circle of cryptographically strong passwords.
Importantly, Schechter himself emphasizes that the smartphone application does not interact with the outside world in any way and is generally "silent" on the air. And, most importantly, the set of cubes in the box, in addition to the base for generating the password, also acts as a backup of this same master password: when the fixed combination is scanned again, the application on the same device will restore the password previously generated for you.
So a scientist from Berkeley, by withdrawing the process of generating a database for a password offline, simultaneously covers three previously voiced weak points in the process of creating a master password:
- its randomizer is truly random and not based on algorithms;
- 2128 , -, , ;
- , ( , , - ).
The last point, about the isolation of the system, is probably the most important. Let's turn on the maximum paranoia mode, twist our foil hats and imagine that an intruder is watching our every step.
As a result, the usual and already implemented methods of collecting random data for generating a password, for example, collecting point-click-window data to accumulate pseudo-random data from some password generators that parse activity on a machine in the background - no longer look so secure.
The isolation of the system vulnerability is generally the cornerstone of information security. Some experts generally say that "if you do not want your data to be stolen, do not store it digitally / on a machine with network access." Apparently, it was this aspect that was guided by Schechter when he worked out the concept of his cubes-keys.
His system is vulnerable only to social engineering if we consider the option of using an isolated smartphone as a platform for generating a master password. But even in the case of physical contact between an attacker and the owner of DiceKeys, an incredible number of conditions must be met.
So, a hacker needs to know that he needs a set of bones. In addition to the kit, to re-generate the password, he will also need the device from which the master key was generated. And he will have to physically get it all.
At the same time, hacking even by social engineering becomes impossible if the user destroys the combination of cubes , that is, cuts off the possibility of re-generating his master password. So, to steal the password, only the "soldering iron" method will remain, provided that the person remembers the password.
Criticism
But the method proposed by Stuart Schechter also has weak points. DiceKyes can now be tested on the dicekeys.app website , which both simulates dice rolls and scans actual sets. The site is used until the mobile application is ready.
Most of the questions arise about the final result of the generation - it is relatively meaningful and based on the lower case. Apparently, the final password is formed according to the English dictionary, so that the master password has at least some meaning, that is, it is remembered by an ordinary user.
Here are several options that the author received for different applications on the same set of faces:
1Password: music booth owls cause tweed mutts lance halve foyer sway suave woven itemAuthy: dudes acre nifty yoyo sixth plugs relic exert sugar aged chili human alarmFacebook: delta had aids pox visa perm spied folic crop cameo old aged smite
All of these passwords do not contain special characters, numbers, or variable case, although they are long enough to make it impossible to boot-force such a combination.
In this case, you can always go further and drive the resulting words through another "generator", or translate into hexadecimal encoding. In fact, there are many options.
Total
In any case, the development of Stuart Schechter is the most niche product for hardcore and paranoid users. There are many acceptable and safe solutions on the market now. For example, you can think of physical access tokens that have worked well in the industry.
At the same time, the password managers themselves are quite safe: the last big hack of this kind, according to Google, took place already in 2015 ( hacked LastPass), which by industry standards is almost an eternity ago. Then the hackers stole a ton of related data, including the email addresses of the LastPass account, password reminders, server records for each user, and authentication hashes. The latter, in theory, could give access to the account's master password, which further opens access to passwords stored in LastPass itself.
But you need to remember that unbreakable systems do not exist, and while they are, in concept, impossible: everything that was invented can be hacked in one way or another. Only that which is not digitized or does not exist at all in physical performance is not hacked.
Remember this and take care of your data.
Advertising
Servers with NVMe are about virtual servers from our company.
For a long time we have been using exclusively fast server drives from Intel and do not save on hardware - only branded equipment and the most modern solutions on the market for providing services.
