The reason for highlighting this threat to US government agencies was a coordinated attack seen in mid-July this year. There are no details in the FBI and CISA bulletin, but there is a lot of interesting information in the publication by Brian Krebs on August 19. Apparently, a group of cybercriminals is seriously engaged in vishing, which provides its services to everyone on the black market. These are long-term, targeted attacks aimed at generating profit through blackmail or identity theft.
Sources:
FBI and US Cybersecurity Agency report (PDF).
An article by Brian Krebs analyzing the actions of the attackers.
News of voice attacks on American bank customers from 2014, one of the earliest mentions of the term vishing.
A case study a year ago about stealing company funds using a sophisticated voice attack.
News on Habré.
Voice phishing can be roughly divided into three categories: a simple attack on a consumer (a call from a bank, a call from a mobile operator, and so on), an attack on a company (a call supposedly from technical support), a complex attack supposedly from a real employee familiar to the victim. Exactly a year ago, the media got information about a successful attack on the company: the CEO called the chief accountant and asked to make a transfer to a certain bank account. 220 thousand euros were stolen, the attackers allegedly used machine learning algorithms to "recreate" the voice of a real person. This time we are talking about attacks below the level. They happen as follows: a company employee receives a phone call from a support representative,The latter informs about the need to "fix the VPN" and redirects the victim to a fake site with subsequent account theft.
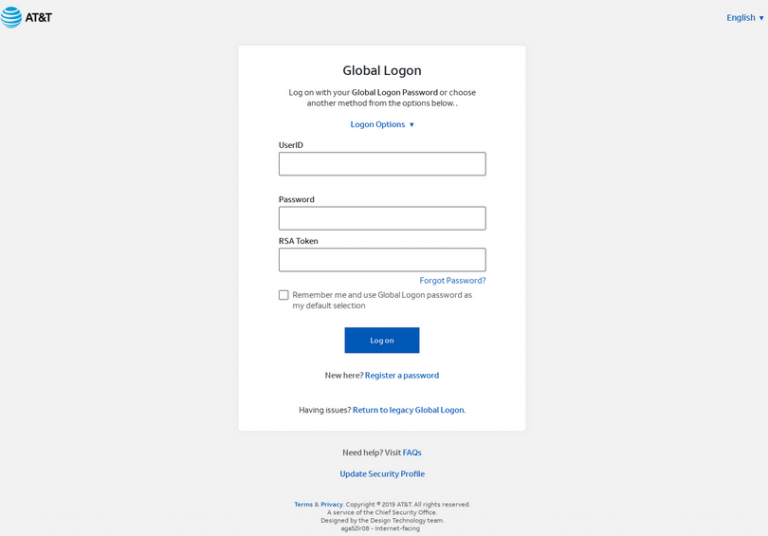
In this case, machine learning is not required: a large corporation, many people work in the IT department - it is easy to convince the victim that a newly hired employee is calling her. Now is the perfect time for such attacks: a lot of people work from home (although nothing prevents them from launching the same attacks in an office environment). Previously, fraudsters lacked only a good organization of the criminal business. And judging by the data from the article by Brian Krebs, now with the organization of the cybercriminals everything is pretty good. Here's how they work:
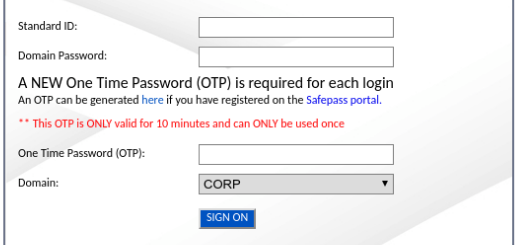
- They create believable copies of authorization pages in the corporate system, with logos and links to real company resources.
- , . , , . , .
- LinkedIn, . , .
- . , .
- After hacking, an additional phone number or smartphone is tied to the account so that access can be restored without social engineering.
- They shut down the fake site immediately after the attack to cover their tracks. This is a new challenge for the cybersecurity industry: to identify phishing pages before they are used.
It is clear that even with this level of preparation, vishing does not always work. In case of failure, the attackers analyze the information received and change tactics. Krebs' interlocutors argue that people employed in this industry have developed their skills over the years. Fortunately, this summer's particular series of attacks shows that its authors are better at social engineering than blackmail, withdrawals and the like.
The countermeasure for any social engineering attack is primarily employee training. For example, in the FBI report, company employees are advised to bookmark a page for accessing the company's web services and open it, and not the link that the attackers send. You can also hinder penetration using technical methods - for example, restricting access to the VPN to devices from the whitelist. The most promising method is a dongle to access corporate resources, which simply won't work on a fake page. But it is not so easy to issue such a key to hundreds or even thousands of employees, especially if they work remotely. The universal recommendation remains to reduce the potential damage from hacking one account.
What else happened
Google has closed a vulnerability in corporate email service (part of the G Suite package) that allowed sending messages on behalf of any Gmail user or G Suite subscriber. The peculiarity of the problem was that during spoofing, Google's "quality marks" (SPF and DMARC) were preserved, which distinguishes this bug from other methods of forging the real address of the sender. The vulnerability was closed a few hours after the publication of the report , although by that time Google had been aware of the bug for six months.
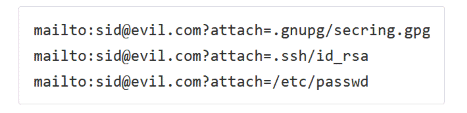
Another interesting email vulnerability: in some clients (for example, in Thunderbird) in standard links like mailto: you can attach a file as an argument. A theoretical example of an attack is shown in the screenshot above: we send the victim a link, clicking on it creates a message with the sender's address and the attached file. Read more in the news and work of researchers from the Ruhr and Westphalian universities. Dozens of people have been arrested
in the US for using a bug in Santander ATMs. A software error allowed to withdraw more money from debit cards than was on the account. The bank had to turn off all ATMs in the country for several hours. Discovered
a new botnet that attacks devices and servers with weak SSH passwords. A feature of the botnet is its decentralization: there is no single command server, the network is controlled distributed among the infected devices.
An interesting method of creating a copy of the keys to the lock: to record the sounds made by a real key, which the owner opens the door with, and then, based on the analysis of clicks, restore the shape of the key.