Summary
- Guardicore discovered the sophisticated peer-to-peer (P2P) botnet FritzFrog , which has been actively hacking into SSH servers since January 2020.
- Malware on Golang : FritzFrog runs modular, multi-threaded, and fileless malicious code on Golang that leaves no trace on the hard drive of an infected device.
- Active targeting of government, educational, financial and other resources : FritzFrog tried to brute force and distribute to tens of millions of IP addresses of government offices, educational institutions, medical centers, banks and many telecommunications companies. Among them, more than 500 servers were successfully attacked, including well-known universities in the US and Europe, and one railway company.
- Complexity : FritzFrog is completely proprietary, its P2P implementation is written from scratch, which indicates a high level of professionalism of its creators in the field of software development.
- : Guardcore Labs Golang, P2P FritzFrog .
- : , FritzFrog, Rakos.
FritzFrog is a very sophisticated peer-to-peer botnet that actively breaks into SSH servers around the world. Thanks to its decentralized structure, it distributes control across all its nodes. This network does not have a single point of failure, and peers constantly communicate with each other to keep it stable, updated, and constantly active. P2P connections are made over an encrypted channel using AES for symmetric encryption and Diffie-Hellman for key exchange.
Unlike other P2P botnets, FritzFrog is unique in its set of properties: it is fileless because it builds and executes packages directly in memory; despite the effective even distribution of targets in his network, he very aggressively brute-forces them; its proprietary P2P protocols are not based on any of the currently known implementations.
The malicious code written in Golang is very changeable and leaves no traces on the hard drive. It creates a backdoor in the form of a public SSH key and thereby gives attackers permanent access to the victim's device. From the very beginning of its activity, we have identified 20 different versions of the executable malware.
In this post, we will explain how FritzFrog was exposed, as well as the nature of its P2P network and the internals of the malicious code - including the infection process, command encryption, and volatile behavior.
Guardicore Labs has made available a Github repository with a script to detect this malware and a list of Indicators of Compromise (IoC) for its activity.
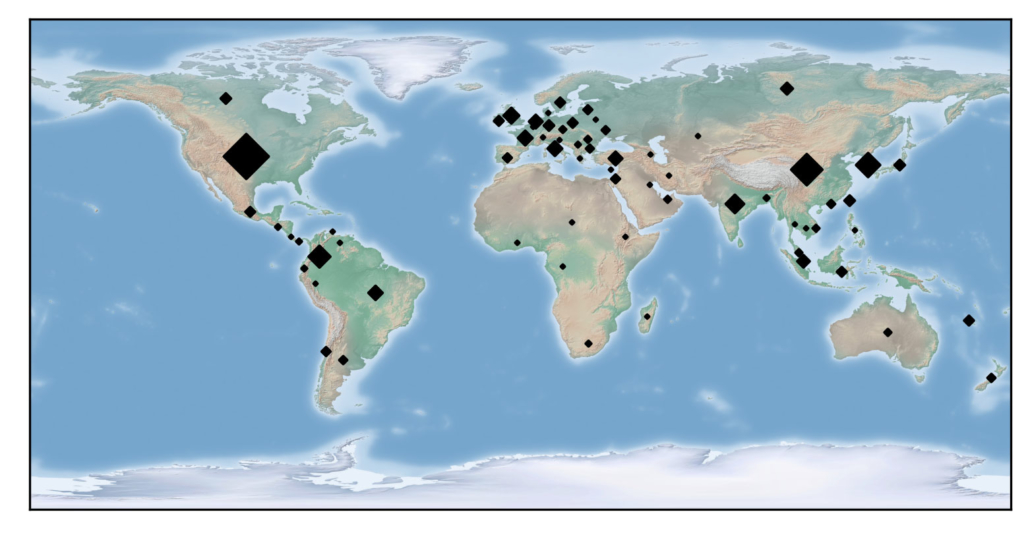
Geographic distribution of infected hosts. The most vulnerable countries were the United States, China and South Korea.
FritzFrog Research
Guardcore Labs first looked at FritzFrog in a Botnet Encyclopedia study . On January 9, new attacks with the execution of malicious processes
ifconfigand nginx. We started tracking a steady and significant increase in malicious activity, which soon reached 13,000 attacks on the Guardcore Global Sensors Network (GGSN). We tracked 20 different versions of the FritzFrog binaries over the years.
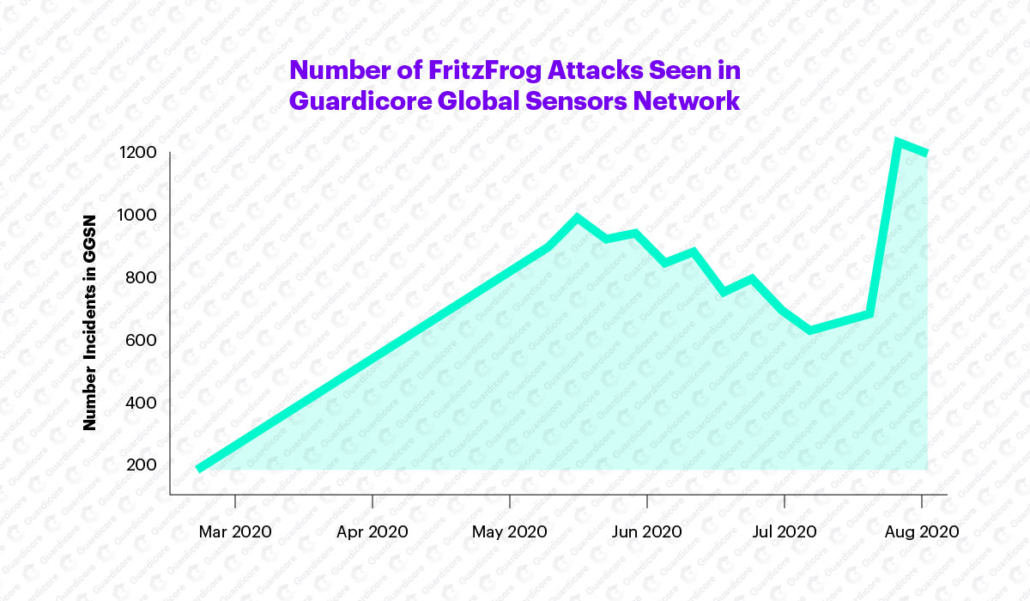
The graph shows the number of FritzFrog attacks on GGSN.
Surprisingly, the malicious code did not seem to communicate with any command and control (CNC) server at first glance. It was only when we started to seriously investigate the botnet that we realized that there was no server at all.
To intercept the botnet network, Guardcore Labs developed a client on Golang that can exchange keys with malware, as well as send commands and receive responses. This program, which we then called "frogger", allowed us to investigate the nature and purpose of the network, and thanks to the frogger we "added" our own nodes to the network, being able to connect to the botnet, and participate in the transmission of active P2P traffic data.
FritzFrog has been brute-forcing millions of IP addresses, including government offices, educational institutions, medical centers, banks and many telecom companies. Of these, more than 500 servers were successfully attacked, including well-known universities in the USA and Europe, and one railway company.
Next generation P2P
Why New Generation?
FritzFrog , :
- : FritzFrog , (BLOB).
- : .
- : . , P2P DDG «root».
- : .
- : P2P - P2P , μTP.
As soon as the victim is successfully hacked, UPX-packed malicious code is launched on it, which then immediately deletes itself. To minimize suspicion, malicious processes are executed under the names ifconfig and nginx. At the very beginning of its work, the malicious code listens on port 1234, waiting for commands. The first commands received synchronize the victim with the database of network peers and brute force targets.
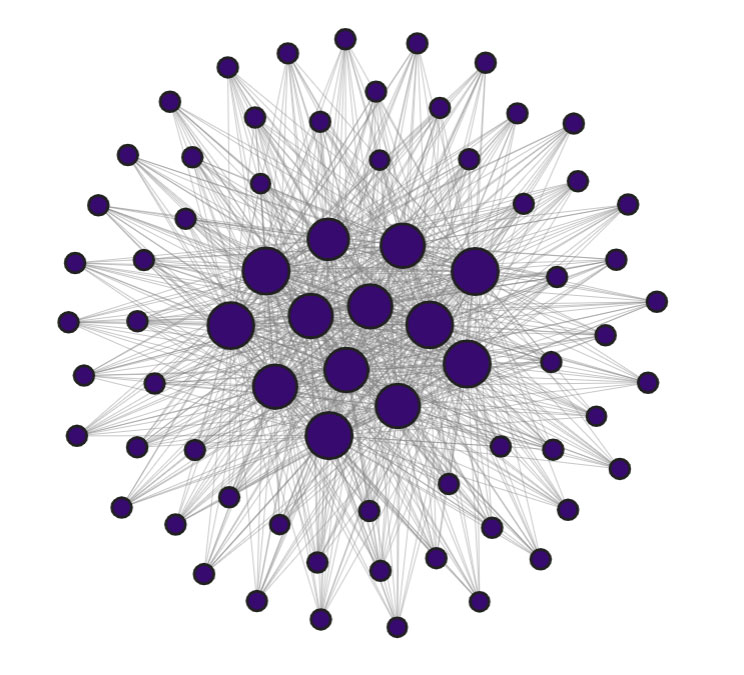
FritzFrog host cluster. Each node is an infected SSH server. The size of the nodes demonstrates their connectivity to the rest of the network.
Traffic on a non-standard port, for example 1234, can be easily noticed and blocked by a firewall or any other security system. Therefore, the developers of FritzFrog approached the problem creatively and instead of directly transmitting commands through port 1234, the attacker connects to the victim via SSH and launches a client on the netcat device, which in turn connects to the botnet server. Thus, any command will be passed over SSH as netcat input and easily reach the malicious code.
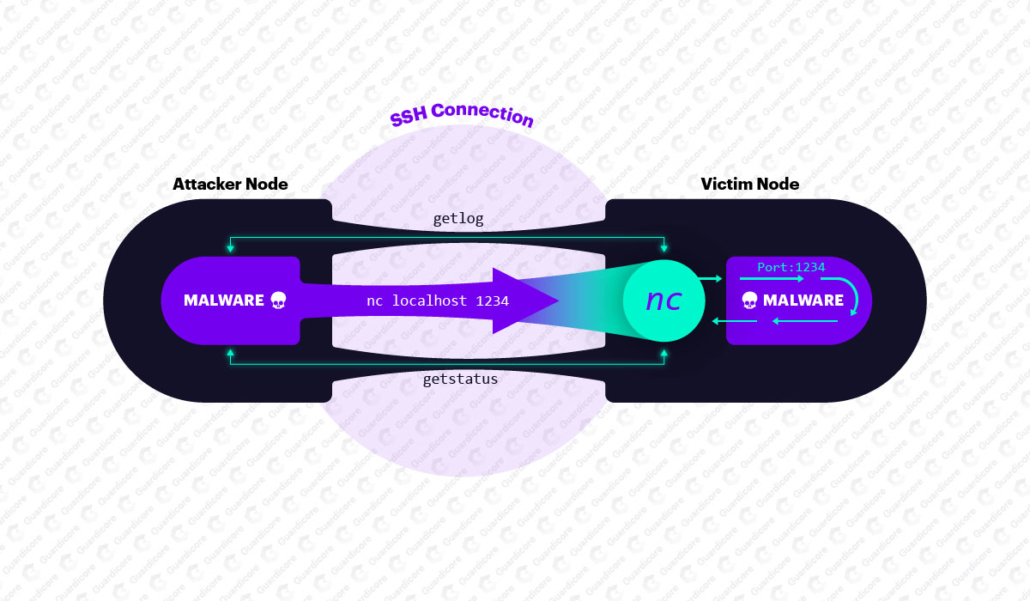
FritzFrog tunnels its P2P commands through the classic SSH port using the local netcat client of the infected device.
FritzFrog attackers have deployed an encrypted command channel with over 30 different commands. Command parameters and responses are passed in specified data structures and released (“mobilized”) in JSON format. The data is encrypted with symmetric AES encryption and encoded in Base64 before being sent. The nodes involved in the data transfer use the Diffie-Hellman protocol to exchange keys.
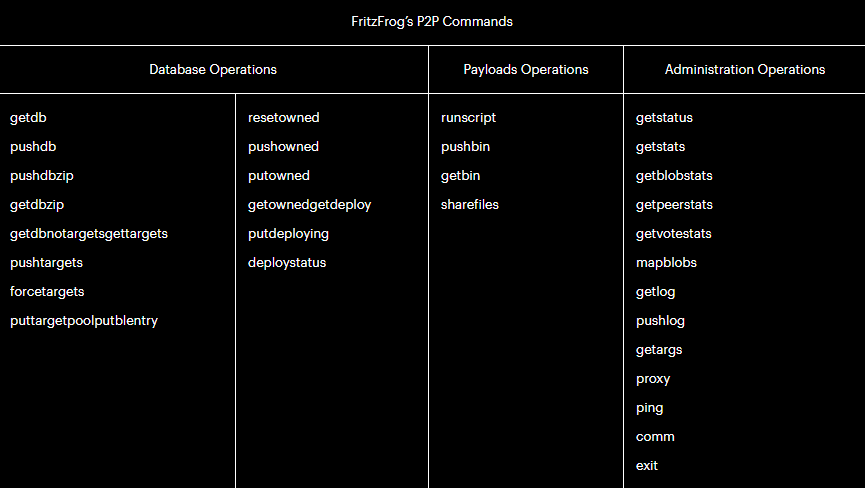
The nodes in the FritzFrog network maintain close contact, constantly pinging each other to verify connectivity, peer and target exchange, and mutual synchronization. Nodes also engage in a clever electoral process that affects the distribution of brute force targets across the network. Observations from Guardcore Labs confirm that targets are evenly distributed across the network and no two nodes will try to hack the same target.
Diving into malicious code
The FritzFrog binary is an advanced malicious code on Golang. It works completely in memory, each node with malicious code stores the entire database of targets and peers in memory. The malicious code creates multiple threads to simultaneously process various tasks, as shown in the table below.
FritzFrog defines victim and target device control states as follows:
- Target : The device from the target request will then be passed to the Cracker module, which in turn will try to scan and crack it.
- Deploy : A successfully compromised device is queued for malware infection through the DeployMgmt module.
- Owned (): P2P Owned.
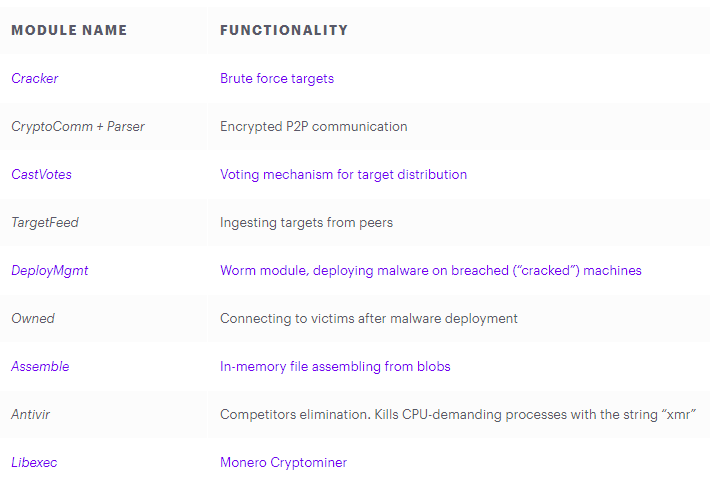
Each node with malicious code has a worker thread that is responsible for receiving commands, parsing them and passing them to the appropriate functions in the code.
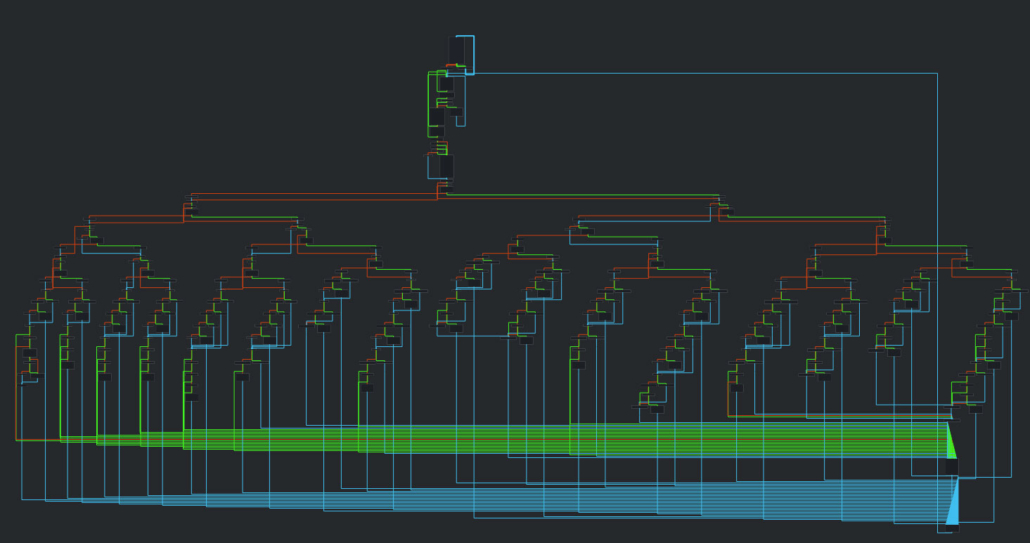
A working function in a disassembler. Each branch corresponds to the supported P2P functionality.
The malicious code is temporary in nature: even though it tries to survive system reboots, for future access to the hacked target, a backdoor is saved, whose login and password are stored by the peers on the network. The malicious code adds the public SSH-RSA key to the file
authorized_keys. This simple backdoor allows an attacker - with a private, private key - to authenticate without a password, in case the original password is changed. The only public key FritzFrog uses is shown below.
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDJYZIsncBTFc+iCRHXkeGfFA67j+kUVf7h/IL+sh0RXJn7yDN0vEXz7ig73hC//2/71sND+x+Wu0zytQhZxrCPzimSyC8FJCRtcqDATSjvWsIoI4j/AJyKk5k3fCzjPex3moc48TEYiSbAgXYVQ62uNhx7ylug50nTcUH1BNKDiknXjnZfueiqAO1vcgNLH4qfqIj7WWXu8YgFJ9qwYmwbMm+S7jYYgCtD107bpSR7/WoXSr1/SJLGX6Hg1sTet2USiNevGbfqNzciNxOp08hHQIYp2W9sMuo02pXj9nEoiximR4gSKrNoVesqNZMcVA0Kku01uOuOBAOReN7KJQBtThe malicious file runs all kinds of shell commands on the local device, some multiple times, to monitor the state of the system. For example, it runs
free –mto check available RAM uptime, journalctl –s @0 –u sshdto track SSH logins, and other commands to display CPU load statistics. These statistics are available to other nodes on the network and are used to make various decisions, for example, whether to run the cryptominer on the device or not. If a decision is made, the malicious code launches a separate process libexecto mine Monero. This miner is based on the popular XMRig miner and communicates with the public pool web.xmrpool.euthrough port 5555.
Vicious torrent-like network
FritzFrog relies on the ability to share files across the entire network, both to infect new devices and to launch malicious elements such as the Monero cryptominer.
To exchange files between nodes, FritzFrog uses a stealthy fileless approach: files are divided into arrays of binary data stored in memory, and malicious code monitors the available arrays by storing them in a map along with the hash value of each array.
When node A wants to receive a file from its peer, node B, it can send a request
getblobstatsto node B to find out what arrays it owns. Then, node A can get a specific array through its hash, either using a P2P command getbinor using HTTP at the address http://1234/. Once node A has received all the arrays, it builds the file through the Assemble module and runs it.
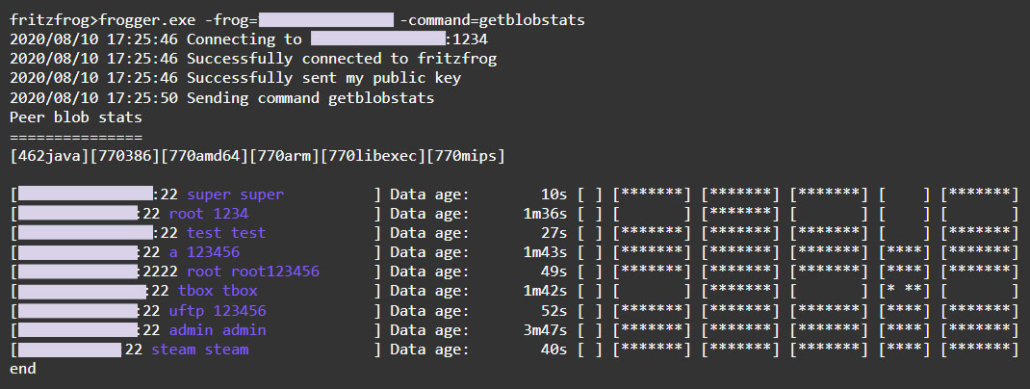
getblolbstats. , .
Tracking P2P botnet operations is difficult. Due to the distributed nature of the network, commands in it can be transmitted from any node to any node. However, we tried to compare this P2P botnet with previous similar threats.
Even when compared to other P2P botnets, FritzFrog remains unique: it does not use IRC like IRCflu does , unlike DDG, it runs directly in memory, and it runs on Unix devices as opposed to the InterPlanetary Storm botnet. If it looks like anyone, especially in terms of feature naming and version numbering, it is on Rakos , a P2P botnet on Golang analyzed by ESET back in 2016.
Activity Tracking & Mitigation
Guardcore Labs provided the FritzFrog tracking script to run on SSH servers. It looks for the following botnet indicators:
- Launching processes
nginx,ifconfigorlibexecwhose executable file no longer exists on the system (as you can see below). - Listening on port 1234.
In addition to this, TCP traffic on port 5555 can indicate network traffic to the Monero pool.
ubuntu@ip-111-11-11-11:~$ ./detect_fritzfrog.sh
FritzFrog Detection Script by Guardicore Labs
=============================================
[*] Fileless process nginx is running on the server.
[*] Listening on port 1234
[*] There is evidence of FritzFrog's malicious activity on this machine.
FritzFrog exploits the port and protocol forcing feature of most firewall systems. You can eliminate such threats by using process-based segmentation rules.
Weak passwords prove to be a key vulnerability for FritzFrog attacks. We recommend using strong passwords and public authorization keys, which are much safer. In addition, it is critically important to exclude the FritzFrog public key from the file
authorization_keysto prevent attackers from gaining access to the device. Routers and IoT devices usually expose their SSH and therefore become vulnerable to FritzFrog attacks; we recommend changing the SSH port for such devices or, if the functionality is not used, completely disable SSH.