Moving forward on our project. We have completed the SIEM part. It's time to move our project from a simple observer to an active responder. One of the important tools we have used for this is Wazuh. In this article, we hope to educate you about the benefits offered by this tool. We will also tell you how to install and use it.
Wazuh is an open source security compliance detection, viewing and comparison engine.
It was created as a fork of OSSEC HIDS, later integrated with Elastic Stack and OpenSCAP, which turned into a more comprehensive solution.
Wazuh helps you gain deeper security visibility across your infrastructure by tracking hosts at the operating system and application layer.
Table of contents for all posts.
- Introduction. Infrastructure and technology deployment for SOC as a Service (SOCasS)
- ELK stack - installation and configuration
- Walking through the open Distro
- Dashboards and ELK SIEM visualization
- Integration with WAZUH
- Alerting
- Making report
- Case Management
The article is divided into the following sections:
- Installing the Wazuh Server and Agent
Installing Wazuh Server
Installing the Wazuh agent
App installation and integration with kibana
Configuring and connecting agents
1- wazuh
Wazuh — , , , . , .
Wazuh: Wazuh, API Filebeat. .
Wazuh: , . Wazuh, .
1.1- Wazuh:
Wazuh , , . , ( , , , . .), / . Elasticsearch .
(Single-host architecture (HIDS)), :
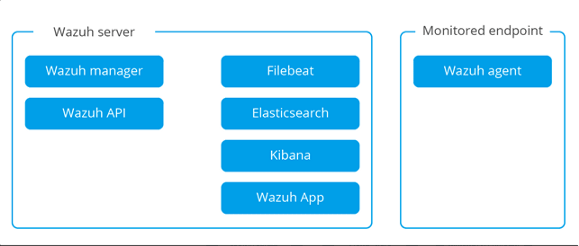
. :
https://documentation.wazuh.com/3.8/getting-started/architecture.html
1.2- Wazuh manager, API Filebeat
wazuh
https://documentation.wazuh.com/3.12/installation-guide/installing-wazuh-manager/linux/ubuntu/wazuh_server_packages_ubuntu.html#wazuh-server-packages-ubuntu
filebeat: filebeat elasticsearch logstash. elasticsearch ssl ( , )
cd /etc/filebeat
nano filebeat.yml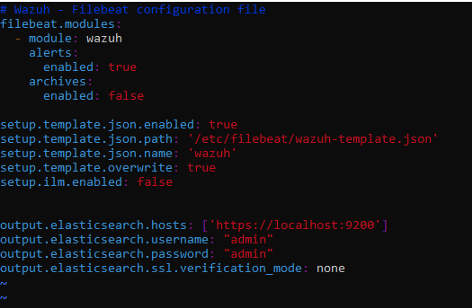
3 :
filebeat setup — index-management
service filebeat start
service wazuh-manager start
service wazuh-api start
1.3- wazuh-
https://documentation.wazuh.com/3.12/installation-guide/installing-wazuh-agent/linux/ubuntu12.04-or-greater/wazuh_agent_package_ubuntu12.04_or_greater.html#wazuh-agent-package-ubuntu12-04-or —
, wazuh-agent:

1.4- wazuh Kibana:
Wazuh Kibana ELK, .
Git Hub, -.
wazuh, ELK Stack 7.6.1. .
cd /usr/share/kibana
sudo -u kibana bin/kibana-plugin install https://packages.wazuh.com/wazuhapp/wazuhapp-3.12.2_7.6.1.zipKibana, :
cat >> /etc/default/kibana << EOF
NODE_OPTIONS=" —max_old_space_size=2048"
EOF:
systemctl restart kibana:
https://github.com/wazuh/wazuh-kibana-app
, wazuh . . wazuh api. . . , . , .
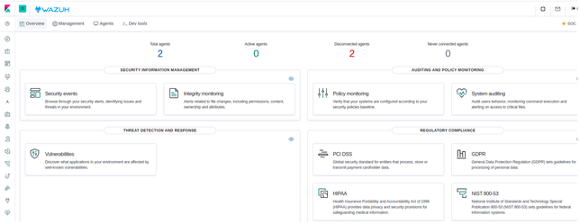
1–5
. .
Wazuh manager manage_agents, . . :
/var/ossec/bin/manage_agents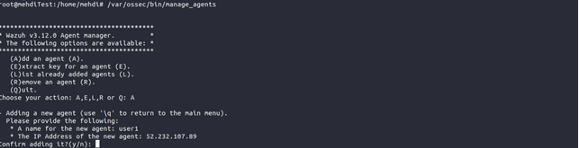
, A . , , user1. IP- . : IP- , () IP-. Enter
, wazuh.
E . , 001.
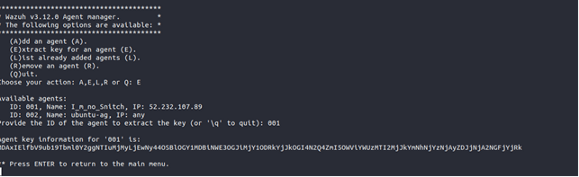
, Wazuh, Linux root. .
/var/ossec/bin/manage_agents -i "__", "y" Enter.

Wazuh /var/ossec/etc/ossec.conf, IP- Wazuh. <> <> MANAGER_IP Wazuh. Wazuh- IP- DNS-:

1.6- :
, ELK wazuh. . - (wazuh-alert wazuh-monitoring)
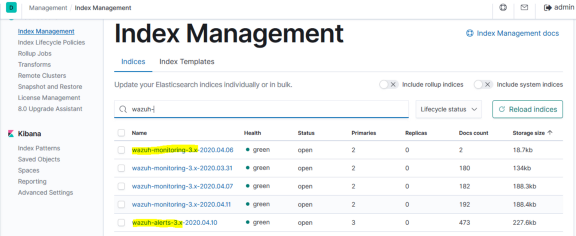
Wazuh:
Wazuh , Wazuh-manager.
— , , . — . , .
, IP- , , , Bruteforce, , RDP SSH, .
, IP- , , Wazuh. SSH-Bruteforce. 8 . , "5712 — SSHD ". . , IP .
-, , .
OSSEC , . / var / ossec / active-response / bin / . firewall-drop.sh, Linux / Unix IP- .
ossec.conf OSSEC Manager:
nano /var/ossec/etc/ossec.conffirewall-drop.sh, Linux / Unix IP- .

OSSEC . :
-command: (firewall-drop).
-location: . , . , local.
-rules_id: , 5712.
-timeout: IP 60 (iptables, ipfilter . .)
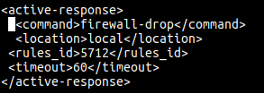
. wazuh-manager :
service wazuh-manager restartwazuh-agent ossec.conf :
<active-response>
<disabled>no</disabled>
</active-response>SSH -, Wazuh, 60 8 .
Wazuh, :
https://documentation.wazuh.com/3.7/user-manual/capabilities/active-response/how-it-works.html
Telegram chat on Elasticsearch: https://t.me/elasticsearch_ru