
Cybercriminals hijack routers and then use them to sell anonymization services, proxies, and organize DDoS attacks. Moreover, several botnets are fighting for the possession of zombie devices. New research from Trend Micro reveals how this war is going, and in this post we'll share the most important details.
According to experts, in 2020 the number of IoT devices connected to the Internet will exceed 31 billion pieces . Each such device contains an operating system with a network stack and a set of programs for performing basic tasks. The most functional IoT devices are routers. Usually their firmware is a lightweight version of Linux that is rarely updated by device owners. Many devices are left with a vendor-supplied password, which, combined with the unpatched vulnerabilities of old Linux, make routers ideal for hijacking and connecting to a botnet.
Why botnets are needed
An army of tens of thousands of devices can be used for different purposes. The most common are anonymous proxies and DDoS attacks. These two areas allow you to get serious income with competent monetization. The more devices a network has, the more potential power it has and the more money it brings to its owners. Therefore, cybercriminals compete to hijack as many routers as possible.
How does infection occur
The data collected shows that the largest number of infections occurs using brute force attacks and open telnet ports.
Brute-force attacks are performed using a special script and are highly effective, since many routers connect to the Internet with a default password. Password brute-force can also be one of the functions of a botnet, so the capture of new devices is quite fast.
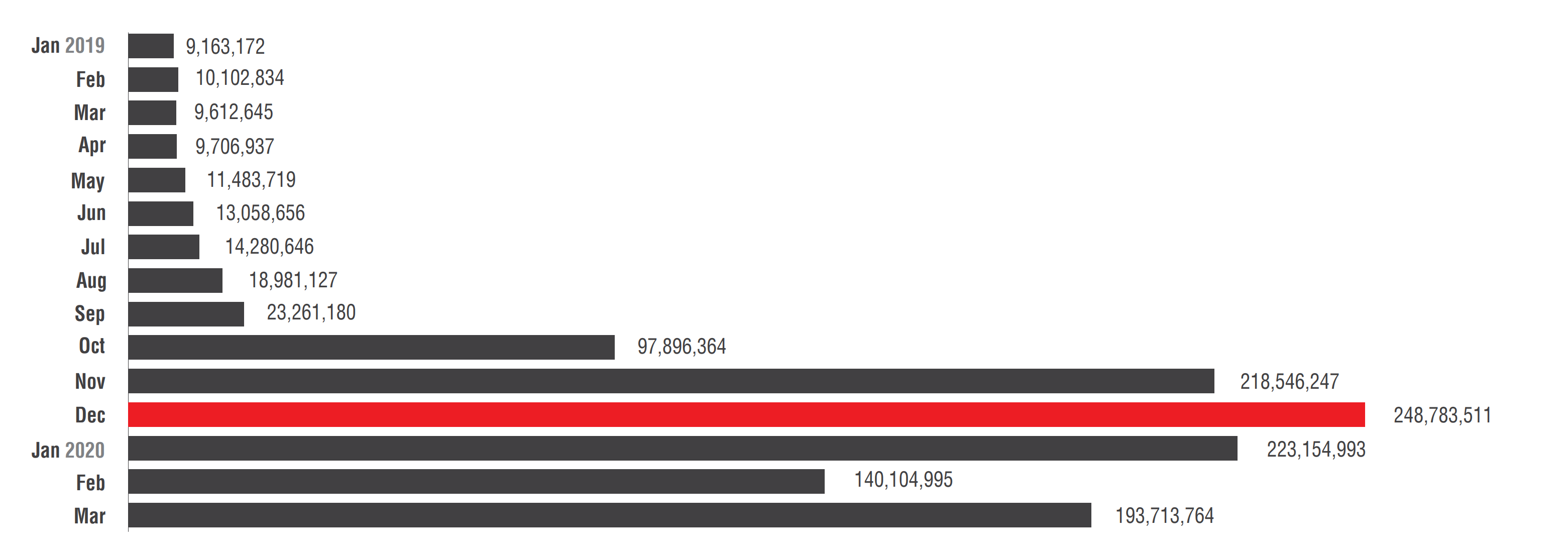
The number of brute force attacks on routers in 2019-2020. Source (hereinafter, unless otherwise noted): Trend Micro
According to Trend Micro telemetry, brute-force attempts to log in to routers increased steadily in 2019. At first, the growth was gradual, but since October the numbers have risen sharply.
The second most popular tool for expanding the reach of IoT botnets is by cracking the telnet protocol. Although telnet is not as widely used today as it was in the past and is not even recommended for use, many IoT devices still use it to provide remote access. Telnet sessions are not encrypted, which allows an attacker or botnets to easily intercept user credentials and other information. As a result, botnets can use the data obtained from the telnet protocol for further expansion.
Attempting to open a telnet session with other devices is not normal router behavior and may indicate an infection attempt. In our research, we used this metric as an indicator of the number of infected routers.

Trend Micro telemetry data from July 2019 to April 2020. Black bars - the number of telnet connection attempts, blue graph - the sources of these attempts
At its peak, the sources of malicious traffic were up to 16 thousand devices per week, after which this number decreased, which coincided with the partial shutdown of one of the most powerful botnets, DoubleGuns .
We found that there are three main botnet codebases that are most commonly used by cybergroups and script kiddies: Mirai, Kaiten, and QBot. Their codes are publicly available, so any tech-savvy crook can easily download the code, tweak and recompile it to hijack routers to create a botnet. Thus, the codes of these three botnets are the main cyber weapons in the ongoing war over routers.
Mirai
This is the most common code used to create botnets. Mirai was launched at the end of 2016, and it immediately changed the landscape of IoT threats. Mirai was created as a DDoS attack tool.
The first Mirai attack was an attack on Minecraft game servers hosted by the Internet service provider OVH. The power of the attack, which began on September 19, 2016, was 799 Gbps. The botnet consisted of 145,000 devices.
Another demonstration of the botnet's capabilities was the 665 Gbps DDoS attack on the Krebs on Security website on September 20, 2016. CDN provider Akamai, unable to cope with the attack, simply disabled the site, which ended up "lying" for four days. The attack itself lasted 77 hours and involved 24,000 hijacked routers.
The largest Mirai campaign wasthe October 12, 2016 attack on DNS provider Dyn , which provided services to Netflix, Reddit, Twitter and other companies. According to experts, the attack power exceeded the capabilities of all available security solutions. At that time, there were more than 11 million devices in the Mirai.
The release of the Mirai source code changed the world forever. The opportunity to create a DDoS club for oneself to kill competitors and lease it turned out to be so attractive that many Mirai forks immediately appeared with additional capabilities in the form of using additional exploits to hack routers, as well as code to clear compromised devices from competitors.


Fragments of Mirai's code to destroy rival Malware Anime. Here Mirai uses the Linux kill () system function to send the SIG_KILL (9) signal to competing processes.
Kaiten / Tsunami
This botnet is not as well-known as Mirai, although it can be considered one of the oldest. Its sources have been in the public domain since 2001. Interaction with control servers is carried out using the IRC (Internet Relay Chat) protocol. The server addresses are written in the Kaiten source code, which can be compiled for SH4, PowerPC, MIPSel, MIPS and ARM architectures.
The search and infection of devices is performed using a Python script that looks for open telnet ports and then tries to connect to it, brute-forcing passwords. The brute-force starts with the most common passwords contained in the body of the script:
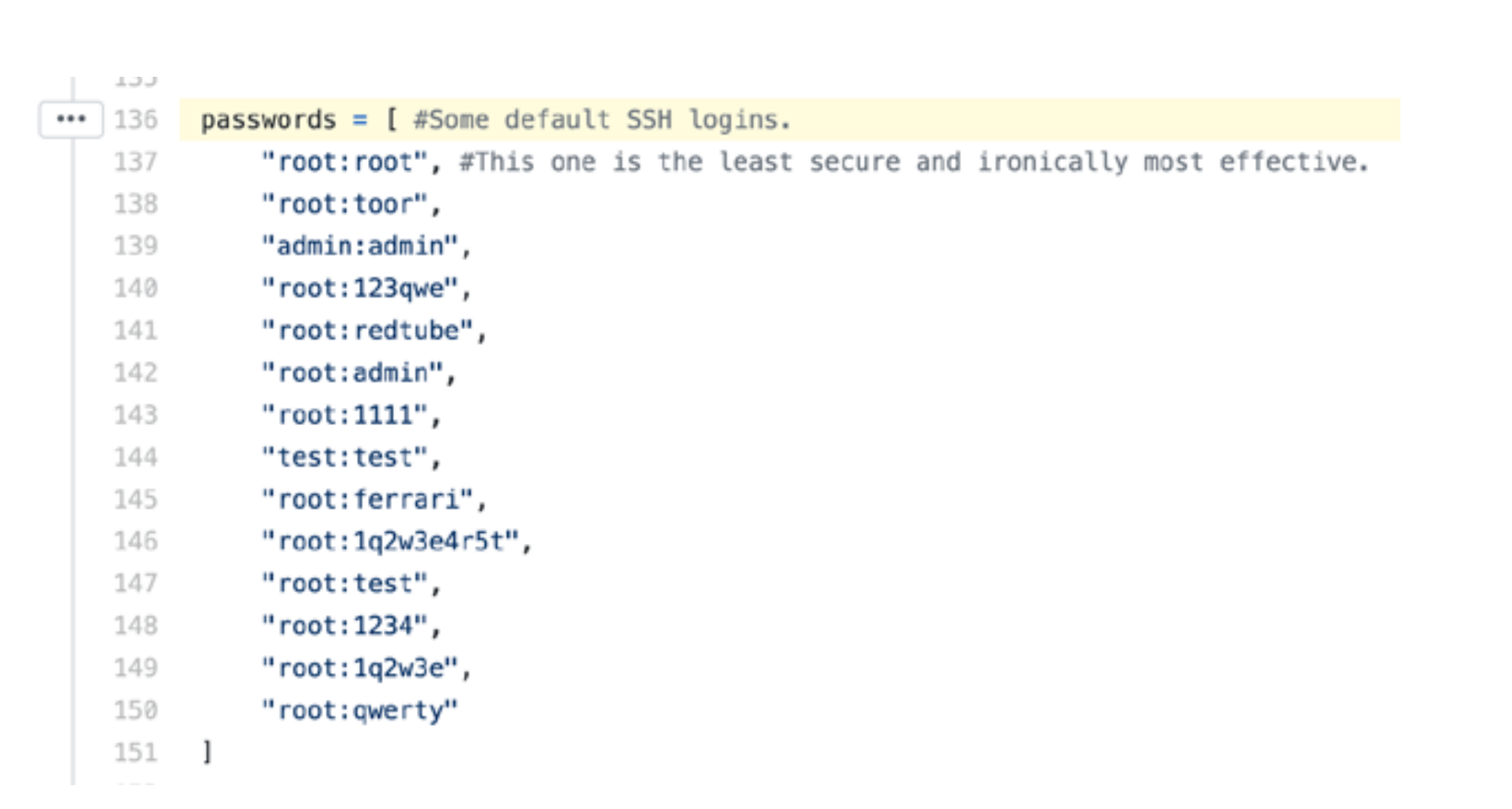
List of the most insecure and common passwords in the body of the Kaiten script
The release of the source code has also resulted in many forks, the latest versions of which also include a "bot killer" feature that cleans up the hijacked device from competitors.
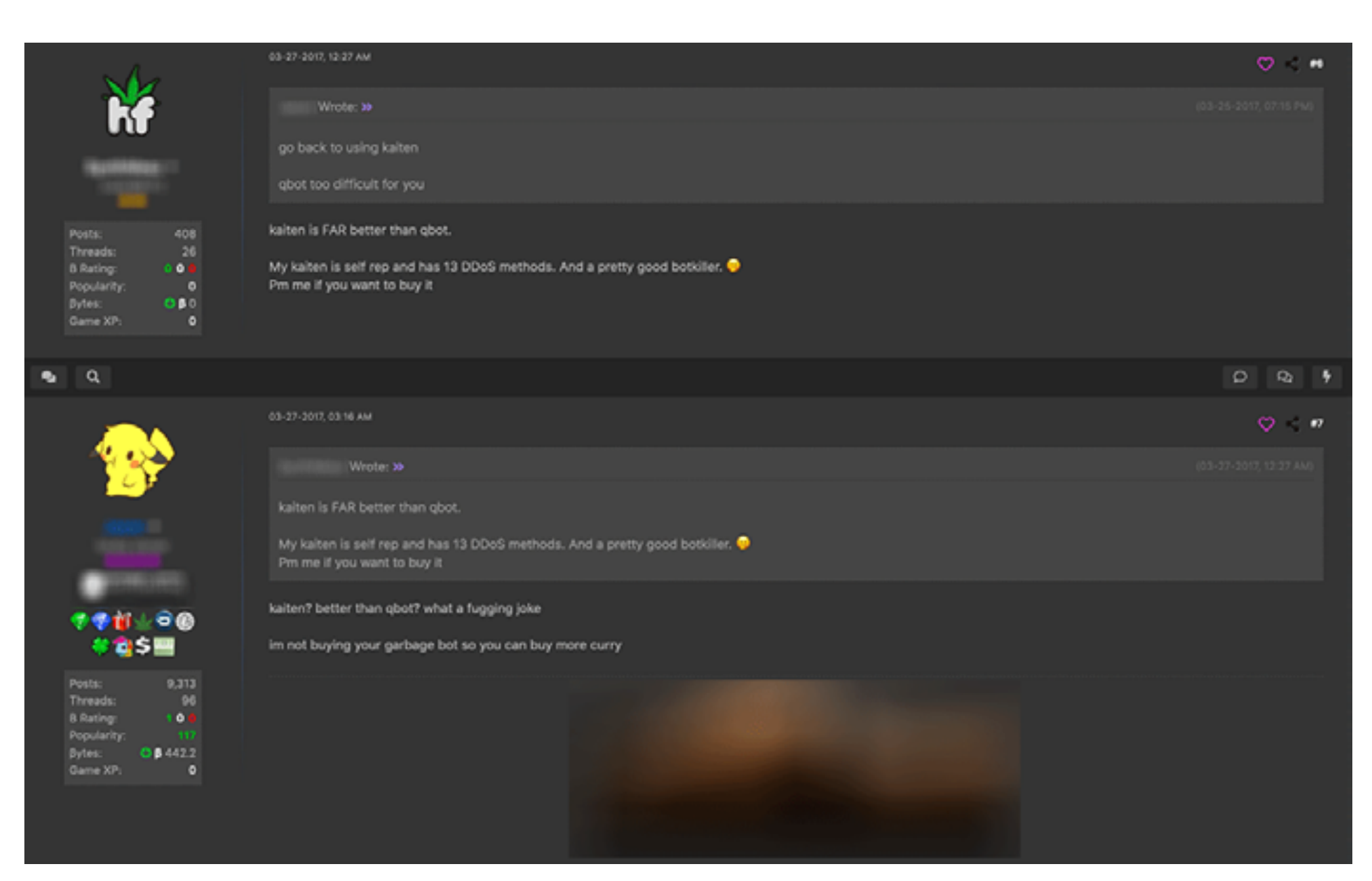
Kaiten Fork Authors Brag about Botkilling Feature on Forums
Qbot
This botnet appeared in the information field in 2008. Its source code consists of only a few files. The whole setup comes down to editing the sources, so this botnet is not so popular among newbies. On cybercrime forums, you can often find threads in which newbies ask for advice on setting up this botnet.
Qbot also supports various hardware architectures, and connects to management servers via TCP, without relying on higher-level protocols.
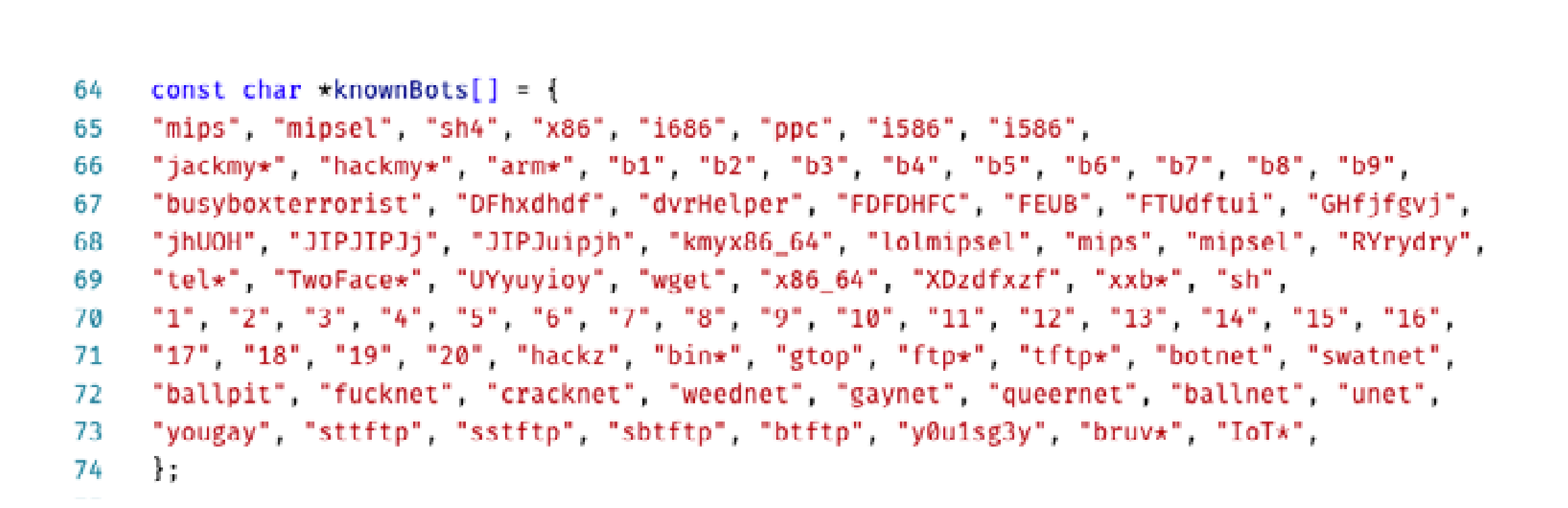
QBot code snippet containing identifier strings for competing malware
Qbot is also intolerant of competitors. One of its forks contains 438 competing process names, including Mirai and Kaiten.
Effects
Attackers can use various tools to compromise as many routers as possible, including those already in the hands of competitors. Infected routers are used for various purposes - from selling services based on infected routers to attacking "enemies", for example, on resources of other groups or on competing servers.
Ordinary Internet users have no idea that this war is happening in their homes, and do not know how it affects them, which makes this problem even more serious. Router owners must take care of the security of their devices and Internet connections, otherwise they risk becoming victims of cybercriminals. This problem is especially true when many employees work remotely from home.
Protection recommendations
We recommend that IT specialists check the status of "subordinate" routers at least once a quarter using this checklist:
- check the logs of the router for unusual behavior, strange accounts, and other anomalies;
- make sure the router has the latest firmware;
- use a strong password and change it from time to time;
- limit the number of attempts to enter the wrong password, if the firmware allows it;
- disable telnet to the router, and only allow logins from the local network.
We also encourage IT staff to help telecommuters secure their home routers.
Among Trend Micro's solutions is the Trend Micro Home Network Security appliance. It examines Internet traffic between the router and the home network, and also helps users assess vulnerabilities in devices connected to the network. This solution helps prevent botnets from hijacking devices in war, where routers are the battleground and the prize money to win.