Raw CAN
bus signal The CAN (Controller Area Network) bus has become a standard in the automotive industry: all new cars are required to support CAN (since 2001 in Europe and since 2008 in the USA). Besides cars, CAN is used in a wide variety of other devices. Manufacturers of diagnostic equipment for CAN advertise its use, in addition to various automotive equipment, in motorcycles, forklift trucks, ships, mine trains, bathyscaphes, unmanned airplanes, etc. Let's see what CAN is.
Several CANs are used in vehicles; for example, in the Ford Focus there are four such tires - three high-speed (500 kbps) for controlling the engine, brakes, dashboard, etc., and one low-speed (125 kbps) for controlling doors, headlights, airbags, audio system, air conditioning and everything other things. By connecting to CAN, you can simulate signals from any device in the car - for example, control the air conditioner from the application on the phone or wind up the odometer without moving the car. By connecting to the Arduino bus and the relay, you can control an additional parking camera from the dashboard . Even startups working on self-driving cars like Voyage, start prototyping by connecting to CAN in a regular production car and learning to simulate signals from the pedals and steering wheel.
To connect to CAN in a car, there is usually an OBD-II (On-Board Diagnostics) connector near the steering wheel.

OBD2-USB adapters for connecting a computer to CAN cost from $ 5 and allow you to track all traffic inside the car. Sometimes the OBD-II connector is protected by a "hardware firewall" that allows you to receive packets from devices connected to the CAN, but does not allow packets to be sent back to the bus. In this case, it is enough to unscrew the connector and connect to the CAN wires instead.

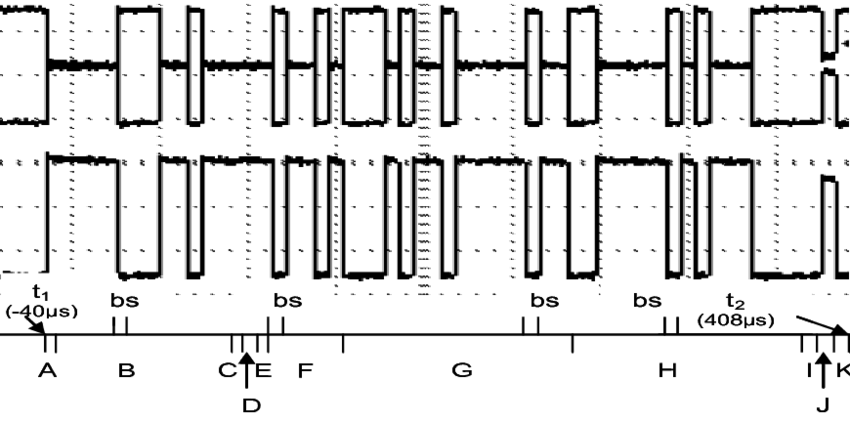
Each packet transmitted on the CAN bus consists of the transmitting device ID (11 or 29 bits), and up to 8 bytes of transmitted data. The traffic passing through the bus when the ignition is turned on may look something like this:
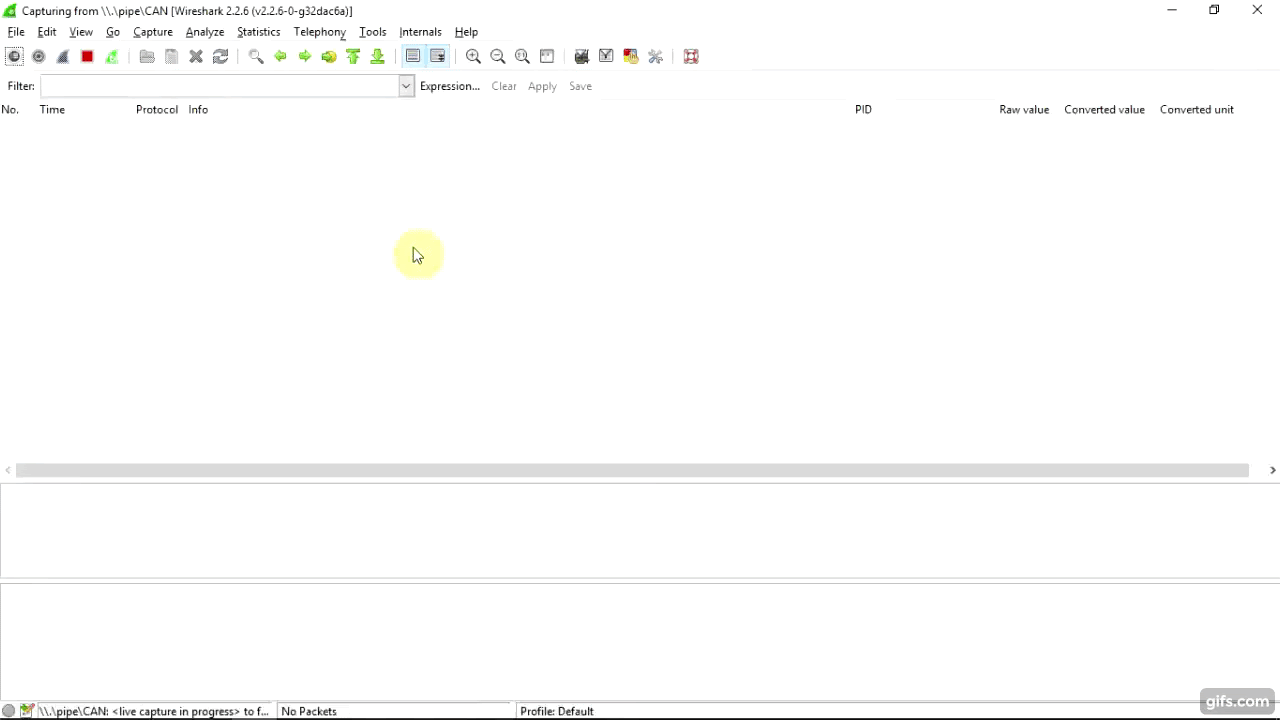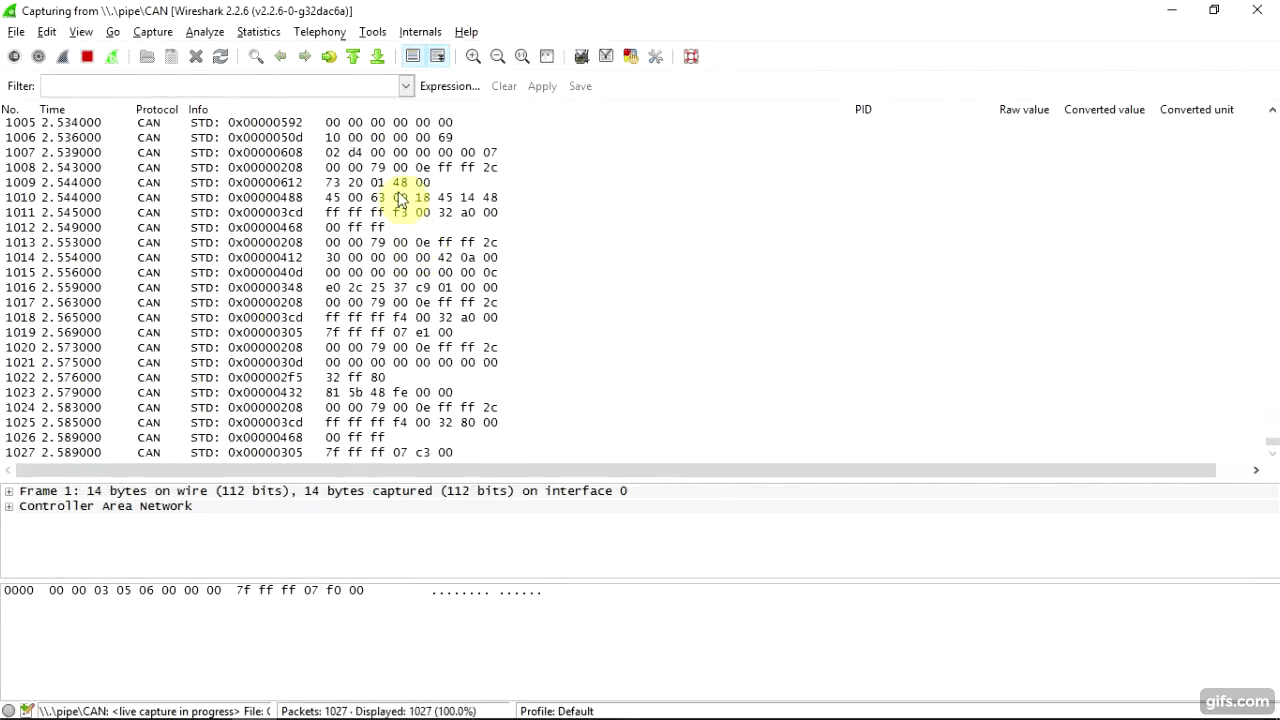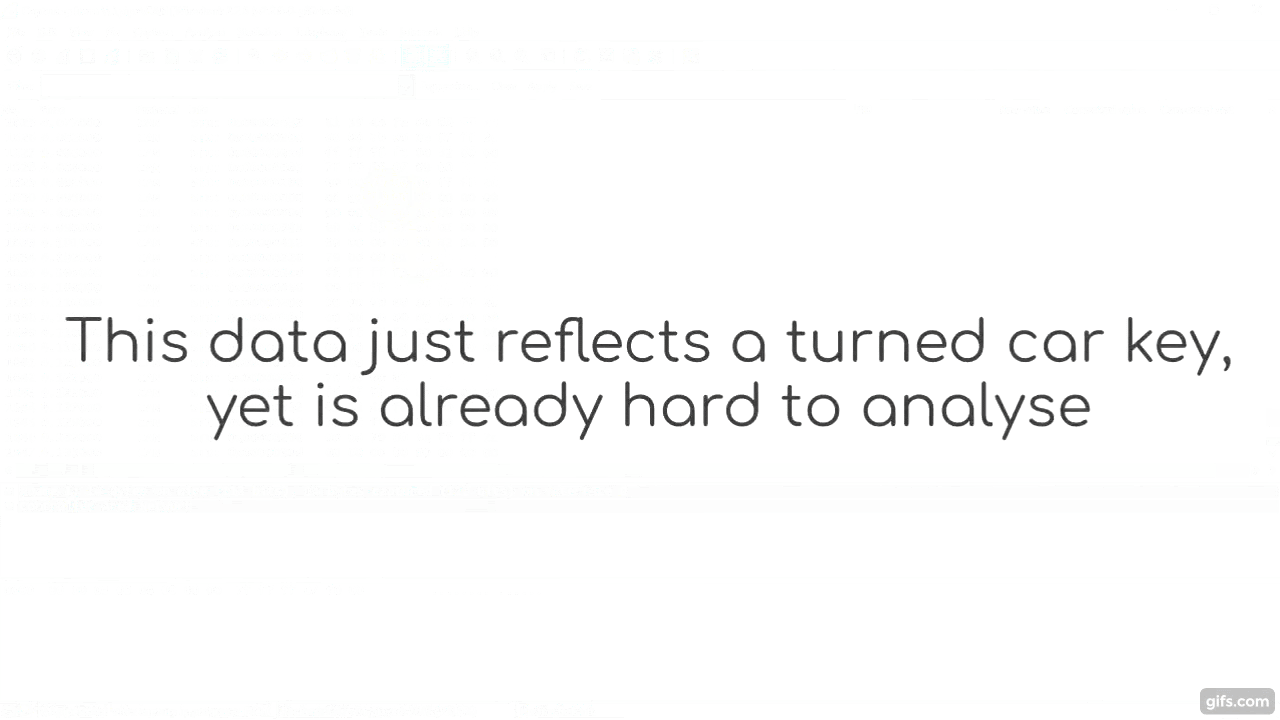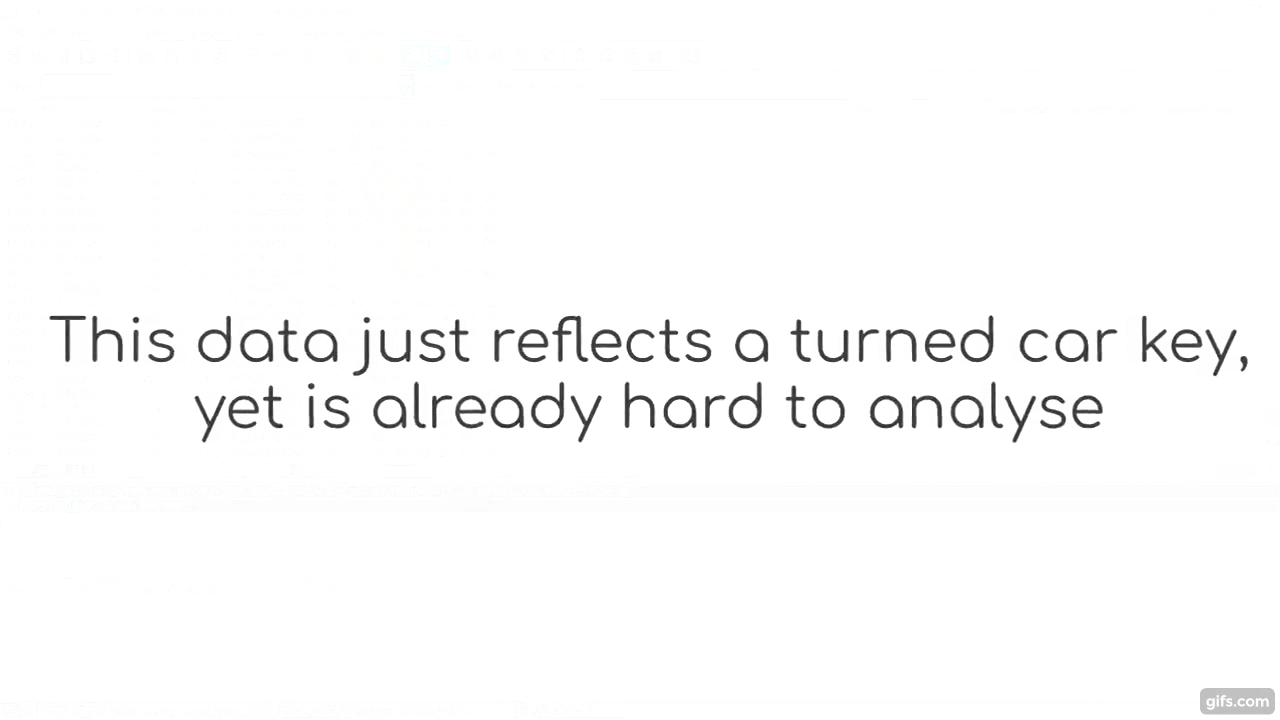
There are many tools for analyzing CAN traffic, both commercial and OpenSource. The can-utils package for Linux includes a utility
cansnifferthat displays for each CAN ID only the last sent packet, and thus allows you to track changes in the readings of each sensor on the bus:

For reverse engineering of CAN traffic, Singaporean researchers, from whose report I took this trace, recorded the dashboard of the experimental car on video, and then correlated the changes on the dashboard with the simultaneous changes in traffic. Having thus determined the CAN ID of the speed sensor and the format of the data transmitted by it, they learned to "fake" its packets, transmitting false readings to the speedometer and tachometer.
It should be understood that in parallel with the transmission of “fake” packets, real signals from the speed sensor continue to be transmitted over the bus. In order for the tachometer to show fabricated readings, it is necessary to monitor the transmission of real readings on the bus and suppress them in some way - for example, immediately after detecting the transmission of the CAN ID of the speed sensor, physically "muffle" the bus by shorting the data lines. A simpler, purely software method of suppressing real readings is to transmit “fake” packets immediately after their transmission, while the tachometer has not yet had time to respond. For example, the following simple shell script monitors a transmission with CAN ID = 0x0C9, and immediately after it transmits a fabricated packet using a utility
cansendfrom the same can-utils:
candump can0 | grep "0C9" | while read line; do cansend can0 0C9 # 8021C0071B101000; done
Even though all devices in the car are connected to CAN, not all of their functions are controlled via CAN. For example, signals about the degree of pressing the gas and brake pedals are transmitted to CAN in the Ford Escape - but these signals are used only by the ABS unit, while the throttle and brake actuators are directly connected to the pedals, bypassing CAN.
From a security point of view, there is no question of any vulnerability in the Singaporeans' report, because physical access to the bus is needed to transmit “fake” CAN packets. In addition, packets can be protected with a checksum - for example, in Toyota vehicles, the last byte of each packet mustequal the sum of all previous ones (modulo 256). In addition, Toyota uses recipient filtering to protect against unwanted packets - for example, it ignores steering turns more than 5% of the current value.
Nevertheless, security researchers managed to gain remote access to CAN: first, at a short distance - through vulnerabilities in a Bluetooth module connected to the same bus; and thenvia Sprint's cellular network, through which SUVs from several American manufacturers received traffic data. Researchers who demonstrated interception of control of a Jeep Cherokee from a distance of several miles received a reward of $ 80,000 from the Defense Advanced Research Projects Agency (DARPA). Since then, many automakers have announced their own bounty programs promising payouts of $ 1,500 or more for each vulnerability discovered. Thus, reverse engineering of traffic on the CAN bus can not only add new possibilities to your car, but also significantly replenish your wallet.
