TL; DR : I install Wireguard on a VPS, connect to it from my home router on OpenWRT, and access the home subnet from my phone.
If you keep your personal infrastructure on your home server or you have a lot of IP-controlled devices at home, then you probably want to have access to them from work, from the bus, train and subway. Most often, for similar tasks, an IP is purchased from a provider, after which the ports of each service are forwarded outside.
Instead, I set up a VPN with home LAN access. The advantages of this solution:
- Transparency : I feel at home under any circumstance.
- Simplicity : set up and forget, no need to think about forwarding each port.
- Price : I already have a VPS, for such tasks a modern VPN is almost free in terms of resources.
- Security : nothing sticks out, you can leave MongoDB without a password and no one will steal the data.
As always, there are downsides. First, you have to configure each client individually, including on the server side. It can be inconvenient if you have a large number of devices from which you want to have access to services. Secondly, at work you may have a local locale that matches the range - you will have to solve this problem.
We need:
- VPS (in my case on Debian 10).
- Router on OpenWRT.
- Phone.
- Home server with some kind of web service to check.
- Straight arms.
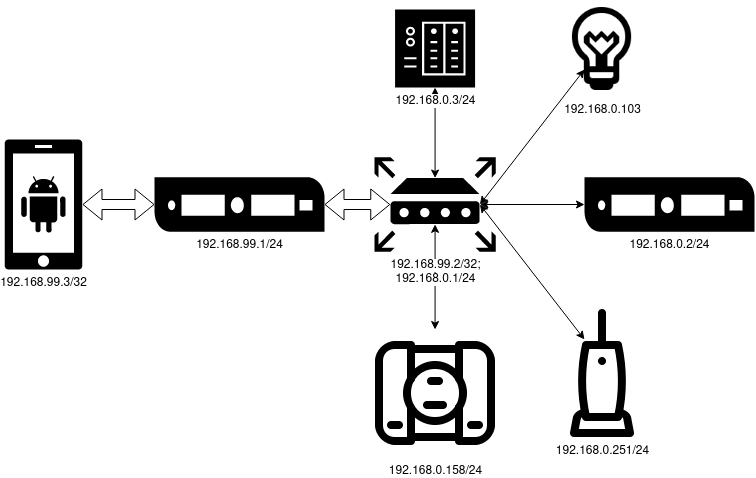
I will be using Wireguard as the VPN technology. This solution also has strengths and weaknesses, I will not describe them. For VPN I use a subnet
192.168.99.0/24, but at home I have 192.168.0.0/24.
VPS configuration
For business enough, even the most wretched VPS for 30 rubles a month, if you are lucky a snatch .
I perform all operations on the server from root on a clean machine, add `sudo` if necessary and adapt the instructions.
Wireguard not have time to bring in the Stable, so I'm doing `apt edit-sources` backporting and add two lines to the file: The package is installed the usual way: . Next, generate the key pair: . Repeat this operation twice more for each device participating in the scheme. Change the paths to the key files for another device and don't forget about the security of the private keys. Now we are preparing the config. The config is placed in the file : In the section
deb http://deb.debian.org/debian/ buster-backports main
# deb-src http://deb.debian.org/debian/ buster-backports main
apt update && apt install wireguard
wg genkey | tee /etc/wireguard/vps.private | wg pubkey | tee /etc/wireguard/vps.public
/etc/wireguard/wg0.conf
[Interface]
Address = 192.168.99.1/24
ListenPort = 57953
PrivateKey = 0JxJPUHz879NenyujROVK0YTzfpmzNtbXmFwItRKdHs=
[Peer] # OpenWRT
PublicKey = 36MMksSoKVsPYv9eyWUKPGMkEs3HS+8yIUqMV8F+JGw=
AllowedIPs = 192.168.99.2/32,192.168.0.0/24
[Peer] # Smartphone
PublicKey = /vMiDxeUHqs40BbMfusB6fZhd+i5CIPHnfirr5m3TTI=
AllowedIPs = 192.168.99.3/32
[Interface]the settings of the machine itself are indicated, and in [Peer]- settings for those who will connect to it. The AllowedIPssubnets that will be routed to the corresponding peer are written in comma separated. Because of this, the peers of the "client" devices in the VPN subnet must have a mask /32, everything else will be routed by the server. Since the home network will be routed through OpenWRT, we AllowedIPsadd the home subnet to the corresponding peer. In PrivateKeyand PublicKeydecompose the private key generated for the VPS and the public keys of the peers, respectively.
On VPS you only run the command, which will raise the interface and add it to the Autoplay:
systemctl enable --now wg-quick@wg0. The current status of the connections can be checked with the command wg.
OpenWRT configuration
Everything you need for this step is in the luci module (OpenWRT web interface). Login to it and open the Software tab in the System menu. OpenWRT does not store a cache on the machine, so you need to update the list of available packages by clicking on the green Update lists button. After completion, drive into the filter
luci-app-wireguardand, looking at the window with a beautiful tree of dependencies, install this package.
In the Networks menu, select Interfaces and click the green Add New Interface button under the list of existing ones. After entering the name (also
wg0in my case) and selecting the WireGuard VPN protocol, a settings form with four tabs opens.
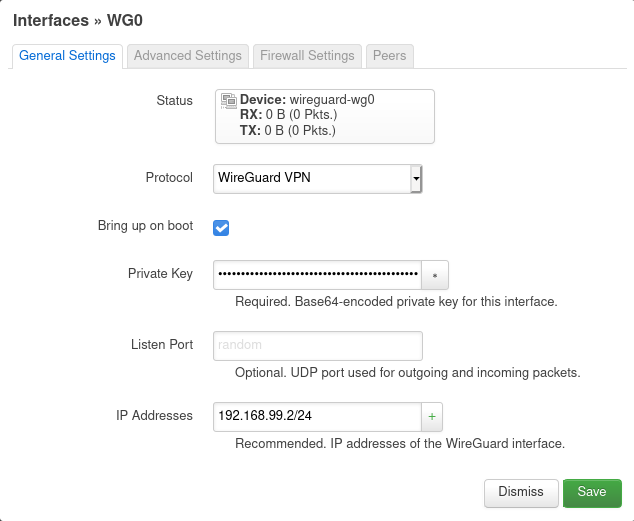
On the General Settings tab, you need to drive in the private key and the IP address prepared for OpenWRT along with the subnet.
On the Firewall Settings tab, connect the interface to the local network. So connections from the VPN will be free to get to the LAN.

On the Peers tab, press the only button, after which, in the updated form, fill in the VPS server data: public key, Allowed IPs (you need to route the entire VPN subnet to the server). In Endpoint Host and Endpoint Port, enter the IP address of the VPS with the port specified in the ListenPort directive, respectively. Check Route Allowed IPs to create routes. And be sure to fill in Persistent Keep Alive, otherwise the tunnel tunnel from the VPS to the router will break if the latter is behind NAT.

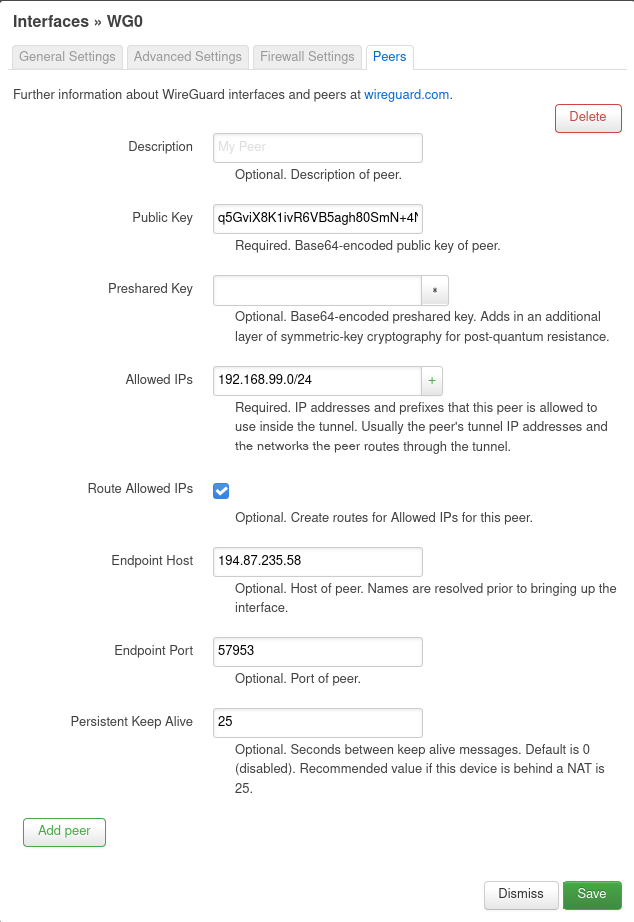
After that, you can save the settings, and then click Save and apply on the page with the list of interfaces. If necessary, explicitly start the interface with the Restart button.
Setting up a smartphone
You will need the Wireguard client and it is available on F-Droid , Google Play and the App Store. After opening the application, press the plus sign and in the Interface section, enter the connection name, the private key (the public key will be generated automatically) and the phone address with the mask / 32. In the Peer section, specify the VPS public key, a pair of addresses: VPN server port as an Endpoint and routes to the VPN and home subnets.
Bold screenshot from phone


Click on the floppy disk in the corner, turn it on and ...
Done
Now you can access home monitoring, change router settings, or do whatever you want at the IP level.
Local screenshots




