
When businesses moved to remote locations, companies opted for RDP because of its ease of setup and use. But the transition was urgent and not everyone paid the necessary attention to safety. As a result, cybercriminals have targeted organizations.
In this article, we decided to analyze the weaknesses of the RDP protocol and tell you how to secure the company's infrastructure. We also conducted an experiment by deploying an RDP honeypot on multiple servers and described forensic artifacts that can be detected in the event of an unauthorized connection by intruders.
▍ Weaknesses of RDP
Almost 4 million RDP servers around the world are accessible from the external network today. No less of them, most likely, are available only from internal networks.
Attackers often specifically look for weaknesses in RDP servers in order to exploit them for their own purposes. So, RDP is often exposed to brute-force attacks. In addition, over the past two years, experts have discovered serious RCE vulnerabilities related to RDP.
Brute force attacks
The most common attacks on RDP are brute force attacks. They can be roughly divided into several groups.
- The simplest attacks , which consist in guessing elementary passwords without using any automation tools.
- Dictionary attacks , during which a brute-force attack of all possible passwords for the intended username is launched.
- , , , .
- Password spraying, , .
- Credential stuffing, .
Having picked up a pair of login and password, the attackers gain full access to the compromised system.
The simplest and dictionary attacks are usually given due consideration and protection by organizations. For example, it is often planned to lock an account after several unsuccessful login attempts.
At the same time, password spraying and credential stuffing attacks are often forgotten. However, such attacks are now not uncommon, but, on the contrary, have rather become commonplace. Blocking IP addresses from which multiple unsuccessful RDP login attempts are made helps to combat them. Also, prohibiting the reuse of passwords will not be superfluous. Also, you shouldn't use the same password on multiple resources.
Vulnerabilities
Since 2019, several serious RCE-related vulnerabilities have been discovered with respect to RDP. Their exploitation leads to remote code execution on the target system.
Vulnerability CVE-2019-0708, dubbed BlueKeep, was discovered not in the RDP protocol itself, but in the implementation of the Remote Desktop Service. This vulnerability allows an unauthenticated user to remotely execute arbitrary code on the target system. The vulnerabilities affect older versions of Windows: from Windows XP (Windows Server 2003) to Windows 7 (Windows Server 2008 R2). For its successful operation, you only need network access to a computer with a vulnerable version of Windows and a running RDP service. To do this, the attacker sends a specially crafted RDP request to the service, which allows the attacker to remotely execute arbitrary code on the target system. Information about BlueKeep was published in May 2019, but more than 289 thousand RDP servers are still vulnerable.
Vulnerabilities CVE-2019-1181 / 1182/1222/1226 are almost identical to BlueKeep. However, while the previous vulnerability only affected older versions of Windows, now all new versions of the OS are at risk. To exploit vulnerabilities, an attacker also needs to send a specially crafted request to the Remote Desktop Service of the target systems using the RDP protocol, which would allow arbitrary code to be executed. These vulnerabilities were published in August 2019.
Another vulnerability - BlueGate (CVE-2020-0609 / 0610) - was found in the Windows Remote Desktop Gateway component in Windows Server (2012, 2012 R2, 2016 and 2019). It also allows attackers to remotely execute code on the target system via RDP and specially crafted requests. BlueGate was published in early 2020.
▍Malware and RDP
The weaknesses of RDP do not remain out of sight of malware operators. It is not uncommon for cybercriminals to use the publicized RDP credentials to launch targeted attacks.
After gaining RDP access to the target system, the attackers manually disable anti-virus protection and launch malware. Such attacks often run ransomware such as Dharma (aka Crysis) on an infected system.
▍ Bait for intruders, or how we deployed honeypot
We decided to conduct an experiment and check what will happen with an RDP server accessible from an external network. For this, two honeypots were deployed. We used the implementation of the RDP protocol in Python - RDPY, which can be found in the public domain .
One honeypot was deployed on the DigitalOcean public server, and the other on a server in our organization's network. Three ports were available from the Internet:
- the standard port is 3389;
- two non-standard ports - 36 and 25300.
The window displayed when connecting is shown in the screenshot below.
The standard port 3389 attracted the maximum attention on the network. During the month and a half that honeypots were working, a total of 15 brute force attempts and 237 attempts to write invalid data to a socket on a public server were recorded; and, respectively, 16 and 135 attempts - on a server in the organization's network.
Also, as you would expect, the standard port 3389 was subjected to numerous scans from the network. At the same time, the public server was scanned on average 2.5 times more often than the server in the organization's network.
The scan rate can be seen in the graph below. The vertical lines here indicate Saturdays and Sundays, which fell during the honeypot period. In most cases, there was a decline in network scans at the end of the working week.
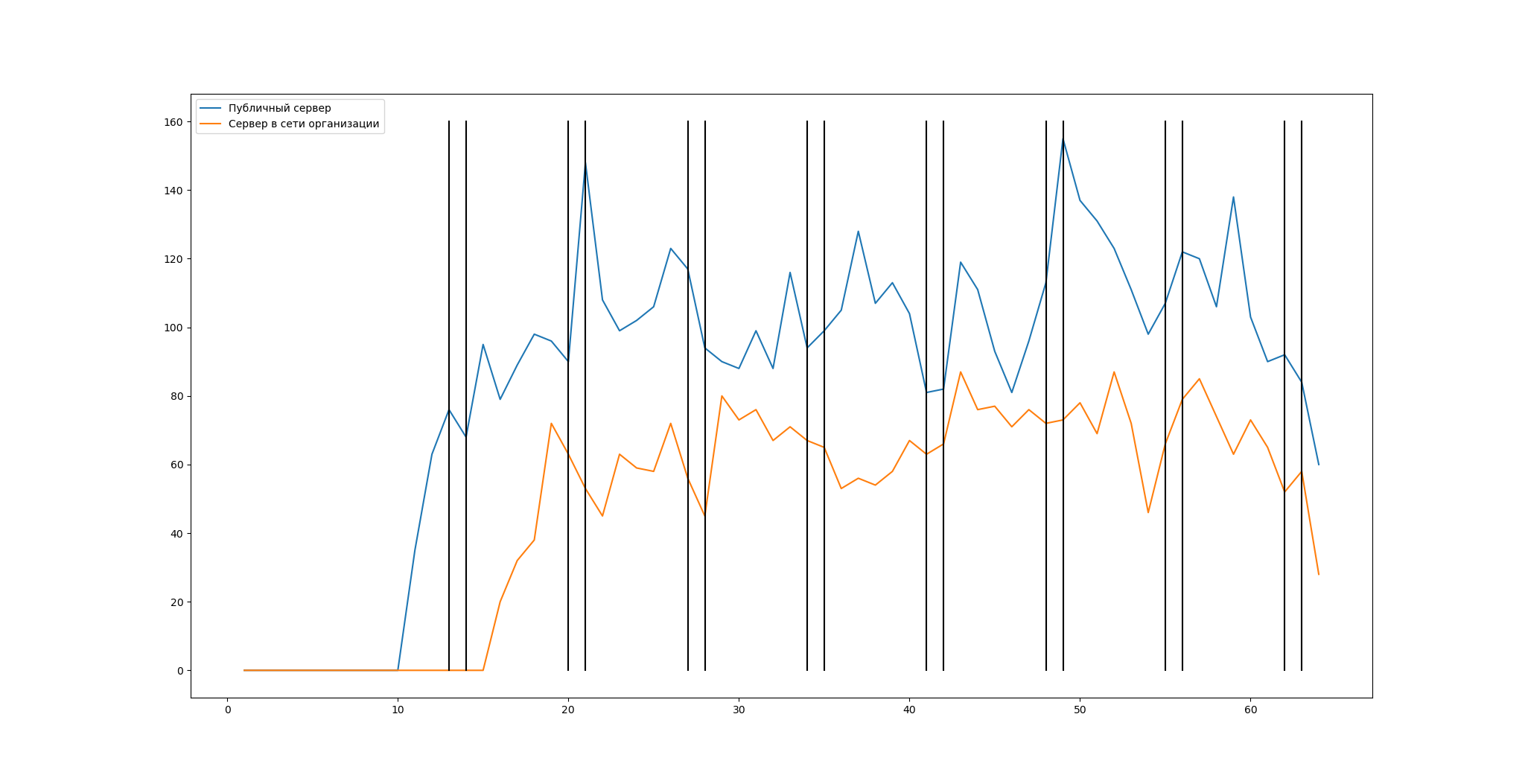
Horizontally - days of honeypots' work, vertically - the number of connections.
The blue curve is public north, the orange curve is the server in the organization's network.
Vertical line - Sat & Sun .
There were practically no attempts to scan non-standard ports. Therefore, porting RDP to a non-standard port will help protect against most attacks.
▍Security
Summarizing all of the above, you can deduce several rules that will help secure the infrastructure when connecting remotely via RDP.
- RDP. , . .
- VPN. , VPN -.
- , , , , , . . password spraying credential stuffing.
- IP-, RDP. password spraying credential stuffing.
- . -.
- Set up auditing for RDP events and regularly review connection logs to catch suspicious activity in time.
▏Where to look for traces of RDP connection▕
If you have any suspicions about compromising your system via RDP, you can try several steps yourself.
- Logs. First of all, you should immediately check the event logs:
- % SystemRoot% \ System32 \ Winevt \ Logs \ Microsoft-Windows-TerminalServices-RemoteConnectionManager% 4Operational.evtx
Event 1149 for a successful connection before authentication using login and password, but after authenticating the IP address of the connection source. It is important to look for connections from unusual IP addresses; brute-force passwords can also get here. - %SystemRoot%\System32\Winevt\Logs\Security.evtx
4624 — , 4625 — , 4778 — , 4634 — . «LogonType». 3, 10 7. IP-, — . - %SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
21, 22 25 — , 23 — . IP-.
IP-, . , (, .).
. Security.evtx, — Security.evtx Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx . , SIEM-. - % SystemRoot% \ System32 \ Winevt \ Logs \ Microsoft-Windows-TerminalServices-RemoteConnectionManager% 4Operational.evtx
- . , , . RDP-, . , , TCP (, RDP). . , , X, X+N . , .
If traces are found
If you find traces of successful penetration through RDP, you must first of all:
- try to isolate the attacker (or completely disconnect the infrastructure from the Internet, or disconnect critical servers from the local network);
- check the domain controller for signs of hacking, as well as check file dumps and other possible targets of the attacker.
There is a significant chance that the infection has already spread through internal resources. If this happens, you need to check for PowerShell startup events, antivirus triggers, and others. And the best thing is to immediately contact a computer forensics specialist.