
Intercepted NATO DVB streams (2002)
For many years hackers have been conducting demonstrative hacking of civil and military satellite communications, but the security of those remains at a low level. At the latest Black Hat 2020 conference, Oxford student James Pavour demonstrated what satellite traffic is currently on the air and what private information can be extracted from it.
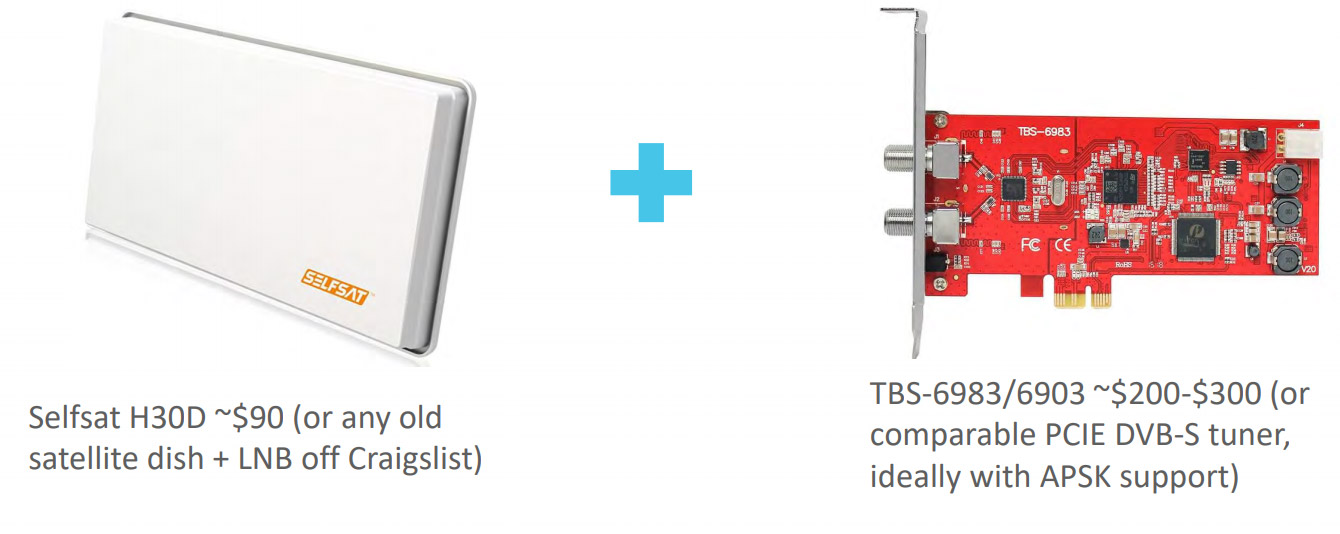
For several years, Pavur listened to signals from 18 Internet satellites from European territory. The recipients of the information are individuals, ships and aircraft on an area of about 100 million square kilometers from the United States to China and India. For the organization of such a station, equipment is available for about $ 300:
Here are some examples of interesting things we managed to find:
- Chinese airliner receiving unencrypted navigation information and flight data. Traffic was on the same connection that passengers used to send emails and browse the web, increasing the likelihood of passengers being hacked.
- A system administrator who logged into a wind turbine control system in the south of France, with a session cookie intercepted for authentication.
- , , . , , , .
- , Windows, LDAP.
- .
- .
During the study, Pavur collected more than 4 terabytes of data from 18 satellites. He also analyzed new protocols like Generic Stream Encapsulation and complex modulations including APSK. Although the essence of the attack has not changed over the past 15 years, there are still many vulnerable satellite streams that are disclosed and analyzed when intercepting traffic.
The attack mechanism is as follows. Using publicly available information showing the location of a geostationary satellite, a hacker points an antenna at it and then scans the Ku-band of the RF spectrum until a signal is found lurking in a lot of interference. This is where the PCIe card is plugged in to interpret the signal and record it like a normal TV signal. The recorded binaries are scanned looking for strings like
httpand conforming to standard programming interfaces to identify Internet traffic.
The installation allows you to intercept almost all transmissions from the provider to the user via satellite, but tracking signals in the opposite direction is much more difficult. As a result, we only see the content of the HTTP sites the user is viewing, or unencrypted emails, but not requests
GETor sent passwords.
Using HTTPS solves most of the problems, but DNS requests are not encrypted and in most cases it is still possible to de-anonymize the client.
At first, Pavur investigated the "sea" traffic that is transmitted to ships.

But then he turned his attention to aviation, where a lot of interesting things are also happening. In particular, in the service messages from the on-board computer, a specific flight number and its coordinates are transmitted.

Information is transmitted over the same channel as the entertainment traffic of passengers, that is, the separation of service and user traffic occurs somewhere at the program level.
The researcher pays special attention to the advantage of a hacker in hijacking TCP sessions, since he has packets that have not yet reached the client. In theory, it is possible to impersonate the plane or ship that the ground station communicates with by sending metadata to the provider that clients use to authenticate - report incorrect location or fuel levels, false readings from heating, ventilation and air conditioning systems, or transmit other fake confidential data. This spoofing can be used for a DoS attack on a ship or aircraft.

Basically, for a hacker, satellites, ships and airplanes are just computers that send data over an open channel.