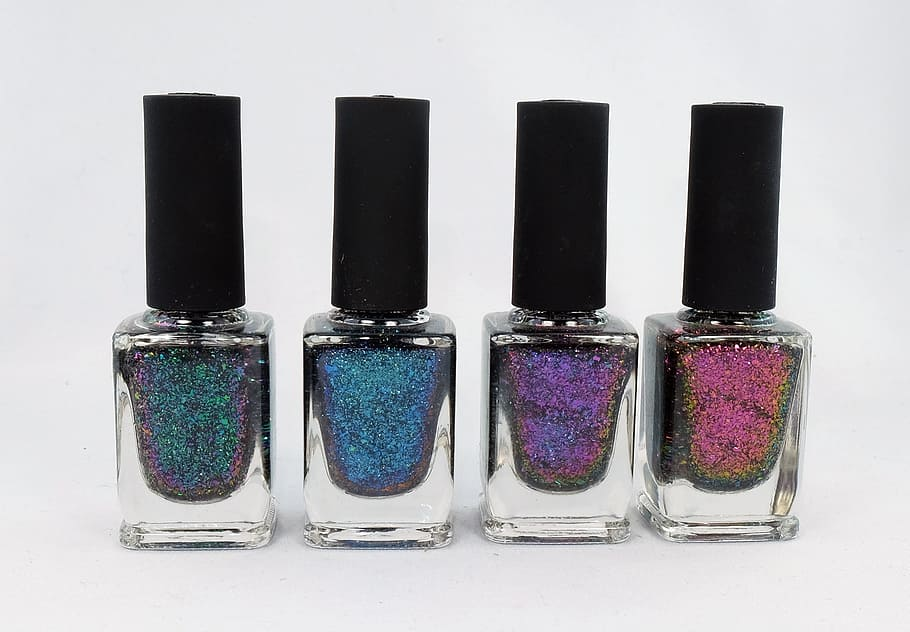
An important component of protection against unauthorized access
Every reasonable person has something to hide. This is normal. No one wants to see his private keys to access the repository, important code or personal photos in a deer sweater leaked.
Therefore, I thought about it and decided to collect in one place a certain standardized checklist for comprehensive protection of my laptop. I deliberately cut off stationary PCs because they are less susceptible to "accidentally forgot in the bar" threats. With 6 kilograms of hard drives, heat pipes and a tower cooler, this is much more difficult to do.
I will try to go through the main threats and protection methods. For example, people often forget that entering a password under the camera is a bad idea. I would be extremely grateful for your additions.
Paranoia is unproductive
We can fantasize as much as we want about termite charges in the battery compartment and booting from an external hard drive disguised as a coffee maker. No, all this can really be implemented, but, as practice shows, it is quite pointless and greatly complicates the life of the owner.

Unfortunately, the most sophisticated schemes are often broken with the same $ 5 wrench. Therefore, we will immediately define the level of protection as reasonably balanced, where, in order to turn on the laptop, it is not required to collect the key of six from Shamir fragments.
Our biggest concern is that the laptop can be physically accessed. This is fraught with leaks of hard drives and rootkit bonuses. This is especially dangerous if you have not noticed that the computer has been in someone's hands.
Feel like a magic princess
The problem of hidden access is solved to idiocy simply. Just to begin with, you will need to learn how to make a poker face in a store that sells the cheapest fake nails, plastic earrings and similar joys for girls of 10 years old. Yes, we need a glitter polish. Oddly enough, but it is almost impossible to disguise the fact of unscrewing the screws of the case, if a drop of such multicolored horror is applied to them for 50 rubles. The structure of the varnish will be disrupted and the orientation of the particles will change even when trying to smooth everything with a drop of solvent. It is especially convenient to use two different polishes with long hair-like particles for this.
In addition, you can use standard options like kensington lock. But this is more likely not about protection from hidden access, but about fastening the laptop to a heavier cabinet so that it will not be dragged away while you are out for coffee.
Unlocking
Any more or less modern OS assumes automatic blocking of the user session when closing the laptop lid, manually blocking it, or after a certain timeout. Unfortunately, any attempt to do it safely leads to the "make it inconvenient" option. Therefore, it makes sense to consider the disadvantages of convenient and popular simplified unlocking methods.
Fingerprint, if there is a dedicated laptop sensor. Not bad in most situations, but has some fundamental problems common to all biometrics. It cannot be replaced as the number of uncompromised fingers tends to run out. It is also very easy to use under duress. I think I won't be mistaken if I assume that most people use the print of the right index finger. In addition, standard consumer-segment sensors do not control indirect parameters such as the presence of capillary pulsation, which allows not only to put a finger separately from the owner, but also a banal replica taken from a glass in a bar.
Various kinds of face unlock have also become quite popular after mobile phones, but in most cases they are absolutely unsuitable for access control. A regular camera is happily unlocked in response to a photo from a social network that is shown on the screen of a mobile phone. Well, all the same problems with involuntary access.
Trusted devices like fitness bracelets are more interesting. But they have another problem - uncontrollable range. It seems to have moved away from the laptop for coffee, but the connection with the bracelet is still preserved. In reality, this method is only suitable for protecting against theft of your computer.
Summary: The best way is to enter the password from the unrecoverable storage in the owner's gray matter. But if it is very annoying, then the fingerprint, although it reduces the protection. And the truth is, you shouldn't enter passwords under surveillance cameras. The permission is more than enough to restore it.
Encryption
This is a point that doesn't really make sense to discuss. It is definitely necessary to encrypt. Yes, formally, this increases the risk of irreversible data loss. But there are two counterarguments at once:
- It is better to bury especially valuable data in the form of encrypted minced meat, but not to give it to the wrong hands.
- The hard drive can already fail at any time, because the stars do not align well. Therefore, encryption does not in any way cancel backups.
It remains to decide how best to implement it. The greatest trust is traditionally given to free implementation options. LUKS with dm-crypt for Linux and full disk variants like VeraCrypt for all OS variants. The latter option is good for its flexibility in the choice of disk encryption algorithms and the ability to use tokens and key files on external media. Unfortunately, using files in addition to a password is only possible for containers at the OS level, but not for full disk encryption.
In addition to these options, I would also like to propose full-disk encryption with SED - Self-encrypting disk. At the moment, there is the TCG OPAL 2.0 specification, which most modern SSDs comply with. The main advantage of this approach is zero encryption overhead. The CPU does not even try to occupy this task, and all encryption is completely transparent to the operating system. Everything is dealt directly with the SSD controller. Moreover, if we look at the specifications for the common Samsung EVO series, it will be clear that they, in principle, perform AES encryption of all data with a hard-wired key out of the box. It just doesn't add another custom key on top of this key by default. But after activating encryption, the disk will be accessible only after entering the user key at boot. There is a very good oneSee Dell's manual on this topic.
It is important not to forget that all encryption is useless the moment the computer is in an unlocked state. Therefore, it is important to take care of automatic blocking after an acceptably short period of time. There is a problem with Self-encrypting disk. The keys are reset at the time of the complete on-off cycle. Since the encryption process is transparent to the OS, regular deauth does not block the hard drive. Moreover, on some laptop models, the SSD does not interrupt power at the time of reboot, which potentially makes the entire system vulnerable. I recommend reading the BlackHat presentation on this topic .
Also, don't forget to back up your data. Usually, the best option would be to use a commercial cloud with encrypted data offloading. Or you can set up your Nextcloud and organize data replicas on trusted machines.
Other obvious and not so obvious points
Please update in a timely manner. I myself sometimes sit for a long time on Ubuntu LTS, which has already gone into oldstable. But still, do not delay until the end of the security support for your OS and key components. Each unclosed CVE is a potential attack vector.
Never connect unknown devices. It's corny, but this is a typical vector of gaining control, especially if the OS has vulnerabilities or is used zero-day. If you really need it, then it is better to use the live-cd of any linux distribution.
Keep track of the software you install. Now all and sundry want to dig into your files. It is difficult to hide from Microsoft, one can only hope that they do not ignore at least some checkboxes. Well, on the efficiency of telemetry filtering at the DNS level from the local pi-hole. But in addition to system utilities, there are also third-party antiviruses, cloud storage clients with a murky EULA and the rights to fill you in a "shortcut for a video conferencing application" of 101 megabytes. Prefer free software alternatives whenever possible. They, as a rule, do not create such game.
Check list
- Protection must be proportionate to the threat. Use simple, reliable methods that don't get in the way.
- Provide protection against hidden opening of the case. A couple of drops of nail polish will solve this problem.
- . , , .
- . — LUKS VeraCrypt , CPU IOPS. — TCG OPAL 2.0. .
- . - , - .
- security- .
- .
- .
